Medjed
Introduction
In this walkthrough we will be solving Proving Grounds Intermediate Windows box Medjed. Let’s start ..
Nmap
TCP
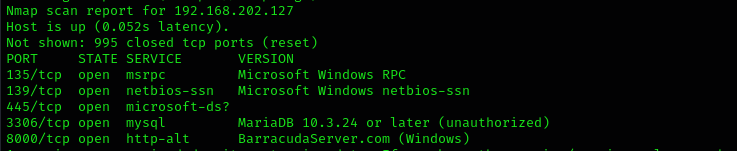
Run a quick Nmap TCP Scan:
1
sudo nmap -sV --open $IP
Services
Port 139/445
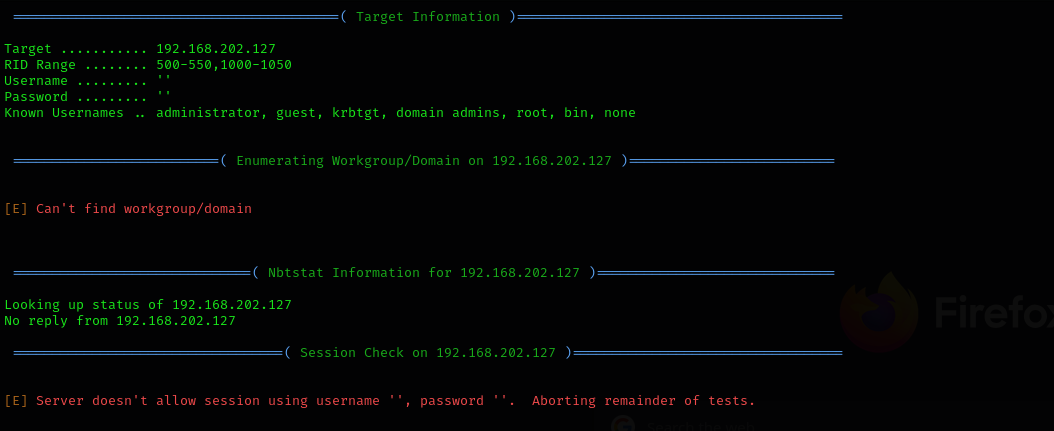
Run enum4linux to check if we can access the machine using null or anonymous credentials
1
enum4linux $IP
Port 3306
Remote login is not allowed
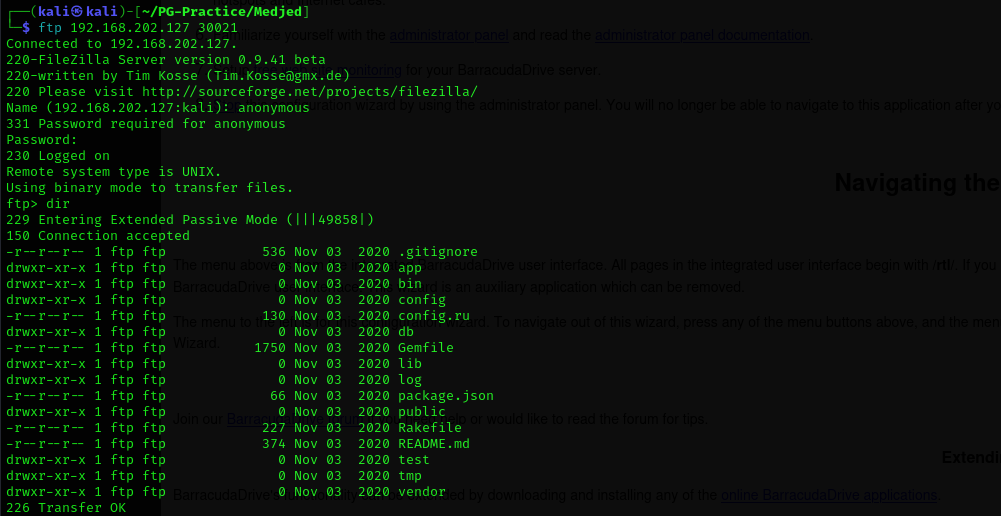
Port 30021
Anonymous login is allowed
But nothing of special interest was found in here.
Web
Port 8000
- Remember this for privilege escalation Barracuda6.5-LocalPrivEsc
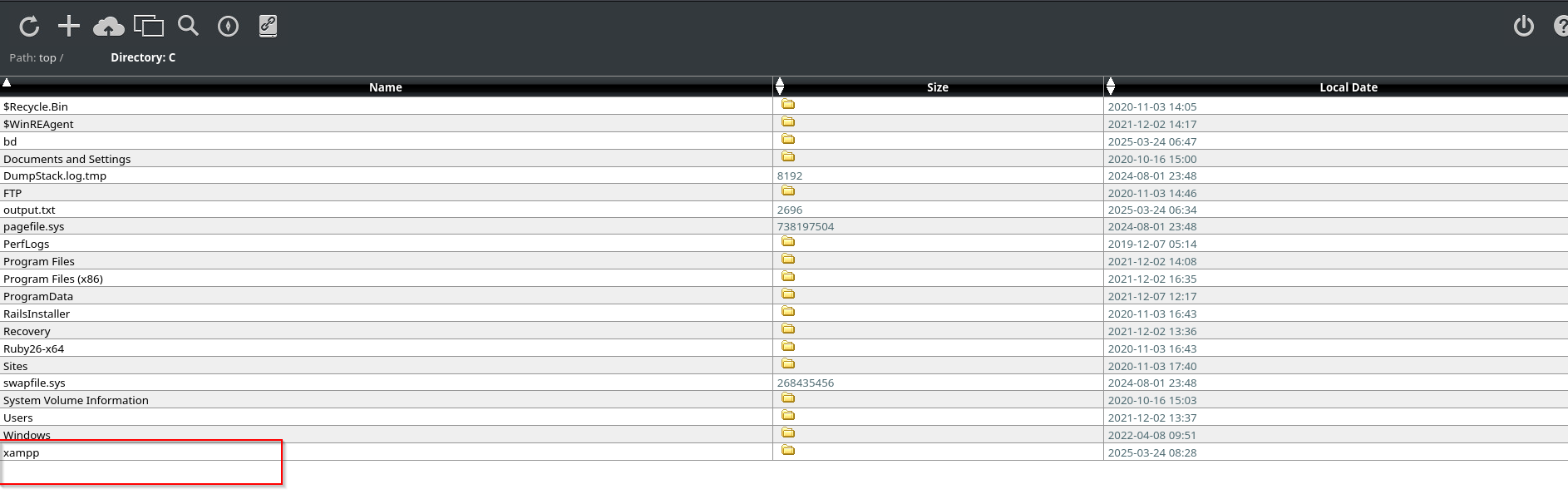
- Found in web file manager under C:\xampp
Exploitation
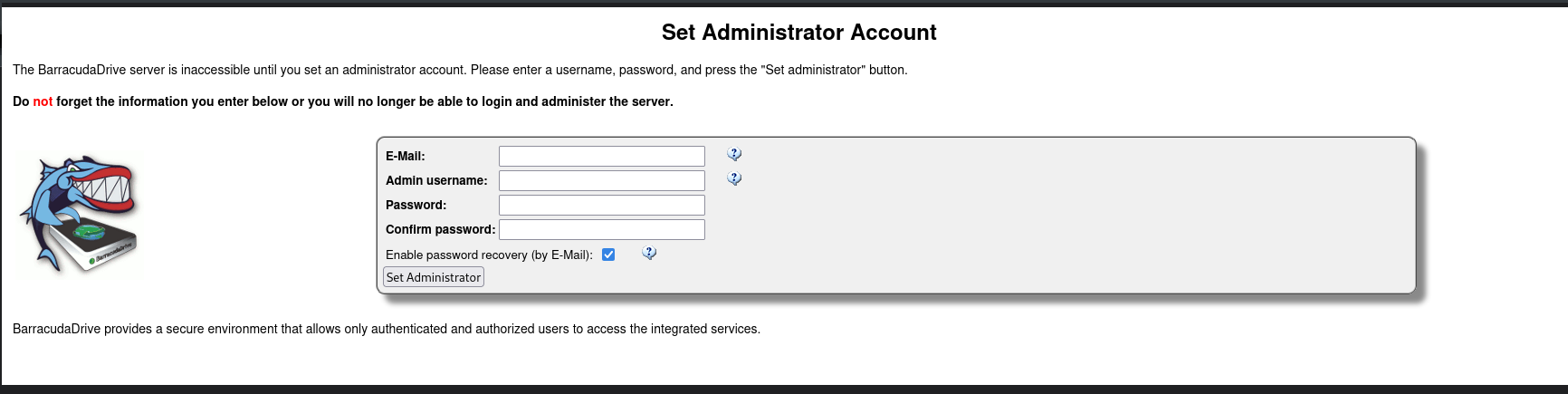
When accessing the web page it says the configuration wizard must be filled before interacting so we can go and set an admin user:
We can see xampp server suite is present on the target machine
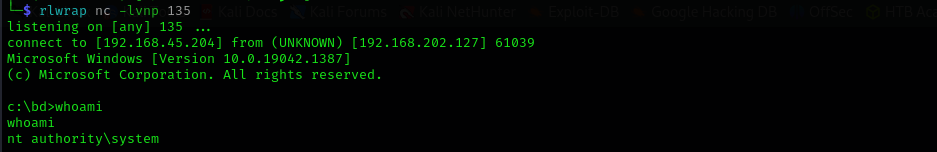
I see that target server can run Lua shells, I am gonna try to uploaded rev.lsp under xampp\htdocs and access it from browser which should return me a reverse shell.
Even if Apache itself runs as a limited user (e.g., LocalService), it may be spawning the Lua interpreter as SYSTEM, especially if:
- The Lua interpreter is installed as a service running as SYSTEM.
- You misconfigured the Apache handler or CGI setup to run Lua with higher privileges.
https://github.com/the-emmons/lsp-reverse-shell
Now we are NT authority\system.
Mitigation
- Restrict Web Root Access: Ensure that the web application does not expose sensitive directories like the entire filesystem. Limit access strictly to required directories, such as the web root (e.g.,
xampp/htdocs). - Disable Unused Interpreters: If Lua scripting is not essential for the application, disable its interpreter on the server. This reduces the attack surface significantly.
- Implement File Upload Restrictions: If file upload is allowed, validate file extensions and MIME types, and store uploads outside the web root to prevent direct execution.